ACME 60 day renewal schedule and scheduled Firewall Rule for HTTP & HTTPS allow
-
Hi Team
A month ago I successfully setup the Lets Encrypt ACME certificates for my pfSense edge appliance and some internal servers within. In creating the ACME certs, I added the 60 day auto-renewal.My pfSense appliance doesn't normally allow HTTP and HTTPS connections from the world so i (unsuccessfully) created a Firewall alias to allow HTTP and HTTPS connections from ACME's FQDN's
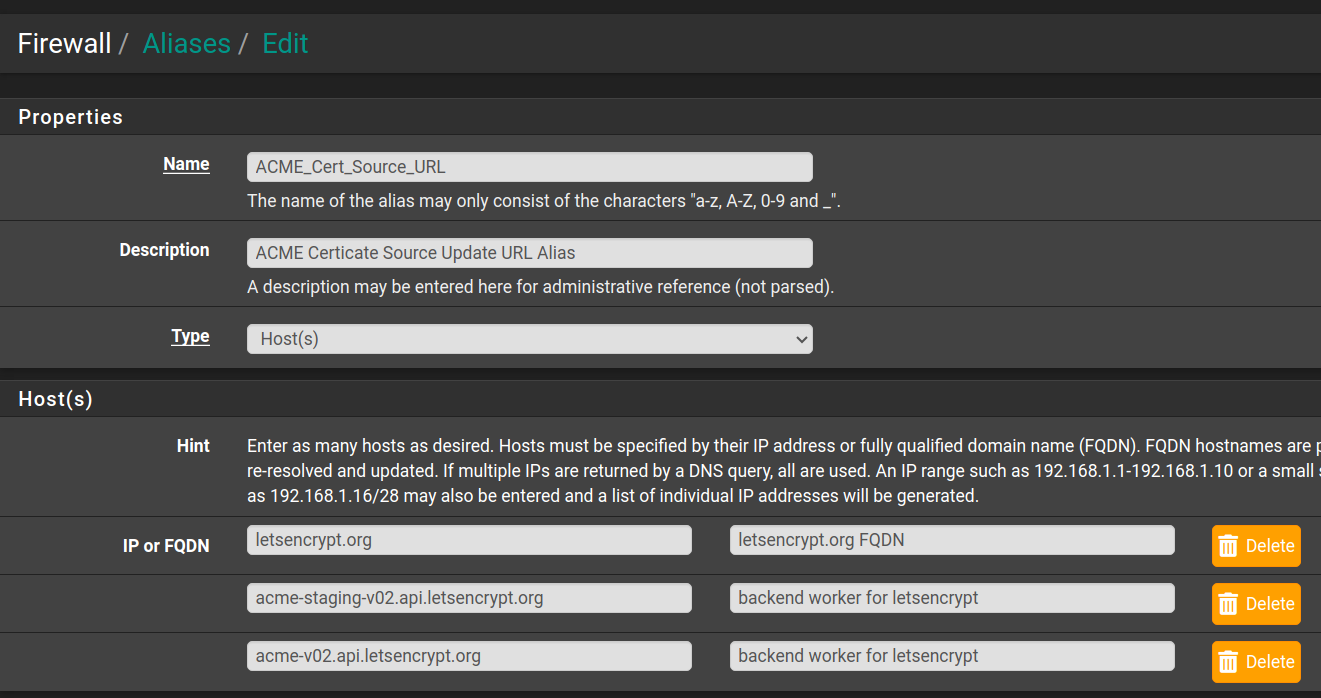 I don't think this is thorough enough for Lets Encrypt as manually renewing the certs created LOTS of inbound connections from LOTS of sources in the firewall logs.
I don't think this is thorough enough for Lets Encrypt as manually renewing the certs created LOTS of inbound connections from LOTS of sources in the firewall logs.Option 2: Create a Firewall schedule that allows HTTP and HTTPS inbound connections from the world for the same 60 day / time period. The Firewall schedule has a 15 minute min time period. (the below s/shots are 3 separate pfSense tabs)
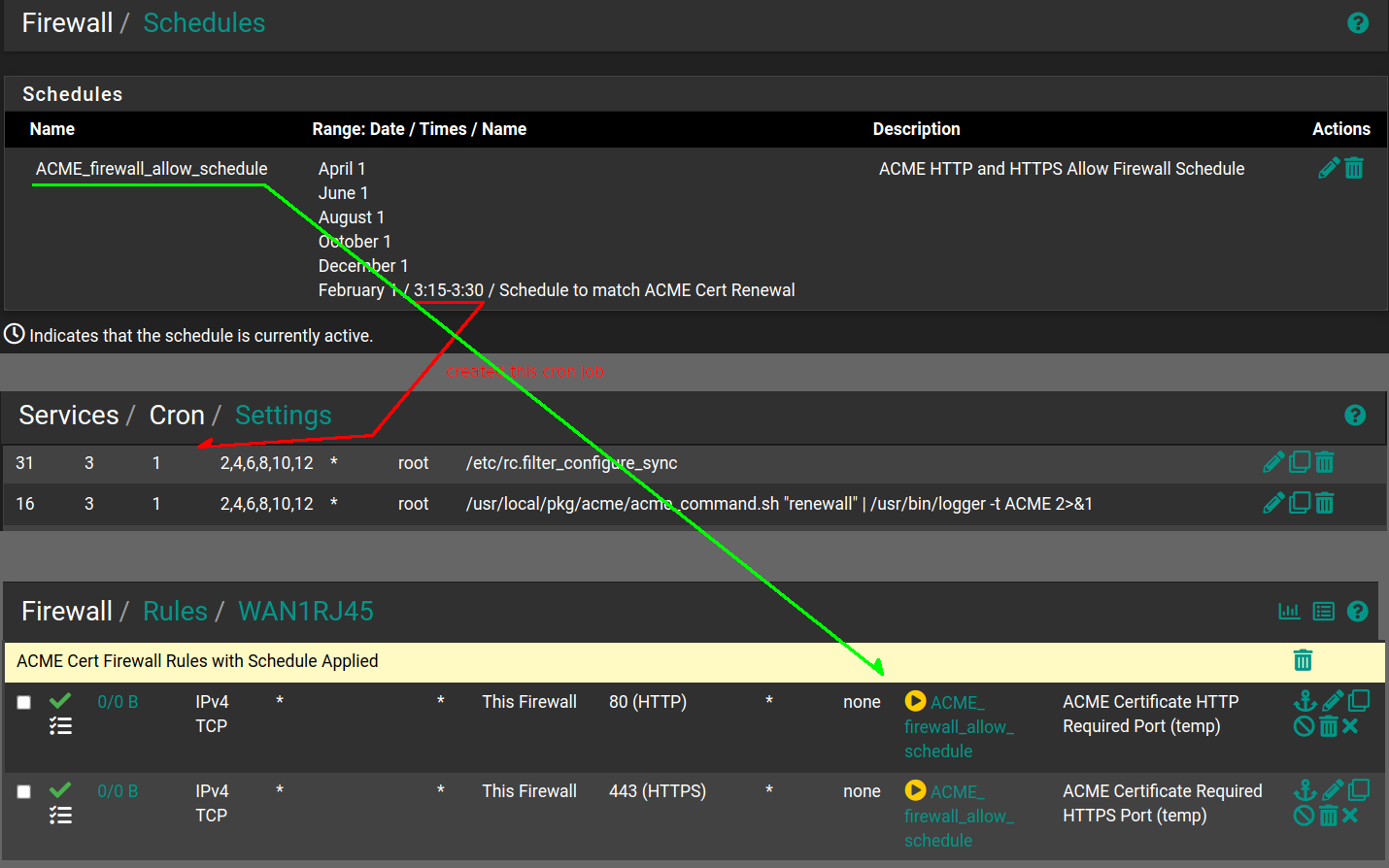
Has anyone had any success doing this -or- are there better ways to accomplish what I'm trying to do? Would I be better off to combine the 2 separate cron job commands into 1 cron job?
-
@Josho_SAI Does ACME cert renewal require inbound HTTP/HTTPS sessions??? I can’t believe that is needed as it would be impossible to handle/allow in bigger organisations.
-
@keyser
Big organisations wouldn't be using the Let's Encrypt Webroot certificates -
Even for small entities, or even for individuals : use RFC 2136 or something that's close to that.
Most serious ( ? ) domain name registrars offer such a service.It works like this :
It cert renewal time.
Ask Letenscrypt for a random hash.
Place this txt record in the domain name's DNS zone (in the registrar). That's what all these acme dns methods are al about.
Wait for a minute or two to give DNS the time to update the zone over all the DNS slaves.
Then tell Letsencrypt : go ahead, check.
Undo the txt recods.
Get the certificate.
Done. -
Another benefit of using the ACME DNS method is wildcard names. I'd previously been using the http method with my namecheap hosted domain. I could not use their DNS API with my account. I then realised I could switch nameservers, on my namecheap account, to cloudflare and can now use the DNS method with pfSense ACME package.