Guest VLAN Firewall Rule Clarification Please
-
Hey All,
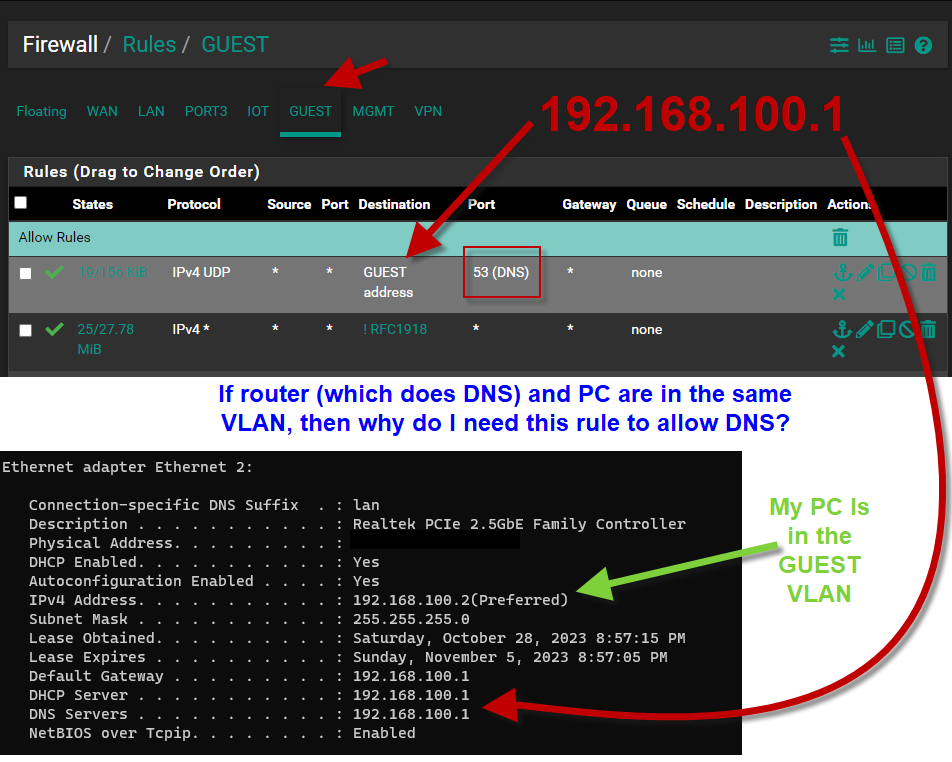
I'm finally getting around to figuring out the firewall rules for my Guest VLAN network. For this network, all I want is the ability to internet browse, but not talk to any other VLAN on my LAN. So, after looking around on the internet, I found this these rules (see below) and they work great.
I have an allow rule to talk to the router for DNS (where I have the DNS resolver enabled on port 53) and another rule that only allows non RFC1918 internal IP (internet) destination traffic.
What I don't understand, is why do I even need the rule to the router for DNS queries? To me this doesn't make sense, since both the router (192.168.100.1) and my PC (192.168.100.2) are in the same VLAN. I thought as long as you're on the same VLAN, traffic doesn't even hit the router (or it's firewall)?
Obviously, I'm lacking in networking knowledge, so I'm hoping someone could enlighten me

-
@uplink said in Guest VLAN Firewall Rule Clarification Please:
why do I even need the rule to the router for DNS queries?
...
I thought as long as you're on the same VLAN, traffic doesn't even hit the router (or it's firewall)?But you want to talk to (hit) the router, now you do need a rule.
-
@uplink
The rule set on the Guest interface filters any traffic entering this interface. If a connected device sends a DNS request to pfSense the packet also enters the guest interface. The none-RFC1918 rule doesn't cover its destination IP, however, hence you need an extra rule for it.Packets destined to any other IP within the guest subnet than pfSense won't pass pfSense and hence it cannot block that traffic.
BTW: for DNS you should also allow TCP (TCP/UDP) protocol.
-
@uplink said in Guest VLAN Firewall Rule Clarification Please:
I'm finally getting around to figuring out the firewall rules for my Guest VLAN network. For this network, all I want is the ability to internet browse, but not talk to any other VLAN on my LAN. So, after looking around on the internet, I found this these rules (see below) and they work great.
I have an allow rule to talk to the router for DNS (where I have the DNS resolver enabled on port 53) and another rule that only allows non RFC1918 internal IP (internet) destination traffic.
What I don't understand, is why do I even need the rule to the router for DNS queries? To me this doesn't make sense, since both the router (192.168.100.1) and my PC (192.168.100.2) are in the same VLAN. I thought as long as you're on the same VLAN, traffic doesn't even hit the router (or it's firewall)?
Obviously, I'm lacking in networking knowledge, so I'm hoping someone could enlighten me
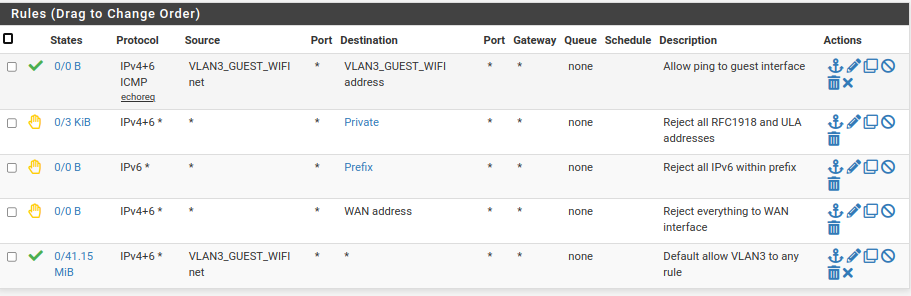
Here are my guest rules. They allow only access to the Internet and pinging the guest interface. Since they can't access anything on my network, I configured the DHCP server to point to the Google DNS, instead of my own.
-
@uplink said in Guest VLAN Firewall Rule Clarification Please:
To me this doesn't make sense, since both the router (192.168.100.1) and my PC (192.168.100.2) are in the same VLAN. I thought as long as you're on the same VLAN, traffic doesn't even hit the router (or it's firewall)?
You are correct if device A wants to talk to B in the same network, they don't need to talk to pfsense. But in this case you specifically want to talk to pfsense (for dns). So yeah you need to allow that. Just like if device B in your network was running its own firewall.. You would need to allow A to talk to it, even though no router is involved in the conversation.