Lets encrypt on my captive portal
-
Hello.
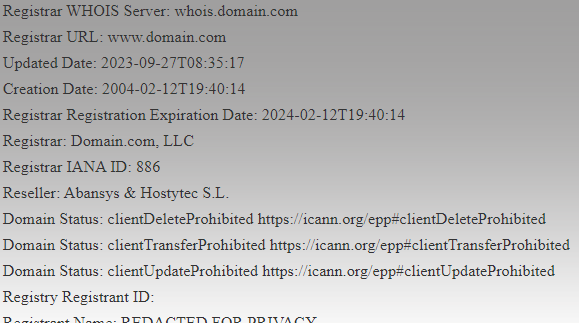
I have a domain on the Internet with my provider in the form www.mydomain.com. My provider uses lets encrypt to generate it and I cannot access it via ssh but I can access it via plex panel. The idea is to be able to use the certificate in the captive portal of my red interior to avoid the certificate security notice displayed by browsers.I have installed acme on pfsense 2.6 and tried to configure it but I can't. In my provider's DNS zone configuration. I see:
www.mydomain.com. CNAME mydomain.com.
_acme-challengemidomain.com. TXT "nGflrSkiJMXNfKebTll_5xLZ9JC-do-7PF3KXht7qVs"What would be the procedure to configure it correctly and update it automatically every 3 months?
-
@jperezme said in Lets encrypt on my captive portal:
n my provider's DNS zone configuration. I see:
www.mydomain.com. CNAME mydomain.com.
_acme-challengemidomain.com. TXT "nGflrSkiJMXNfKebTll_5xLZ9JC-do-7PF3KXht7qVs"Normally, you wouldn't be able to see DNS record.
If acme + the selected DNS-api is able to "add" a TXT record, like_acme-challenge.mydomain.com TXT "nGflrSkiJMXNfKebTll_5xLZ9JC-do-7PF3KXht7qVs"You should be able to 'dig' it
dig _acme-challenge.mydomain.com TXTIf acme was able to add the TXT record, it will also 'delete' the record right after Let's encrypt did the check (it use a sub domain "_acme-challenge" lookup, like "dig"). The record would be delete if success, or error.
Btw : when the transaction start, acme asks Letencrypt for a random TXT value. That value has to be stored by 'acme' into the TXT record on your DNS server.
Letsenscrypt will then question your dns server.
If the TXT is found, then that proofs you have access to that domain DNS server = you "own" (rent) that domain.See here : Let's encrypt Challenge types.
Take note "_acme-challengemidomain.com" is wrong.
Check this file :
/tmp/acme/[domain-name]/acme_issuecert.log
as it contains all the details about what acme is doing.@jperezme said in Lets encrypt on my captive portal:
update it automatically every 3 months?
I advise you to use 60 days or so.
If something goes wrong after 90 days, you have 0 days to resolve the issue. -
@Gertjan
Thanks in advance.
I used DNS-Manual to create it. In this way, will the certificate be automatically renewed every 60 days? -
@jperezme said in Lets encrypt on my captive portal:
I used DNS-Manual to create it. In this way, will the certificate be automatically renewed every 60 days?
Manual is to opposite of automatic

Manual is good for the nerd that want to the the "rocket science" themselves.
If your domain registrar is on this list and you can find the correct acme DNS API :
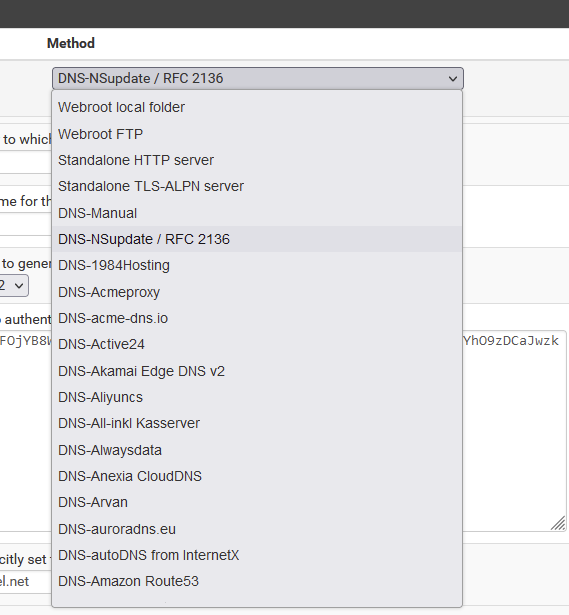
edit :
Better safe then sorry : Set DNS-Sleep to 120 seconds or more.
-
@Gertjan
My domain registar is not on that list. -
@jperezme said in Lets encrypt on my captive portal:
My domain registar is not on that list.
The list represents the methods.
Check with your registrar what method they propose.
Who is it ? -
-

If domain.com is your registrar, all I (not me, I use Google, so blame them if I'm mistaken) could find is :
https://www.domain.com/help/article/enable-your-free-ssl-certificate
and that means : If you have a domain name with them, you can activate a free "Letsencrypt" certicate for your site (hosted on their equipment). You probably can't download the certificate files.
Also : when you rent a domain name, and you want to use it for your local captive portal so login takes place using an url like https://portal.your-local-site.tld then you shouldn't use the "your-local-site.tld" domain name on the Internet. It still exists on the Internet, of course, as you rented it.Example.
I have a hotel, which means clients are always asking : what is your hotel's Wifi ?
I have a domain name, "bhf.net" which I use for my LAN devices, and my captive portal, so I can support the https login page for my portal.
The acme pfSense package handles the wild card domain "bhf.net" renewal every 60 days.
I had also declared "portal.bhf.net" (added to the Resolver page : Host overrides) "portal.bhf.net" where it points to 192.168.2.1, which my pfSense captive portal dedicated interface.On the captive portal settings page, I select this :
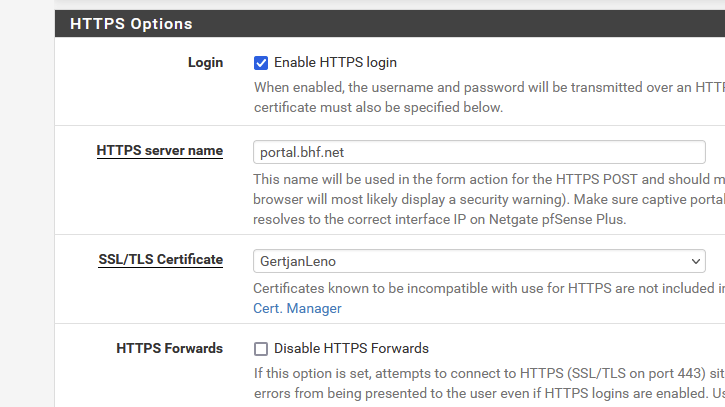
and done.
The pfSense GUI web server uses the same certificate, so https access for the GUI is now also set up.
-
@Gertjan
I still don't understand how I can tell Acme when I create the certificate which DNS method to use.
I have created in DNS to resolve the entry portal.midominio.com pointing to the address 172.16.30.1, which is the IP of the captive portal.
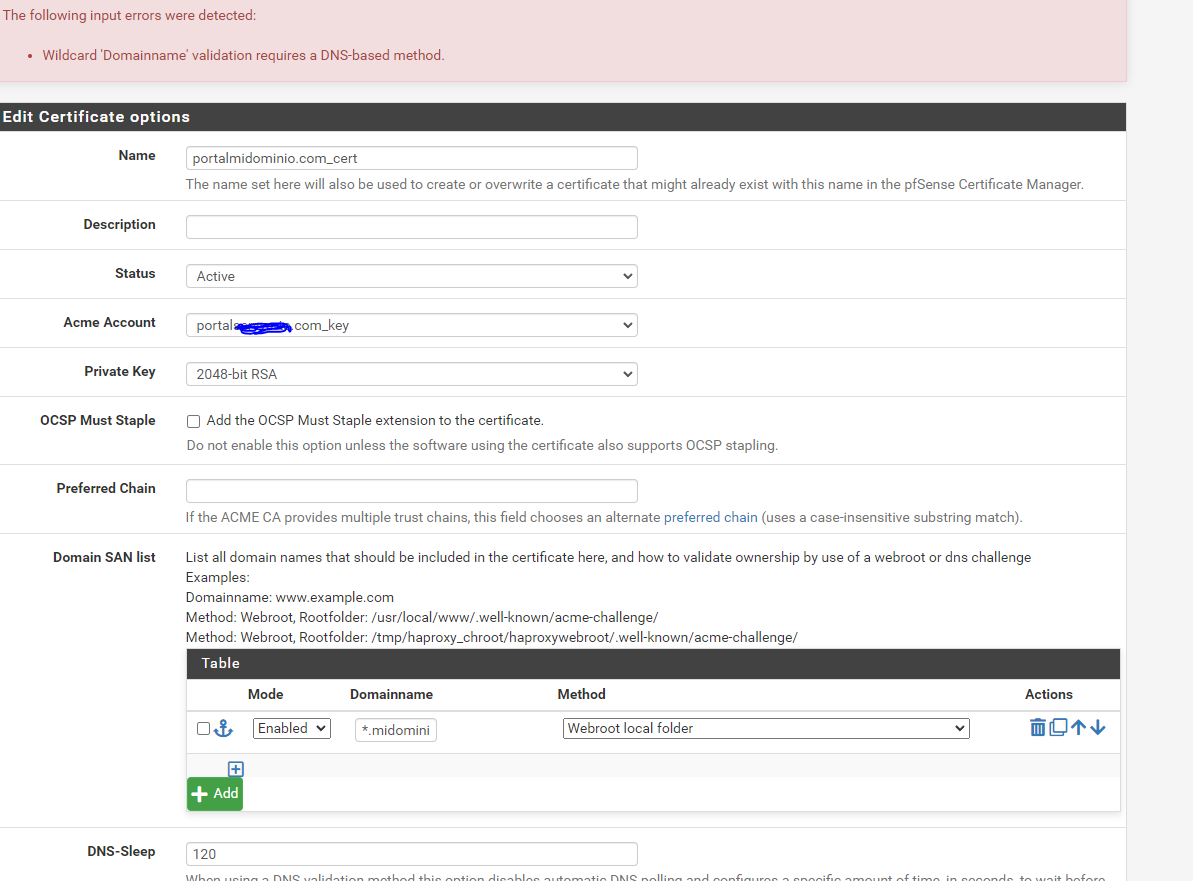
-
That's a wild card.
These are the "rules" :
You have to do this :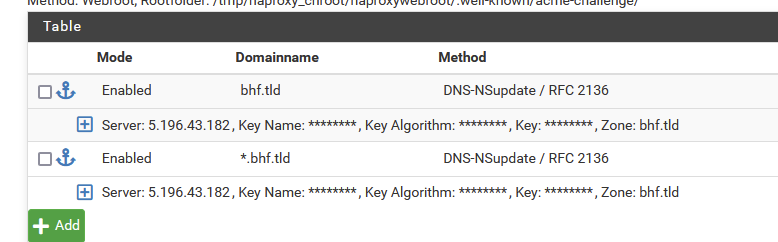
add two domainname's - as shown in the image.
One with the domain name only, the other with a *. in front of it.And, as mentioned here : Let's encrypt Challenge types :
DNS-01 challenge
This challenge asks you to prove that you control the DNS for your domain name by putting a specific value in a TXT record under that domain name. It is harder to configure than HTTP-01, but can work in scenarios that HTTP-01 can’t. It also allows you to issue wildcard certificates.
HTTP-01, like your selected webroot method, can't.
-
I have used wild card because you told me previus message i only need works with portal.midominio.com
I suppose i ddn't understand you. -
Methods used, wildcards etc, don't forget to watch the movie.