Blocking access to pfSense Web GUI for a set network
-
Hi folks,
I am quite new to pfSense and I'm slowly getting to grips with it. I would like to block access to the web GUI on one of the networks I have setup and cannot find any clear this is how to block access instructions.
I have pfSense installed on a protectli vault (4port).
LAN is my main network and is all hardwired.
OPT1 - is reserved for future install of NAS / Home Lab
OPT2 - is set up with an access point and as IOT network.I have siloed the IOT network so that it cannot establish connection to the LAN and OPT1 networks.
To further increase security I have hidden the SSID of the access point. However once logged on to the OPT2 network access to the web GUI is possible via : 192.168.xxx.1.
I appreciate that in order to gain access to my router someone would need to gain access to the access point or via a compromised IOT device. Then crack the 20 random character password. But I rather not allow anyone to access the router to change settings and gain access to all networks.
How do I go about restricting access to the router from 192.168.xxx.1 while allowing access from 192.168.yyy.1 and 192.168.zzz.1?
Any help gratefully accepted.
Cheers
Jungle -
@Jungle153 Put in a rule on this interface before your rules that allow access to the internet, and below the rules that allow access to pfsense that you want on this network..
So for example..
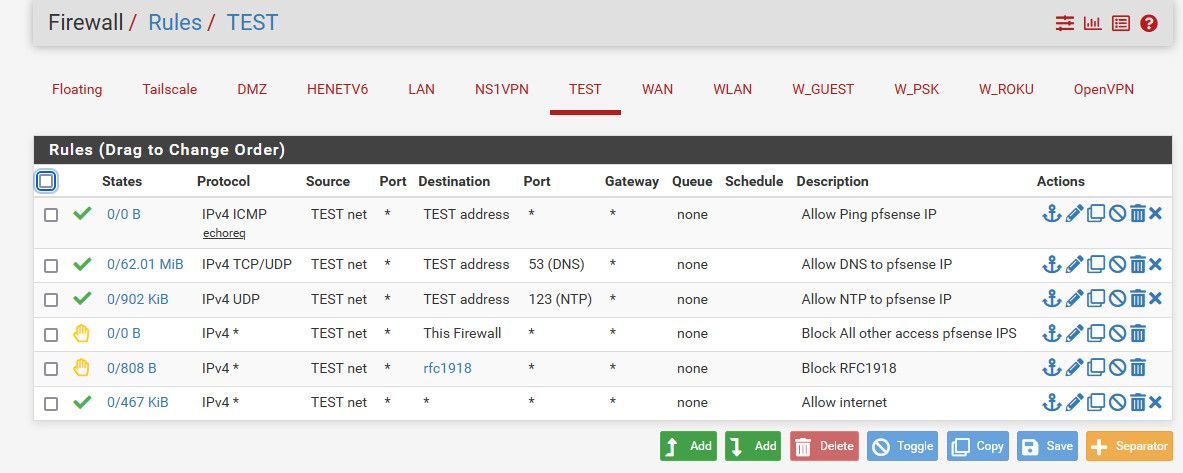
So as rules are evaluated top down, first rule to trigger wins.. You will see I allow icmp (ping), dns and ntp to pfsense IP address on this network.. The next rule would be any and all other access to any IP on "this firewall".. This would be this interfaces IP, any other IPs on any other interface of pfsense.
This would prevent say access to your wan IP, most likely public - that that last rule would allow - which is the internet rule that allows any any.. And also this wan IP might change, so using the built in alias of "this firewall" will handle any IP changes or additional interfaces you add with new IPs, etc.
The next rule that blocks access to an alias rfc1918, is an alias blocks access to any other network I might create - which would be in the rfc1918 space (192.168/16,10/8,172.16/12).. You can use such a rule if you want or not. Now normally using this rule blocking all rfc1918 would work to block access to the gui ports, but your wan IP might be public, and might change - so the "this firewall" rule makes sure no device on this network can access any IP/port on pfsense, other then the ones I explicitly allowed on the rules above.
You could if you want also just use "this firewall" destination and put in the ports your webgui listen on - 80/443 or whatever you have configured. There are a few ways to skin any cat.
-
Thanks for the reply.
It seems that was the ticket. Access to internet works fine and cannot access GUI.
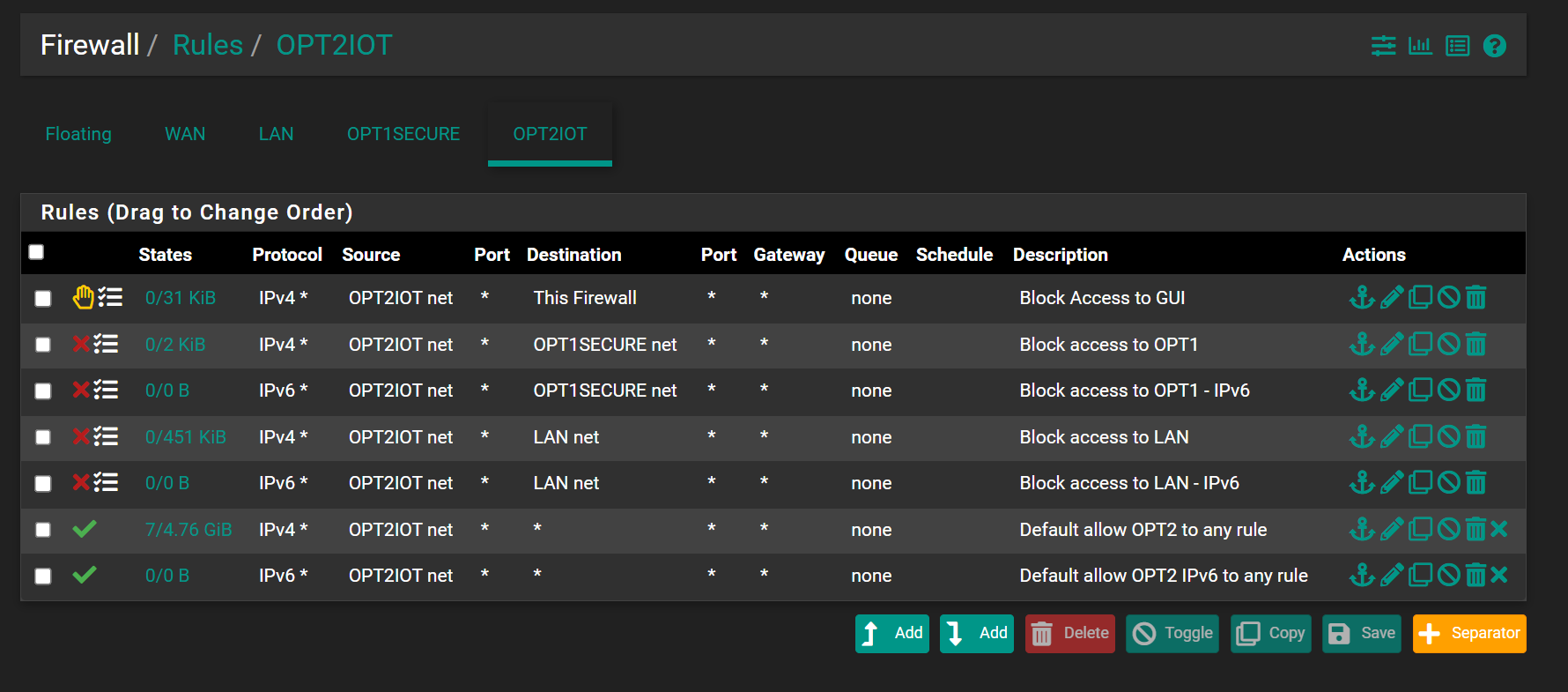
Cheers
Jungle -
@Jungle153 those rules would not allow any access to pfsense IP for dns, ntp - I take it all of these devices are using some external dns and ntp.
Not a fan of blocking ping either, I want to atleast validate connectivity with a simple ping if need be. But hey you do you..
-
Thanks again. Just after I read your reply I realised I had killed the internet when little one said she couldn't stream anything on the ROKU.
I've now added rules for allowing DNS and NTP and also ping.
Thank you for taking the time to explain, its a steep learning curve. I've gone from using an ISP issue router to this in a week and learning fast how to secure my network.
Cheers
Jungle