Snort blocking Windows Store downloads without alerts?
-
Hello all,
I encounter a little annoying issue and I cannot figure out what is really blocking in Snort.
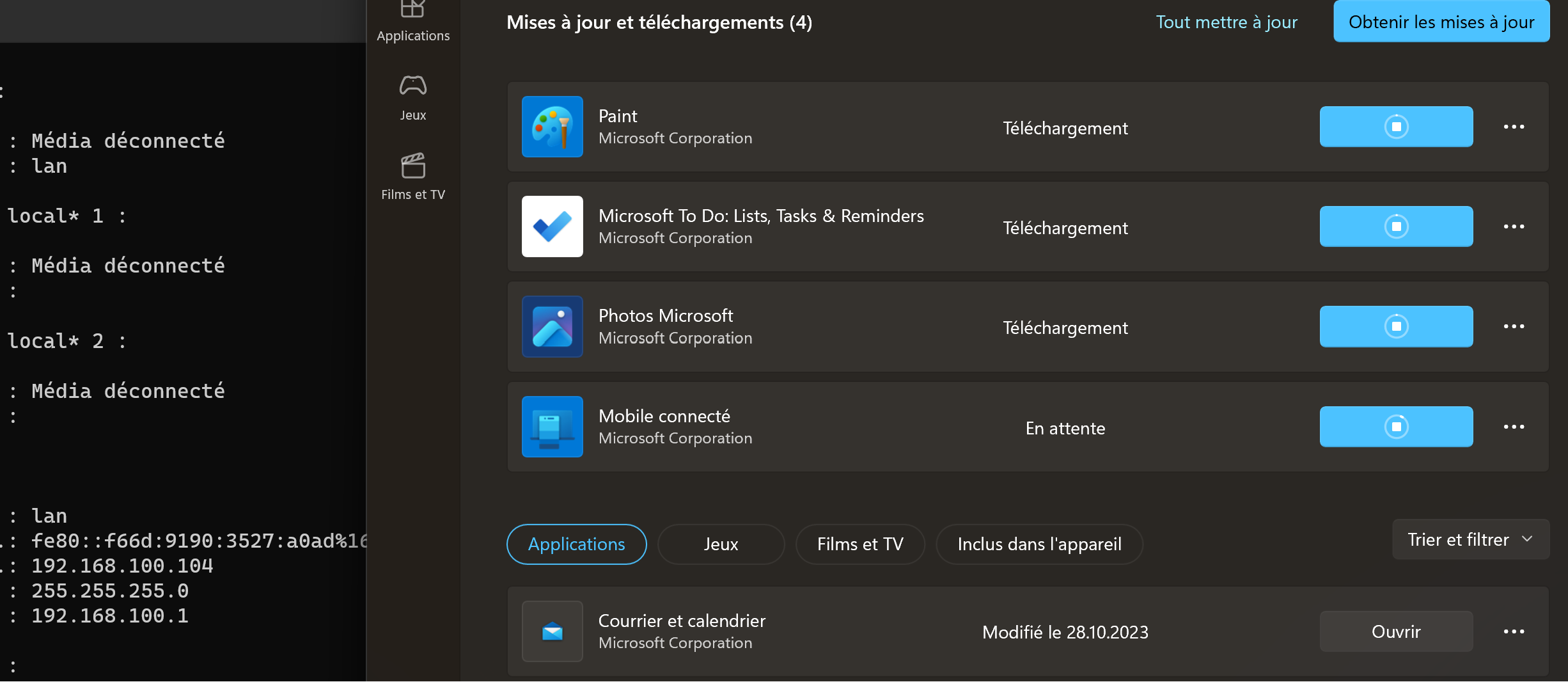
Sometime, my Windows computers cannot download the updates from the Windows Store. The downloads are stuck:
I checked in the firewall logs and I clearly see that some traffic have been intercepted by Snort:
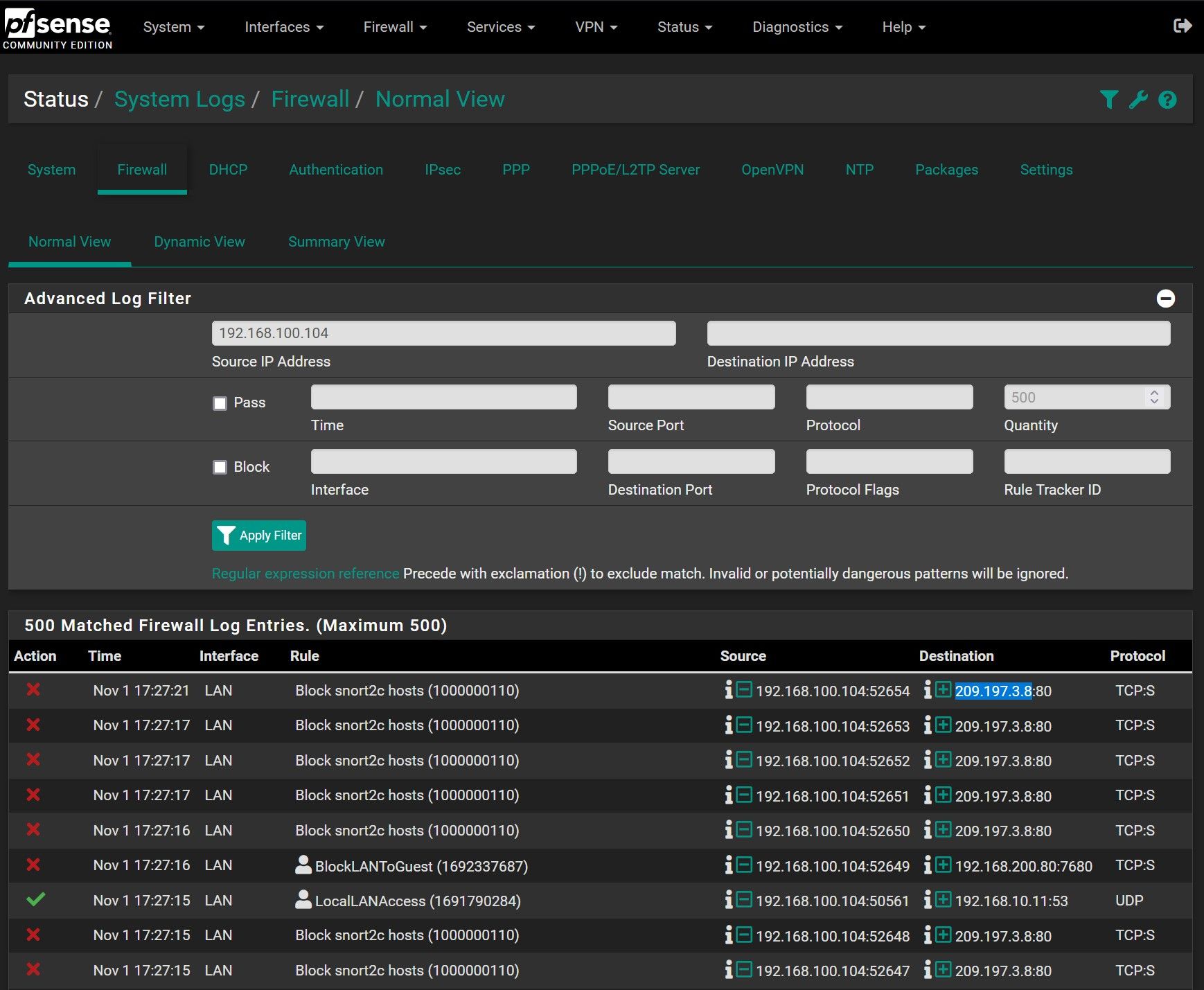
Then, I try to search in the Snort module what is really blocking and I don't see any alerts at that time or older to this IP.
From my pfsense external/WAN IP filtered:
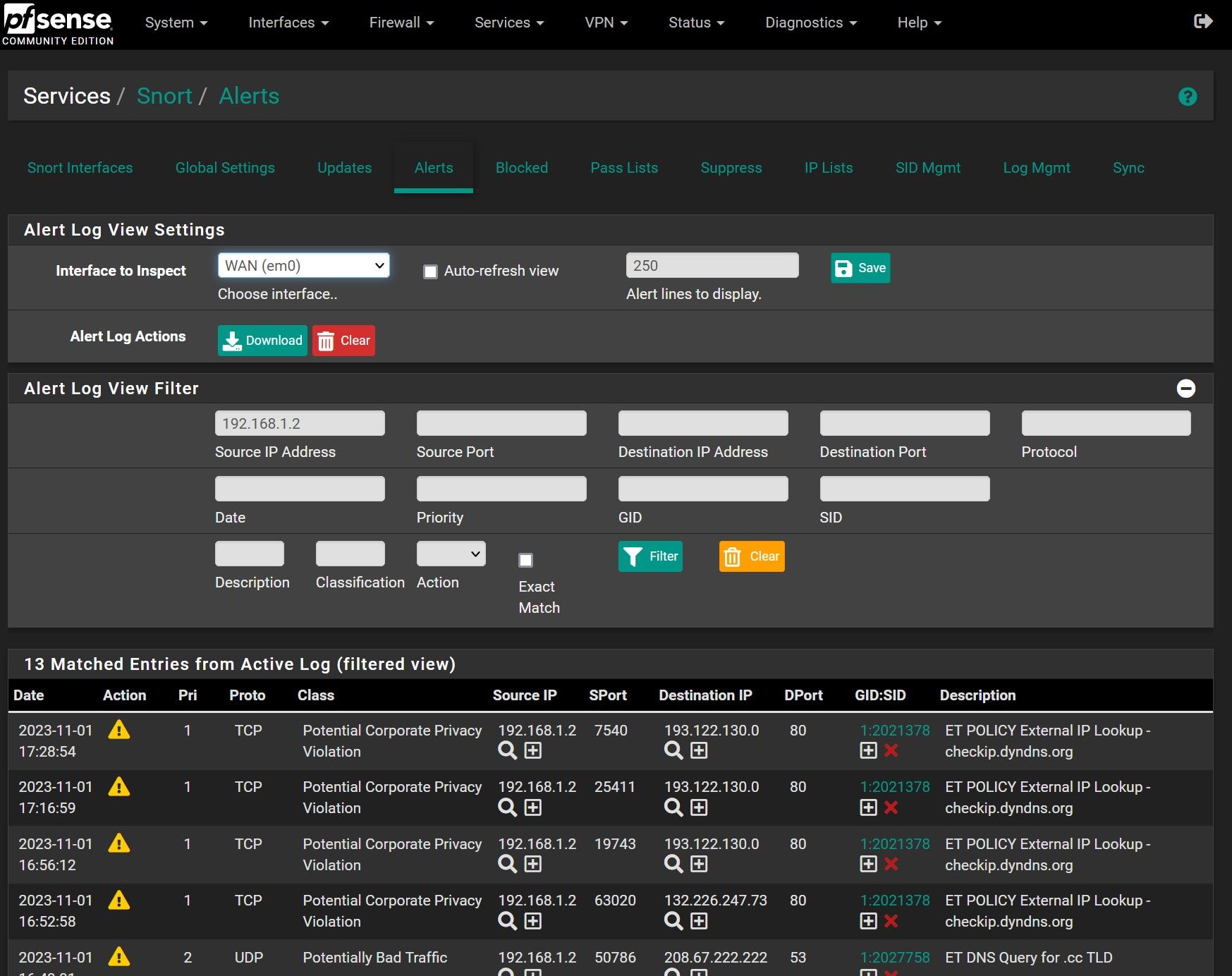
(nothing at 17:27)To the specific external IP address filtered:
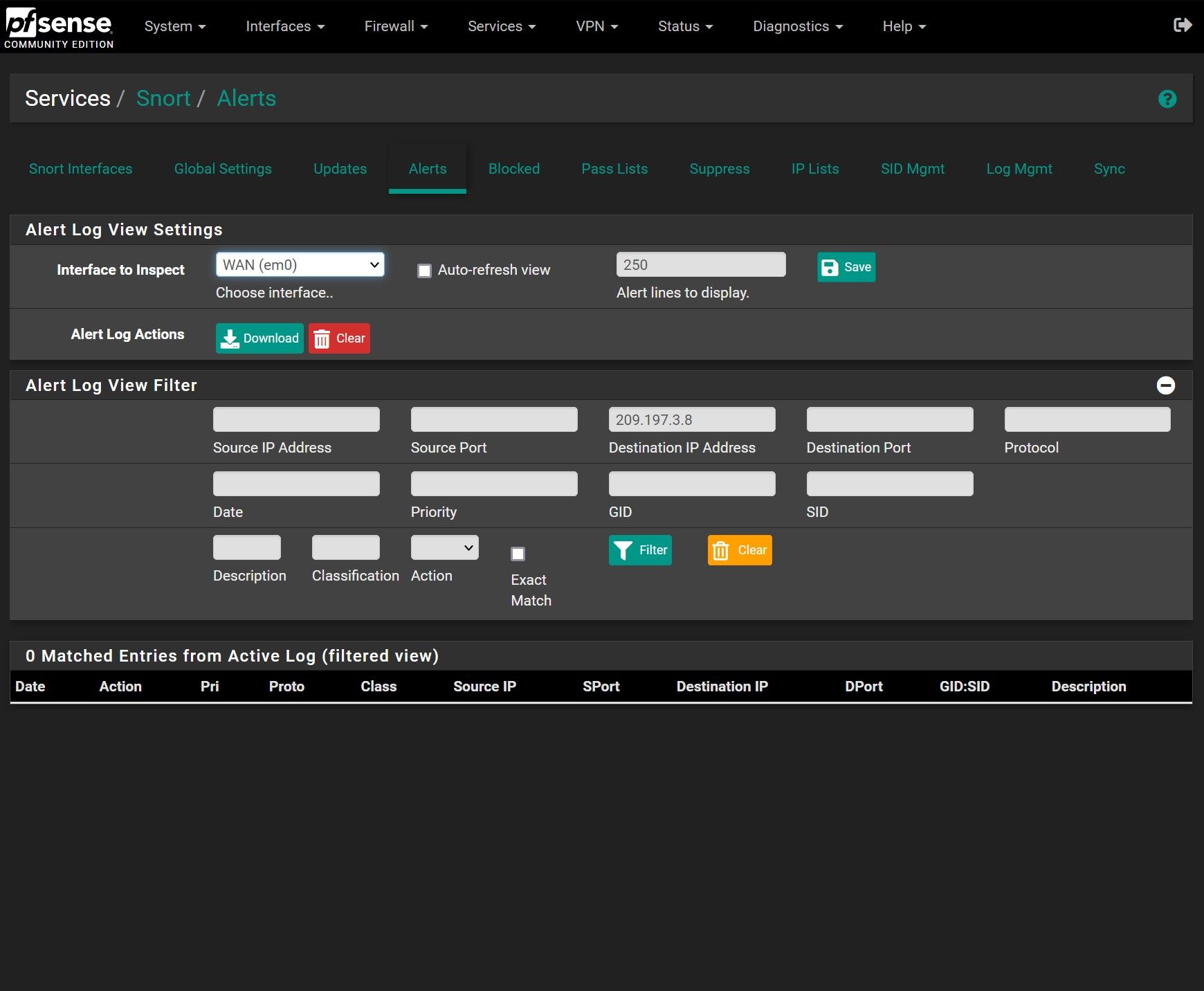
(nothing at all)But I clearly see that there is some blockage in the blocked list for this IP:
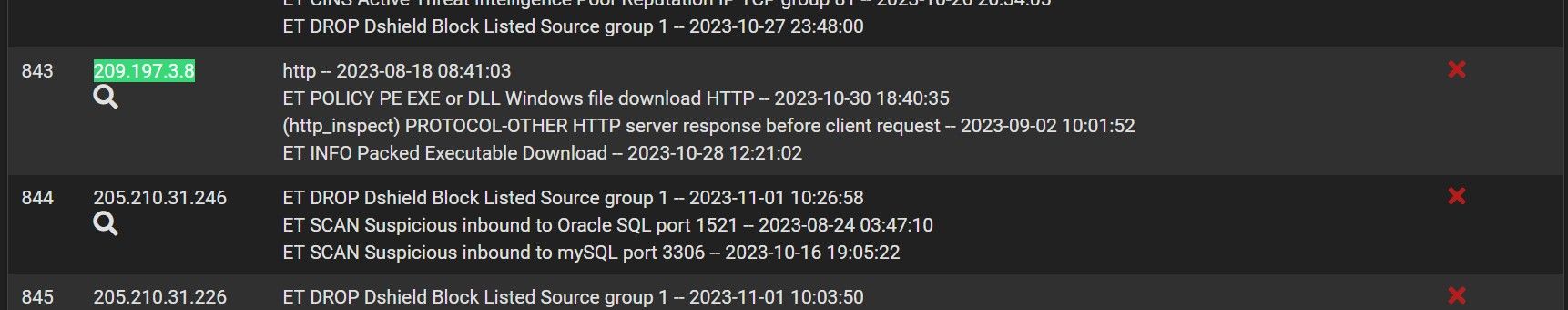
If i delete this blockage alert (ID 843), my Windows Store downloads start right away and some days after, the issue appears again.
Do you have any clue on what rules/alerts/signature might be blocking? I don't know how to find it and I never clear the alerts in snort so it should be there :/
-
@bibou635 If you're running it on WAN Snort is only going to see your WAN IP, not PCs behind NAT. Though, alerts should show on the Alerts page. The rule there should match the entries on the block tab ("ET POLICY...").
If you remove the IP on the filter does the Alerts tab have any content?
A couple side notes...
You can set up a feed for DShield in pfBlocker.
Per BMeeks (package maintainer) the Policy and Info rules are meant more for monitoring traffic than blocking. Of course they can be used to block those things though. -
Hi,
Yes, if I clear all filters, I have a lot of logs. But there is too much lines to be able to really search something.
I did an extract of all the logs and I still don't see any alerts for the timing Nov 1 17:27:17 but I found this:
10/29/23-17:20:44.789615 ,1,2018959,4,"ET POLICY PE EXE or DLL Windows file download HTTP",TCP,209.197.3.8,80,192.168.1.2,20083,53462,Potential Corporate Privacy Violation,1,alert,Allowand this:
10/30/23-18:40:35.728636 ,1,2018959,4,"ET POLICY PE EXE or DLL Windows file download HTTP",TCP,209.197.3.8,80,192.168.1.2,41714,55381,Potential Corporate Privacy Violation,1,alert,AllowDo you think that this alert has blocked the traffic and since everything is blocked without creating new alerts?
I try to search this line via the Alert filter search but I don't know what to search to see it (to easily add to my supress list). -
@bibou635 said in Snort blocking Windows Store downloads without alerts?:
Do you think that this alert has blocked the traffic and since everything is blocked without creating new alerts?
Are you running Snort in Legacy Blocking Mode? I'm going to assume "yes" since you showed a screenshot of the BLOCKS tab.
The alerts you see on the ALERTS tab are only those present in the currently active
alert.logfile. If you have a busy system and/or have a short log rotation interval configured, it is possible for thealert.logfile to get rotated often. You cannot see any alerts on the ALERTS tab from rotatedalert.logfiles. That's what I suspect is going on for you. Thealert.logfile containing that alert entry has been rotated since 10/29/23 when that alert happened and caused the block. Limiting the displayed alerts on the ALERTS tab to only the currently active file is necessary. Otherwise, PHP would choke and crash trying to digest potentially gigabytes of rotated and archived logs to display the contents.Unless you enable the option on the GLOBAL SETTINGS tab to periodically clear the blocked hosts table, then once Snort issues a block for an IP address that block will stay in place until either you reboot the firewall or you manually clear the block. That's why I highly recommend to folks that they enable the "Clear Blocked Hosts" option and set it for something reasonable like 1 hour. If the same host initiates any further traffic, Snort will catch it and block it again. Otherwise, no sense in having a given IP blocked forever - especially harmless IPs like this one from a Microsoft site.
Lastly, there is really no good reason to be using the ET INFO or ET POLICY rules in most small business environments. Using them with Inline IPS Mode and leaving their action set to alert and not drop can be okay if there is a real need. But I would never use those rules with Legacy Blocking Mode. Those rules are going to generate a number of aggravating false positives in most instances, and when used with Legacy Blocking Mode will generate nuisance blocks. This example you are posting about is one of them. Only enable rules that actually detect legitimate threats to hosts in your network environment. I doubt the Microsoft Store is a "threat" unless you have some corporate policy that forbids connection to it. IDS/IPS installs require careful analysis and tuning of enabled rules before you turn on blocking
 . Let it run in non-blocking mode for weeks and constantly peruse the alerts to see what is "normal" for your network. Then make sure any rules triggering on "normal traffic" for your network are disabled or appropriately suppressed. Note that in many instances it's better to disable a rule rather than simply suppress it as disabling saves computing resources. Suppressing a rule saves almost no resources as the rule is still processed and traffic is analyzed with it - only the actual alert log entry and putting the IP in the snort2c table is skipped when a rule is suppressed.
. Let it run in non-blocking mode for weeks and constantly peruse the alerts to see what is "normal" for your network. Then make sure any rules triggering on "normal traffic" for your network are disabled or appropriately suppressed. Note that in many instances it's better to disable a rule rather than simply suppress it as disabling saves computing resources. Suppressing a rule saves almost no resources as the rule is still processed and traffic is analyzed with it - only the actual alert log entry and putting the IP in the snort2c table is skipped when a rule is suppressed. -
Hi bmeeks !
Yep, my snort is running in Legacy mode.
Noted for the alerts content, my settings "Remove Blocked Hosts Interval" is at 4 days but might be a good idea to set 1 hours like you mentioned.I have disabled the ET INFO and ET POLICY rules and so far it looks to be working. Let's see in the coming weeks.
Thanks again for your responses, it helped a lot :)