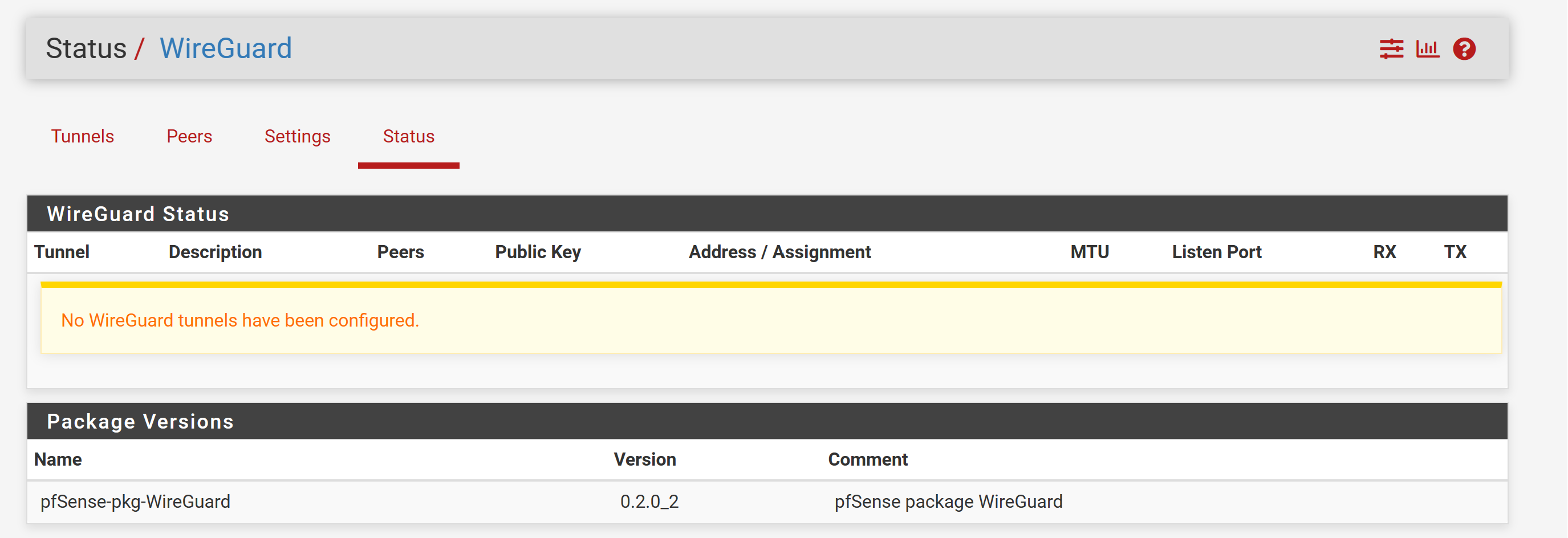
PIA using pfSense WireGuard Package
-
Re: PIA on Wireguard
I have 4 PIA VPN connections I have setup for various reasons on using the OpenVPN package in pfSense+ for policy based routing but would like to transition to WireGuard as it seems to be a better VPN protocol.
Is it possible using the WireGuard Package in pfSense+ and, if so, can someone provide a setup that I could follow?
Thanks.
-
@FCS001FCS said in PIA using pfSense WireGuard Package:
I have 4 PIA VPN connections I have setup for various reasons on using the OpenVPN package in pfSense+ for policy based routing but would like to transition to WireGuard as it seems to be a better VPN protocol.
Not necessarily. Many Privacy-VPN-Providers only support a WireGuard config which won't allow more than one connection at a time. So my advice, stick with OpenVPN.
-
@Bob-Dig said in PIA using pfSense WireGuard Package:
@FCS001FCS said in PIA using pfSense WireGuard Package:
I have 4 PIA VPN connections I have setup for various reasons on using the OpenVPN package in pfSense+ for policy based routing but would like to transition to WireGuard as it seems to be a better VPN protocol.
Not necessarily. Many Privacy-VPN-Providers only support a WireGuard config which won't allow more than one connection at a time. So my advice, stick with OpenVPN.
FWIW - PIA advertises unlimited number of connections and never stated that is only limited to OpenVPN. The PIA App for Windows, IOS and Android has WireGuard as an option and multiple WireGuard connections can be made on one account.
-
Refs: 1. - PIA on Wireguard - 2022 NetGate thread on "PIA on Wireguard"
------2. - https://github.com/hsand/pia-wg
------3. - https://github.com/pia-foss/manual-connections
------4. - https://github.com/glorious1/manual-connectionsThe question still stands:
Has anyone been able to setup Private Internet Access (PIA) VPN Provider to use the WireGuard Protocol in pfSense 23.09-RELEASE (amd64) for a SG-2100 (or 2.7 CE) with either the pfSense WireGuard Package 0.2.0_2 (preferred) or using some scripts as explained in the GitHub links referenced above?
If so, can you provide a setup instruction that a non-expert in Linux could follow?
Thanks.
-
In case anyone still wants to do this, I was able to configure my pfSense to connect to PIA using WireGuard.
Steps:
1 - Use scripts from https://github.com/pia-foss/manual-connections to connect to PIA. Just clone the repository and run ./run_setup.sh2 - Follow the setup steps from #1 and the scripts will generate a file: /etc/wireguard/pia.conf
3 - Open this file on a text editor. You will find the following information for you to configure your WireGuard tunnel and peer through the pfSense Web UI:
[Interface]
Address: 10.1.149.3 (or whatever is in your pia.conf). You must use this address on a NEW pfSense interface you must create (make sure to select static IP address for it) which is associated with the WireGuard tunnel.
PrivateKey: xxxxxyuyyyyyyxxxyxyxyxyx --> you will use this during the creation of the new WireGuard tunnel in pfSense. Enter this on "Interface Keys / private key"[peer]
PublicKey: xhxhxhxhxhxhxhxhxxhxh --> copy and paste this to a new peer you're associating with your newly-created WG tunnel
AllowedIPs: 0.0.0.0/24 --> copy/paste on your new peer
EndPoint: somePIA-FQDN.com:1337 --> copy and paste this to your new peer. Make sure you de-select dynamic endpoint4 - You need to configure outbound NATs on pfSense using the new interface for all traffic from 192.168.1.1/24 (or whatever your LAN network address is)
5 - You need to configure a new gateway for your new interface.
6 - Use policy routing to route all traffic from your LAN (or desired network) to the newly-created gateway from #6.
Hope this helps, it's working for me. With WireGuard I can get 900mbps down and up from PIA, rather than the ridiculous 300mbps I was getting with OpenVPN connected to the same servers.
-
@eidi said in PIA using pfSense WireGuard Package:
In case anyone still wants to do this, I was able to configure my pfSense to connect to PIA using WireGuard.
Steps:
1 - Use scripts from https://github.com/pia-foss/manual-connections to connect to PIA. Just clone the repository and run ./run_setup.sh2 - Follow the setup steps from #1 and the scripts will generate a file: /etc/wireguard/pia.conf
3 - Open this file on a text editor. You will find the following information for you to configure your WireGuard tunnel and peer through the pfSense Web UI:
[Interface]
Address: 10.1.149.3 (or whatever is in your pia.conf). You must use this address on a NEW pfSense interface you must create (make sure to select static IP address for it) which is associated with the WireGuard tunnel.
PrivateKey: xxxxxyuyyyyyyxxxyxyxyxyx --> you will use this during the creation of the new WireGuard tunnel in pfSense. Enter this on "Interface Keys / private key"[peer]
PublicKey: xhxhxhxhxhxhxhxhxxhxh --> copy and paste this to a new peer you're associating with your newly-created WG tunnel
AllowedIPs: 0.0.0.0/24 --> copy/paste on your new peer
EndPoint: somePIA-FQDN.com:1337 --> copy and paste this to your new peer. Make sure you de-select dynamic endpoint4 - You need to configure outbound NATs on pfSense using the new interface for all traffic from 192.168.1.1/24 (or whatever your LAN network address is)
5 - You need to configure a new gateway for your new interface.
6 - Use policy routing to route all traffic from your LAN (or desired network) to the newly-created gateway from #6.
Hope this helps, it's working for me. With WireGuard I can get 900mbps down and up from PIA, rather than the ridiculous 300mbps I was getting with OpenVPN connected to the same servers.
Many thanks for the PIA WireGuard instructions for pfSense.
I am busy on other non-IT projects at the moment, so it may take some time before I can get into this; but if it works for you I am sure it will work for me. If I run into any issues, I will get back to you here.
Again, thanks a lot for all your efforts to figure this issue out to a working configuration instruction.
-
I tried the "git clone" on my mini-pc running pfSense 2.7.2-RELEASE (amd64) but it comes up with a "Command not found" error.
Did you install any FreeBSD packages prior to starting this install procedure? If so, which ones?
-
@FCS001FCS I performed steps 1 through 6 on a dummy Debian VM. I installed the wireguard client using apt...
All you really need is the /etc/wireguard/pia.conf file generated when you successfully execute ./run_setup.sh
Just FYI, if you successfully run ./run_setup.sh, it will create a wireguard tunnel between your VM and PIA, and that will kill your ssh remote session to the VM. Be ready to jump to the console session of the VM and run "wg-quick down pia" to disconnect the wireguard tunnel, or just use the console session to read the contents of /etc/wireguard/pia.conf which is what really matters to successfully configure the WG client in pfSense
I will also say this: the "Address: 10.1.149.3" section of step #3 occasionally changes to some other IP address, and that requires me to re-run ./run_setup.sh to get the new IP, private key, etc and update all these in pfSense... So using WG with PIA in pfSense is not very stable as PIA changes things every once in a while.
-
@FCS001FCS The github page has this:
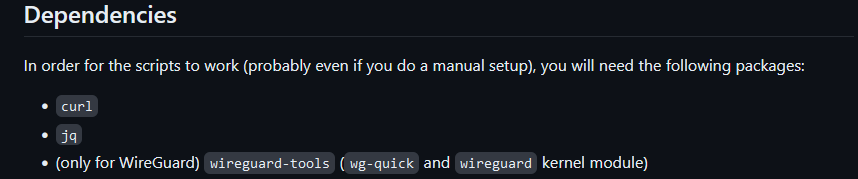
I dont know if those packages exist in FreeBSD so I just used Debian to make sure
-
I think this is too complicate for me at the moment and I will stay with Open VPN when using PIA on my pfSense bare-metal setup.
Hopefully, either PIA, or someone more knowledgeable with pfSense/FreeBSD, with create a pfSense package that does what you described for us less knowledgeable users.
Thanks for the help.
-
@eidi First, thanks for this guide, and a little shame for PIA for not offering something like this themselves, as other VPNs are more than happy to oblige.
But I'm not able to get it to work, probably due to ignorance.
I did as you did and spun up a VM to the configuration OK, but there are some things missing from your guide that I can't fill in the blanks myself.
EndPoint: somePIA-FQDN.com:1337 - This wasn't visible in my config, endpoint was an IP, I assume that's okay?
outbound NATs on pfSense - That's something I have done for openvpn, but for wireguard, there was no interface created automatically (probably because the wireguard package is new?)
So I created one myself using the address parameter from my config file as a static IP:
[Interface]
Address = xyzneed to configure a new gateway - Then of course there's no gateway automatically created, so I did exactly the same thing there, but the gateway IP is of course dynamic.
Then policy based routing...I did this too from my LAN rules, forcing traffic out through the above gateway.
Now, packets are routing through the above rule, but when I check my public IP, it's my ISP.
In addition, for wireguard status I've got zero TX/RX packets and 'Latest Handshake' is 'never'.Is anything jumping out at you here please?
-
If your "last handshake" for the new WG tunnel says "never", the WG connection was not properly established. Until the little handshake icon shows up in green, there's something wrong in your set up
Yes, the endpoint can be an IP address
Interface creation: yes, this process is manual --> go to Interface/Assignments, create a new interface and associate it with the new WG tunnel (in my case it's called "tun_wg2 (tun_wg2)". In the interface configuration, select static IPv4 and on the IPv4 address field, enter the IP you saw in the pia.conf file under [interface]/Address: in my initial example earlier in the thread, this was 10.1.149.3
The gateway. What you did is correct, you took the IP from [Interface]/Address from pia.conf and used it there.
The whole problem in using PIA's WireGuard implementation is that every once in a while (a few weeks usually), the IP from [Interface]/Address changes, so you need to reconfigure both your gateway and interface manually. Its a big pain in the ass!
I'm thinking about switching this whole set up to not use pfSense's WireGuard VPN client. Instead, maybe I'll create a simple debian VM with the scripts from https://github.com/pia-foss/manual-connections and use this VM's internal IP address as a gateway in pfSense (so the VM becomes a router). I think at least with this set up, the WG client should auto manage the occasional change in the IP, and I can have some watchdog script in the VM reconnect if it detects the WG tunnel is no longer working for some reason. But this will take time, I'm not very familiar with linux scripting
-
@eidi thanks again dude.
I might hang up my gloves on this one.
Sounds like I'd fare better offloading wireguard to a 'router on a stick' with better WG support from PIA, similar to how you're doing it. -
@ctuchik In case you still want to do this, I found the permanent solution to the problem. Instead of trying to have pfSense's wireguard client establish the WireGuard connection to PIA, if you run pfSense in a virtualized environment like proxmox or ESXi, you can easily create a linux VM with two network interfaces whose only purpose in life is to establish the VPN session with PIA and serve as a gateway for pfSense. That way, PIA's scripts work out of the box in the way they're supposed to, and for pfSense your linux VM is just another WAN interface for practical effects. It was quite easy to create the linux vm, I used a distribution based on Debian called DietPi which is super slim and I give it less than 1GB of RAM, 2 virtual processors, and it can easily sustain 700mbps down and up with PIA's WireGuard connection active.
With this approach, even if stuff changes in PIA's side, their scripts handle the disconnect / reconnect in the correct way.
-
@eidi Nice one thanks.
I do have proxmox and strangely, I have also deployed dietpi a few times before haha!
Are you me? :)I don't know if I mentioned it, but my workaround was to make 4x openvpn clients, then make a gateway group.
I was aiming to use this as a patchwork to the lack of openvpn 3 threading, but it turns out it's increased my anonymity greatly by presenting a constantly shifting public presence. -
-
@eidi @ctuchik: I got the DietPi setup and have it connected to WG with PIA. I am only getting 400 mbps on a 1gbps line.
My questions is.-
I have 2 NIC where the WAN is connected to PFSense. So that means the DietPi are getting IP address from PFSense DHCP Server then connect to PIA not directly with WAN network but through PFSenses WAN.
If I create 2 NIC in ESXi for DietPi, 1 for LAN, 1 for WAN, won't it create a problem with 2 VMs getting each WAN IP? -
And how do I get my endpoints to point to DietPi?
-
-
@Bjur I personally didn't get very far with the WG box, though I have done it in the past.
You would set your default gateway via DHCP to ensure traffic goes through the WG connection.
You would make sure that the traffic out to the Internet from the WG box is directly out, if it's got to go via pfSense itself.I run my hypervisor behind the ISP's router, while that's probably super inefficient, it does mean I can make as many gateways as I please.
-
@ctuchik Thanks for the answer.
I'm not sure I follow.
When you set you default gateway, it's normally just an IP address like 192.168.1.1. What do you mean setting it via DHCP?You would make sure that the traffic out to the Internet from the WG box is directly out, if it's got to go via pfSense itself.
So in Esxi I should dedicate a WAN interface to DietPi and still have the WAN interface also on PfSense?
-
@Bjur So, I think maybe we misunderstand each other?
Are you asking me how you set the default gateway for hosts on your LAN?
Because if you are, that's typically allocated by the DHCP server (Services > DHCP Server > Other DHCP Options > Gateway)If you mean pfsense' gateway, I'm not sure exactly of your unique setup?
What most people do to route traffic to the right place is make a PASS firewall rule for traffic from a particular place (like the IP of the dietpi box maybe) and under advanced options, specify the gateway you want the traffic to take:
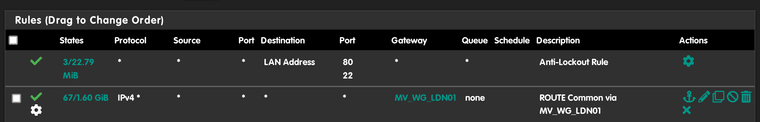
For what it's worth, I just gave up bothering with PIA - I've moved to mullvad because they have an excellent self-written guide on setting up wireguard with pfsense.
It's reasonably fast too, compared to openvpn - I'm getting about 5-10x the speed, which still isn't near my uplink max, but far superior still.