WOL Doesnt Seem To Be Working
-
hi i know the WOL worked long ago and i hadnt used it.. but i wanted to start using it again and my pre defined ones werent working
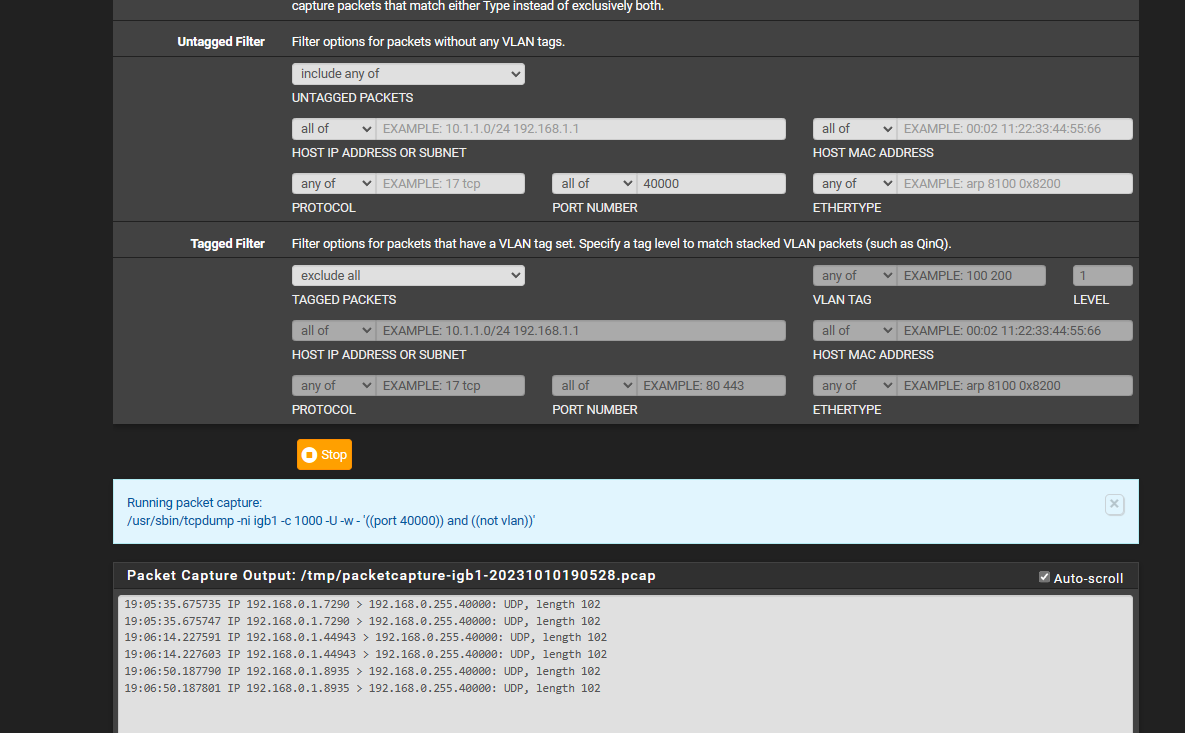
i checked the MAC address's and they still correct...i tried the Packet Capture and under the Port i did 7 9 and hit start and when i did WOL in pfsense in another window it doesnt show up... what should i loook for what could be blocking the only thing i really did to the rules page was add the the Bypass Policy Rule
so not sure... what should i all post .or what other things to test
i did try Packet Capture 192.168.0.255 and that least captures broadcast captures but it doesnt captures Port 7 or 9 for WOL port
here is the rules
i added the rules port 7 and 9 before bypass policy rule and i moved it after.. and neither has worked
-
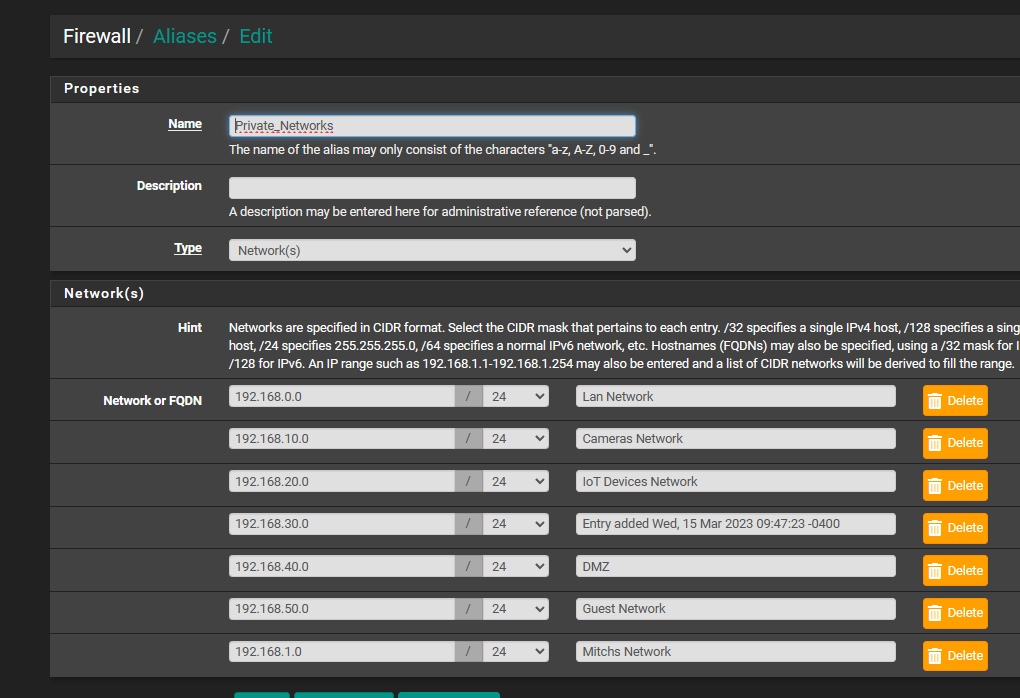
and here is my private networks screen shot
-
You don't need firewall rules to allow that, the packets sent are outbound.
What version are you testing on?
You should see it in a pcap but not if you filter like that. For example, as tested in 2.7:
22:44:55.173683 00:a0:c9:00:00:00 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 144: (tos 0x0, ttl 64, id 12655, offset 0, flags [none], proto UDP (17), length 130) 192.168.70.1.50837 > 192.168.70.127.40000: [bad udp cksum 0x0e51 -> 0x62a7!] UDP, length 102Note that the IP addresses and ports used don't matter. The packet is broadcast and the content of the packet has the target MAC.
Steve
-
ah ok
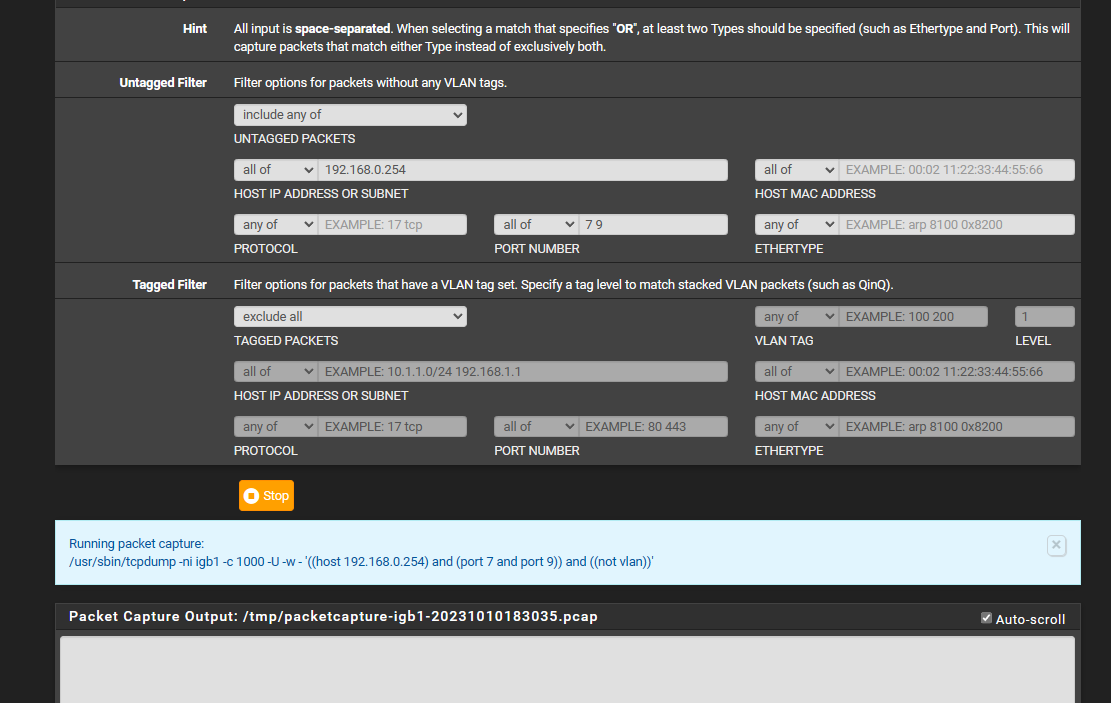
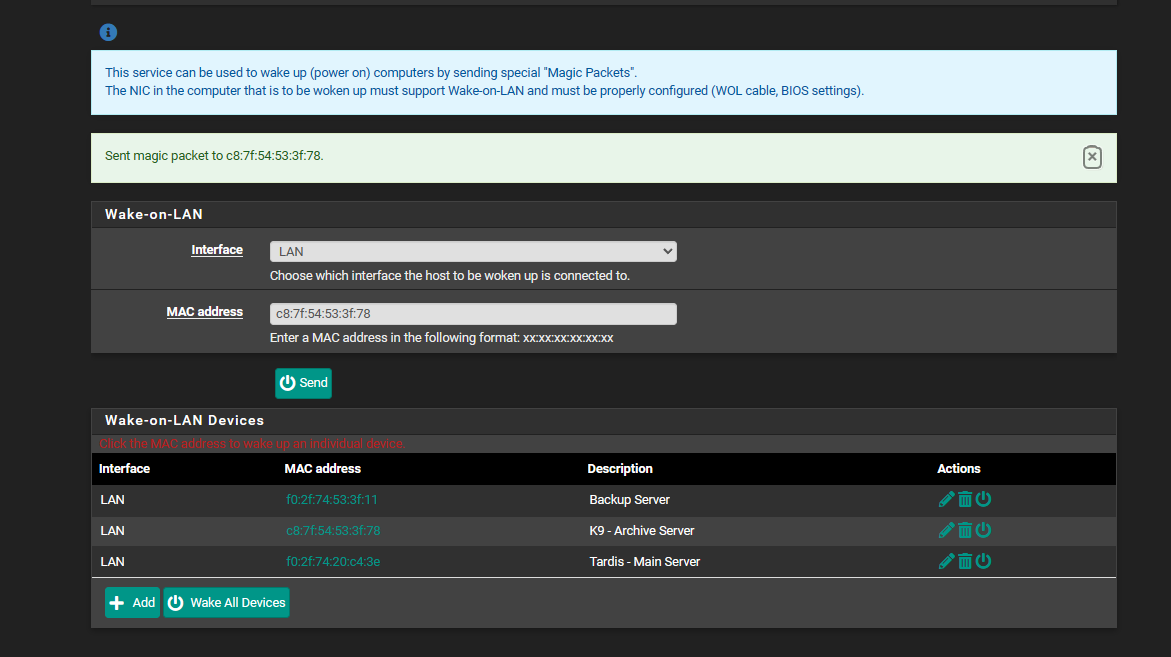
and im using 2.7so in the ports i put 7 9 least i think thats how your supposed to do it?
im also using a MikroTik Switch if that matters too? CSS326-24G-2S+here is the screen shot i did
ive tried with Ip address and with it blank and both show nothing in the bottom when i hit the WOL buttons in pfsense on another window
-
If you look at my pcap you can see pfSense sends WoL packet from a random port to port 40000 so, no, filtering for port 7 or 9 isn't going to match it.
I'm assuming you're sending WoL from pfSense itself?
-
@stephenw10
i had googled what WOL ports were and thats how i found about port 7 and 9 as i didnt know what ports WOL usedand ya i using it directly from Pfsense
-
i tried this and then wol but still no packets
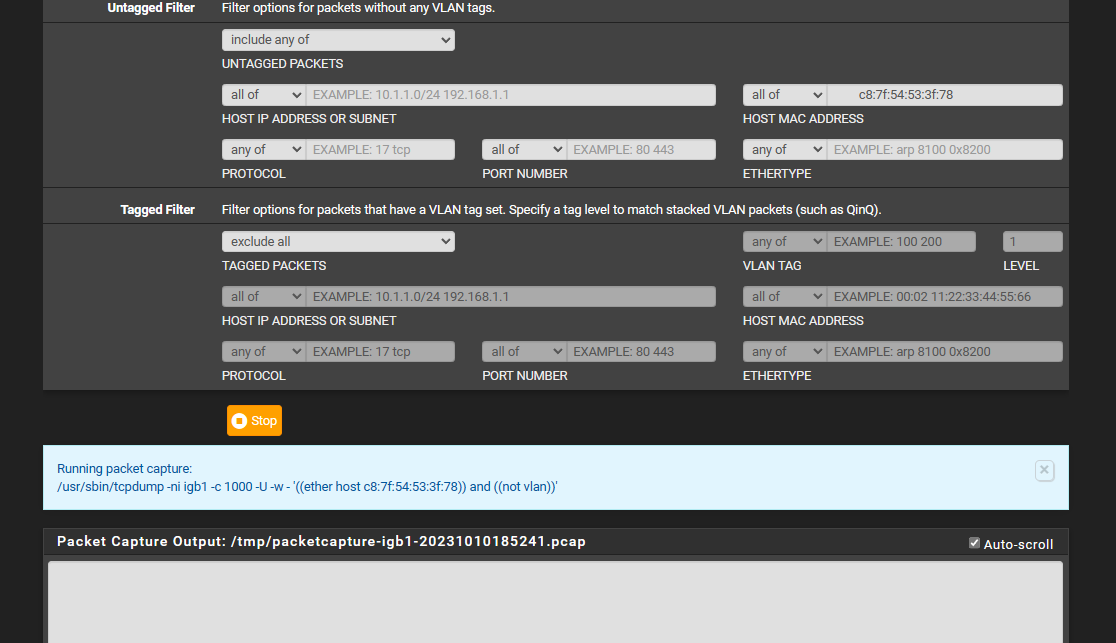
-
Yes, you won't see it by filtering by the target MAC because the WoL packet is broadcast to ff:ff:ff:ff:ff:ff. The target MAC is in the packet contents and is not the source or destination MAC so that won't match.
Set only port 40000 in the pcap if you need to filter it and retest.
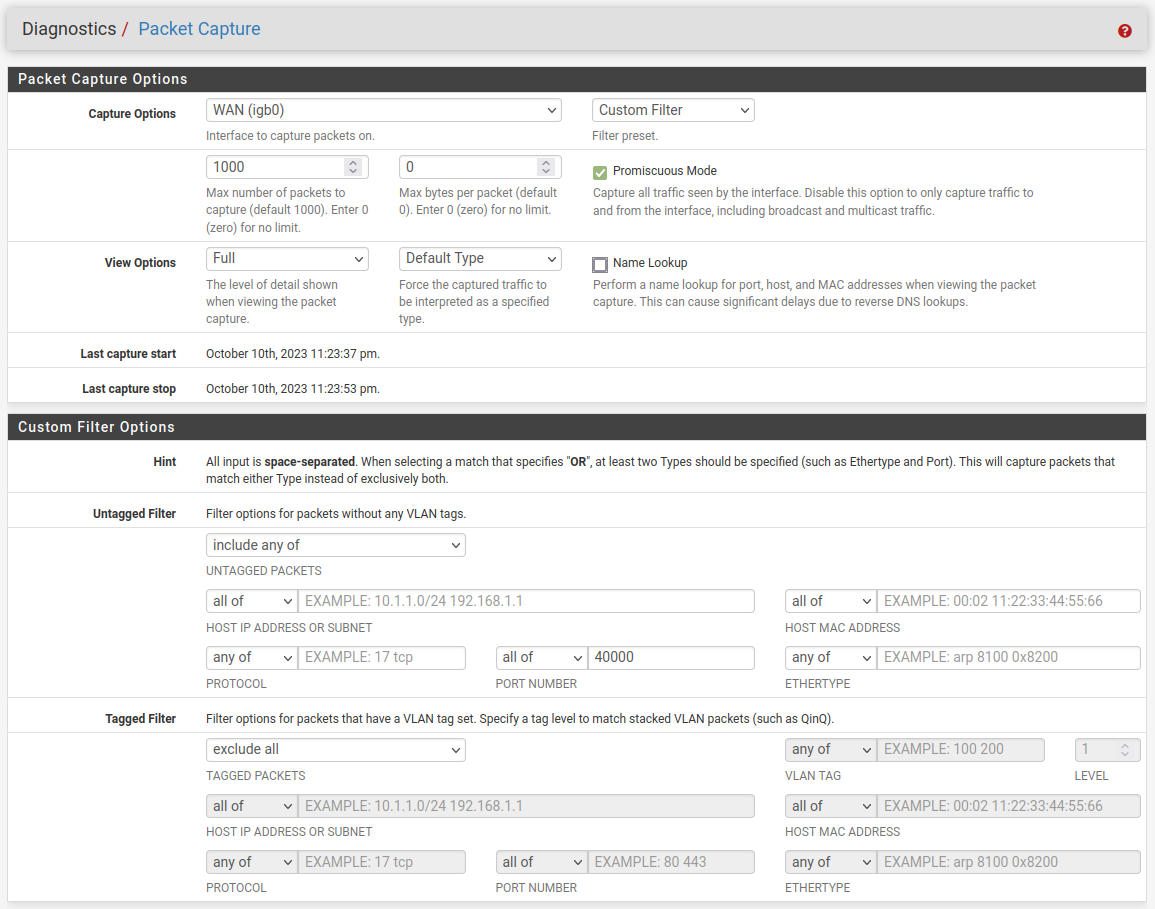
-
@stephenw10
ok so i tested all 3... each one gave a reading 2 times... they gave a different port? and i guess the mac address is hidden in the packetsso then that part is working something is wrong in the configuration of my switch then correct? as my computers are set for WOL and the network amber light flashes while the computer is off it just doesnt wanna wake up
the mikrotik documenation is poor
-
-
Ok, there you go. So, assuming that's the correct interface it is sending the packets. Either they aren't arriving at the target devices or the target devices are not listening for them. Probably the latter. Some machines are a PITA to ensure they shutdown in the correct mode for WoL.
-
@stephenw10 ya the interface is the lan and it does the vlans too so vlans 10 20 30 40 50 all go out the same interface and into the miktrotek switch...
the servers all run unraid and when they boot up i have a go file that runs
ethtool -s eth0 wol gthat enables the the ethernet to go into wake up lan mode when it shuts down plus the motherboard are set if power is off or so they get wake up lan from the motherboard...
what is a PITA?
and is there a way to test if the WOL packets are being sent to the switch or the ports etc?
-
If you can set a mirror port on the switch you can pcap on that see what's actually leaving whatever it's mirroring.
-
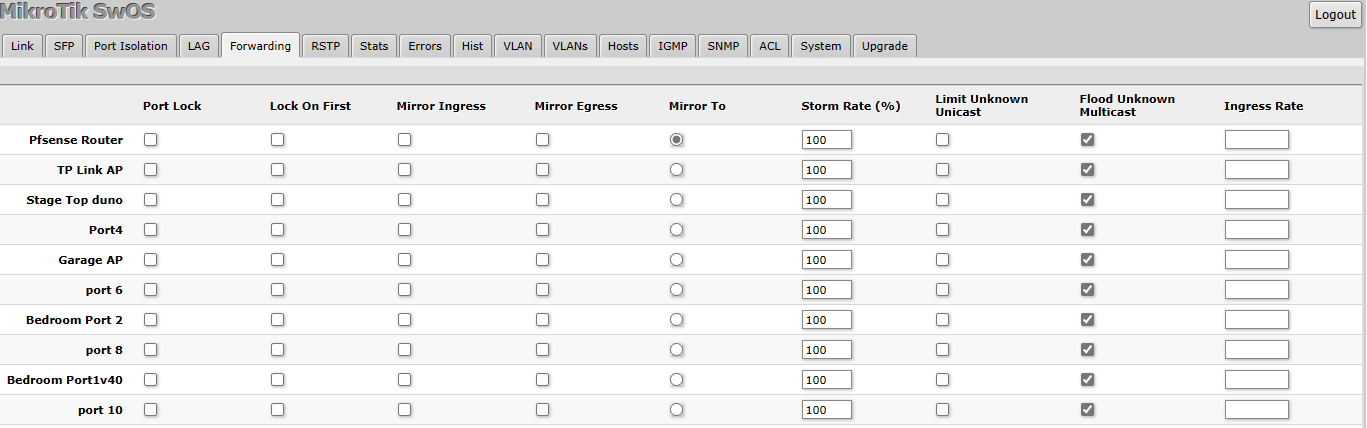
@stephenw10 it has a mirror to option on one of the pages not sure how i use it though
and how do i pcap on the mirror port?
-
I've never used Mikrotik SwOS so I can't be sure but I'd expect to select a port as mirror ingress and another port to mirror it to. Unclear what the difference would be between 'mirror to' and 'mirror egress'. Then connect a laptop (or something suitable) to the egress port and pcap on that.
-
@stephenw10
i tried a setting and i downloaded some program called WireShark... i though program be easy more of a headache i wanted it it to just sit there and wait till i hit the WOL in pfsense and it would populate like pfsense did but its going haywire i havent figure out how to slow it downhave you used it or is there a pfense pcap that i can use on the laptop to see if its getting the wol packet.. cuz this crazy its going sooooooooo fast i cant even read it lol
-
Yup Wireshark is pretty much the standard packet capture analysis tool and can also capture directly.
You can apply a filter to the capture. So destination port 40000 for example:
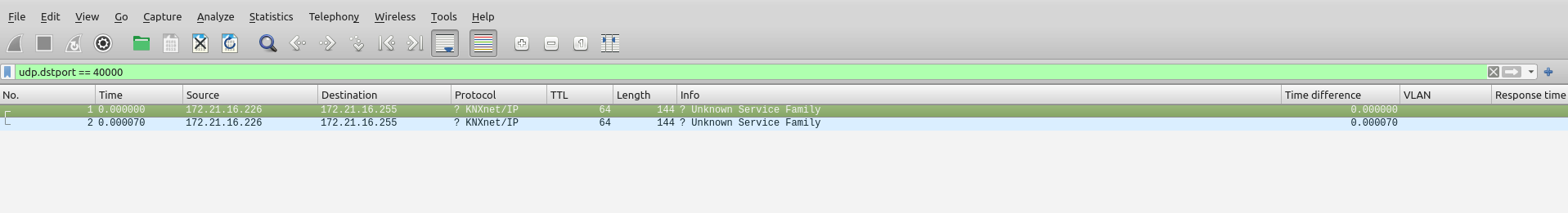
Steve
-
@comet424 said in WOL Doesnt Seem To Be Working:
cuz this crazy its going sooooooooo fast i cant even read it lol
If your going to run wireshark on your machine to make sure your machine is seeing some specific traffic. Its best to shut down all other connections, like browser or apps, etc. And also you can set a capture filter to only show the specifics your looking for.
The gui in pfsense packet capture simplifies doing that. But if you want to do it directly with wireshark running on your device.
https://wiki.wireshark.org/CaptureFilters
edit: not sure what version of wireshark @stephenw10 is using there, but seems a bit dated ;) ?
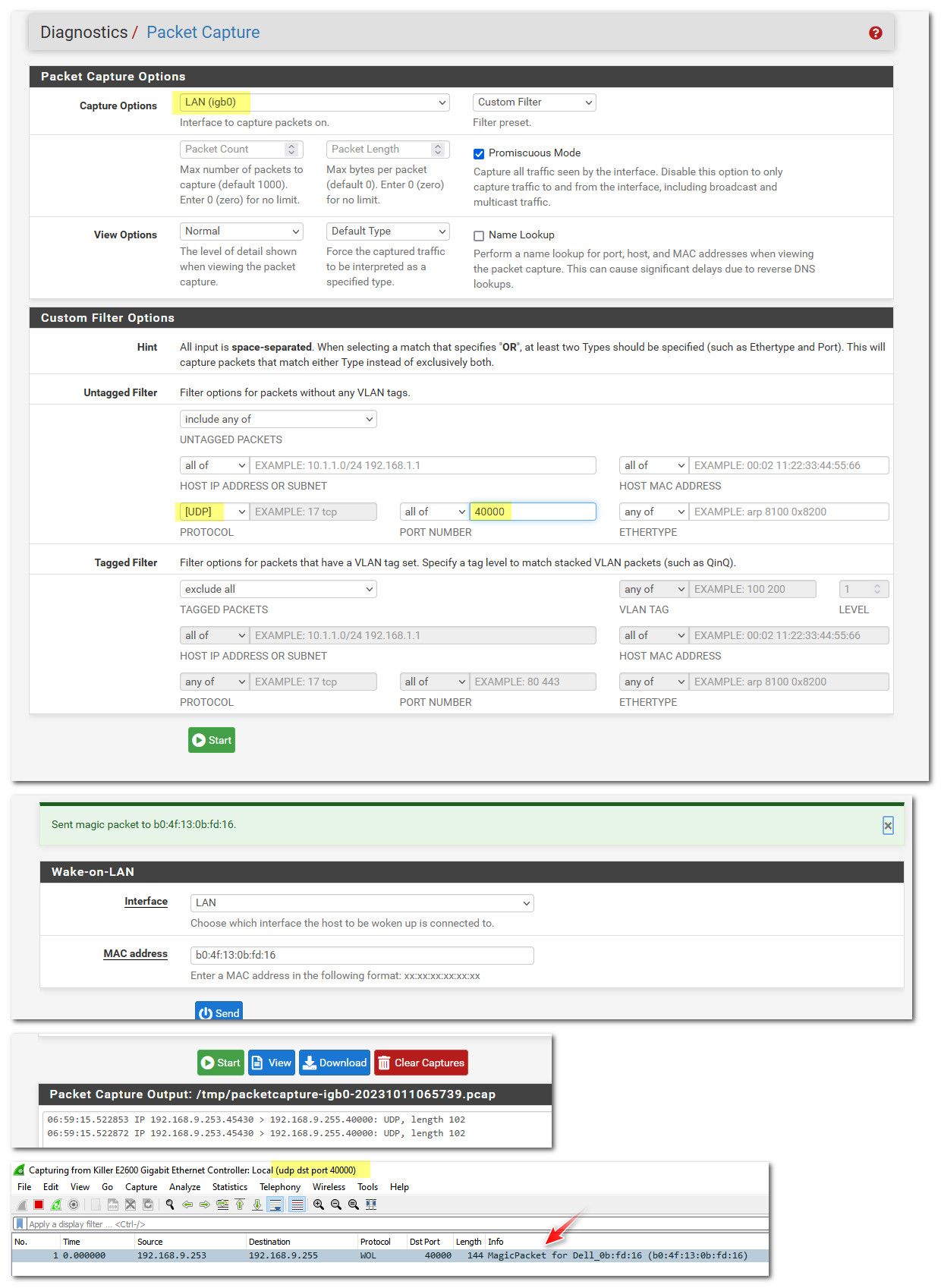
There is the packet capture from pfsense, and also from wireshark running on my pc with capture filter in place.
-
@comet424 said in WOL Doesnt Seem To Be Working:
ya the interface is the lan and it does the vlans too so vlans 10 20 30 40 50 all go out the same interface and into the miktrotek switch...
So on what VLAN is the host you want to wake...
-
@comet424 said in WOL Doesnt Seem To Be Working:
hi i know the WOL worked long ago and i hadnt used it.. but i wanted to start using it again and my pre defined ones werent working
i checked the MAC address's and they still correct...Assuming everything is on the same LAN, WoL has nothing to do with IP or firewall rules. A magic packet is sent for the MAC address, which the hardware responds to. This means the hardware must support WoL and it must be enabled.