Captive portal issue
-
In a captive portal, I'm creating 3 different zones with different quota settings. However, users in Zone1 can access Zone2 and Zone3. I want Zone1 users to only access Zone1. The quota settings for the zones are not working; internet usage continues even after the quota is exhausted. How can I resolve these issues?
zone1: localzone -- 192.168.100.1/24
zone2: wifi1zone -- 172.10.10.1/24
zone3: wifi2zone -- 172.10.20.1/24The zones are configured as stated, but users from 'localzone' can still log in to 'wifi1zone' captive portal and access other zones in the same way.
What should happen is that users from "localzone" should only have access to the "localzone" captive portal.I am waiting for your helps in this matter.
-
Hi,
@mra said in Captive portal issue:
zone1: localzone -- 192.168.100.1/24
zone2: wifi1zone -- 172.10.10.1/24
zone3: wifi2zone -- 172.10.20.1/24By default, these 3 interfaces have no firewall rules.
So, nobody can access nothing suing any of these 3.
Then you added firewall rules....@mra said in Captive portal issue:
The quota settings for the zones are not working; internet usage continues even after the quota is exhausted. How can I resolve these issues?
What did you do to enforce quotas ?
What quotas : Amount of Download and Upload Traffic - or time based ?@mra said in Captive portal issue:
but users from 'localzone' can still log in to 'wifi1zone' captive portal
Who do you identify / authenticate users ?
@mra said in Captive portal issue:
What should happen is that users from "localzone" should only have access to the "localzone" captive portal.
Normally, a modern OS will handle a new network as public : il will not use niether share any any local resources.
Modern access points can be put in "AP Isolation" mode : none of the Wifi connected devices can 'see' each other'. But be carefull if you have more then one AP on a portal segment : users from AP1 can 'see' wifi connected users on AP2 (AP1 and AP2 being on the same network). To change this : you'll be needing MAC ( ! ) based firewall rules on each AP ... Or maybe the AP has also user (GUI) setting :for this. -
@Gertjan thank you for replying.
What kind of firewall rule should I write? I need to group the users, otherwise users will always be able to log in to other captive portals.
WiFi will broadcast SSID without a password, and when it automatically redirects to the captive portal, it will be necessary to log in with local users.
My problem is that when connected to wifi1's wifi, the user who needs to log in to wifi2 will also be able to log in to wifi1. In this way, I want to create a user group for wifi1 and connect only to wifi1 captive portal.
-
A possible approach could be to setup 3 (at least 2) RADIUS servers for authentication.
So you can use in each zone a dedicated authentication server (and/or the local database).
Users from other zones cant access.
But this is a very oversized and uncomfortable solution, you need to administrate different authentication servers and need to know, which user is to create at which server.
Anyhow, I do not see any other way using default pfSense configuration.Cant find any menuitem to allow/disallow zone access at a per user/group object.
Regards
-
@mra said in Captive portal issue:
My problem is that when connected to wifi1's wifi, the user who needs to log in to wifi2 will also be able to log in to wifi1. In this way, I want to create a user group for wifi1 and connect only to wifi1 captive portal.
I think I have a solution for you.
No radius needed, just pfSense.Locate Line 263 of the main portal /usr/local/captiveportal/index.php file.
It's an empty line, just before the function$auth_result = captiveportal_authenticate_user($user, $passwd, $clientmac, $clientip, $pipeno, $context)where a user name and password are used to check if a user is authorized.
These are your 'zone' names :
zone1: "localzone"
zone2: "wifi1zone"
zone3: "wifi2zone"Add this single line line :
$user = $cpzone.$user;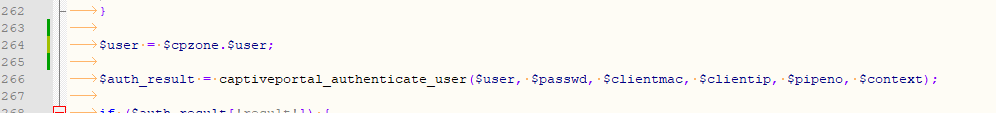
Now, goto the pfSense User manager.
Example :
Let's presume you have a user called "001" that is allowed to visit your "localzone" captive portal.
Make the user info look like this :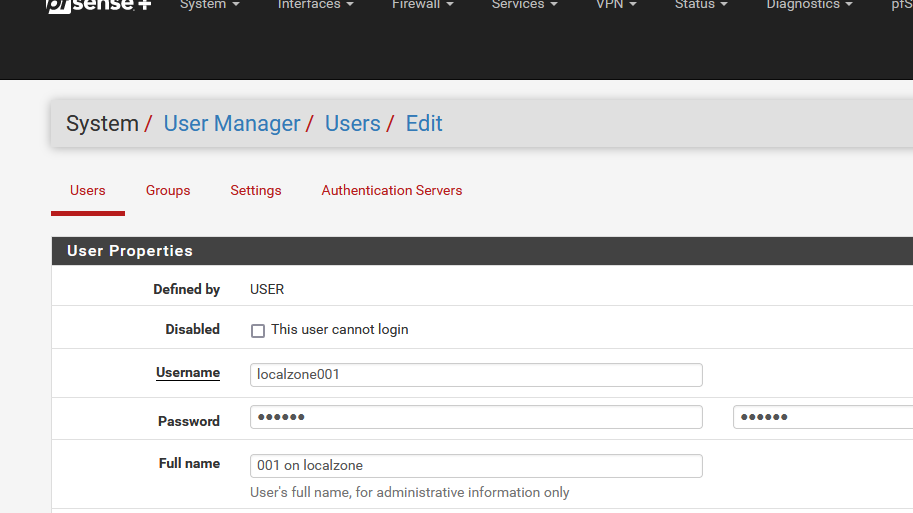
If user "001" also needs to be able to visit the "wifi1zone" portal zone add another user like this :