Firewall keeping ARP table differently when Netgate-4100 and 2100.
-
Hello Professionals,
We are using SD-WAN devices provided from ISP and those are connected to Netgate-2100 or 4100.
There is VRRP issue, and ISP thinks that firewall is suspicious.Here is architecture of Site-A and Site-B.
Site-A>> VRRP works good.
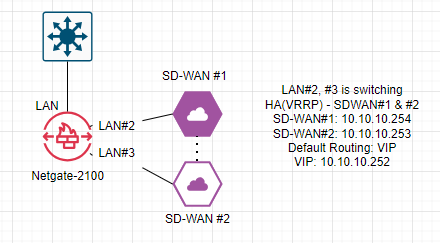
Site-B>> VRRP not working.
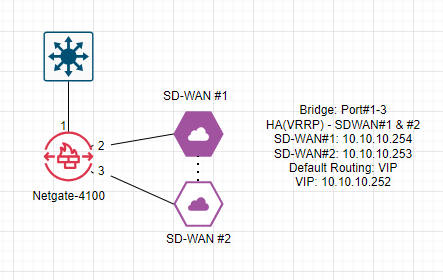
Vendor told me how VRRP running between SD-WAN#1 and #2:
When SD-WAN#1 is dead (Powered off or next hop is down), traffic goes to SD-WAN#2.
VRRP works by the VIP's mac address. Which means,- SD-WAN#1's mac - aa:bb:cc:11:22:33
- SD-WAN#2's mac - 11:33:55:dd:ee:ff
- VIP: SD-WAN#1's mac (aa:bb:cc:11:22:33) by default.
- When SD-WAN#1 down, VIP: SD-WAN#2's mac (11:33:55:dd:ee:ff).
Vendor is seeing this issue cause of my device (Netgate-4100).
Due to Netgate-4100 keeps ARP table for 20minutes by default ARP age time, it does not send packets properly. So when I clear ARP table right away, packets flows to SD-WAN#2.However, Netgate-2100 has same arp_age value but VRRP working fine.
Could it be the reason why I got different result that I configured Netgate-4100 ports to be bridge? If so, why?
Other than that, all configuration is same such as Firewall - Advance, routing tables, ACL rules.I appreciate your comments.
-
@eeebbune
VRRP requires that the interfaces of both nodes are connected via layer 2. But pfSense works on layer 3.
So get a small dumb layer 2 switch and put it in between the ISP boxes and pfSense. On pfSense you have to configure only one WAN Interface.