VLAN can not ping gateway
-
running pfsense 2.7.0 and have it setup with LAN 172.16.5.0/24, VLAN10 172.16.10.0/24 and VLAN100 172.16.0.0/24 and it is connected to a an L2 switch, which is setup on LAN 172.16.5.10. Switch has GW of 172.16.5.1. On the pfsense the VLANs hang off of the LAN interface, and shows that way in routing. the LAN, VLAN10 and VLAN100 all have allow all in FW rules and all 3 have DHCP setup. Odd part is that none of the vlan devices can ping their gateways. Everything in LAN (172.16.5.0/24) works fine, but the VLANs can not ping their own GWs (172.16.10.1, 172.16.0.1). From the switch I can ping everything, but why can't devices in VLANs, which get the correct DHCP address, can not ping their own GW ?
-
@jebzit so you want to route these vlans on your switch? Why would you create them in pfsense then? You would only create vlans in pfsense when they are directly attached.
if its a L2 switch, its not going to do any routing.
-
@johnpoz the vlans were setup on the pfsense in a router on a stick fashion, the L2 switch had the trunk interface to pfsense, and the interfaces for the devices were placed in their corresponding vlan. For device in vlan 1, everything worked, vlan 10 the device got dhcp address from pfsense as configured, but could not ping its own gw, same with device plugged into interface set as vlan 100. The switch had a mgmt address in vlan 1 so I can sign on to it. From this cli, I could ping all the gw - vlan 1, 10 and 100
-
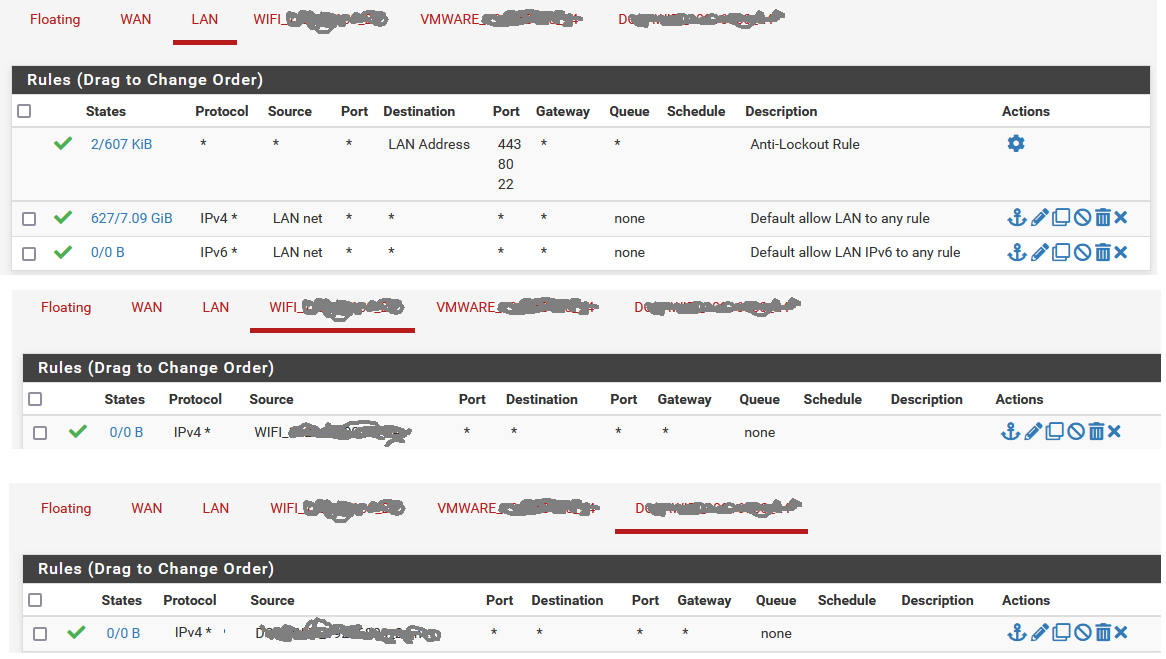
@jebzit Check the rules. Be sure they are not protocol TCP only or some other common mistake. You might want to post a screen shot here.
-
-
@jebzit said in VLAN can not ping gateway:
From the switch I can ping everything
the L2 switch had the trunk interface to pfsenseIf the switch really was configured only for L2 the ping to the devices would have to pass pfSense in both directions. Means, the devices has to route the responds to their gateways.
But I suspect, this is not the case and the switch is not configured properly.
Maybe it's just leaking L2 traffic.You can sniff the traffic on pfSense to investigate this. If there is nothing, what I assume, the switch doesn't work properly.
-
@jebzit well you have hidden the source on your rules - so can not tell if that is "net" or "address"
I don't see any evaluations on the rules - so maybe you have it set to address vs net, which would never trigger.
On any interface, the source of the traffic would be net of whatever that network is.
A simple way to validate if a rules thing or downstream thing - would be to sniff (packet capture via pfsense diag menu) on that interface for icmp and then ping pfsense IP address on that interface from a client in that network.
-
@jebzit Did you find a solution to this issue? I'm having the exact same issue with my pfSense box and Cisco 2960x Switch.