Wan port blocking internet access
-
I have a problem with our third router of which I would like a resolve. the original Protectli (The Vault) router PfSense software crashed and it was replaced with a new one. Configurations were copied from one of the existing routers and loaded on to the new one. All went well after assigning the ports to their respective IPs. The Wan was set to one of the available static IPs provided by Comcast. The fire wall rules were left at defaults. No Connection to the internet at this point. it was not until an ICMP ping rule was applied to the Wan port and it wouldn't work unless the source is set to ANY.
I have a problem with that and don't want to have it this wide open. what is bothering me is that we did not have to create such a rule on the 2 other functioning routers. what am I missing?
and Yes I am new to the vault and PfSense. -
@ama said in Wan port blocking internet access:
The Wan was set to one of the available static IPs provided by Comcast
A static IP setup needs 3 details.
The IP in question.
The mask or network, like /32 or 255.255.255.255
The gateway, an IP also - this is the one you nevr set on a LAN type interface, but have to set on a WAN type interface.So, you mentioned the first - what about the others ?
"DHCP" on WAN doesn't work for your ISP ?
You have to add an ICMP rule on WAN .... can you show that rule ?
You were sending your ping command from where, to who ?What what it's worth : I confirm : most pfSense setups work great without ever needing to add a rule on the WAN interface. This interface normally has no rules what so ever.
As these rules are need if you need traffic to come in from the Internet somewhere in your local networks, or pfSense itself.
-
@Gertjan
The IP in question.
The mask or network, like /32 or 255.255.255.255
The gateway, an IP also - this is the one you nevr set on a LAN type interface, but have to set on a WAN type interface.
I have that base covered. Static IP provided for the Wan interface, the provider's subnet and gateway.@Gertjan said in Wan port blocking internet access:
So, you mentioned the first - what about the others ?
%(#000000)[I actually uploaded the configuration of one to the problem one(IPs were modified accordingly). it still did not do me any good.]@Gertjan said in Wan port blocking internet access:
You have to add an ICMP rule on WAN .... can you show that rule ?
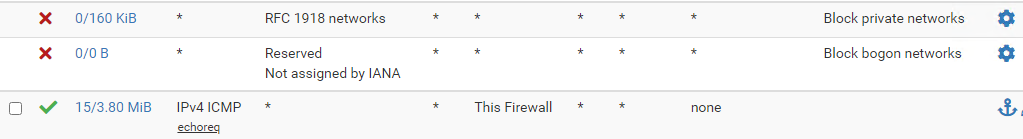
@Gertjan said in Wan port blocking internet access:
You were sending your ping command from where, to who ?
I didn't no have to. I was searching up online trying to figure out why I am unable to get internet access and came across an article that led me to try this rule. it did not make any sense to me but was the sure cure on first try.
@Gertjan said in Wan port blocking internet access:
What what it's worth : I confirm : most pfSense setups work great without ever needing to add a rule on the WAN interface. This interface normally has no rules what so ever.
Thank you. agreed on almost all routers. you just need the basics. The rest is optional and customizable.
@Gertjan said in Wan port blocking internet access:
As these rules are need if you need traffic to come in from the Internet somewhere in your local networks, or pfSense itself.
This is where it is a bit confusing. The router is doing DNS and Comcast is Secondary. all other use VPN for access to resources behind the firewall. -
This
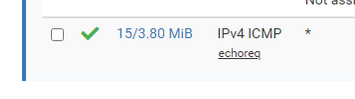
is just incoming ICMPv4 traffic/packets - not your traffic goint to the "Internet" and coming back.
Look at my ICMPv4 WAN rule :
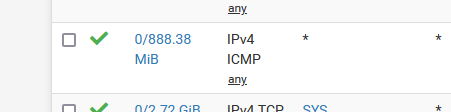
This can only be incoming ICMPv4 traffic and is not related to my ordinary "LAN to Internet (and back)" traffic
Wan port blocking internet access
The subject line is awkward.
Router firewall pfSense interfaces can block incoming traffic.
Look (physical) at the WAN port, or any other (LAN) port.
Firewall rules apply to traffic going into (into pfSense), not at traffic that comes out of the interface.
What boils down to : WAN firewall rules - or the absence of - can't block "internet access".
Only the "Floating" interface has that power.Anyway, all this just to be sure, you probably know already all this.
Next thing to check :
System > Routing > Gateways is ok ?
The routing table ( Diagnostics > Routes ) looks ok ?