Allow outbound rule for all public addresses
-
Hello,
I am really struggling with trying to get what I think is a basic rule working.
All I am trying to do (at this point) is to allow an IoT device outbound to all public IP address ranges.
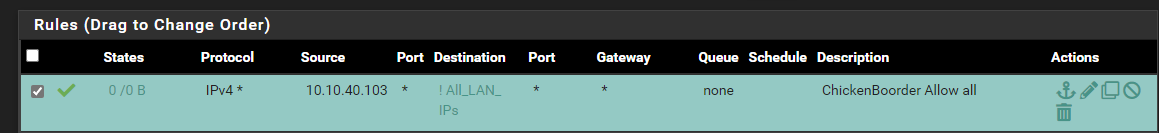
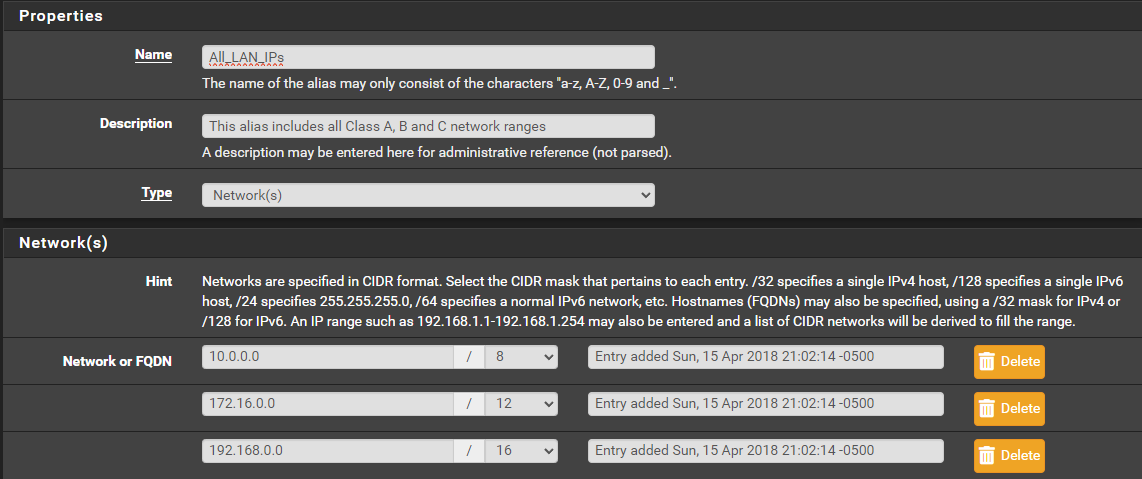
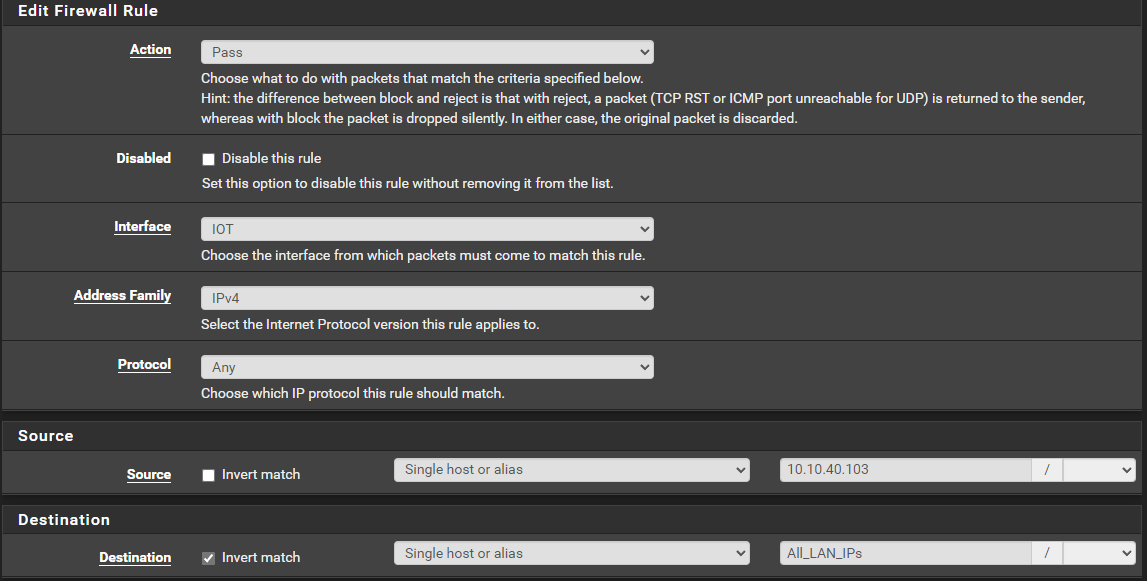
I created a simple allow rule that has the source IP address of the device which matches any port/protocol destined to any NON private IP address... (I have an alias configured which specifies private IP addresses). I am inverting the All_LAN_IP's, so it should be allowing any outbound traffic bound for any IP address that is not in the range of the Alias...
For some reason, I cannot get the rule to match any traffic that is being sent. The rule never shows any connections or bytes transferred.
Does anyone have any ideas why this rule might not match outbound traffic?
Thanks!
-
@ZipleR have you just tried pinging say 8.8.8.8?
If that is the only rule you have, I could se the device trying to talk to pfsense IP for say dns, and it not resolving - so then no it wouldn't have an IP to try and send traffic too.
-
@johnpoz
Sorry for not including all of the rules.. Just didn't think it was necessary.I put the rule at the top of the list so it would be the first rule that applies...
I have many other things on this network that are working just fine.
As far as DNS goes, I actually do have DNS using a public DNS server just to make sure my PIHole is not blocking anything. The public DNS server is allowed with the rule above - and actually a 2nd rule that would catch it either way.
Other than a reserved IP address and DNS settings, there is nothing tricky about this network.
Every other light/switch/outlet/sensor/etc in my house uses it.
I just can't figure out why a single device that I am creating a specific rule for is not hitting the first/custom rule.
Is there maybe something wrong with the way I think "Invert match" works?
-
@ZipleR said in Allow outbound rule for all public addresses:
I put the rule at the top of the list so it would be the first rule that applies...
which would then block access to dns and then my scenario would be possible to why you don't have "internet"
Is there maybe something wrong with the way I think "Invert match" works?
No you have the concept down,. but have no idea what other rules you have in place. Do you have any rules in floating? We don't even know if you put that rule on the correct interface.
We don't know that the device even has that IP, or is using pfsense as its gateway..
Also inverted rules can run into issues if your using vips, using an alias could be causing it issues? Here would be a much better way to lock down.. This 1 specific IP from talking to the rest of your network, while allowing others on the network to talk to other things..
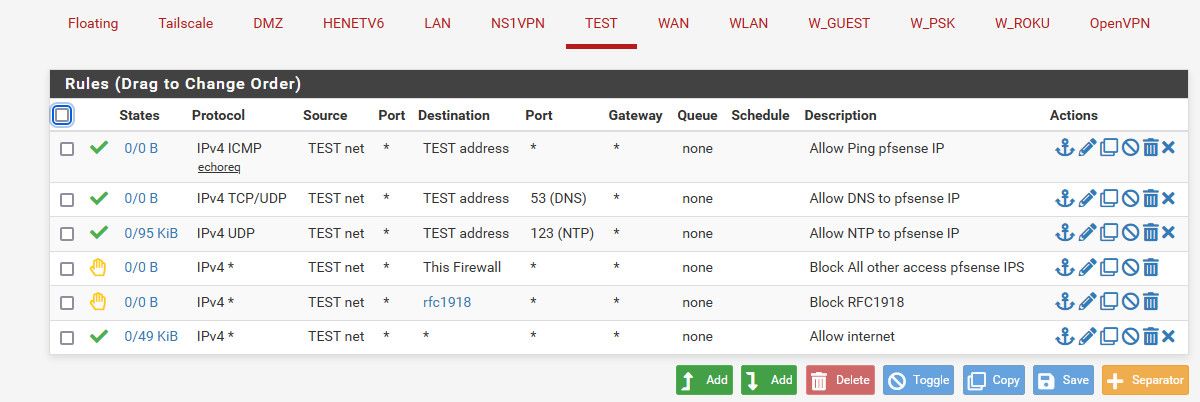
It is better to be very explicit in your rules.. Lets see the full rule set.. Setup your rules to specific block to what you don't want it to go to, vs trying a bang rule.
Here is a set of rules that would prevent this network from talking to anything else on any other vlans, but allow internet.. Could be easy adjusted to allow other things on that network, but block this 1 IP.