Port forwarding not working properly
-
Bring it here to discuss and see if anyone else has encountered this problem or can understand what I mean?
https://redmine.pfsense.org/issues/14776
when I creat wiregaurd vpn tunnel and setup NAT rule, if Default gateway IPv4 not setup the wiregaurd interface, then NAT will can't work.
tested on pfsense plus 23.09.01
Previous versions of pfsense allowed multiple wireguard interfaces to support NAT forwarding at the same time.
For my purpose, when I have multiple wireguard VPN connections in different regions, I need to forward each wg to pfsense.
and openvpn p2p mode never work for this.
For example I have several wiregaurd p2p tunnels,the wg0 public ip is 15.5.5.5 and the wg1 public ip is 15.8.6.5, I set up these two tunnels LAN NAT port 25 to 10.50.2.6 :25 of the intranet.
If I don't set both WG tunnel interfaces as system default routing gateway, then neither WG tunnel NAT works.Only when I set one of the two tunnels as the system default gateway, the WG tunnel NAT of this default gateway works.
I think it's wrong that the tunnel must be set as the default gateway for NAT to work.
-
@yon-0 said in Port forwarding not working properly:
Only when I set one of the two tunnels as the system default gateway, the WG tunnel NAT of this default gateway works.
You don't set any of them as the default gateway, use your WAN for that. You can NAT as you please with pfSense.
Many privacy-VPN-providers will let you only have one tunnel to them because all the tunnels use the same ip configuration though. -
As jimp said in the bug report what you're describing there is reply-to function not working.
You can confirm that by checking the traffic when NAT is not working. Do you see replies leaving via the default gateway instead of back over the expected wg tunnel?
Where have you passed the incoming traffic? On the Wireguard group interface? It would need to be on the individually assigned interfaces to apply reply-to.
Steve
-
@Bob-Dig i am not buy vpn, i am buy vps . I forwarded the IPv4 of the VPS to pfsense, and pfsense forwarded it to my intranet server.
-
@stephenw10 Before I upgraded pfsense, it had been working normally. The current version causes it to not work unless wg is set as the default gateway.Each wg tunnel is assigned a separate interface, so there must be something wrong now.
In the previous version of Pfsense, I had nearly 6 tunnels in different regions connected to pfsense, and the public IPv4 of each tunnel could be forwarded to my intranet server normally through pfsense.
-
I used to forward each tunnel's public IPv4 to my LAN mail server. Now it is necessary to set the tunnel interface as the system default gateway, so the problem is with pfsense because my previous tunnel configuration has not changed.
-
@yon-0 Maybe show some screenshots of your rules, gateways etc. at least for one WG interface. What is running on those VPS, Linux?
-
What version did you upgrade from where it did work? Is this only failing in 23.09?
Check the ruleset in /tmp/rules.debug. Do the pass rules you have on the WG interfaces have the reply-to tags?
-
@Bob-Dig said in Port forwarding not working properly:
@yon-0 Maybe show some screenshots of your rules, gateways etc. at least for one WG interface. What is running on those VPS, Linux?
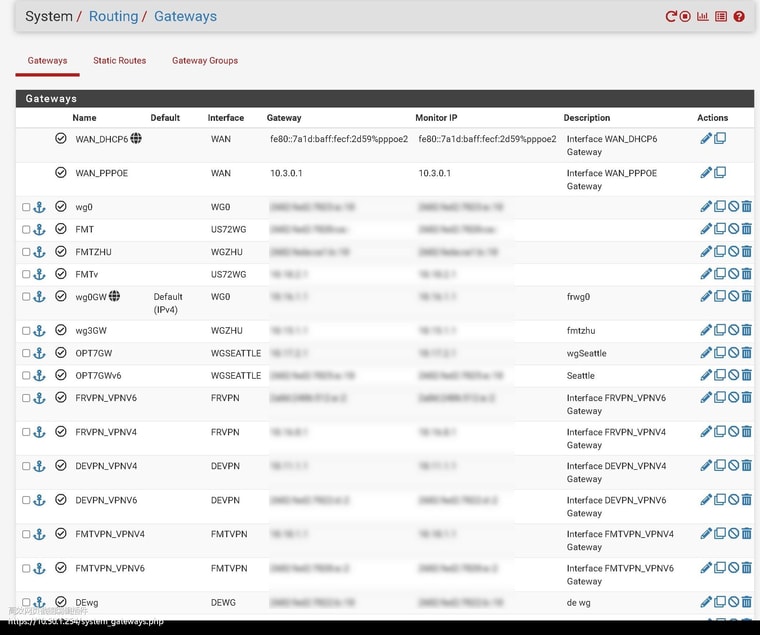
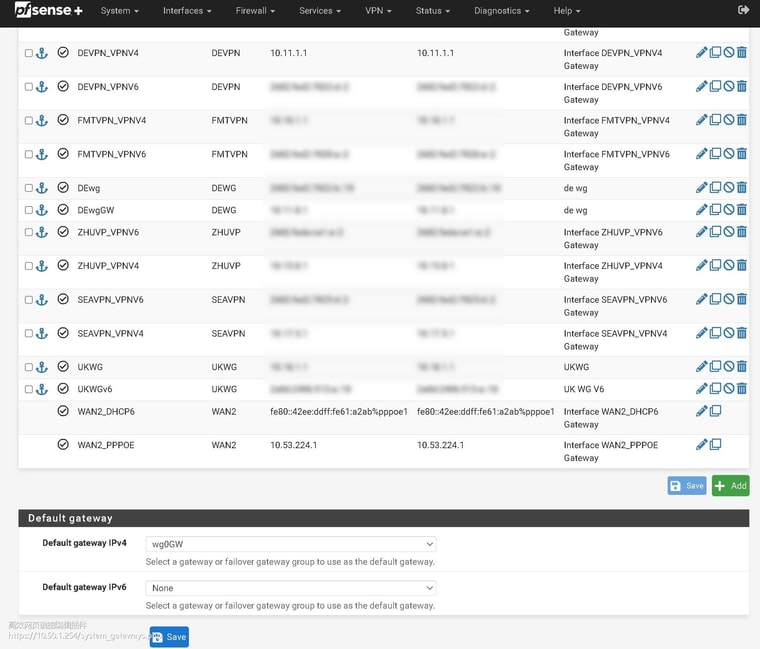
now i have setup Default gateway IPv4 with wg0, so only wg0 can normal work, if i am not setup this, then all wg tunnle port forwarding can't normal work.
-
@stephenw10 said in Port forwarding not working properly:
reply-to
pass in quick on $US72WG reply-to ( tun_wg1 10.10.2.1 ) inet proto tcp from any to 10.50.2.5 port 25 ridentifier 1645607936 flags S/SA keep state label "USER_RULE: NAT smtp" label "id:1645607936" # array key "mwan" does not exist for "http" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: http" # array key "mwan" does not exist for "http" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: http" # array key "mwan" does not exist for "FTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP" # array key "mwan" does not exist for "FTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP" # array key "mwan" does not exist for "DNS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: DNS" # array key "mwan" does not exist for "DNS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: DNS" # array key "mwan" does not exist for "SMTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: SMTP" # array key "mwan" does not exist for "SMTP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: SMTP" # array key "mwan" does not exist for "HTTPS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: HTTPS" # array key "mwan" does not exist for "HTTPS" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: HTTPS" # array key "mwan" does not exist for "IMAP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAP" # array key "mwan" does not exist for "IMAP" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAP" # array key "mwan" does not exist for "IMAPs" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAPs" # array key "mwan" does not exist for "IMAPs" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: IMAPs" # array key "mwan" does not exist for "pop3" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: pop3" # array key "mwan" does not exist for "pop3" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: pop3" # array key "mwan" does not exist for "FTP pass " in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP pass " # array key "mwan" does not exist for "FTP pass" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: FTP pass" # array key "mwan" does not exist for "smtp" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: smtp" # array key "mwan" does not exist for "smtp" in array: {WAN LAN WAN2 WG0 US72WG WGZHU SEAVPN WGSEATTLE ZHUVP UKWG FRVPN DEVPN FMTVPN DEWG OpenVPN WireGuard } label "USER_RULE: smtp"I'm not sure which version stopped working. I found it didn't work in version 23.09.01. I think it should work in version 23.05 because I tested it when I set up port forwarding.
-
@yon-0 said in Port forwarding not working properly:
10.10.2.1
Do you see states/traffic on that pass rule?
Do you have pass rules on the WireGuard group interface? That would prevent the reply-to being applied.
-
@stephenw10 said in Port forwarding not working properly:
@yon-0 said in Port forwarding not working properly:
10.10.2.1
Do you see states/traffic on that pass rule?
Do you have pass rules on the WireGuard group interface? That would prevent the reply-to being applied.
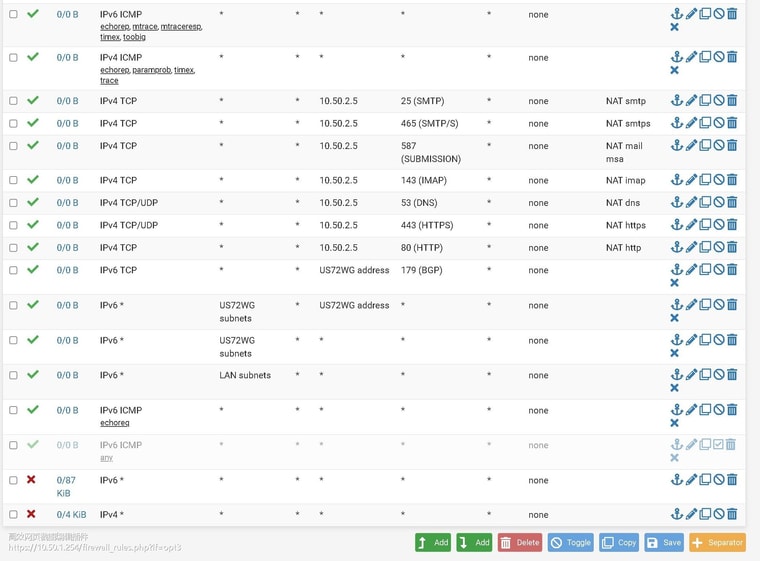
-
@stephenw10 said in Port forwarding not working properly:
Do you see states/traffic on that pass rule?
no, No traffic shows up on wg forwarding port
-
Ok, so no traffic is hitting those rules. Most likely it's being passed on the WG group interface. If that is the case then reply-to would not be applied.
What rules do you have on the WG group?
-
@stephenw10 said in Port forwarding not working properly:
Ok, so no traffic is hitting those rules. Most likely it's being passed on the WG group interface. If that is the case then reply-to would not be applied.
What rules do you have on the WG group?
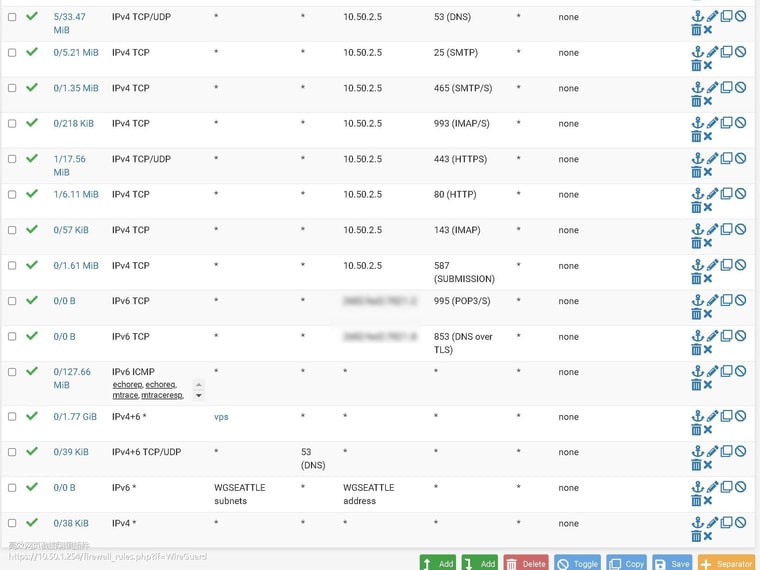
-
because wg0 has setup to pfsense default gateway, so wg0 is normal, other wireguard tunnel can't work.
-
You have to pass that traffic on the assigned interface tabs and not on the Wireguard group tab otherwise reply-to cannot work.
So disable the rules on the group tab.
-
i will try it...
-
i have been deleted all wg group rule, and add rule to each wg . but it still can't work.
-
Do you see states/traffic on the assigned interface tabs now?