Cannot get OpenVPN remote access to work
-
Have been working on this on and off for a month. Have even reset and started from scratch - nothing works. Hoping someone can offer some suggestions.
- SG-1100 running latest code (23.05.1-RELEASE)
- WAN connected to cable modem and has a pubic IP
- LAN connected to my home LAN
- OPT1 is my DMZ segment which I'm trying to access remotely
- Used the OpenVPN wizard to create server (created the CA, generated the server and client certs, firewall rules...)
- Used the Client export utility to export a config which I use on another Linux box to try to connect to (over the Internet)
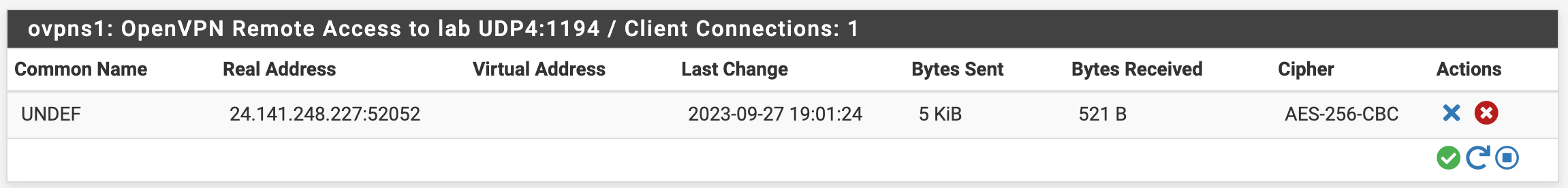
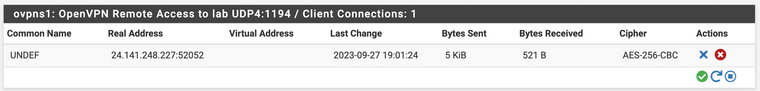
Server sees session come in - but just sits like this, never gets a virtual IP:
Client sees TLS handshake failure:
2023-09-27 19:01:18 OpenVPN 2.5.5 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Jul 14 2022 2023-09-27 19:01:18 library versions: OpenSSL 3.0.2 15 Mar 2022, LZO 2.10 Enter Auth Username: jonh 🔐 Enter Auth Password: ******** 2023-09-27 19:01:24 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 19:01:24 UDPv4 link local: (not bound) 2023-09-27 19:01:24 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 19:02:24 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) 2023-09-27 19:02:24 TLS Error: TLS handshake failed 2023-09-27 19:02:24 SIGUSR1[soft,tls-error] received, process restartingServer config
dev ovpns1 disable-dco verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 24.XXX.XXX.70 tls-server server 192.168.33.0 255.255.255.0 client-config-dir /var/etc/openvpn/server1/csc verify-client-cert none username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'lab.XXXXXXXX.net' 1" lport 1194 management /var/etc/openvpn/server1/sock unix max-clients 10 push "route 192.168.22.0 255.255.255.0" duplicate-cn capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC allow-compression no persist-remote-ip float topology subnet explicit-exit-notify 1 inactive 300CLIENT CONFIG
dev tun persist-tun persist-key data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC auth SHA256 tls-client client resolv-retry infinite remote lab.XXXXXXXX.net 1194 udp4 nobind auth-user-pass remote-cert-tls server explicit-exit-notify <ca> -----BEGIN CERTIFICATE----- MIIEHTCCAwWgAwIBAgIIF8+iABPtBtEwDQYJKoZIhvcNAQELBQAwYzEUMBIGA1UE ..... m3L48hAotFGsoVbCul1fDuctEvee6+2E4gT818rP3DT4GZtisZIK9xqTBkTMUaRf TA== -----END CERTIFICATE----- </ca> setenv CLIENT_CERT 0 key-direction 1 <tls-auth> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- 0a142924fc4f395723509c0b034ce3d3 ..... cba5c256f1be873a4e2a3f213d159a6b -----END OpenVPN Static key V1----- </tls-auth>openvpn client command with verbosity
2023-09-27 22:38:19 us=294029 library versions: OpenSSL 3.0.2 15 Mar 2022, LZO 2.10 Enter Auth Username: jonh 🔐 Enter Auth Password: ******** 2023-09-27 22:38:27 us=451423 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:38:27 us=451513 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:38:27 us=451680 Control Channel MTU parms [ L:1621 D:1172 EF:78 EB:0 ET:0 EL:3 ] 2023-09-27 22:38:27 us=514450 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] 2023-09-27 22:38:27 us=514587 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client' 2023-09-27 22:38:27 us=514614 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-server' 2023-09-27 22:38:27 us=514640 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:38:27 us=514687 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-09-27 22:38:27 us=514724 UDPv4 link local: (not bound) 2023-09-27 22:38:27 us=514746 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:38:27 us=514865 UDPv4 WRITE [54] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 pid=[ #1 ] [ ] pid=0 DATA len=0 2023-09-27 22:38:27 us=536331 UDPv4 READ [66] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 pid=[ #1 ] [ 0 ] pid=0 DATA len=0 2023-09-27 22:38:27 us=536461 TLS: Initial packet from [AF_INET]24.XXX.XXX.70:1194, sid=02b91245 da09003a 2023-09-27 22:38:27 us=536559 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #2 ] [ 0 ] 2023-09-27 22:38:27 us=536723 UDPv4 WRITE [335] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ ] pid=1 DATA len=281 2023-09-27 22:38:27 us=578143 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #2 ] [ 1 ] pid=1 DATA len=1156 2023-09-27 22:38:27 us=578748 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #4 ] [ 1 ] 2023-09-27 22:38:27 us=579200 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ 1 ] pid=2 DATA len=1156 2023-09-27 22:38:27 us=579300 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #5 ] [ 2 ] 2023-09-27 22:38:27 us=580235 UDPv4 READ [566] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #4 ] [ 1 ] pid=3 DATA len=500 2023-09-27 22:38:27 us=581796 VERIFY OK: depth=1, CN=internal-ca, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:38:27 us=582006 VERIFY KU OK 2023-09-27 22:38:27 us=582051 Validating certificate extended key usage 2023-09-27 22:38:27 us=582069 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2023-09-27 22:38:27 us=582084 VERIFY EKU OK 2023-09-27 22:38:27 us=582099 VERIFY OK: depth=0, CN=lab.XXXXXXXX.net, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:38:27 us=582328 UDPv4 WRITE [632] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #6 ] [ 3 ] pid=2 DATA len=566 2023-09-27 22:38:29 us=667242 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #7 ] [ ] pid=2 DATA len=566 2023-09-27 22:38:29 us=800671 UDPv4 READ [566] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #5 ] [ 1 ] pid=3 DATA len=500 2023-09-27 22:38:29 us=800828 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #8 ] [ 3 ] 2023-09-27 22:38:33 us=970050 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #9 ] [ ] pid=2 DATA len=566 2023-09-27 22:38:41 us=922228 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #10 ] [ ] pid=2 DATA len=566 2023-09-27 22:38:57 us=948437 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #11 ] [ ] pid=2 DATA len=566 2023-09-27 22:39:27 us=999697 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) 2023-09-27 22:39:27 us=999755 TLS Error: TLS handshake failed 2023-09-27 22:39:27 us=999862 TCP/UDP: Closing socket 2023-09-27 22:39:27 us=999909 SIGUSR1[soft,tls-error] received, process restarting 2023-09-27 22:39:27 us=999938 Restart pause, 5 second(s) 2023-09-27 22:39:33 us=210 Re-using SSL/TLS context 2023-09-27 22:39:33 us=345 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:39:33 us=365 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:39:33 us=429 Control Channel MTU parms [ L:1621 D:1172 EF:78 EB:0 ET:0 EL:3 ] 2023-09-27 22:39:33 us=30494 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] 2023-09-27 22:39:33 us=30567 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client' 2023-09-27 22:39:33 us=30579 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-server' 2023-09-27 22:39:33 us=30591 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:39:33 us=30623 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-09-27 22:39:33 us=30633 UDPv4 link local: (not bound) 2023-09-27 22:39:33 us=30641 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:39:33 us=30683 UDPv4 WRITE [54] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 pid=[ #1 ] [ ] pid=0 DATA len=0 2023-09-27 22:39:33 us=54084 UDPv4 READ [66] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 pid=[ #1 ] [ 0 ] pid=0 DATA len=0 2023-09-27 22:39:33 us=54140 TLS: Initial packet from [AF_INET]24.XXX.XXX.70:1194, sid=ac9a5e5b 81a9271b 2023-09-27 22:39:33 us=54199 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #2 ] [ 0 ] 2023-09-27 22:39:33 us=54325 UDPv4 WRITE [335] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ ] pid=1 DATA len=281 2023-09-27 22:39:33 us=94234 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #2 ] [ 1 ] pid=1 DATA len=1156 2023-09-27 22:39:33 us=94557 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #4 ] [ 1 ] 2023-09-27 22:39:33 us=95284 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ 1 ] pid=2 DATA len=1156 2023-09-27 22:39:33 us=95334 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #5 ] [ 2 ] 2023-09-27 22:39:35 us=544016 UDPv4 READ [566] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #5 ] [ 1 ] pid=3 DATA len=500 2023-09-27 22:39:35 us=546234 VERIFY OK: depth=1, CN=internal-ca, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:39:35 us=546400 VERIFY KU OK 2023-09-27 22:39:35 us=546417 Validating certificate extended key usage 2023-09-27 22:39:35 us=546427 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2023-09-27 22:39:35 us=546436 VERIFY EKU OK 2023-09-27 22:39:35 us=546445 VERIFY OK: depth=0, CN=lab.XXXXXXXX.net, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:39:35 us=546720 UDPv4 WRITE [632] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #6 ] [ 3 ] pid=2 DATA len=566 2023-09-27 22:39:37 us=965456 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #7 ] [ ] pid=2 DATA len=566 2023-09-27 22:39:41 us=594109 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #8 ] [ ] pid=2 DATA len=566 2023-09-27 22:39:49 us=825620 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #9 ] [ ] pid=2 DATA len=566 2023-09-27 22:40:05 us=231987 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #10 ] [ ] pid=2 DATA len=566 2023-09-27 22:40:33 us=845090 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) 2023-09-27 22:40:33 us=845131 TLS Error: TLS handshake failed 2023-09-27 22:40:33 us=845238 TCP/UDP: Closing socket 2023-09-27 22:40:33 us=845270 SIGUSR1[soft,tls-error] received, process restarting 2023-09-27 22:40:33 us=845288 Restart pause, 5 second(s) 2023-09-27 22:40:38 us=845749 Re-using SSL/TLS context 2023-09-27 22:40:38 us=845978 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:40:38 us=846039 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-27 22:40:38 us=846137 Control Channel MTU parms [ L:1621 D:1172 EF:78 EB:0 ET:0 EL:3 ] 2023-09-27 22:40:39 us=104110 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] 2023-09-27 22:40:39 us=104196 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client' 2023-09-27 22:40:39 us=104207 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-server' 2023-09-27 22:40:39 us=104220 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:40:39 us=104277 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-09-27 22:40:39 us=104372 UDPv4 link local: (not bound) 2023-09-27 22:40:39 us=104399 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-27 22:40:39 us=104503 UDPv4 WRITE [54] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 pid=[ #1 ] [ ] pid=0 DATA len=0 2023-09-27 22:40:39 us=129503 UDPv4 READ [66] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 pid=[ #1 ] [ 0 ] pid=0 DATA len=0 2023-09-27 22:40:39 us=129576 TLS: Initial packet from [AF_INET]24.XXX.XXX.70:1194, sid=df50a0e7 dbfb844e 2023-09-27 22:40:39 us=129633 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #2 ] [ 0 ] 2023-09-27 22:40:39 us=129738 UDPv4 WRITE [335] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ ] pid=1 DATA len=281 2023-09-27 22:40:39 us=175035 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #2 ] [ 1 ] pid=1 DATA len=1156 2023-09-27 22:40:39 us=175327 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #4 ] [ 1 ] 2023-09-27 22:40:39 us=176114 UDPv4 READ [1222] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #3 ] [ 1 ] pid=2 DATA len=1156 2023-09-27 22:40:39 us=176185 UDPv4 WRITE [62] to [AF_INET]24.XXX.XXX.70:1194: P_ACK_V1 kid=0 pid=[ #5 ] [ 2 ] 2023-09-27 22:40:41 us=515862 UDPv4 READ [566] from [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #5 ] [ 1 ] pid=3 DATA len=500 2023-09-27 22:40:41 us=517818 VERIFY OK: depth=1, CN=internal-ca, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:40:41 us=518054 VERIFY KU OK 2023-09-27 22:40:41 us=518082 Validating certificate extended key usage 2023-09-27 22:40:41 us=518091 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2023-09-27 22:40:41 us=518099 VERIFY EKU OK 2023-09-27 22:40:41 us=518114 VERIFY OK: depth=0, CN=lab.XXXXXXXX.net, C=CA, ST=ON, L=Oakville, O=XXXXXXXX, OU=lab 2023-09-27 22:40:41 us=518345 UDPv4 WRITE [632] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #6 ] [ 3 ] pid=2 DATA len=566 2023-09-27 22:40:43 us=763172 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #7 ] [ ] pid=2 DATA len=566 2023-09-27 22:40:47 us=130865 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #8 ] [ ] pid=2 DATA len=566 2023-09-27 22:40:55 us=372922 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #9 ] [ ] pid=2 DATA len=566 2023-09-27 22:41:11 us=47440 UDPv4 WRITE [620] to [AF_INET]24.XXX.XXX.70:1194: P_CONTROL_V1 kid=0 pid=[ #10 ] [ ] pid=2 DATA len=566 ^C2023-09-27 22:41:24 us=953199 event_wait : Interrupted system call (code=4) -
@jonh001
What do you see in the server log with verb level 4? -
verb level 4
2023-09-28 09:11:30 us=845423 Current Parameter Settings: 2023-09-28 09:11:30 us=845490 config = 'nvb-UDP4-1194-config.ovpn' 2023-09-28 09:11:30 us=845499 mode = 0 2023-09-28 09:11:30 us=845505 persist_config = DISABLED 2023-09-28 09:11:30 us=845511 persist_mode = 1 2023-09-28 09:11:30 us=845517 show_ciphers = DISABLED 2023-09-28 09:11:30 us=845522 show_digests = DISABLED 2023-09-28 09:11:30 us=845528 show_engines = DISABLED 2023-09-28 09:11:30 us=845533 genkey = DISABLED 2023-09-28 09:11:30 us=845539 genkey_filename = '[UNDEF]' 2023-09-28 09:11:30 us=845544 key_pass_file = '[UNDEF]' 2023-09-28 09:11:30 us=845550 show_tls_ciphers = DISABLED 2023-09-28 09:11:30 us=845555 connect_retry_max = 0 2023-09-28 09:11:30 us=845561 Connection profiles [0]: 2023-09-28 09:11:30 us=845567 proto = udp4 2023-09-28 09:11:30 us=845572 local = '[UNDEF]' 2023-09-28 09:11:30 us=845578 local_port = '[UNDEF]' 2023-09-28 09:11:30 us=845583 remote = 'lab.XXXXXXXX.net' 2023-09-28 09:11:30 us=845589 remote_port = '1194' 2023-09-28 09:11:30 us=845594 remote_float = DISABLED 2023-09-28 09:11:30 us=845600 bind_defined = DISABLED 2023-09-28 09:11:30 us=845605 bind_local = DISABLED 2023-09-28 09:11:30 us=845611 bind_ipv6_only = DISABLED 2023-09-28 09:11:30 us=845616 connect_retry_seconds = 5 2023-09-28 09:11:30 us=845622 connect_timeout = 120 2023-09-28 09:11:30 us=845628 socks_proxy_server = '[UNDEF]' 2023-09-28 09:11:30 us=845634 socks_proxy_port = '[UNDEF]' 2023-09-28 09:11:30 us=845639 tun_mtu = 1500 2023-09-28 09:11:30 us=845645 tun_mtu_defined = ENABLED 2023-09-28 09:11:30 us=845651 link_mtu = 1500 2023-09-28 09:11:30 us=845656 link_mtu_defined = DISABLED 2023-09-28 09:11:30 us=845662 tun_mtu_extra = 0 2023-09-28 09:11:30 us=845667 tun_mtu_extra_defined = DISABLED 2023-09-28 09:11:30 us=845673 mtu_discover_type = -1 2023-09-28 09:11:30 us=845679 fragment = 0 2023-09-28 09:11:30 us=845684 mssfix = 1450 2023-09-28 09:11:30 us=845690 explicit_exit_notification = 1 2023-09-28 09:11:30 us=845695 tls_auth_file = '[INLINE]' 2023-09-28 09:11:30 us=845701 key_direction = 1 2023-09-28 09:11:30 us=845706 tls_crypt_file = '[UNDEF]' 2023-09-28 09:11:30 us=845712 tls_crypt_v2_file = '[UNDEF]' 2023-09-28 09:11:30 us=845718 Connection profiles END 2023-09-28 09:11:30 us=845723 remote_random = DISABLED 2023-09-28 09:11:30 us=845729 ipchange = '[UNDEF]' 2023-09-28 09:11:30 us=845734 dev = 'tun' 2023-09-28 09:11:30 us=845740 dev_type = '[UNDEF]' 2023-09-28 09:11:30 us=845745 dev_node = '[UNDEF]' 2023-09-28 09:11:30 us=845751 lladdr = '[UNDEF]' 2023-09-28 09:11:30 us=845756 topology = 1 2023-09-28 09:11:30 us=845762 ifconfig_local = '[UNDEF]' 2023-09-28 09:11:30 us=845767 ifconfig_remote_netmask = '[UNDEF]' 2023-09-28 09:11:30 us=845773 ifconfig_noexec = DISABLED 2023-09-28 09:11:30 us=845779 ifconfig_nowarn = DISABLED 2023-09-28 09:11:30 us=845784 ifconfig_ipv6_local = '[UNDEF]' 2023-09-28 09:11:30 us=845790 ifconfig_ipv6_netbits = 0 2023-09-28 09:11:30 us=845795 ifconfig_ipv6_remote = '[UNDEF]' 2023-09-28 09:11:30 us=845801 shaper = 0 2023-09-28 09:11:30 us=845807 mtu_test = 0 2023-09-28 09:11:30 us=845812 mlock = DISABLED 2023-09-28 09:11:30 us=845818 keepalive_ping = 0 2023-09-28 09:11:30 us=845823 keepalive_timeout = 0 2023-09-28 09:11:30 us=845829 inactivity_timeout = 0 2023-09-28 09:11:30 us=845834 ping_send_timeout = 0 2023-09-28 09:11:30 us=845840 ping_rec_timeout = 0 2023-09-28 09:11:30 us=845845 ping_rec_timeout_action = 0 2023-09-28 09:11:30 us=845851 ping_timer_remote = DISABLED 2023-09-28 09:11:30 us=845856 remap_sigusr1 = 0 2023-09-28 09:11:30 us=845862 persist_tun = ENABLED 2023-09-28 09:11:30 us=845868 persist_local_ip = DISABLED 2023-09-28 09:11:30 us=845873 persist_remote_ip = DISABLED 2023-09-28 09:11:30 us=845879 persist_key = ENABLED 2023-09-28 09:11:30 us=845884 passtos = DISABLED 2023-09-28 09:11:30 us=845890 resolve_retry_seconds = 1000000000 2023-09-28 09:11:30 us=845895 resolve_in_advance = DISABLED 2023-09-28 09:11:30 us=845901 username = '[UNDEF]' 2023-09-28 09:11:30 us=845906 groupname = '[UNDEF]' 2023-09-28 09:11:30 us=845912 chroot_dir = '[UNDEF]' 2023-09-28 09:11:30 us=845918 cd_dir = '[UNDEF]' 2023-09-28 09:11:30 us=845923 writepid = '[UNDEF]' 2023-09-28 09:11:30 us=845929 up_script = '[UNDEF]' 2023-09-28 09:11:30 us=845934 down_script = '[UNDEF]' 2023-09-28 09:11:30 us=845940 down_pre = DISABLED 2023-09-28 09:11:30 us=845945 up_restart = DISABLED 2023-09-28 09:11:30 us=845950 up_delay = DISABLED 2023-09-28 09:11:30 us=845956 daemon = DISABLED 2023-09-28 09:11:30 us=845962 inetd = 0 2023-09-28 09:11:30 us=845967 log = DISABLED 2023-09-28 09:11:30 us=845973 suppress_timestamps = DISABLED 2023-09-28 09:11:30 us=845978 machine_readable_output = DISABLED 2023-09-28 09:11:30 us=845984 nice = 0 2023-09-28 09:11:30 us=845989 verbosity = 4 2023-09-28 09:11:30 us=845995 mute = 0 2023-09-28 09:11:30 us=846000 gremlin = 0 2023-09-28 09:11:30 us=846006 status_file = '[UNDEF]' 2023-09-28 09:11:30 us=846011 status_file_version = 1 2023-09-28 09:11:30 us=846017 status_file_update_freq = 60 2023-09-28 09:11:30 us=846023 occ = ENABLED 2023-09-28 09:11:30 us=846028 rcvbuf = 0 2023-09-28 09:11:30 us=846034 sndbuf = 0 2023-09-28 09:11:30 us=846039 mark = 0 2023-09-28 09:11:30 us=846045 sockflags = 0 2023-09-28 09:11:30 us=846051 fast_io = DISABLED 2023-09-28 09:11:30 us=846056 comp.alg = 0 2023-09-28 09:11:30 us=846062 comp.flags = 0 2023-09-28 09:11:30 us=846067 route_script = '[UNDEF]' 2023-09-28 09:11:30 us=846074 route_default_gateway = '[UNDEF]' 2023-09-28 09:11:30 us=846079 route_default_metric = 0 2023-09-28 09:11:30 us=846085 route_noexec = DISABLED 2023-09-28 09:11:30 us=846090 route_delay = 0 2023-09-28 09:11:30 us=846096 route_delay_window = 30 2023-09-28 09:11:30 us=846102 route_delay_defined = DISABLED 2023-09-28 09:11:30 us=846107 route_nopull = DISABLED 2023-09-28 09:11:30 us=846113 route_gateway_via_dhcp = DISABLED 2023-09-28 09:11:30 us=846119 allow_pull_fqdn = DISABLED 2023-09-28 09:11:30 us=846124 management_addr = '[UNDEF]' 2023-09-28 09:11:30 us=846130 management_port = '[UNDEF]' 2023-09-28 09:11:30 us=846135 management_user_pass = '[UNDEF]' 2023-09-28 09:11:30 us=846141 management_log_history_cache = 250 2023-09-28 09:11:30 us=846147 management_echo_buffer_size = 100 2023-09-28 09:11:30 us=846153 management_write_peer_info_file = '[UNDEF]' 2023-09-28 09:11:30 us=846159 management_client_user = '[UNDEF]' 2023-09-28 09:11:30 us=846164 management_client_group = '[UNDEF]' 2023-09-28 09:11:30 us=846170 management_flags = 0 2023-09-28 09:11:30 us=846176 shared_secret_file = '[UNDEF]' 2023-09-28 09:11:30 us=846181 key_direction = 1 2023-09-28 09:11:30 us=846187 ciphername = 'AES-256-CBC' 2023-09-28 09:11:30 us=846193 ncp_enabled = ENABLED 2023-09-28 09:11:30 us=846199 ncp_ciphers = 'AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC' 2023-09-28 09:11:30 us=846205 authname = 'SHA256' 2023-09-28 09:11:30 us=846210 prng_hash = 'SHA1' 2023-09-28 09:11:30 us=846216 prng_nonce_secret_len = 16 2023-09-28 09:11:30 us=846222 keysize = 0 2023-09-28 09:11:30 us=846227 engine = DISABLED 2023-09-28 09:11:30 us=846233 replay = ENABLED 2023-09-28 09:11:30 us=846239 mute_replay_warnings = DISABLED 2023-09-28 09:11:30 us=846244 replay_window = 64 2023-09-28 09:11:30 us=846250 replay_time = 15 2023-09-28 09:11:30 us=846256 packet_id_file = '[UNDEF]' 2023-09-28 09:11:30 us=846262 test_crypto = DISABLED 2023-09-28 09:11:30 us=846267 tls_server = DISABLED 2023-09-28 09:11:30 us=846273 tls_client = ENABLED 2023-09-28 09:11:30 us=846315 ca_file = '[INLINE]' 2023-09-28 09:11:30 us=846321 ca_path = '[UNDEF]' 2023-09-28 09:11:30 us=846327 dh_file = '[UNDEF]' 2023-09-28 09:11:30 us=846333 cert_file = '[UNDEF]' 2023-09-28 09:11:30 us=846339 extra_certs_file = '[UNDEF]' 2023-09-28 09:11:30 us=846353 priv_key_file = '[UNDEF]' 2023-09-28 09:11:30 us=846359 pkcs12_file = '[UNDEF]' 2023-09-28 09:11:30 us=846365 cipher_list = '[UNDEF]' 2023-09-28 09:11:30 us=846377 cipher_list_tls13 = '[UNDEF]' 2023-09-28 09:11:30 us=846383 tls_cert_profile = '[UNDEF]' 2023-09-28 09:11:30 us=846395 tls_verify = '[UNDEF]' 2023-09-28 09:11:30 us=846401 tls_export_cert = '[UNDEF]' 2023-09-28 09:11:30 us=846413 verify_x509_type = 0 2023-09-28 09:11:30 us=846419 verify_x509_name = '[UNDEF]' 2023-09-28 09:11:30 us=846425 crl_file = '[UNDEF]' 2023-09-28 09:11:30 us=846431 ns_cert_type = 0 2023-09-28 09:11:30 us=846436 remote_cert_ku[i] = 65535 2023-09-28 09:11:30 us=846448 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846454 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846460 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846471 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846478 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846483 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846489 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846500 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846507 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846518 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846524 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846536 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846542 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846548 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846559 remote_cert_ku[i] = 0 2023-09-28 09:11:30 us=846565 remote_cert_eku = 'TLS Web Server Authentication' 2023-09-28 09:11:30 us=846577 ssl_flags = 0 2023-09-28 09:11:30 us=846583 tls_timeout = 2 2023-09-28 09:11:30 us=846595 renegotiate_bytes = -1 2023-09-28 09:11:30 us=846601 renegotiate_packets = 0 2023-09-28 09:11:30 us=846613 renegotiate_seconds = 3600 2023-09-28 09:11:30 us=846619 handshake_window = 60 2023-09-28 09:11:30 us=846631 transition_window = 3600 2023-09-28 09:11:30 us=846637 single_session = DISABLED 2023-09-28 09:11:30 us=846648 push_peer_info = DISABLED 2023-09-28 09:11:30 us=846654 tls_exit = DISABLED 2023-09-28 09:11:30 us=846660 tls_crypt_v2_metadata = '[UNDEF]' 2023-09-28 09:11:30 us=846672 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846678 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846690 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846696 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846708 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846714 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846726 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846732 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846743 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846753 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846766 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846772 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846784 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846790 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846802 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846808 pkcs11_protected_authentication = DISABLED 2023-09-28 09:11:30 us=846820 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846826 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846838 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846844 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846856 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846862 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846873 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846879 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846891 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846897 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846909 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846914 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846926 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846932 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846943 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846949 pkcs11_private_mode = 00000000 2023-09-28 09:11:30 us=846961 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=846967 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=846978 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=846984 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=846996 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847002 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847013 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847019 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847031 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847037 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847048 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847054 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847066 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847072 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847083 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847089 pkcs11_cert_private = DISABLED 2023-09-28 09:11:30 us=847101 pkcs11_pin_cache_period = -1 2023-09-28 09:11:30 us=847107 pkcs11_id = '[UNDEF]' 2023-09-28 09:11:30 us=847119 pkcs11_id_management = DISABLED 2023-09-28 09:11:30 us=847131 server_network = 0.0.0.0 2023-09-28 09:11:30 us=847144 server_netmask = 0.0.0.0 2023-09-28 09:11:30 us=847156 server_network_ipv6 = :: 2023-09-28 09:11:30 us=847168 server_netbits_ipv6 = 0 2023-09-28 09:11:30 us=847175 server_bridge_ip = 0.0.0.0 2023-09-28 09:11:30 us=847187 server_bridge_netmask = 0.0.0.0 2023-09-28 09:11:30 us=847194 server_bridge_pool_start = 0.0.0.0 2023-09-28 09:11:30 us=847206 server_bridge_pool_end = 0.0.0.0 2023-09-28 09:11:30 us=847212 ifconfig_pool_defined = DISABLED 2023-09-28 09:11:30 us=847224 ifconfig_pool_start = 0.0.0.0 2023-09-28 09:11:30 us=847231 ifconfig_pool_end = 0.0.0.0 2023-09-28 09:11:30 us=847243 ifconfig_pool_netmask = 0.0.0.0 2023-09-28 09:11:30 us=847249 ifconfig_pool_persist_filename = '[UNDEF]' 2023-09-28 09:11:30 us=847261 ifconfig_pool_persist_refresh_freq = 600 2023-09-28 09:11:30 us=847267 ifconfig_ipv6_pool_defined = DISABLED 2023-09-28 09:11:30 us=847279 ifconfig_ipv6_pool_base = :: 2023-09-28 09:11:30 us=847285 ifconfig_ipv6_pool_netbits = 0 2023-09-28 09:11:30 us=847297 n_bcast_buf = 256 2023-09-28 09:11:30 us=847303 tcp_queue_limit = 64 2023-09-28 09:11:30 us=847309 real_hash_size = 256 2023-09-28 09:11:30 us=847320 virtual_hash_size = 256 2023-09-28 09:11:30 us=847326 client_connect_script = '[UNDEF]' 2023-09-28 09:11:30 us=847338 learn_address_script = '[UNDEF]' 2023-09-28 09:11:30 us=847344 client_disconnect_script = '[UNDEF]' 2023-09-28 09:11:30 us=847356 client_config_dir = '[UNDEF]' 2023-09-28 09:11:30 us=847362 ccd_exclusive = DISABLED 2023-09-28 09:11:30 us=847373 tmp_dir = '/tmp' 2023-09-28 09:11:30 us=847380 push_ifconfig_defined = DISABLED 2023-09-28 09:11:30 us=847392 push_ifconfig_local = 0.0.0.0 2023-09-28 09:11:30 us=847399 push_ifconfig_remote_netmask = 0.0.0.0 2023-09-28 09:11:30 us=847411 push_ifconfig_ipv6_defined = DISABLED 2023-09-28 09:11:30 us=847417 push_ifconfig_ipv6_local = ::/0 2023-09-28 09:11:30 us=847429 push_ifconfig_ipv6_remote = :: 2023-09-28 09:11:30 us=847435 enable_c2c = DISABLED 2023-09-28 09:11:30 us=847447 duplicate_cn = DISABLED 2023-09-28 09:11:30 us=847454 cf_max = 0 2023-09-28 09:11:30 us=847465 cf_per = 0 2023-09-28 09:11:30 us=847471 max_clients = 1024 2023-09-28 09:11:30 us=847477 max_routes_per_client = 256 2023-09-28 09:11:30 us=847489 auth_user_pass_verify_script = '[UNDEF]' 2023-09-28 09:11:30 us=847495 auth_user_pass_verify_script_via_file = DISABLED 2023-09-28 09:11:30 us=847507 auth_token_generate = DISABLED 2023-09-28 09:11:30 us=847513 auth_token_lifetime = 0 2023-09-28 09:11:30 us=847524 auth_token_secret_file = '[UNDEF]' 2023-09-28 09:11:30 us=847530 port_share_host = '[UNDEF]' 2023-09-28 09:11:30 us=847536 port_share_port = '[UNDEF]' 2023-09-28 09:11:30 us=847548 vlan_tagging = DISABLED 2023-09-28 09:11:30 us=847554 vlan_accept = all 2023-09-28 09:11:30 us=847559 vlan_pvid = 1 2023-09-28 09:11:30 us=847565 client = ENABLED 2023-09-28 09:11:30 us=847571 pull = ENABLED 2023-09-28 09:11:30 us=847576 auth_user_pass_file = 'stdin' 2023-09-28 09:11:30 us=847583 OpenVPN 2.5.5 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Jul 14 2022 2023-09-28 09:11:30 us=847597 library versions: OpenSSL 3.0.2 15 Mar 2022, LZO 2.10 Enter Auth Username: jonh 🔐 Enter Auth Password: ******** 2023-09-28 09:11:41 us=800136 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-28 09:11:41 us=800204 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-28 09:11:41 us=800313 Control Channel MTU parms [ L:1621 D:1172 EF:78 EB:0 ET:0 EL:3 ] 2023-09-28 09:11:41 us=861231 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] 2023-09-28 09:11:41 us=861368 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client' 2023-09-28 09:11:41 us=861395 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-server' 2023-09-28 09:11:41 us=861422 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-28 09:11:41 us=861469 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-09-28 09:11:41 us=861512 UDPv4 link local: (not bound) 2023-09-28 09:11:41 us=861535 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-28 09:11:41 us=883767 TLS: Initial packet from [AF_INET]24.XXX.XXX.70:1194, sid=9364b1cb d34c4d04 2023-09-28 09:11:44 us=4 VERIFY OK: depth=1, CN=internal-ca, C=CA, ST=ON, L=Oakville, O.XXXXXXXX, OU=lab 2023-09-28 09:11:44 us=401412 VERIFY KU OK 2023-09-28 09:11:44 us=401450 Validating certificate extended key usage 2023-09-28 09:11:44 us=401465 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2023-09-28 09:11:44 us=401495 VERIFY EKU OK 2023-09-28 09:11:44 us=401508 VERIFY OK: depth=0, CN=lab.XXXXXXXX.net, C=CA, ST=ON, L=Oakville, O.XXXXXXXX, OU=lab 2023-09-28 09:12:41 us=480977 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) 2023-09-28 09:12:41 us=481031 TLS Error: TLS handshake failed 2023-09-28 09:12:41 us=481159 TCP/UDP: Closing socket 2023-09-28 09:12:41 us=481203 SIGUSR1[soft,tls-error] received, process restarting 2023-09-28 09:12:41 us=481228 Restart pause, 5 second(s) 2023-09-28 09:12:46 us=481699 Re-using SSL/TLS context 2023-09-28 09:12:46 us=481912 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-28 09:12:46 us=481944 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication 2023-09-28 09:12:46 us=482046 Control Channel MTU parms [ L:1621 D:1172 EF:78 EB:0 ET:0 EL:3 ] 2023-09-28 09:12:46 us=529328 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] 2023-09-28 09:12:46 us=529431 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client' 2023-09-28 09:12:46 us=529459 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-server' 2023-09-28 09:12:46 us=529476 TCP/UDP: Preserving recently used remote address: [AF_INET]24.XXX.XXX.70:1194 2023-09-28 09:12:46 us=529523 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-09-28 09:12:46 us=529545 UDPv4 link local: (not bound) 2023-09-28 09:12:46 us=529556 UDPv4 link remote: [AF_INET]24.XXX.XXX.70:1194 2023-09-28 09:12:46 us=553920 TLS: Initial packet from [AF_INET]24.XXX.XXX.70:1194, sid=3fa5583f 729cc034 2023-09-28 09:12:46 us=600295 VERIFY OK: depth=1, CN=internal-ca, C=CA, ST=ON, L=Oakville, O.XXXXXXXX, OU=lab 2023-09-28 09:12:46 us=600483 VERIFY KU OK 2023-09-28 09:12:46 us=600511 Validating certificate extended key usage 2023-09-28 09:12:46 us=600520 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2023-09-28 09:12:46 us=600527 VERIFY EKU OK 2023-09-28 09:12:46 us=600542 VERIFY OK: depth=0, CN=lab.XXXXXXXX.net, C=CA, ST=ON, L=Oakville, O.XXXXXXXX, OU=lab ^C2023-09-28 09:12:56 us=645614 event_wait : Interrupted system call (code=4) 2023-09-28 09:12:56 us=645681 SIGTERM received, sending exit notification to peer 2023-09-28 09:12:57 us=776075 TCP/UDP: Closing socket 2023-09-28 09:12:57 us=776167 SIGTERM[soft,exit-with-notification] received, process exiting -
@jonh001
This seems to be the clients log. We got this already. -
@viragomann
Sorry about that - server log attached.
Couldn't insert it here inline because it kept being flagged as spam
server_log.txt
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.