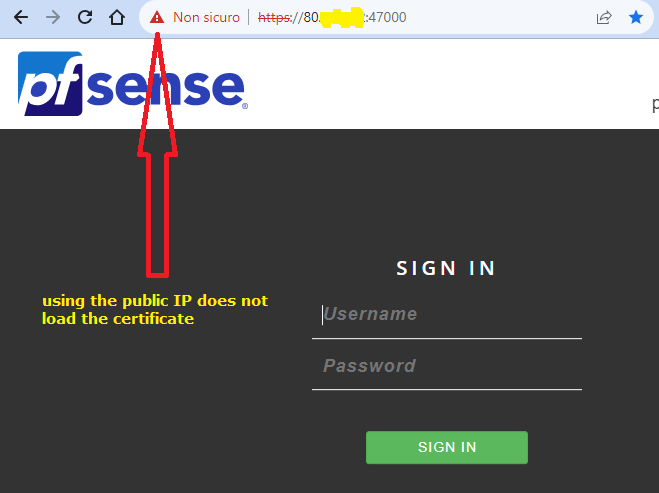
WEB GUI login using https with public IP address Certificate "Let's Encrypt" not working
-
Don't point at it


Click on it !!
Dig downwards, and look at the certificate :
You'll find :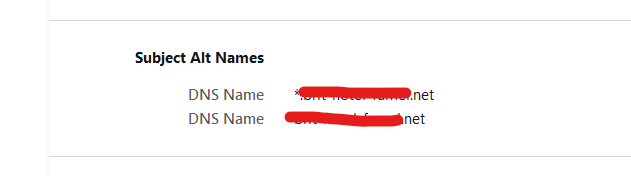
Yours will show the domain name with "it" as a tld.
These are the "names" that can be used to make this certificate valid and your browser happy.
You forgot to include

and before you try to do that : Letsencrypt won't let you include IP addresses. .... so the question is wrong ^^
And every time your IPv4 or IPv6 changes, you have to redo your certificate.
The correct way of doing things :
Never ever connect to SSH and or https from the outside.
First : activate a VPN connection to the pfSEnse OpenVPN server.
Now use
https://pfsense.your-pfsense-network-domain.it which normally point to your pfSense LAN : you are connected to the GUI.
because :
SSH : doesn't use these certificates. It use sits own certificates, valid for 10 years or so.
You can see one here, under the admin User Manager :
Don't forget to disable user.password login.
Only accept :
Before using SSH, activate the OpenVPN first. Don't (IMHO) expose SSH to the outside.
-
In the LAN using the pfsense fqn not work;

In the LAN using local IP of the gateway:

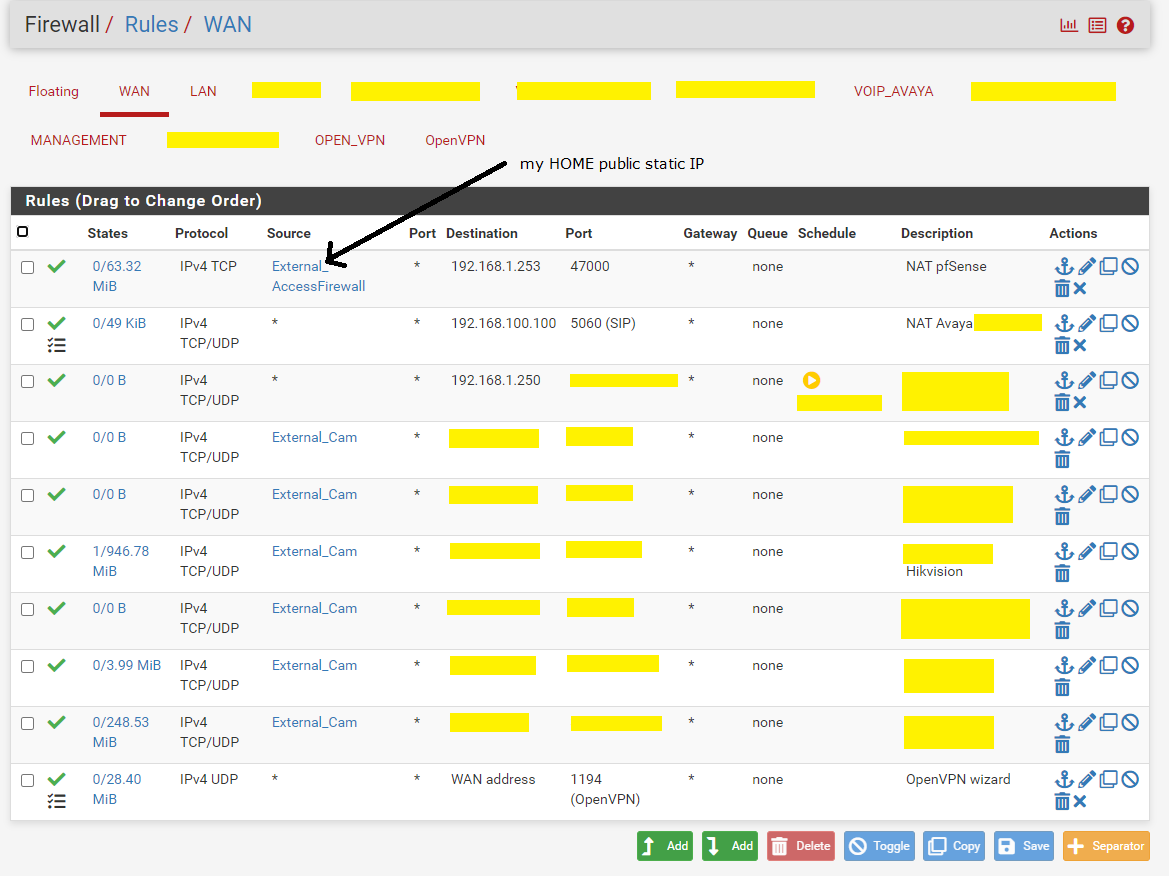
I have a 16 static public IP. Virtual IP Address
Pfsense answer on the firstFor security, how do I disable access to the firewall from the public static IP? My IP address never changes and is static 80.xxxxxxx

-
@Unoptanio said in WEB GUI login using https with public IP address Certificate "Let's Encrypt" not working:
For security, how do I disable access to the firewall from the public static IP?
In your WAN-rules...
-
@Bob-Dig can you help me make the rule?
-
@Unoptanio Show your WAN-rules and if you have (you shouldn't) your floating-rules. And you are missing the basics for using certificates so don't use LE for now.
-
@Bob-Dig
-
@Unoptanio said in WEB GUI login using https with public IP address Certificate "Let's Encrypt" not working:
For security, how do I disable access to the firewall from the public static IP?
Why do you want to disable access from your static public IP at home?
-
@Bob-Dig
@gertian says the correct safe way to do things is to access from outside via openvpn and acces to the firewal using local IP address of pfsense https://192.168.1.253:47000/
the idea is to not allow external access to the static public IP address pointing to the pfsense firewall. For web gui access only
-
@Unoptanio said in WEB GUI login using https with public IP address Certificate "Let's Encrypt" not working:
For web gui access only
In a perfect world, the pfSense GUI is only accessible from your LAN - nothings else.
Your LAN should only have devices that you trust.
The rest : on other 'LANs' ( OPTx interfaces).This is not a golden rule of course. It's just mine.
-
OK
using the GUI, I deactivated the admin user.
I created a new user "test2023"and gave him administrator privileges.
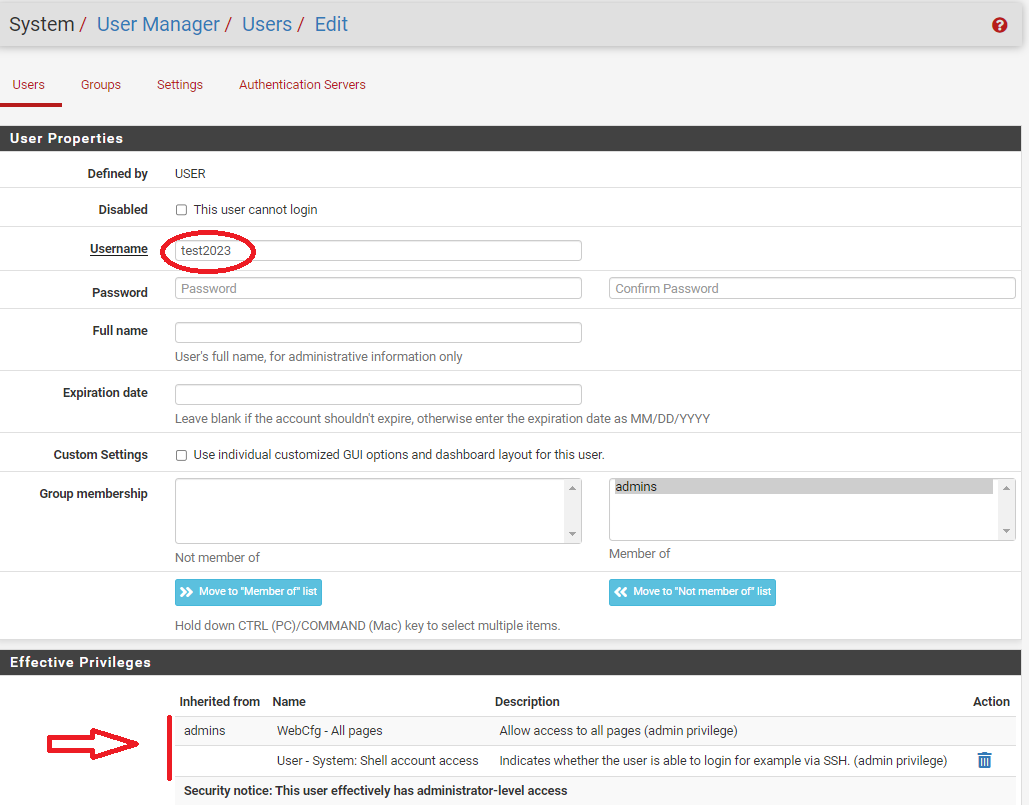
Problem:
by connecting with the putty the pfsense shell no longer offers the classic menu that appeared when logging in as Admin.
Only a prompt appearsLogin with user Test2023:

Login with user Admin:
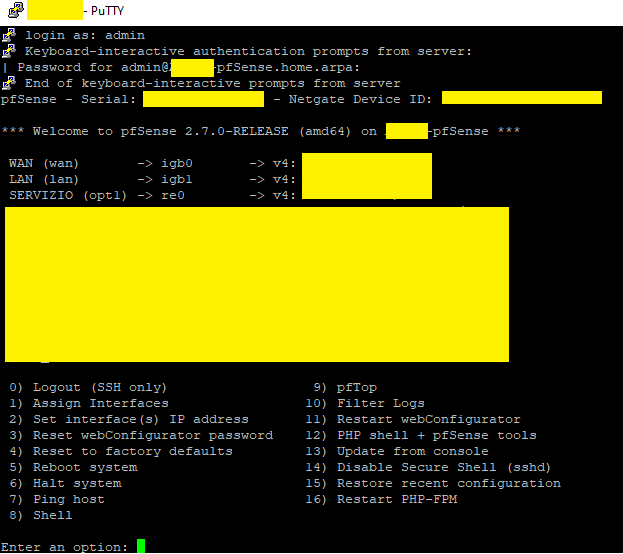
How do I view this menu, logging in with the Test2023 user?
-
@Unoptanio said in WEB GUI login using https with public IP address Certificate "Let's Encrypt" not working:
using the GUI, I deactivated the admin user.
I created a new user "test2023"and gave him administrator privileges.
Oho.
Seems like a very bad idea to me.
Non of the official Netgate docs gives such an advise.pfSEnse is a firewall, not some sort of NAS, or media serving thing with "multiple" users.
Ones in a while, the big chief comes in (the admin) does it things, and then he leaves.True : others "users" can be created for OpenVPN purposes, but these do not interact with pfSense GUI, or SSH etc, it's just a means to identify and authorize the (OpenVPN) connection.
Another example : captive portal users