Allowing only LAN users while blocking all others.
-
I'm looking to configure my HAproxy to only allow access to specific services for local LAN users. Despite trying various ACL configurations, I haven't been able to achieve the desired outcome. Does anyone have a sample configuration to restrict site access exclusively to users within the 192.168.0 network?
I assume this should be implemented within the backend configuration, particularly in the Access Control Lists and Actions section. Is my understanding correct?
I'm grateful for all the suggestions, tips, and ideas that have been shared to help me work towards a solution. Thank you!
-
@tomasenskede quite simple. There’s an option to use an Alias when building the ACL. I utilize this when wanting to keep certain resources available only to my net admin vlan
-
@tomasenskede who are you wanting to block exactly? For example if you don't want public to get to it, why would you even have it listen on your wan, or why would you create the firewall.
If you don't want some other local network to use it, just block that network or IP from talking to the frontend IP and port.
-
@johnpoz I think it all depends on what the network looks like if a firewall ACL is practical.
So for example my HA Proxy listen IP on the LAN is 192.168.50.250. All my internal services sit behind that VIP. That means if i have lets say dns.example.com and password.example.com there is no way to block users to the specific service using pf rules (actually as im writing this you could by putting the hostname in the source field). Another way is to use the built in feature to use an Alias within HA Proxy which would be my preference as you dont need to update multiple interfaces (assuming a routed network or vlans) and just update the Alias.
Different ways to cut up an onion i suppose -
@michmoor Yeah I agree there would be times where you would want/need to use the acls in a specific setup, and even limit or allow on source IPs, etc.. Not saying its not a viable tool to use when circumstance warrants it.
I am just curious in this scenario.. If I only want locals networks or IPs to use my haproxy - why would I even allow public to talk to it in the first place. Or if only want specific locals to access it, then again its quite possible could just be done with firewall rules..
Different ways to cut up an onion i suppose
Or skin the cat for sure - but if you don't know the breed of the cat, you can't actually determine all the ways to skin it.. Or which way might be the easiest ;)
-
Alias here?
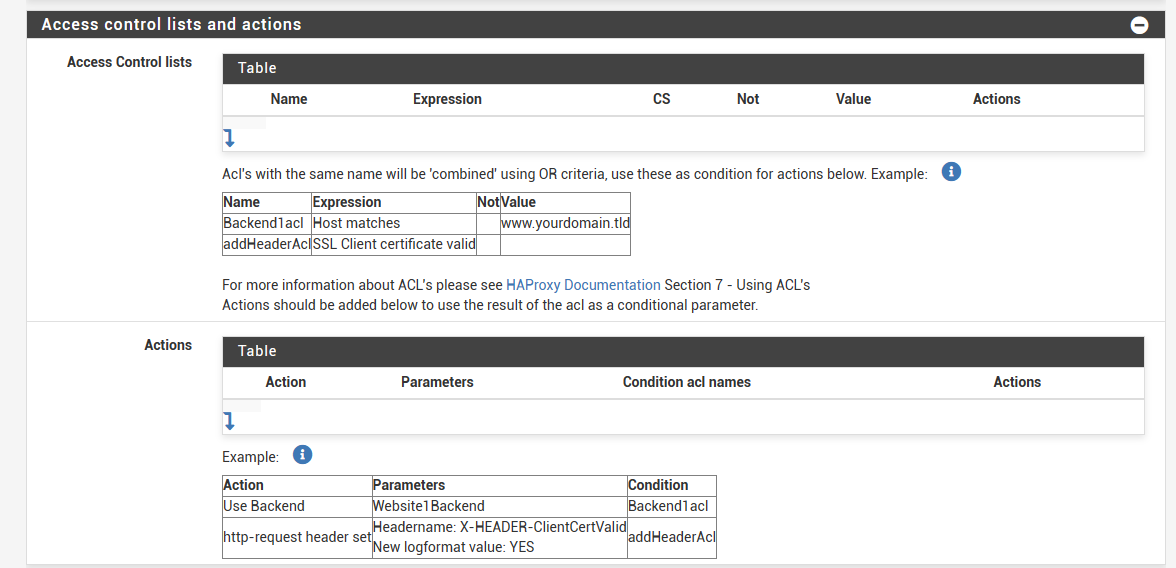
-
@johnpoz said in Allowing only LAN users while blocking all others.:
@michmoor Yeah I agree there would be times where you would want/need to use the acls in a specific setup, and even limit or allow on source IPs, etc.. Not saying its not a viable tool to use when circumstance warrants it.
I am just curious in this scenario.. If I only want locals networks or IPs to use my haproxy - why would I even allow public to talk to it in the first place. Or if only want specific locals to access it, then again its quite possible could just be done with firewall rules..
Different ways to cut up an onion i suppose
Or skin the cat for sure - but if you don't know the breed of the cat, you can't actually determine all the ways to skin it.. Or which way might be the easiest ;)
I have multiple services that I make accessible through HAproxy, and they function well. However, there are several services that I prefer not to make public, and I'd like to restrict access to them to only the LAN-side, rather than the WAN-side.
-
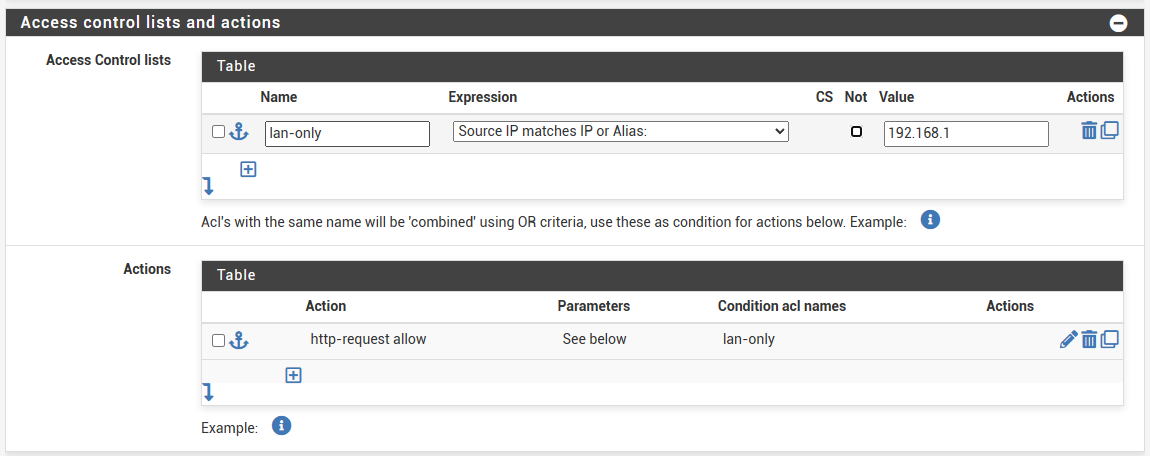
This isn't functioning correctly. Am I heading in the right direction?