Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?
-
@Gertjan said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
Btw : What I never quit well understood :
My IPv6 LAN : 2a01:cb19:beef:a6dc:92ec:77ff:fe29:392c
Why can't I select / set it to 2a01:cb19:907:a6dc::1
or something like that. Why the random "92ec:77ff:fe29:392c" ?It is most probably a SLAAC-address. See this from the online-help of my fritzbox (with vDSL).
The Assign IPv6 address FRITZ!Box randomly option works only if the FRITZ!Box determines the interface ID of your IPv6 address itself via SLAAC (Stateless Address Auto-Configuration). The interface ID is the second component of the IPv6 address. The first component is the IPv6 prefix, which is assigned by the internet provider. The interface ID is derived from the MAC address of the FRITZ!Box in accordance with the EUI-64 method.
-
@Bob-Dig
Ah, yeah, that figures.
But I'm not using a Fritz, but pfSense ;)I wonder : can I static-DHCPv6-MAC-Lease the LAN IP of pfSense itself ??

dit : euh ... what is the DUID of my 4100 igc0 LAN interface ?
-
@Gertjan said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
But I'm not using a Fritz, but pfSense ;)
Why LAN-Interface, it is about the WAN. You could look into NPt if you want more than one subnet of IPv6. But to be honest, I haven't understand that fully either.
-
@Bob-Dig said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
@Gertjan said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
But I'm not using a Fritz, but pfSense ;)
Why LAN-Interface, it is about the WAN. You could look into NPt if you want more than one subnet of IPv6. But to be honest, I haven't understand that fully either.
Ah, sorry. I haven't read your post close enough, I thought it was about the WAN-interface.
Still it would be SLAAC.

-
@bmeeks said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
By the way, your errors above with the "Best Practices Analyzer" indicate that you do not have some things correctly configured in your Active Directory environment -- even IPv4 related things. So, I'm not surprised the DHCPv6 configuration is also not operating properly.
Yes - that happens when I set the DNS fully back to pfSense in the AD/DS server....you get errors that indicate that pfSense must also resolve the Global Catalog and Kerberos records. It does not do this, and I was never able to get rid of those. Even on a fully functioning pfSense which is doing DNS/DHCP/DHCPv6 and no errors - which mine was. I then installed 2019 and activated the AD/DS role, which also turns on DNS I start getting those almost immediately.
I have not found a 'solid' set of instructions on how to set AD/DS with pfSense that has a walk-through setup on it. BEFORE pfSense when the Netgear ORBI was between Modem (ISP) and my network - I never saw any of that...I went with pfSense as ORBI was causing all sorts of fits with my newly installed SmartHome.
Everything that I can find on setting up pfSense to work with COMCAST (ISP) says to set WAN to DHCP and DHCPv6 - but the v6 addresses always look like SLAAC addresses. Never once has it given me an address which does not have the "MAC looking" part at the end.
-
@bearhntr said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
@bmeeks said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
By the way, your errors above with the "Best Practices Analyzer" indicate that you do not have some things correctly configured in your Active Directory environment -- even IPv4 related things. So, I'm not surprised the DHCPv6 configuration is also not operating properly.
Yes - that happens when I set the DNS fully back to pfSense in the AD/DS server....you get errors that indicate that pfSense must also resolve the Global Catalog and Kerberos records. It does not do this, and I was never able to get rid of those. Even on a fully functioning pfSense which is doing DNS/DHCP/DHCPv6 and no errors - which mine was. I then installed 2019 and activated the AD/DS role, which also turns on DNS I start getting those almost immediately.
I have not found a 'solid' set of instructions on how to set AD/DS with pfSense that has a walk-through setup on it. BEFORE pfSense when the Netgear ORBI was between Modem (ISP) and my network - I never saw any of that...I went with pfSense as ORBI was causing all sorts of fits with my newly installed SmartHome.
You can't get rid of your Windows AD DNS server so long as you have a functioning Active Directory setup. But you can let pfSense be your DHCP server and DNS also, if you desire. But in that scenario you must configure the proper domain overrides so that pfSense will always send any DNS request for something in your AD domain to the Windows DNS server. All the clients on your network would be pointed to pfSense for DNS in that configuration. But anything they asked about pertaining to your local AD domain would be "forwarded" by pfSense to the Windows DNS server for resolution. Anything for an Internet domain would either be resolved or forwarded by
unboundon pfSense depending on how you have it configured.You would need to configure your WIndows DNS server to use itself for AD domain lookups and forward any external lookups to pfSense. You set pfSense as a Forwarder in the WIndows AD DNS configuration if doing what I described above.
-
@bearhntr said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
Everything that I can find on setting up pfSense to work with COMCAST (ISP) says to set WAN to DHCP and DHCPv6 - but the v6 addresses always look like SLAAC addresses. Never once has it given me an address which does not have the "MAC looking" part at the end.
What you see on the WAN has nothing to do with what you need to have on your LAN. They can be different with prefix delegation in use. Quit worrying about your WAN's address. It has one, so it's good.
The reason the guides say to use DHCPv6 is because the ONLY way prefix delegation works is through the DHCP client on your pfSense box. That client reads the special prefix delegation commands and processes them. Your WAN and LAN will likely have totally different IPv6 addresses, but your ISP is taking care of routing both of those for you behind the scenes. And with prefix delegation in use, the WAN can still get its address through SLAAC.
Configure the DHCP client on pfSense to print debug messages as @Gertjan shows, then examine the DHCP tab under STATUS > SYSTEM LOGS. It will show you the IPv6 prefix that Comcast is assigning for you.
This thread has gotten quite long and has a sideline conversation in it as well, but I think I recall reading a post up near the top where you said if you let pfSense do everything (DHCP and DNS) that your IPv6 stuff worked. But this excluded your Windows AD stuff, and you wanted that in the loop with DHCPv6 on your LAN from Windows AD. Making that work is more difficult, but possible. It just will have a need for manual intervention should your prefix from Comcast change.
I think your problem with that not working is related to you not having the correct IPv6 prefix assigned as the address scope for your LAN in the Windows DHCP server.
-
I thought that I had that setup once before---I will have to go back through all the settings, or simply rebuild the AD/DS. It was fairly brand new - only had added 2x users (one for pfSense Admin and one for NAS Admin - both using LDAP). Those were working. I really wanted to use my PROXMOX box and put the pfSense and AD/DS on there - but never could them to place nice together and get to the Internet.
I am guessing that is the only way I am going to get this working.
I cleared the logs this AM and within 10 mins I am getting these again, too. I hate seeing WARNINGS and errors in the logs - makes me think that something is broken or mis-configured:
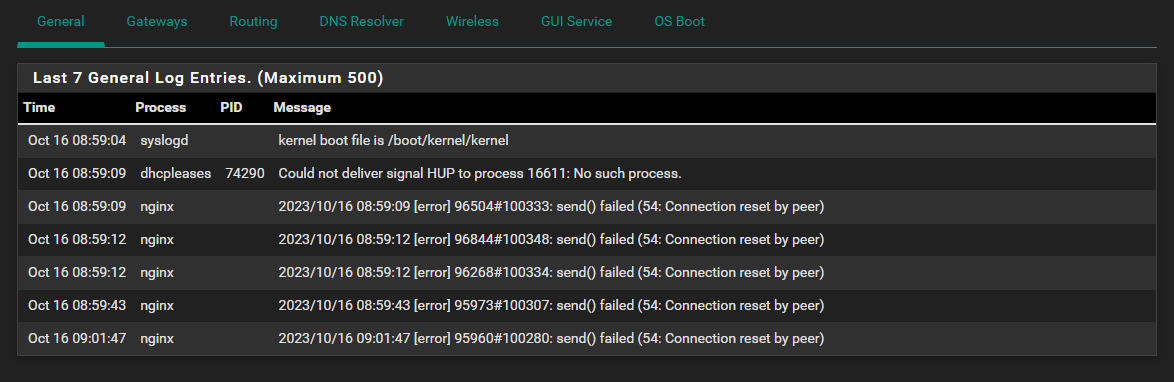
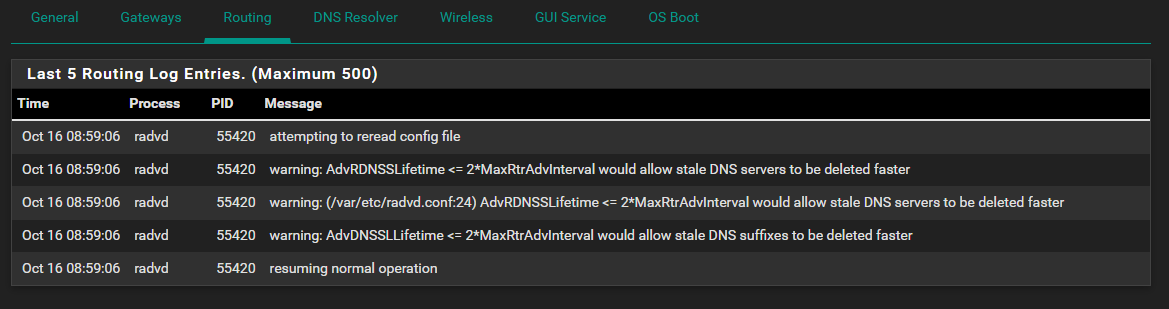
-
@bmeeks said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
What you see on the WAN has nothing to do with what you need to have on your LAN. They can be different with prefix delegation in use. Quit worrying about your WAN's address. It has one, so it's good.
I am not worried about WAN - and I realize that has nothing to do with that I am trying to do. I look that as OUTSIDE THE FIREWALL stuff anyway. pfSense is the wall around the castle and the draw bridge is WAN.
@bmeeks said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
I think your problem with that not working is related to you not having the correct IPv6 prefix assigned as the address scope for your LAN in the Windows DHCP server.
I have done this numerous times before ever coming here for help. I would take the IP Address that COMCAST (with Track Interface) to my LAN - and setup the DHCPv6 scope on the AD/DS server to use the first 4 hex blocks (and ::1/64) as the rest of it. Things still never worked right.
Looks like today I was able to FORCE COMCAST to give me a new prefix completely.... lol. I set WAN to SLAAC .. SAVED and applied. I did indeed get an address, and it changed
from 2601:c4:c501:7aa0: to 2601:c4:c501:8bf0: the rest of the address is the same.
I then changed it back to DHCP6 and for now have the PD set to 64 - I do not really have a need for the others until get this working and figure out how to put WIRED and WIRELESS on separate segments. The box that pfSense is running on (an HP t620+ ThinClient has built in wireless - which I disabled in the BIOS).
-
Thanks again for all the help. I am going to leave the IPv6 stuff to pfSense and re-build my DC (I have learned that once you enable something in Windows for a DC - turning it OFF does not always un-do the changes ... gotta love MS). I found an old posting of yours (below) and wonder if you can help me do this with my setup:
Using pfSense as firewall and Windows Server as DHCP and DNS server
@bmeeks Oct 13, 2021, 10:16 AMIf you have an Active Directory setup on your Windows server, then you absolutely need to use Windows for DHCP and DNS (especially DNS as the unbound DNS daemon on pfSense is really not suitable for Active Directory).
So here is what I suggest:
Use Windows for DHCP and DNS. Configure DHCP on your Windows Server to handout the Domain Controller as the DNS server for all clients.
In the Windows DNS setup, you have two options. Let Windows DNS act as a resolver, or have Windows DNS forward non-local lookup requests to either pfSense or an external DNS provider like Cloudfare, Google, OpenDNS, etc. I prefer to let Windows DNS resolve. There are several Google tutorials for how to configure that in Windows.
Over on the pfSense box, you can leave the DNS setup at the out-of-the-box defaults. Don't put any IP addresses for DNS in the SYSTEM > GENERAL SETUP page.
There are two things you want to configure on the DNS Resolver tab under SERVICES > DNS RESOLVER. First, in the Custom Options box you need to provide the name of your Windows AD domain like so --
server:
private-domain: "yourdomain.tld"
Second, you will want to configure two domain overrides so that pfSense will know to contact your Windows DNS server when it wants to resolve the IP address of any local hosts, or if it wants to perform a reverse pointer lookup on a local IP. So configure one domain override for your domain name and point to your Windows DNS server as the authoritative server for the domain, and configure a second override for the *.in-addr.arpa reverse IP pointer range.These DNS overrides are necessary so that pfSense can find your local host names if you do things like perform lookups on firewall log entries or view the ARP table. The overrides tell pfSense which DNS server is authoritative for your domain and reverse IP pointer range.]
This sounds like what I want to do. I have my own 'domain' regsitered with CloudFlare and I would like to use that on AD/DS. Is that doable?
-
@bearhntr said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
I have my own 'domain' regsitered with CloudFlare and I would like to use that on AD/DS. Is that doable?
No, you generally can't do this because the IP addresses are different. Your Windows AD domain controller is behind your firewall on private RFC1918 address space. Your Cloudfare hosted domain has a public IP. That can't work for Active Directory without jumping through a lot of advanced hoops to configure what is essentially a split-DNS setup.
The correct way to handle this is to use a separate sub-domain for your internal AD setup. Something like
mydomain.comfor the public IP domain name andinternal.mydomain.comfor the Windows AD network in RFC1918 space. That can work. A quick Google search will lead you to a Microsoft best practices and how-to article on this configuration. I highly recommend you restructure you AD configuration to match what is described at this older Microsoft link here: https://social.technet.microsoft.com/wiki/contents/articles/34981.active-directory-best-practices-for-internal-domain-and-network-names.aspx. And here is a slightly newer document showing the same thing: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc772970(v=ws.10).My older post you referenced was assuming the network was IPv4 only with no IPv6 in use. You want to use IPv6, but your ISP is not guaranteeing you a static assignment (they use prefix delegation which means the IPv6 space might change unexpectedly). That's going to be an issue unless you use both ULA and GUA IPv6 addresses. My post also assumed that your Active Directory domain was never going to be accessed from outside. Sounds like that is not what you intend as you mentioned somewhere up above about using some type of home automation with LDAP authentication I believe (unless I'm confusing this thread with another one).
-
@bmeeks said in Why do I have to 'Track Interface' on LAN to WAN for IPv6 to work?:
The correct way to handle this is to use a separate sub-domain for your internal AD setup. Something like mydomain.com for the public IP domain name and internal.mydomain.com for the Windows AD network in RFC1918 space. That can work. A quick Google search will lead you to a Microsoft best practices and how-to article on this configuration. I highly recommend you restructure you AD configuration to match what is described at this older Microsoft link here: https://social.technet.microsoft.com/wiki/contents/articles/34981.active-directory-best-practices-for-internal-domain-and-network-names.aspx. And here is a slightly newer document showing the same thing: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc772970(v=ws.10).
Thanks for the links - one of them I had looked already (as a Google search pointed to it). My public domain name has a - {dash} in it, and apparently my old ass NAS does not like that. I have tried and tried to get it to recognize the domain-name that I first setup as ad.{mypublicdomain} - even a chat session with them for over an hour (nothing worked - they plan no updates to it. It also only does CIFSv1/SMBv1 - FTP (no sFTP) and NFS (but only to Linux boxes) - and some form of iSCSI. I have over 6TB of files and stuff on there, and they "SEAGATE" is not even willing to 'help' me with another NAS to replace it. One of my IT buddies said I should use {mypublicdomain}.loc for my AD/DS...but still going to resolve the - {dash} in there unless I remove it completely. I have considered creating (renaming my public-facing-domain) as only HomeAssistant uses it (well their app on my phone and the ALEXA and GOOGLE links do too).
My older post you referenced was assuming the network was IPv4 only with no IPv6 in use. You want to use IPv6, but your ISP is not guaranteeing you a static assignment (they use prefix delegation which means the IPv6 space might change unexpectedly). That's going to be an issue unless you use both ULA and GUA IPv6 addresses. My post also assumed that your Active Directory domain was never going to be accessed from outside. Sounds like that is not what you intend as you mentioned somewhere up above about using some type of home automation with LDAP authentication I believe (unless I'm confusing this thread with another one).
Pretty much what I am going to. Every guide that I have read says not to DISABLE the IPv6 on a DC. I am going to leave it at its default settings and let pfSense take care of it. Same for DHCPv4 - going to only do DNS on AD/DS and I am guessing that pfSense is RESOLVER with the FORWARDING option turned on. I would also need a Domain Override setup to point to AD/DS name and IPv4 address as well. Still trying to grasp the REV LOOKUP (setup in pfSense) thing and the HOST OVERRIDE too.
The LDAP stuff that I want to do is not really for Home Automation, per se. I do have HomeAssisitant - what I want to do is sign-ins to the various parts with LDAP credentials so that I do not have to keep up with (currently 22) separate login accounts. All of that stuff is 'inside' my pfSense Firewall - only Alexa and Google can access from outside and their app. I got that working, and hoping that I do not have to go through that again. WHEW!!!