OpenVPN connection issue
-
@Stef93
I'm new to pfsense, is there an easy way to get the server settings without screenshots of the GUI? -
/var/etc/openvpn/server(your server id)/config.ovpn
example
/var/etc/openvpn/server1/config.ovpn -
server1.ovpn
dev ovpns1
disable-dco
verb 3
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
local 2x.xx.xx.x5
engine devcrypto
tls-server
server 192.168.222.0 255.255.255.0
client-config-dir /var/etc/openvpn/server1/csc
plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'openvpn_server' 1"
lport 1194
management /var/etc/openvpn/server1/sock unix
max-clients 5
push "route 192.168.22.0 255.255.255.0"
duplicate-cn
remote-cert-tls client
capath /var/etc/openvpn/server1/ca
cert /var/etc/openvpn/server1/cert
key /var/etc/openvpn/server1/key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server1/tls-auth 0
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
allow-compression no
persist-remote-ip
float
topology subnet
explicit-exit-notify 1
inactive 300CLIENT.ovpn
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote FQDN_to_WAN 1194 udp4
nobind
verify-x509-name "openvpn_server" name
auth-user-pass
remote-cert-tls server
explicit-exit-notify<ca>
-----BEGIN CERTIFICATE-----
MIID8TCCAtmgAwIBAgIIWHUO2JAZN+wwDQYJKoZIhvcNAQELBQAwVTEUMBIGA1UE
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIEOzCCAyOgAwIBAgIBAzANBgkqhkiG9w0BAQsFADBVMRQwEgYDVQQDEwtpbnRl
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC+XaVPf5oMFoPc
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
5cb31652d73c24ad65db0b111fbb68eb
-----END OpenVPN Static key V1-----
</tls-auth> -
@jonh001 said in OpenVPN connection issue:
push "route 192.168.22.0 255.255.255.0"
duplicate-cnRemove route 192.168.22.0 255.255.255.0 and disable duplicate-cn
Client Specific Overrides there is?
Has the interface been added?
after everything restart opevpnI still advise you to read it, netgate writes excellent instructions and even offers examples with pictures)
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-ra.html -
@Stef93
I did review all the documentation and watched several YouTube videos before posting in the forums.
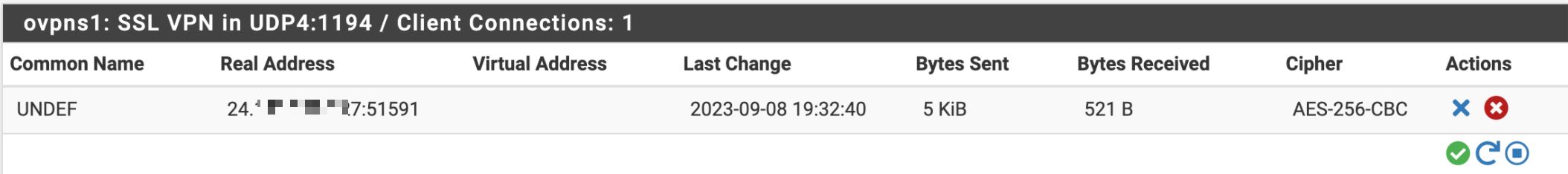
I was under the impression that the wizard would take care of 99% of the configurations for a basic scenario.The interface has been added (I think) - when I look at OpenVPN status, the header shows "ovpns1: SSL VPN in UDP4:1194 / Client Connections: 0" where I believe ovpns1 is the interface name. It also shows up under the Firewall Rules section. However I don't see it specifically listed under Interface Assignments - I only see the usual WAN, LAN and OPT1 (which is my DMZ).
I have since deleted the VPN config and associated rules and rebuilt it - same issue.
-
@jonh001 said in OpenVPN connection issue:
However I don't see it specifically listed under Interface Assignments
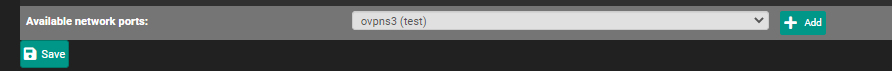
-
I think the OpenVPN interface is created automatically even though it doesn't show up in Interface Assignments as there is a "OpenVPN" item in the Firewall rules.
If I go to Interface Assignments and create a new one, it will show up in the Firewall rules as well.
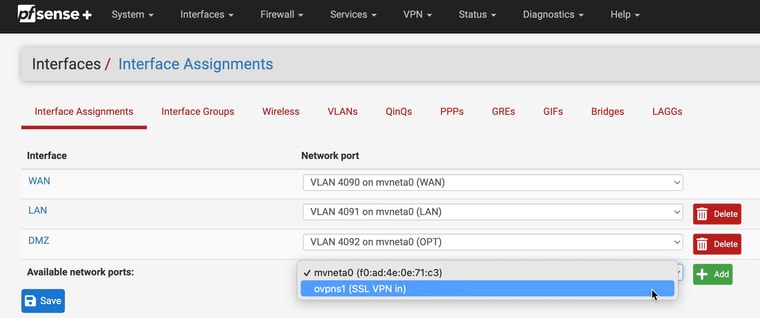
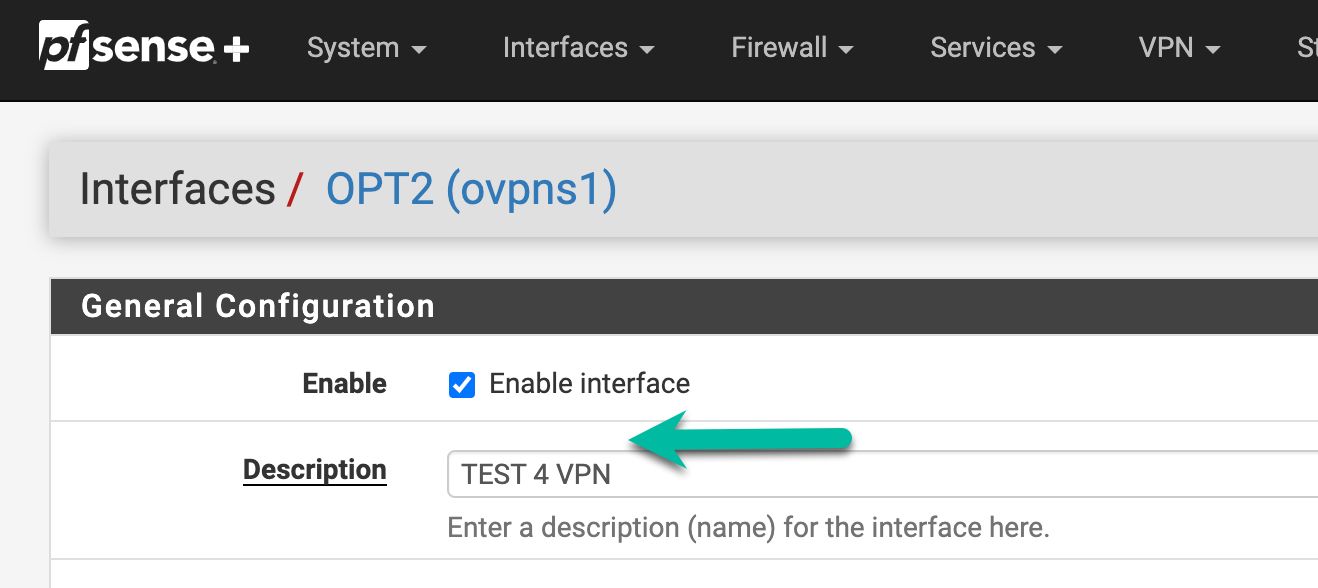
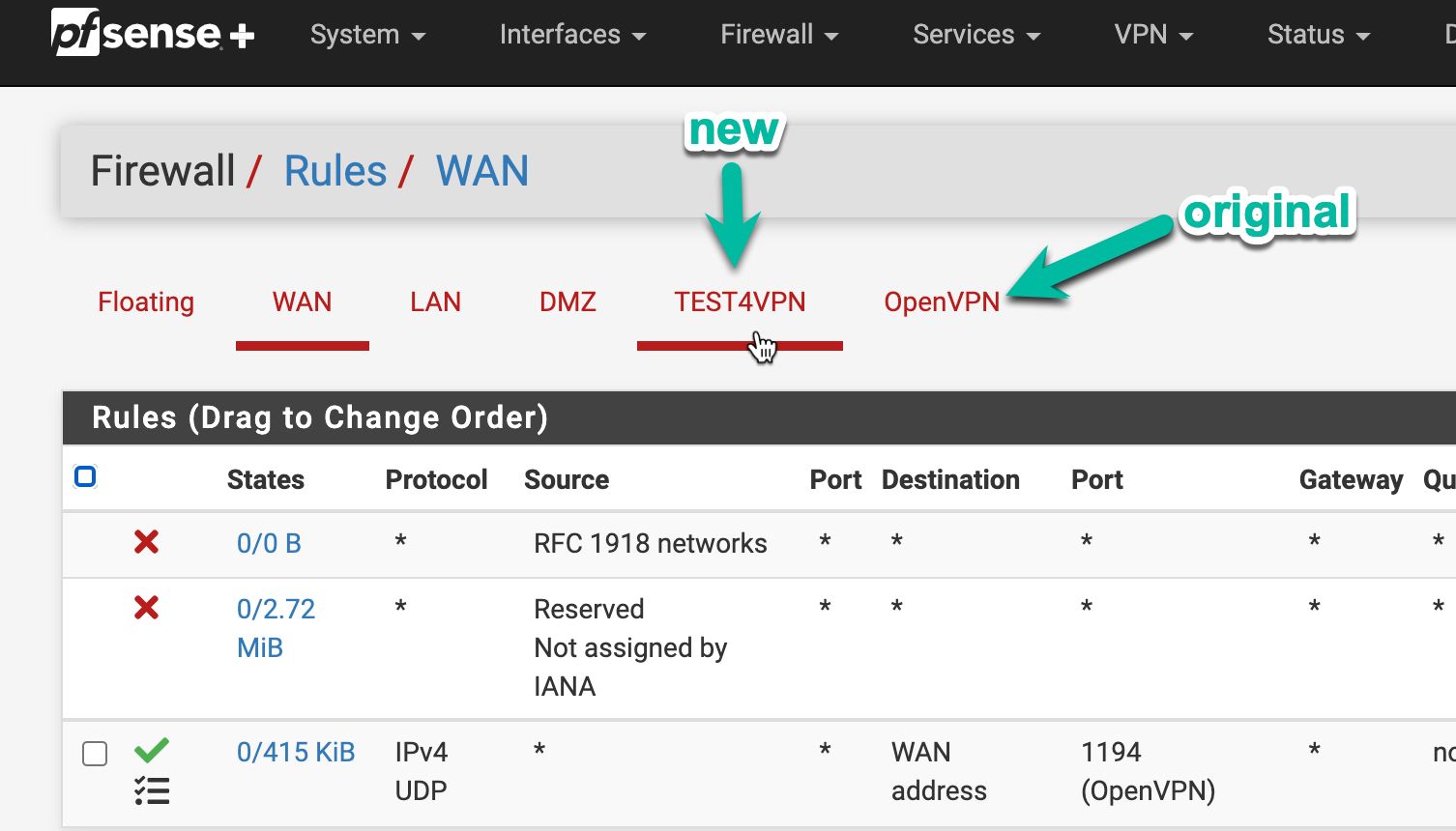
Even if I create a new rule for the new interface, I still have the same issue
-
@jonh001
That's not all, you can add a rule that allows everything on the new interface.
Did you get the user settings through the wizard?
Get it again through Packages - openvpn-client-export, only there it is possible to specify the connection interface you will need -
I'm confused by your client settings, since such settings are only for the mobile application, are you going to use it on the phone?
-
@Stef93
Yes everything was through the wizard. And the client portion was via the client export utility. -
@Stef93
It gets stranger. When I use the client export utility to get the IOS config and then import it into the OpenVPN app on my iPad, it DOES connect, although I still cannot see anything on the permitted subnet. The iPad was just a test, I don't plan on using this via a mobile device.