Cannot connect with RDP via openVPN
-
Nothing, absolutely nothing, has changed in openVPN's settings since I reanimated the network which was recently. Whether pfsense is partly to blame for that, I don't know.
Pfsense and openVPN sucks because of this problem. Can't be unless it sabotaged itself. No one seems to know the answer.
Did I mention with the build-in terminal in pfsense you can't connect with a cisco terminal console! That's why it sucks!
The RDP client from microsoft on android also sucks! It sometimes loses connection with my windows servers. Is it openVPN to blame, might be.
I don't have that problem from the inside!
-
@IrixOS said in Cannot connect with RDP via openVPN:
build-in terminal in pfsense you can't connect with a cisco terminal console!
I ssh from pfsense to my switches all the time - I don't know what you would be trying to do with actual console cable?
Are you getting an error like this?
Unable to negotiate with 192.168.9.98 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1The RDP client from microsoft on android also sucks! It sometimes loses connection with my windows servers. Is it openVPN to blame
Which is - you can't connect, or you connect and the connection drops?
-
@johnpoz No I was in windows server with the desktop in front of me and suddenly zippo, can't remember which error it gave, happened occasionally. Regarding our issue here,I am thinking to reinstall pfsense on the box. I have no other choice unless someone comes up with some findings.
First I have to buy another switch, I think this one has a hardware error. That piece of trash is brand new, can't believe it is failing.
-
@IrixOS said in Cannot connect with RDP via openVPN:
unless someone comes up with some findings.
Findings from what - you haven't provided any info.. Did you do the sniff like I showed? Lets see that the traffic even gets sent to your box your trying to rdp to - that test takes all of like 1 minute to do.
-
@johnpoz I haven't forgotten about that, I tried to do that today, but I have no knowledge of wireshark, not yet. I installed it one week ago. When I came back from sports, I saw the switch was failing so I am stuck right now.
-
@IrixOS packet capture under diagnostics - clicky clicky..
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
@johnpoz Thanks I am looking forward to perform the sniff.
-
Plan A is getting the internet back running
Plan B is the sniff for that horseshit vpn-RDP problem.The switch has been swapped. I ran into some other problem. I had to free networkspace for my management vlan. So I also had to recalculate the subnet of pfsense.
The procedure to change the ip address of pfsense according to the documentation seems to be quiet easy. I changed the LAN IP en guess what? No internet. That's very silly.
I knew I was going to run in some bullshit problem.Again an error in disguise, and I'm stuck.
Did I mention that serial console not working on pfsense? That's why it sucks, could be very valuable if you have your cisco switch near the pfsense box and can't mobilize it.
Any thoughts about the changed LAN ip in pfsense? There is alot of configuration, I an not planning to begin from scratch.
Thank you,
-
@IrixOS said in Cannot connect with RDP via openVPN:
Did I mention that serial console not working on pfsense?
Works for me..
I console in pretty much every time I do an update. I like to watch the progress.

Is this a netgate appliance - console on some other hardware would be on that hardware maker, etc.
Changing the lan IP - confuses a lot of users, they forget to update their pc they are using to the new IP range, or don't renew their dhcp lease.
When changing the IP your connecting too, especially if in a different range - that can be difficult. Would be best to change that either via console, or just connect to another IP on a different interface..
-
@johnpoz I will look into that later.
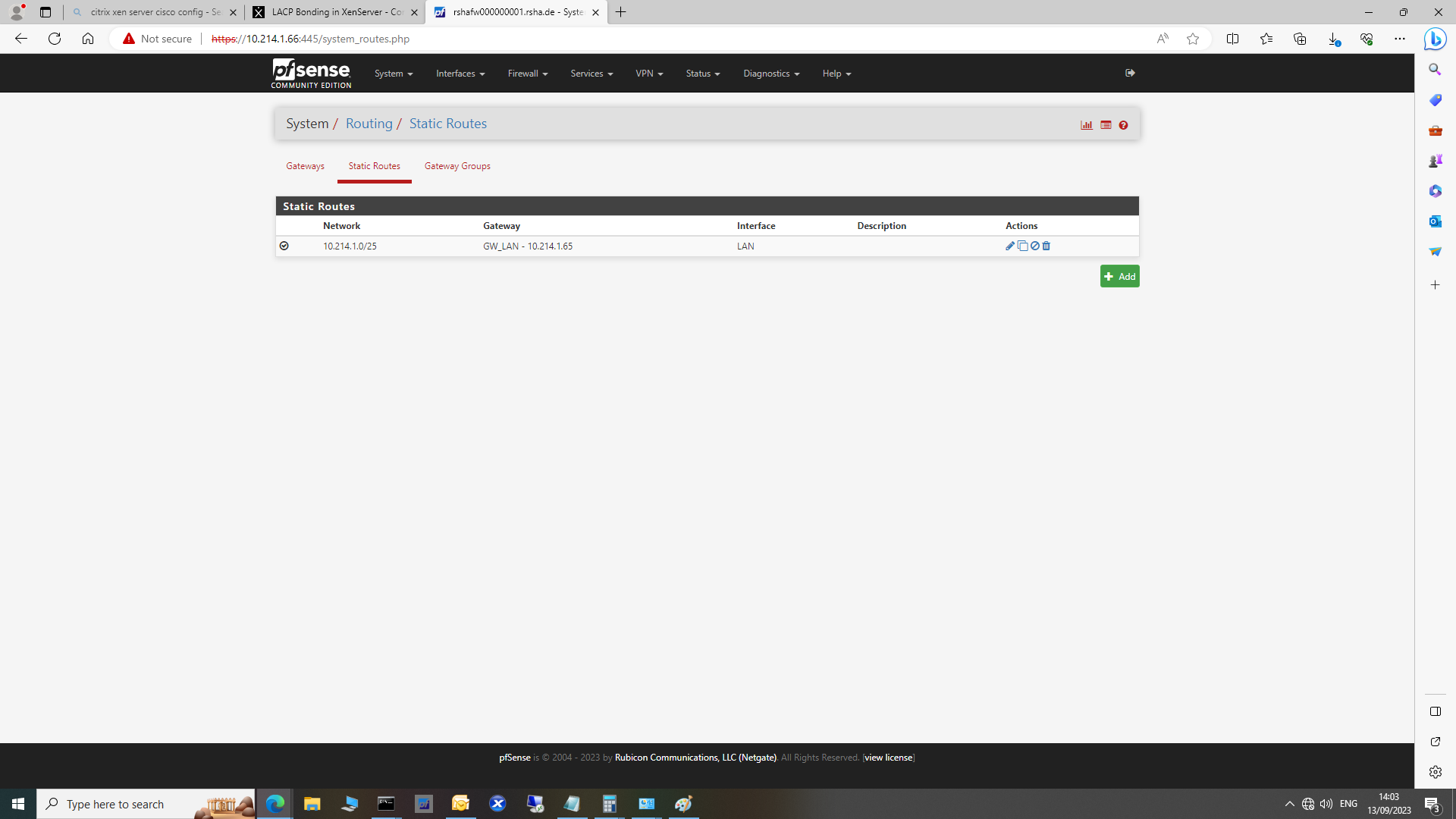
I have a subnet /30 between pfsense and the internal network.
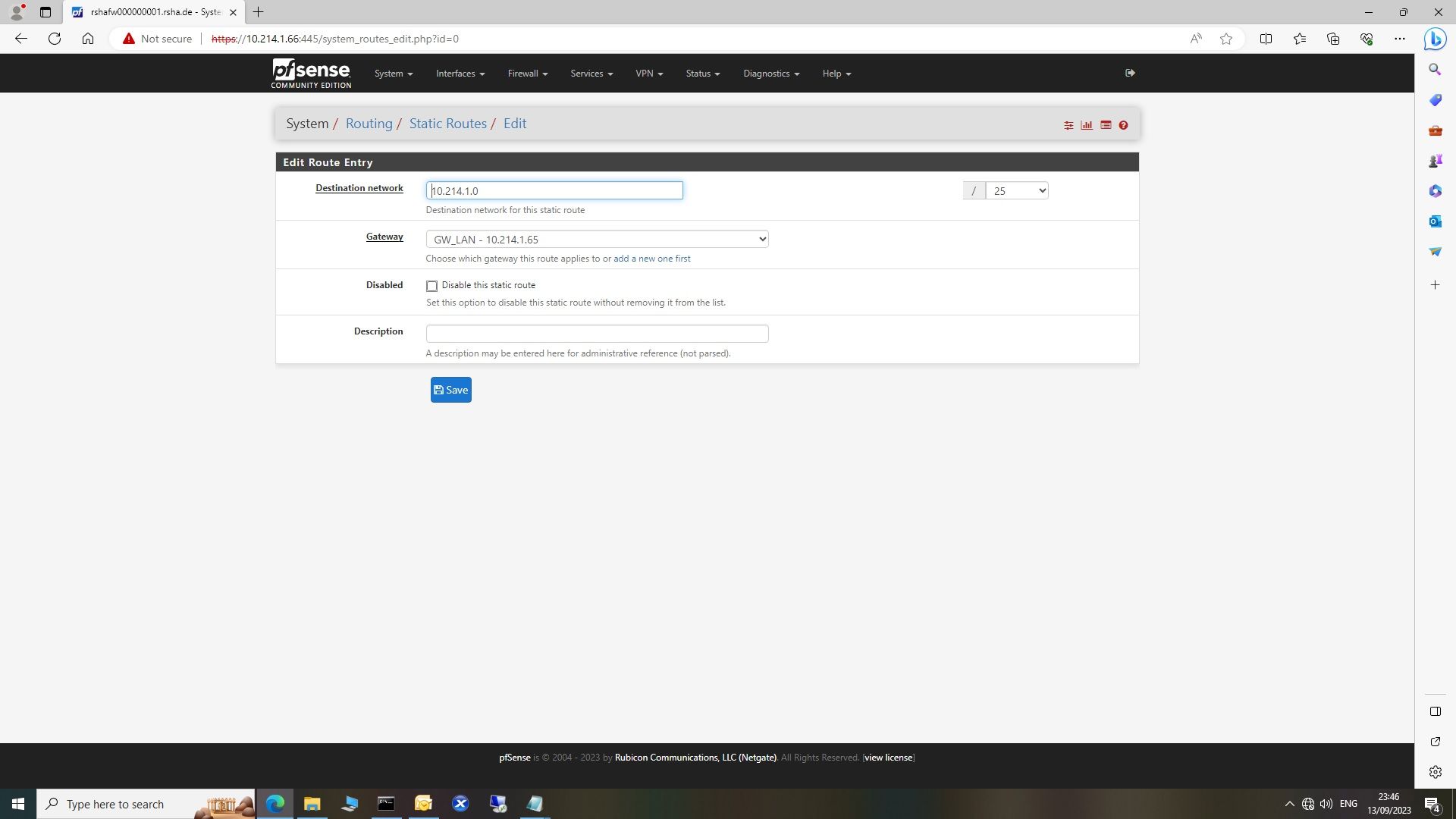
I defined the gateway and the static route in pfsense. As soon as I do that, I cannot access the internet. Took me two days and two nights to realize that. However I can ping my ISP DNS servers or access the bridged modem.Normally that should work, it always have worked with that exact setup.
I have the feeling there is some DNS issue.
When I connect my PC straight with the pfsense, I can access the net, strange,...Do you have a clue why this occurs? Normally DNS on pfsense should work out of the box.
Thank you,
-
@IrixOS so you have a transit network.. Did you adjust rules on the transit to allow for this downstream network?
Out of the box sure it should just work for dns, but you setup your routing - this should auto adjust your acls on unbound to allow your downstream network to query unbound.
Easy enough to test for dns, just do a dig or nslookup or host - whatever your fav dns tool is.
I don't use the auto acls - when you add a route to your downstream network(s) the acl should adjust. But you might have to restart unbound?
-
@johnpoz said in Cannot connect with RDP via openVPN:
Did you adjust rules on the transit to allow for this downstream network?
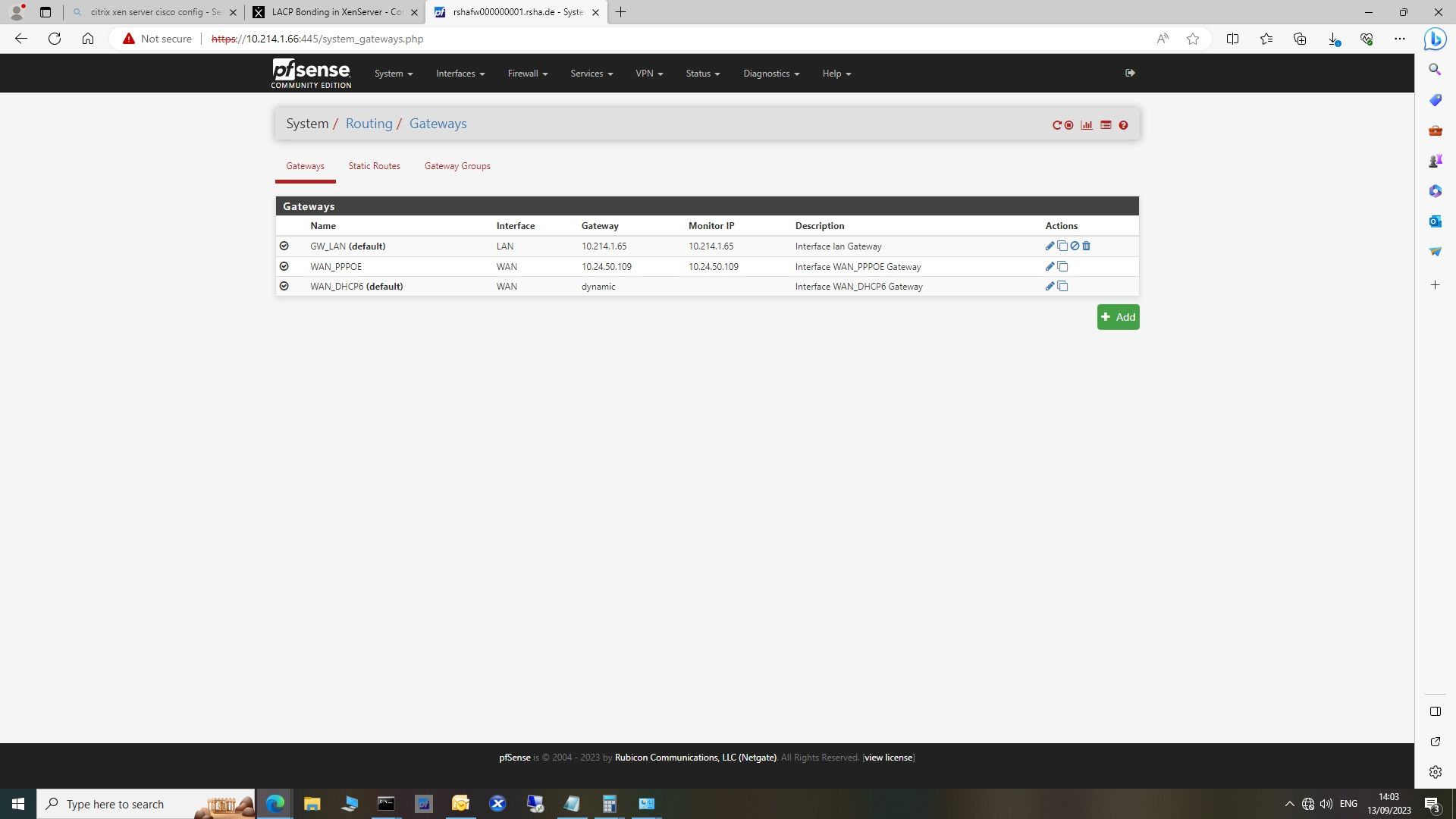
10.214.1.66/30 is the ip of the pfsensebox, 10.214.1.65/30 is the interfaces of the Layer3 switch that performs intervlan routing. I have a 0.0.0.0 0.0.0.0 default route pointing to the pfsense interface address.The 10.214.1.0/25 is the summary of all subnets.
-
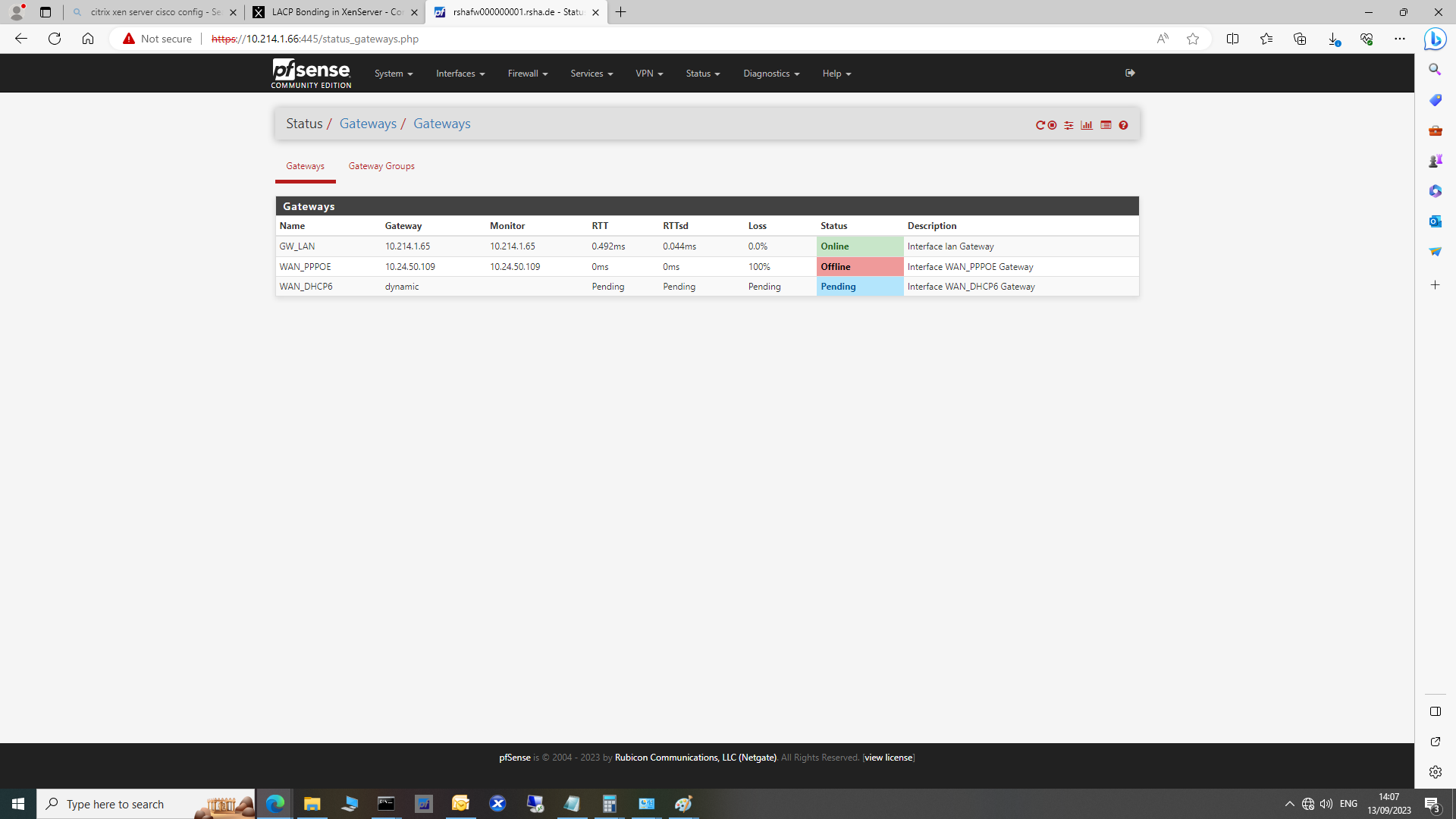
@IrixOS looks like your actual internet is down, ie your wan_pppoe so not sure how internet would work??
And your default gateway for pfsense is your LAN, so its pointing to the switch to go anywhere.. So not sure how that would work either.
-
@johnpoz I know that. When I connect my PC straight with the pfsense with a slash 30, I can access the net even despite of the red mark. How can that be?
-
@IrixOS not sure - it is possible to set interface to be up even when the monitoring says its down.
But looking at what you posted those 2 things jumped out at me, your default gateway is set to the gateway you setup for the lan.. That can be problematic, and monitoring is showing your pppoe connection is down..
So when you created the route to this downstream network, that should of auto updated the acls for unbound. But it might need to be restarted for those to talk effect. or you would want to create your own acl listing.. You can view what unbound has for acls here
[23.05.1-RELEASE][root@sg4860.local.lan]/: cat /var/unbound/access_lists.conf #snoop access-control: 2001:470:snipped:9::/64 allow_snoop access-control: 192.168.0.0/16 allow_snoop access-control: 127.0.0.0/8 allow_snoop access-control: ::1/128 allow_snoop access-control: 172.16.0.0/12 allow_snoop access-control: 10.0.0.0/8 allow_snoop [23.05.1-RELEASE][root@sg4860.local.lan]/:Just do a simple dns query to pfsense IP using your fav dns tool..
user@i9-win:~$ dig @192.168.9.253 google.com ; <<>> DiG 9.18.18-1+ubuntu22.04.1+isc+1-Ubuntu <<>> @192.168.9.253 google.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33568 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;google.com. IN A ;; ANSWER SECTION: google.com. 594 IN A 142.250.191.238 ;; Query time: 0 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) (UDP) ;; WHEN: Fri Sep 15 10:38:26 CDT 2023 ;; MSG SIZE rcvd: 55 user@i9-win:~$ nslookup > server 192.168.9.253 Default server: 192.168.9.253 Address: 192.168.9.253#53 > www.google.com Server: 192.168.9.253 Address: 192.168.9.253#53 Non-authoritative answer: Name: www.google.com Address: 142.250.190.100 Name: www.google.com Address: 2607:f8b0:4009:80b::2004 user@i9-win:~$ host www.google.com 192.168.9.253 Using domain server: Name: 192.168.9.253 Address: 192.168.9.253#53 Aliases: www.google.com has address 142.250.190.100 www.google.com has IPv6 address 2607:f8b0:4009:80b::2004 user@i9-win:~$ -
I am configuring and refitting my network with new hardware to avoid all previous problems,
Got a chinese Micro Firewall and is running pfsense+ and a bunch of 1Gb and 10Gb cisco material.
No I struggle with a new problem.I'm having a problem, I followed the NetGate manual in setting up interfaces in a lagg configuration and the 'Migrate LAN to a LAGG' section.
It says:
Navigate to Interfaces > Assignments, change the assignment of LAN to the newly created LAGG interface (lagg0)
Click Save
From then on things go wrong.
As soon as I tap 'Save', I lose my connection to the LAN interface.
There is a similar post from someone who has the same problem, but it appears that the topic is seriously deviated from, so the solution is not clear.
So,
I have a link 10.216.64.16/30 between the laptop and the LAN interface of pfsense currently.
And two links connected between the switch and two other ports on the pfsense Micro firewall.
LACP is configured correctly on the switch side,etherchannel is up and blinking. I can ping the etherchannel ip from the switch 10.216.64.21 to 10.216.64.22 but that doesn't mean that NAT is working over the port channel, unless I can unite the LAN and LAGG ports, that's what the manual says you have to do.igc1 -> LAN 10.216.64.18
igc2,3 -> lagg0 and put it into OPT and configured an ip 10.216.64.21/30So have two links, the LAN (10.216.64.17/30-10.216.64.18/30) and the LAGG (10.216.64.21/30-10.216.64.22/30)
The above from the handbook does not work.
How do I connect igc1 with igc2,igc3 without losing connection and how can I be sure that the data flow comes over both the LAN interface and the lagg ports?I would like to have those lagg ports and the LAN port over 1 Layer 3 port-channel.
And then with static routing over the Layer 3 port-channel, I can transit to the cisco internal network.I posted my question on this forum and waited a couple of days to see if there is a reaction. No one seems to answer.
Other than a few paragraphs in the manual regarding lagg, there isn't much info available.Can you help me?
-
@IrixOS said in Cannot connect with RDP via openVPN:
followed the NetGate manual in setting up interfaces in a lagg configuration and the 'Migrate LAN to a LAGG' section.
But you missed the big warning at the top of the page?
It is best to perform this change from an interface that is not involved, such as a secondary LAN, DMZ, OPT port, perhaps WAN or VPN.
I would connect to pfsense on some other interface that your not playing with.. And also connection to the switch that is not via the ports your going to be working with.. Make sure they all come up how you want, etc.
You can for sure run multiple vlans over the lag.. But you need to get it up first before you start doing anything with multiple vlans on it, etc..
-
How can I have secondary LAN other than existing one?
The LAGG is currently configured into OPT with an IP 10.216.64.21/30, the port channel works, can ping but I don't know yet if it connects to the internet over the portchannel.
Can you explain further what I must do?
Thank you,
-
@IrixOS use another interface.. that your not going to put into the lagg.. Are you saying you only have 2 interfaces and you want both of them in the lagg?
As to secondary lan? I have 6 different interfaces I could config it from.. How many interfaces does the device your running pfsense have? Or as mentioned as well come in from the wan interface if you don't have any other lan side interfaces that you don't want in the lagg.
-
igc0 -> WAN (ppoe)
igc1-> LAN (10.216.64.16/30 subnet)
igc2,igc3 -> LAGG