Port forwarding not working properly
-
@Bob-Dig said in Port forwarding not working properly:
@yon-0 Maybe show some screenshots of your rules, gateways etc. at least for one WG interface. What is running on those VPS, Linux?
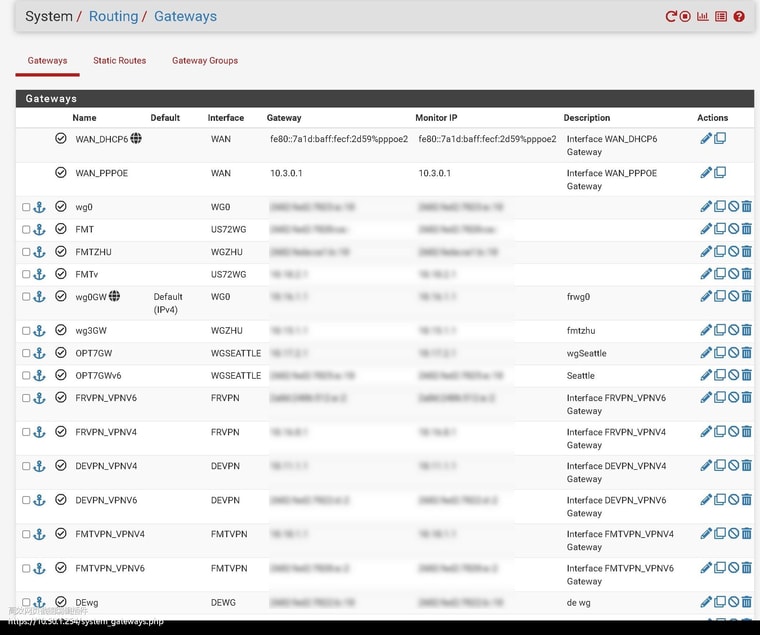
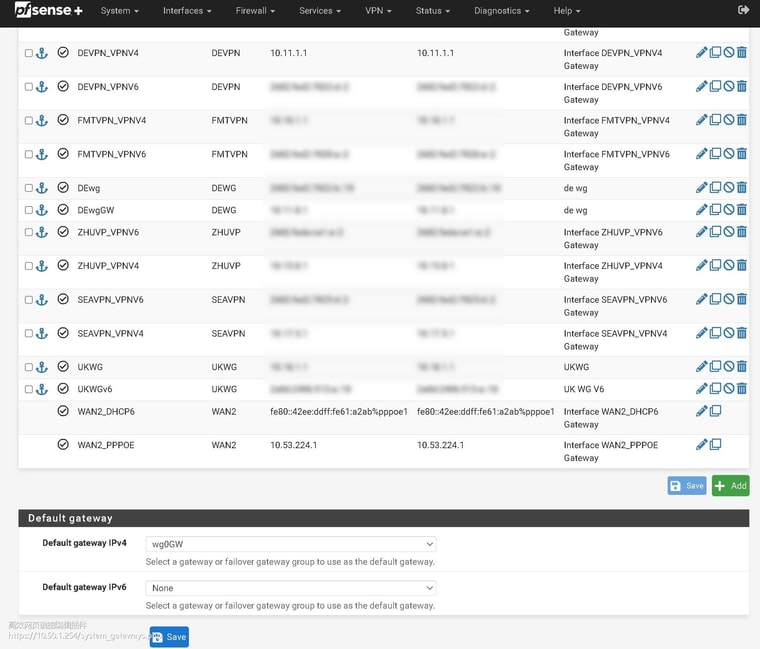
now i have setup Default gateway IPv4 with wg0, so only wg0 can normal work, if i am not setup this, then all wg tunnle port forwarding can't normal work.
-
@stephenw10 said in Port forwarding not working properly:
reply-to
pass in quick on $US72WG reply-to ( tun_wg1 10.10.2.1 ) inet proto tcp from any to 10.50.2.5 port 25 ridentifier 1645607936 flags S/SA keep state label "USER_RULE: NAT smtp" label "id:1645607936" # array key "mwan" does not exist for "http" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: http" # array key "mwan" does not exist for "http" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: http" # array key "mwan" does not exist for "FTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP" # array key "mwan" does not exist for "FTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP" # array key "mwan" does not exist for "DNS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: DNS" # array key "mwan" does not exist for "DNS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: DNS" # array key "mwan" does not exist for "SMTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: SMTP" # array key "mwan" does not exist for "SMTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: SMTP" # array key "mwan" does not exist for "HTTPS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: HTTPS" # array key "mwan" does not exist for "HTTPS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: HTTPS" # array key "mwan" does not exist for "IMAP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAP" # array key "mwan" does not exist for "IMAP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAP" # array key "mwan" does not exist for "IMAPs" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAPs" # array key "mwan" does not exist for "IMAPs" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAPs" # array key "mwan" does not exist for "pop3" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: pop3" # array key "mwan" does not exist for "pop3" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: pop3" # array key "mwan" does not exist for "FTP pass " in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP pass " # array key "mwan" does not exist for "FTP pass" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP pass" # array key "mwan" does not exist for "smtp" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: smtp" # array key "mwan" does not exist for "smtp" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: smtp"I'm not sure which version stopped working. I found it didn't work in version 23.09.01. I think it should work in version 23.05 because I tested it when I set up port forwarding.
-
@yon-0 said in Port forwarding not working properly:
10.10.2.1
Do you see states/traffic on that pass rule?
Do you have pass rules on the WireGuard group interface? That would prevent the reply-to being applied.
-
@stephenw10 said in Port forwarding not working properly:
@yon-0 said in Port forwarding not working properly:
10.10.2.1
Do you see states/traffic on that pass rule?
Do you have pass rules on the WireGuard group interface? That would prevent the reply-to being applied.
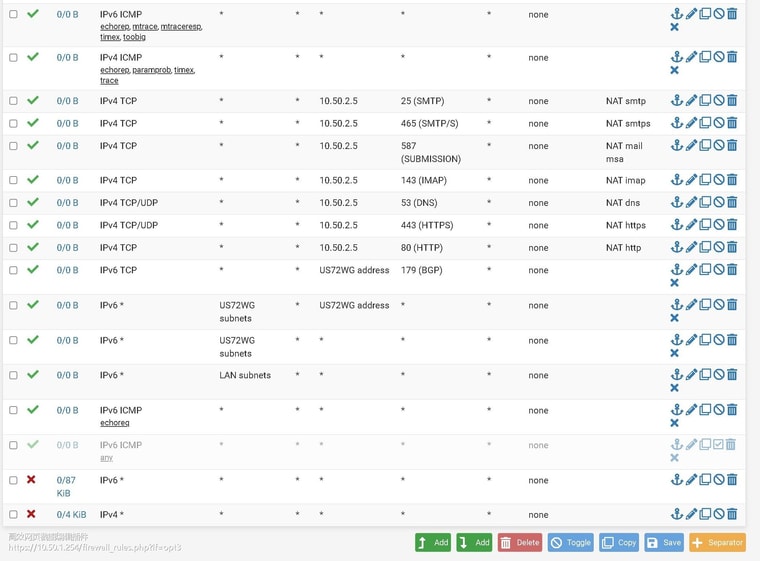
-
@stephenw10 said in Port forwarding not working properly:
Do you see states/traffic on that pass rule?
no, No traffic shows up on wg forwarding port
-
Ok, so no traffic is hitting those rules. Most likely it's being passed on the WG group interface. If that is the case then reply-to would not be applied.
What rules do you have on the WG group?
-
@stephenw10 said in Port forwarding not working properly:
Ok, so no traffic is hitting those rules. Most likely it's being passed on the WG group interface. If that is the case then reply-to would not be applied.
What rules do you have on the WG group?
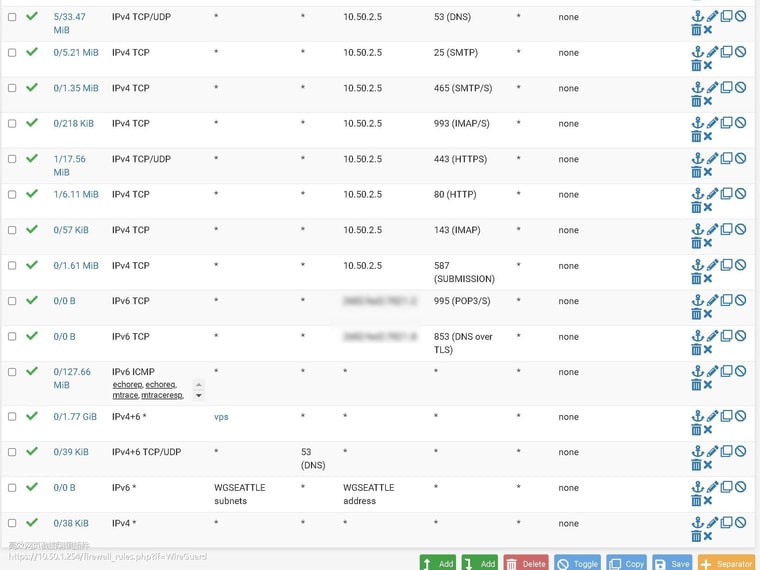
-
because wg0 has setup to pfsense default gateway, so wg0 is normal, other wireguard tunnel can't work.
-
You have to pass that traffic on the assigned interface tabs and not on the Wireguard group tab otherwise reply-to cannot work.
So disable the rules on the group tab.
-
i will try it...
-
i have been deleted all wg group rule, and add rule to each wg . but it still can't work.
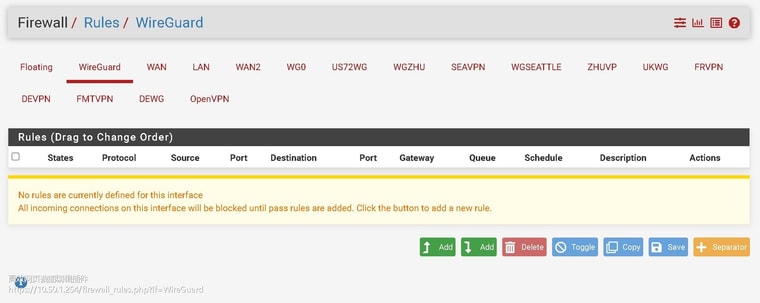
-
Do you see states/traffic on the assigned interface tabs now?
-
no, i can't it.
-
The firewall rules have been delayed for too long. Now I can test a port 25. Let me test the others.
-
I have a question, if I have ipv6 bgp, should ipv6 use group rules or per-interface rules? of cause ipv6 no need port farwarding. Does it affect multiple routing exports?
-
With IPv6 there would usually only be one route, defined by BGP, since there is no NAT. I would not expect there to be any policy based routing.
-
@stephenw10 So what you mean is that you ipv6 only need to set up group firewall rules? Do I understand correctly?
-
That's what I would expect because the system routing table should be correct. Incoming traffic should always come from that route unless you have some route asymmetry somehow.
It's the port forwards (NAT) that allows traffic from a single source IP to arrive via any gateway.