IP Address format of firewall aliases
-
Hey Guys,
I'm testing ranges of CIDR addresses that I have imported into firewall network aliases.
They have been added onto and not checked for duplicates or sorted.I've noticed that some IP addresses that should be caught by the aliases are not being caught...
I've tried checking openbsd.org for pf guidance but can't find any reference to how to prepare lists of aliases.Are their any hard and fast rules to compile lists or aliases? Deduplicate / Sort?
Thanks.
-
@ASGR71 said in IP Address format of firewall aliases:
I've noticed that some IP addresses that should be caught by the aliases are not being caught...
Example ?
@ASGR71 said in IP Address format of firewall aliases:
openbsd.org for pf
Didn't know that OpenBSD was also using 'pf'.
pfSense is based upon FreeBSD.@ASGR71 said in IP Address format of firewall aliases:
rules to compile lists
I don't understand what you mean by compile.
From what I know :
Do this :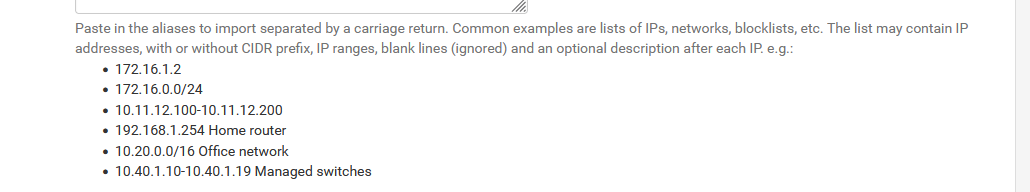
and you'll be fine.
I would not be surprised that the file isn't "checked" for errors, inconsistencies, duplicates etc. -
@Gertjan Thanks Gertjan...
I've been receiving a LOT of traffic from 'certain companies' in a 'certain country' and
I'm compiling (i.e. data scraping) all related CIDR address ranges from ASN data.I've called the file and corresponding firewall alias, for the sakes or argument, BLOCK_CN
that contains all registered CIDR ranges to telecommunications companies but the
firewall logs still show that some addresses within the CIDR range are still getting through!These are the first few lines from ASN4811:
27.109.124.0/22
43.240.126.0/23
43.254.44.0/22
45.115.44.0/22
45.124.124.0/22
59.153.92.0/22
...
and then I copy / paste the next ASN range on to the end of this list to create a long list of addresses
that I copy / paste into Firewall->Alias->Import feature. It's sorted by ASN but not sorted as an
entire list of CIDR addresses. Don't know if pfsense stops searching after a partial match...I believe pfBLOCKERng can do the same thing but I've only got an SG1100 that can't handle
too many applications so imported lists is the way I'm going with for now. You're probably
going to say that pfsense blocks all incoming traffic by default... but I'm using this as a
coding project. I'm in the process of setting up a local http server so that pfsense can digest
the files everyday.NB: I thought I read that pfSense uses a ported openbsd.org firewall called 'pf'.
I've got it on my MacBookAir but it's not fully enabled! Crazy Apple!Thanks.
-
@ASGR71 said in IP Address format of firewall aliases:
within the CIDR range are still getting through!
Like what? What IP and in what cidr do you think it should hit. If your going to create an alias.. Validate that aliases actually populated with what you put in via the table listing under diagnostics.
As to doing this with pfblocker on a sg1100.. Why prob not a good idea to use pfblocker with some crazy amount of dnsbl settings.. Creating some asn based aliases is pretty low resource requirement.