Modem-WAN ethernet rule for AT&T bypass allows interrupt manipulation and stateless access
-
I have had one gaming monitor's kernel corrupted on an AT&T bypass setup. The first setup was with a Ryzen 7 1700X and GTX 1050TI. I was unknowingly changing CPU mappings while tuning and possibly allowed the wrong TX/RX queues on a logical or hard cpu. I believe my GPU was utilized to attack my gaming monitor, or unknowingly caused interrupts against my Nintendo Switch, which passed the interrupts to my gaming monitor over HDMI.
My second setup is on a Ryzen 5 PRO 3400GE APU (I freed up a PCI express slot). I set up Machdep with separate_txrx sysctl and use_logical_cores sysctl in accordance with this online guide:
https://lists.freebsd.org/pipermail/dev-commits-src-main/2021-April/003820.html
Referenced CPU mapping behavior is listed at the end of this posting.
The issue lies with the Modem-WAN ethernet rule being advised to allow "all" inbound. After changing this rule to 802.1X only, creating IPV4 and ARP L2 block rules and block all other L2 protocol rules, I noticed lots of unauthorized traffic that was magically authorized. Yesterday, the system even went as far as to attack my Television's kernel, causing cursors and menus to pop up. It is an attack point.
Additionally, because WOL_Magic Packets are enabled on all interfaces by default, my PC kept booting up magically while in sleep mode. This was remedied with the shellcmd utility and command ifconfig igbX -wol on all interfaces.
Allowing all L2 IPV4 and any other L2 protocol to and from the AT&T router gives people time to hack it and attack your system. While I am not 100% sure this is what happened, as stateless connections were used, it caused damages which were thankfully covered by warranty at Microcenter.
Some CPU mappings seem to make attacks to the BGW-210 router and GPU/APU easier than others. Fortunately, I have the gall to only have one device plugged in at a time and change my setup every day obsessively. All the while, learning more ways to audit this firewall. PS, ICMP management kind of stinks on pfSense.
-
- CPU mapping behaviors
-
-
-
- 'separate txrx' refers to the separate_txrx sysctl
-
- 'use logical' refers to the use_logical_cores sysctl
-
- 'INTR CPUS' indicates whether bus_get_cpus(INTR_CPUS) succeeded
-
-
- separate use INTR
-
- txrx logical CPUS result
-
-
-
-
- - X RX and TX queues mapped to consecutive physical
-
-
-
cores with RX/TX pairs on same core and excess
-
-
-
of either following
-
-
-
- X X RX and TX queues mapped to consecutive cores
-
-
-
of any type with RX/TX pairs on same core and
-
-
-
excess of either following
-
-
-
X - X RX and TX queues mapped to consecutive physical
-
-
-
cores; all RX then all TX
-
-
-
X X X RX queues mapped to consecutive physical cores
-
-
-
first, then TX queues mapped to L2 neighbor of
-
-
-
the corresponding RX queue if one exists,
-
-
-
otherwise to consecutive physical cores
-
-
-
- n/a - RX and TX queues mapped to consecutive cores of
-
-
-
any type with RX/TX pairs on same core and excess
-
-
-
of either following
-
-
-
X n/a - RX and TX queues mapped to consecutive cores of
-
-
-
any type; all RX then all TX
-
- */
-
-
@HLPPC Also, L2 ethertype rules randomly change order when pressing the save button or rebooting. Which is hot garbage.
-
@HLPPC I also have a static IP block which is constant malicious traffic flooding my system, in addition to the standard AT&T DHCP lease.
-
@HLPPC And to make matters worse I am also using an old realtek card for the MODEM interface. Probably a major cause. 🥵
-
@HLPPC I've also found that it helps to disable all ifconfig options on the MODEM interface and to audit the L2 firewall rules:
ifconfig igbx -txcsum -rxcsum -txcsum6 -rxcsum6 -lro -tso4 -tso6 -vlanhwcsum -vlanhwtag -vlanmtu -vlanhwfilter -vlanhwtso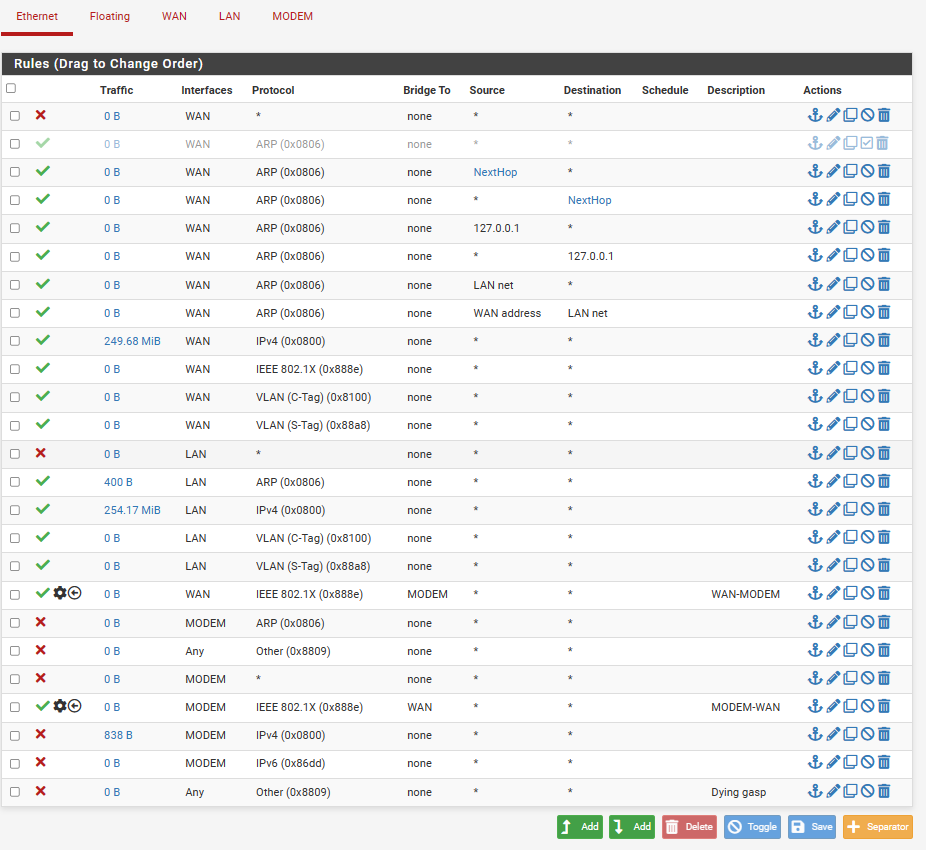
Thanks in the dc for mentioning this vulnerability to me.
https://derekabdine.com/blog/2022-arris-advisory.html