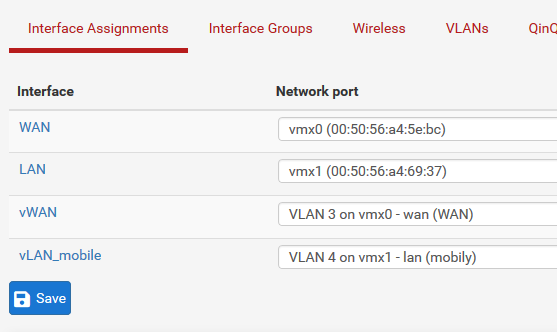
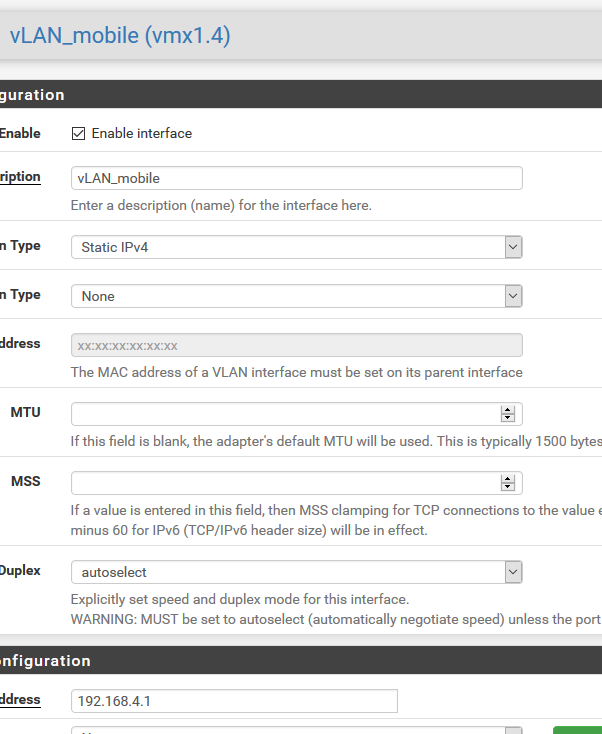
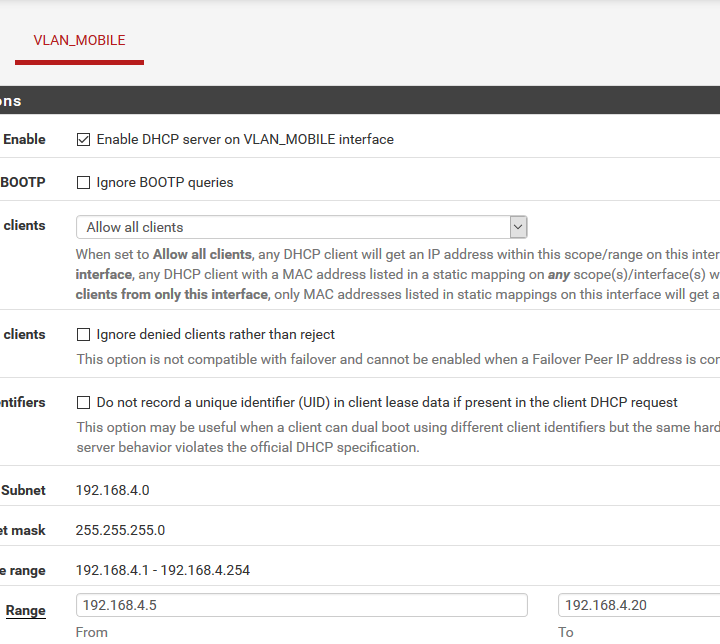
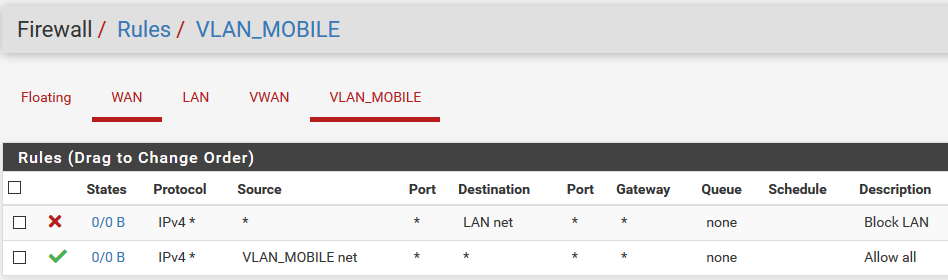
VLAN not getting internet access
-
@Octopuss said in VLAN not getting internet access:
but I cannot specify a VLAN or anything.
You show port 28 tagged on vlan 4.. If you want vlan X also tagged on port 28 then open up vlan X and set it to be tagged on port 28 as well..
Here like this cheap switch... for vlan 3! see the box were I set 3 - I can then put a port as either tagged or untagged on vlan 3..
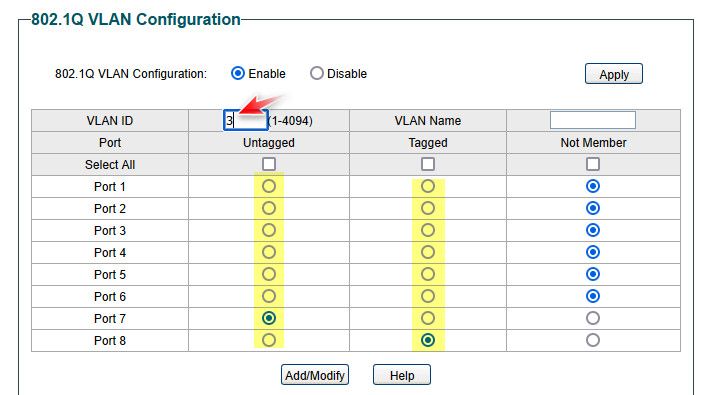
You don't understand
I have been working with vlans since they have even been a thing... I am quite sure I understand how vlans work ;) hahahaha
-
@johnpoz I meant you didn't understand what I didn't understand. lol
This is probably an extremely simple thing from technical point of view, but different wording across different interfaces and different ways to explain it just prevents me from understanding it.I will have another coffee and try to read it all again. I really feel like an idiot over what's a one click in a GUI somewhere. I mean, jesus.
-
@Octopuss on your switch - how did you get to vlan 4..
Click whatever port you want the vlan 4 to be untagged or tagged in..
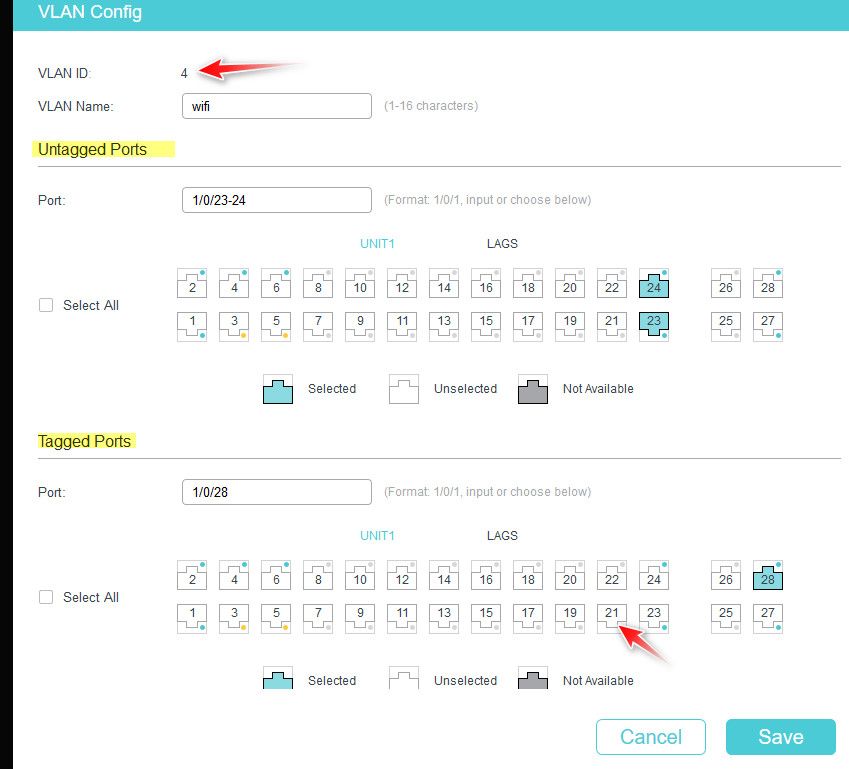
Say for example you wanted vlan 4 to be also tagged on port 21.. Click that little icon.
If you want to edit vlan 3.. Then call up that vlan 3 on your switch and click the buttons you want vlan 3 to be untagged or tagged in.. Or edit the listt port box to do the setting for you..
See how untagged you show 1/0/23-24, and tagged you show 1/0/28 in the boxes
-
@johnpoz Oh you know what? I AM an idiot. I wasn't thinking in the correct direction, or maybe thinking at all and overcomplicating it.
All I'm doing is adding frigging VLAN 4's tag to port 28, and it does not matter what VLAN 28 is in.All the stupid articles I tried reading that were numerous pages long confused the hell out of me and I couldn't think in a simple way. OMG!
edit: Yep, I was kind of thinking about it backwards: Last question is, why do I have to have a tagged port from VLAN 2 (Where pfSense is) in VLAN 4? What a simple shit and I just couldn't wrap my head around it.
-
@Octopuss said in VLAN not getting internet access:
I couldn't think in a simple way.
Which is why I tried to use the envelope example.. Once it clicks yeah you will feel stupid for not getting it before ;)
-
@johnpoz Now I just have one more VLAN-related question: shall I use the default VLAN 1 at all or not? I googled up conflicting suggestions.
-
@Octopuss So it is common practice in an enterprise to not use the default vlan 1.. But this is more about preventing mistakes, etc..
There is really no reason why you can't just use the default vlan 1 in your network. For example vlan 1 would be fine for just the native network you put on your "lan" interface that is connected to your switch.,.,
-
@johnpoz I read some posts/articles about how it behaves differently or something and you must not use it or else... something like that.
-
@Octopuss Where did you read this - the default vlan is where control is.. In a home/smb this is not going to be an issue. when you have normal user traffic on vlan 1, user broadcast and multicast traffic could be processed by the supervisor.. Its not going to be a big deal in a small network that is for damn sure..
If you don't want to move user data over the default vlan than don't, but in home setup its not going to be an issue..
-
@johnpoz I don't know. Random sources over time. Something along the lines of default (undeletable) VLAN always having access somewhere or something. Something not being able to be configured about it, etc. I mean, I don't know! Networking is one of those thing I should have never touched, but I'm stuck with the server (and I'm not going back to Synology boxes either, which is one of the reasons why I originally started building all this).
-
@Octopuss again if you have concerns don't use it for user data.. Only use it for management. You can't really disable vlan 1, you can change it on some switches like cisco. But you can not really disable the management vlan. You can remove it from ports you don't want it on, etc.
It is not a real concern in a home network that is for damn sure..
-
@johnpoz Oh it's not that I care, I'm just curious what is it really about, or if there's anything to those claims (but I presume it's very switch-dependant anyway)
-
@Octopuss again control is used..
here is example of some control info
If you want to get into some weeds about layer 2.. Here is a really old presentation, 20 years.. That goes over some of the attack vectors on layer 2
https://www.blackhat.com/presentations/bh-usa-02/bh-us-02-convery-switches.pdf
Are you really concerned with a vlan hop attack on your network, or any of the others things mentioned in it?
If your concerned then don't use the management vlan of the switch for anything other than management. Put all your user data on another vlan. But if you want to actually manage the switch, something is going to need to talk to it on the management vlan ;)
edit: For example what I did, I changed the management vlan ID to 9 on my cisco switches to be inline withe the IPs I use on it 192.168.9.0/24 - the only devices in this network are my PC, and my nas.. And then the switches on my network management.
All other devices, iot, wireless networks, my rokus/tvs/etc are on other vlans. And I also from habit any and all ports not actively used are put into a unused vlan.. Notice that vlan 10 from my post above.
Now sure I could move my pc and nas to something other than the switches management vlan (1 by default).. But as I said is not normally a concern in home or your typical smb network.
-
@johnpoz said in VLAN not getting internet access:
@Octopuss again if you have concerns don't use it for user data.. Only use it for management. You can't really disable vlan 1, you can change it on some switches like cisco. But you can not really disable the management vlan. You can remove it from ports you don't want it on, etc.
It is not a real concern in a home network that is for damn sure..
Let me come back to this post for a second - what do you mean to use it for management?
-
@Octopuss Don't put any devices on that network other than your Admin PC or laptop or phone, etc.. Ie that is say the network you could talk to the pfsense web gui from..
My 192.168.9.0/24 which is the default vlan on the switch, I just changed it from ID 1 to 9.. is my management/trust network.. My box is on it, an my nas.. This is the network my 3 switches management IPs are on, via their default vlan..
All my other devices - lets call them "users" on on other vlans - which are not the default vlan of the switches, etc. Tvs, printer, iot stuff like all my lightbulbs, my garage door opener, my thermostat, etc.. all on different vlans.. Not even the same vlan.. I have a roku vlan - which is TVs, rokus, directTV box, etc. Then there is an iot vlans where like my lightbulbs and thermostat and alexas are on, etc.
Trusted wifi devices, are on a different vlan all together. Then there is a "guest" wifi, etc again a different vlan.. None of those vlans are the default vlan of the switches..
The default vlan of the switch is what I call my management/trust/infrastructure vlan, etc. If you really wanted to get paranoid - you don't have to put anything on it.. Other than the switches management IPs, which you could allow other devices from other vlans to get to..
A layer 2 switch is normally not going to let you put an IP on another vlan (SVI) that you could access its management functions from. None of the entry level switches for sure would even allow you to change the ID of the default vlan, or create a svi on another vlan, etc. So if you want to "manage" that switch your going to need to be able to get to that vlan, even if you don't have any other devices on it other than that switch or other switches, etc.