Selective VPN Routing
-
I feel like I've been struggling with this for too long. So, I turn to the community for help.
I have a Netgate 3100 on version 23.05.1
I am trying to route only certain hosts on my LAN through a specific VPN which I have set up in the router as an OpenVPN client. The VPN Provider is ExpressVPN, and the connection completes successfully. I can ping the interface's IP address from the router and from hosts on my LAN. However, I get no ping response from that interface's gateway. ExpressVPN setup a /32 between themselves and me. I suspect they are just dropping ICMP traffic because I can ping and traceroute through this interface using the '-S' options to those tools (ex. traceroute 8.8.8.8 shows a path through the WAN and traceroute -S <ExpressVPN_IP> 8.8.8.8 shows a path that uses the ExpressVPN connection. I think the VPN itself is functioning normally.
I am trying to configure things such that members of a host alias express_vpn_clients are routed through the ExpressVPN connection. I have configured NAT > Outbound rules such that source traffic from express_vpn_clients that is not destined for rfc1918 networks can be translated through the ExpressVPN connection and I have created a pass rule in LAN with the same source/destination selectors with the gateway of the ExpressVPN connection selected under "Advanced".
Filter logs show that traffic from a host in the express_vpn_clients alias do trigger this rule. However, when I check my apparent IP from any of the hosts in that alias, it's clear they're using the WAN as their gateway (ex. curl icanhazip.com shows my ISP provided IP rather than an IP from the VPN).
I'm stumpped as to what to try next and I'm looking for help.
To complicate matter, I have two other OpenVPN clients set up for two different sites at work. I have LAN rules that hosts NOT in a work_vpn alias with traffic destined any my work subnets should be dropped. I have the Outbound NAT rules for those two VPNs set up just like I've done for the ExpressVPN connection. This allows my home office to connect to my work sites and prevents my families devices from being able to traverse those tunnels. In this case things are working, I think because I have setup "IPv4 Remote network(s)" in those OpenVPN client descriptions, which adds routes in my router for those networks. I can see those routes on the router using "netstat -r".
Thanks in advance for any help!
-
@Hudson-1 Set 8.8.4.4 as your monitoring address for the vpn gateway, is it working? And show your LAN rules.
-
@Bob-Dig Thanks for your reply!
The forum keeps flagging my reply as spam...
Here are my LAN rules:
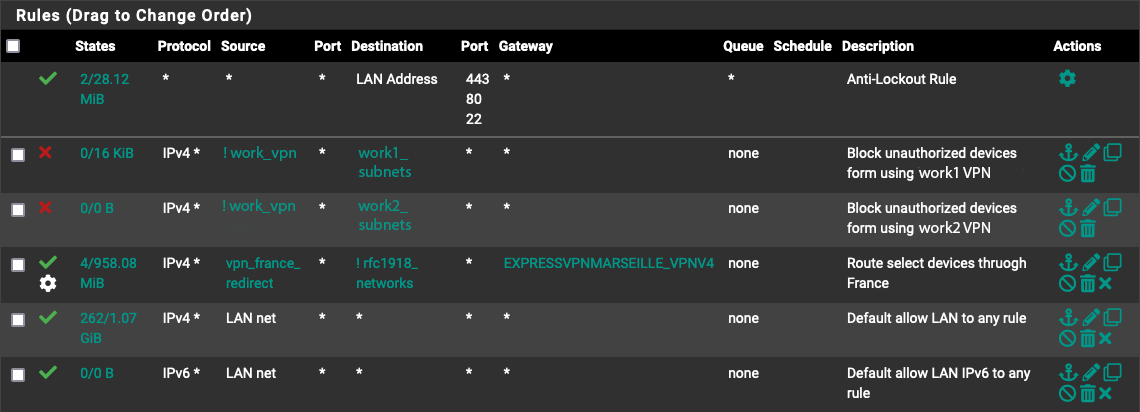
-
I'm not sure what is getting flagged as spam in my reply. Its infuriating. Here is a highly abbreviated version of my original response.
Setting that monitoring IP and checking Status > Gateways shows the VPN gateway as "Pending". Previously, It showed "Offline, packetloss 100%". That didn't concern me because the WAN gateway and one of my work VPN gateways showed the same. The other Work VPN gateway shows "Online"
I had followed the <VPN Vendor>'s guide for setting up their client in pfSense. However, I had to remove 'comp-lzo' from their reccommended "Custom Settings" string in order to establish the connection due to compression warnings/errors.
-
@Hudson-1 said in Selective VPN Routing:
Setting that monitoring IP and checking Status > Gateways shows the VPN gateway as "Pending". Previously, It showed "Offline, packetloss 100%". That didn't concern me because the WAN gateway and one of my work VPN gateways showed the same. The other Work VPN gateway shows "Online"
But it shouldn't if you use googles dns server as monitoring adress. So there is already your problem, your rules look ok.
-
@Bob-Dig Looking further into the Gateway settings. I decided to clear that google address. and check the box for "Disable Gateway Monitoring Action". That worked! My phone which is in the vpn hosts alias now looks like it's coming from the VPN when hitting a "show me my ip and location" site.
-
-
I would like to understand why the gateway looks down. Or pending when using an outside IP. I'd rather get it working properly but at least now my wife can stream the Rugby World cup on the T.V.
Thinking about it, I had trouble initially with my work1 set up too which is what lead me to put the remote subnets into the client configuration. I would prefer to get this set up where instead of blocking unauthorized clients, I'm instead flagging good traffic and routing them out the proper gateway, more like what's happening with this commercially provided VPN. (I think the spam filter doesn't want me mentioning them by name).
-
@Hudson-1 said in Selective VPN Routing:
I have configured NAT > Outbound rules such that source traffic from express_vpn_clients that is not destined for rfc1918 networks can be translated through the ExpressVPN connection
I guess, that was your fault.
This NAT rule only covers connections from the IPs in the alias, but not from pfSense itself. So the ping fails.
So either set the source to any or add an additional rule for pfSense.There is no need to limit the source in this rule. You ca far better control access with filter rules.
Also the RFC1918 alias as destination makes not really much sense. Your firewall rule should care that only non-rfc1918 destinations can go out on this interface.
-
@viragomann I didn't mention it previously but I do have another NAT > Outbound rule to translate from 127.0.0.0/8 to the VPN.
This is the same setup as on the the two work related VPNs as well.
-
@Hudson-1
So I expect, that pings to public IPs are working.
However, 8.8.8.4 is not a good advice. The server doesn't respond to ping requests obviously. Try 8.8.8.8 instead.
