How to authorize only a source from LAN to use internet
-
Hello,
I have 3 differents networks :- LAN
- LAN B
- LAN C
I want to isolate
LANfromLAN BandLAN C. I don't wantLANcan reachLAN BandLAN Cbut I permitsLAN BandLAN Cto communicate toLAN.
However, I want thatLANcan communicate with internet. For example, to use mails, internet or other. I have only one machine in this network :192.168.1.10. The gateway is192.168.1.1.I created the firewall rule :
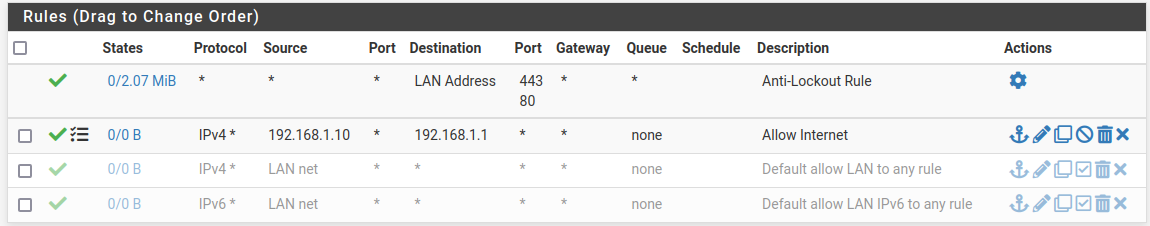
The packets are blocked, for example, I can't
ping 1.1.1.1or visit a website.
If I set destination asany, I canping 1.1.1.1and reach internet. However, I can also ping other machines inLAN BorLAN Cwhich is not I want.
How to properly isolate thisLANfrom other and keep the ability to reach internet? I would like by default deny and only whitelist the traffic I want.
Thanks in advance. -
@Dave07186 well 192.168.1.10 to 192.168.1.1 wouldn't be the "internet" that would be ANY.. public IP is quite large. That would be just pfsense IP I assume..
if you do not want lan to talk to your other lans, then create a block rule to those networks.. Or use an alias for rfc1918.. I would allow your lan to talk to say 192.168.1.1 for dns, icmp, etc.
here is example of locked down setting where - can not talk to any other network, since they are all rfc1918, but can talk to the internet
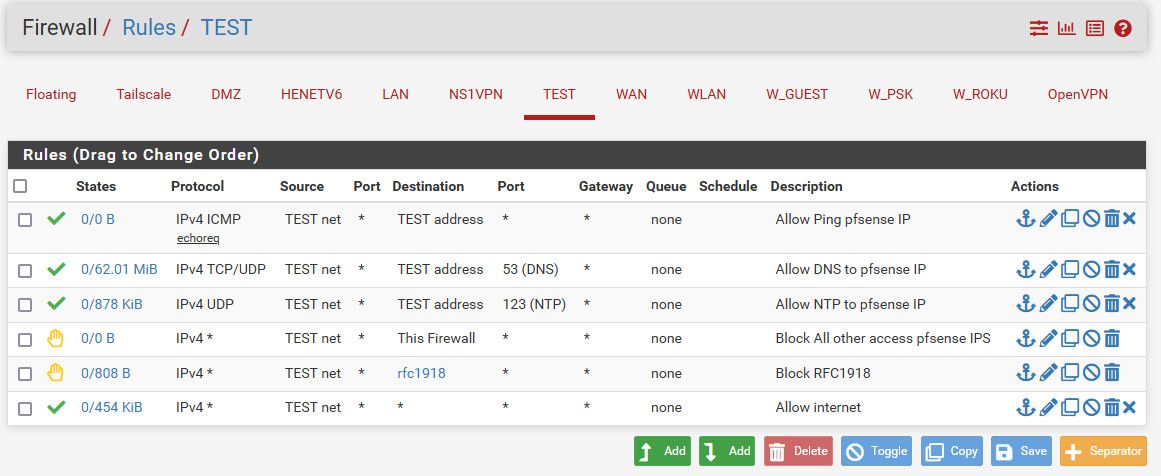
So rules are evaluated top down, first rule to trigger wins..
So can ping, dns and ntp to the pfsense IP 192.168.200.1/24 on this interface.
Then any other traffic to ANY other pfsense IP is blocked.. you may or may not want such a rule on your lan, because take it your using stuff on your lan to manage pfsense? The anti-lockout rule.
But that next rule that blocks anything to alias I call rfc1918 which contains 192.168/16, 10/8 and 172.16/12 all the rfc1918 space, so if you had another network say 192.168.3.0/24 lan would not be able to talk to it.
But if client on the lan wanted to talk to say 8.8.8.8 it would be allowed by the last rule, Ie any, ie the internet.
-
@johnpoz Thanks for your explication, this is what I needed:
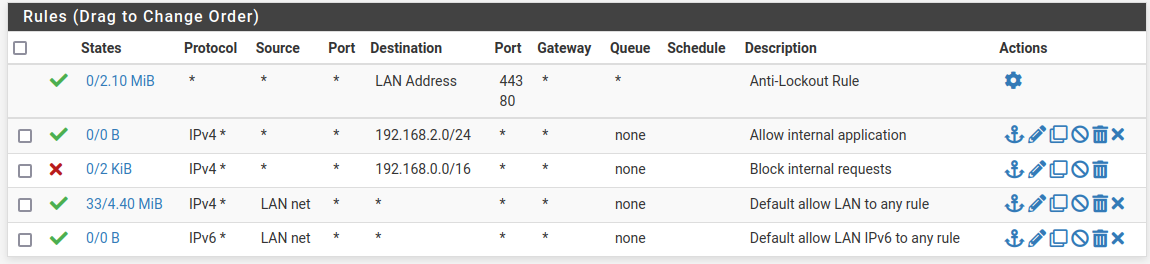
LANcan reach internet, all request to internal other LAN are blocked, except192.168.2.0/24which is what I need because of there is several internal applications.
Problem solved. -
@Dave07186 said in How to authorize only a source from LAN to use internet:
there is several internal applications
You could make that rule more explicit - and only allow to the actual IPs in the 192.168.2/24 network, or even more explicit only to the specific IPs and ports these applications are using..
The problem I see with those rules - but hey its up to you.. Is you do not even all ping to pfsense, which can be problematic in troubleshooting if you can not even ping your gateway to test for connectivity.
And your rules do not allow for local dns, unless your running dns on the 192.168.2 network, or using external dns.. Normally you would allow asking pfsense for dns.
-
I've had this problem... isolating subnets etc...
This is a common issue with firewalls and you can find out how to do this in the documentation...
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/opt-lan.html
It will give you a fully explanation than is possible in the forums.;-)