Establish openVPN tunnel from remote
-
Hi, I'd like to have a list of the steps necessary to make it possible to establish an openVPN tunnel from a remote network in presence of multiple subnets on openVPN server side. I've seen this topic but I think a more structured post would be useful.
The typical scenario would be the following, with B being a network provided of a public IP address:
openVPN client on LAN-A1 --- GATEWAY/FIREWALL-A --- internet --- GATEWAY/FIREWALL-B --- LAN-B1 --- LAN-B2 --- pfSense openVPN server --- LAN-B3Let's suppose VPN is correctly configured on openVPN server, i.e. it is possible to establish an openVPN tunnel from a client located in LAN-B2. What is missing is the set of rules to enforce in network B to make it possible to reach openVPN server from a remote network.
From what I've understood, the following steps must be carried out on network B configuration:
- openVPN traffic must be allowed to and from openVPN server address (the device WAN port) in the whole network B. Tipically, this means allowing UDP traffic on port 1194.
- openVPN traffic must be forwarded to openVPN server address (i.e. the device WAN port IP address).
- There must exist in network B routing rules allowing network B devices to reach openVPN server
- There must exist in network B routing rules allowing openVPN server to reach network B gateway/firewall.
- openVPN server needs to be able to communicate through internet
Is this correct? are all of these steps required? are they precise enough? if not, could you please specify them better?
Thanks,
Alessandro -
@AMartinelli
What is your goal? Which devices should be able to communicate across the VPN?And this part is not clear:
-- LAN-B1 --- LAN-B2 --
Does this mean, you have two different LAN subnets between the internet gateway and the OpenVPN server? If so I would expect that there is a router in between.
-
@viragomann you're right, I was not clear enough. I try to re-write the question in a more clear way.
Scenario:
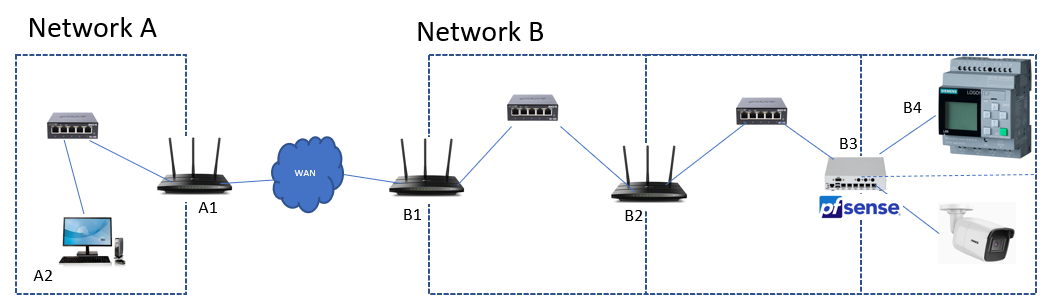
where B is a network provided with a public IP address, pfSense is the device where the openVPN Server is running and A2 is a PC where OpenVPN client is running and wants to access subnets behind the pfSense, like B4.
Assuming that the openVPN Server is configured correctly, I'd like to fully understand which are the steps to be carried out to configure network B to allow the VPN tunnel to be established. From my understanding, the steps should be these ones:
- openVPN traffic must be allowed to and from B3 WAN port in the whole network B. Tipically, this means allowing UDP traffic on port 1194 for B3 WAN IP address.
- openVPN traffic reaching B1 must be forwarded to B3, more specifically to its WAN port IP address.
- There must exist in network B routing rules allowing network B devices (in this example B1 and B2) to reach B3 WAN port.
- B3 needs to be able to communicate through internet
-
@AMartinelli said in Establish openVPN tunnel from remote:
From my understanding, the steps should be these ones:
openVPN traffic must be allowed to and from B3 WAN port in the whole network B. Tipically, this means allowing UDP traffic on port 1194 for B3 WAN IP address.Since B3 is the server, it is sufficient to allow the OpenVPN traffic (e.g. port 1194) to B3. The OpenVPN server itself doesn't initiate a connection on its own.
openVPN traffic reaching B1 must be forwarded to B3, more specifically to its WAN port IP address.So you have to forward UDP 1194 to B3.
As ist seems B2 is also a router in between, you have to forward it on B1 to the WAN port of B2, and on B2 to B3.There must exist in network B routing rules allowing network B devices (in this example B1 and B2) to reach B3 WAN port.If you only need to access B4 devices as you stated above, there are no routes needed for the other networks.
I assume, you have stated the LAN address of B2 as the WAN gateway on pfSense in the interface settings. If this is the case, pfSense nats outbound traffic on the WAN to its interface address.
If the VPN is for your own private purposes, what I assume, this would be fine and you would also be able to access B2 without the need of a static route. However, since B1 is behind a router from the point of pfSense you would need to add routes to access this subnet.In either case, you need to enter all subnets you want to access (B1, B2, B4) from the remote site into the "Local Networks" box in the OpenVPN server settings.
Maybe the B4 devices need additional settings to allow access from outside of their subnets, if it's even possible. At least, they need to have the pfSense LAN IP as their default gateway.
Try to access them from B2 to check this.B3 needs to be able to communicate through internetThis is not necessary to connect to the OpenVPN server, however, it is for installing packages and updates on pfSense.