Unbound Resolver - failed to resolve host
-
I'm just going to mention two topics which are related to the same problem:
Unable to resolve acb.netgate.com - it also seems here people are not addressing the real issue.
-
Today I couldn't make it into
login.live.com[23.09-RELEASE][admin@pfs-fw]/root: date && ping login.live.com Thu Nov 9 13:37:28 WET 2023 ping: Unknown host [23.09-RELEASE][admin@pfs-fw]/root: date && ping login.live.com Thu Nov 9 13:40:27 WET 2023 PING www.tm.v4.a.prd.aadg.akadns.net (20.190.177.23): 56 data bytes 64 bytes from 20.190.177.23: icmp_seq=0 ttl=115 time=29.112 ms ^C --- www.tm.v4.a.prd.aadg.akadns.net ping statistics --- 1 packets transmitted, 1 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 29.112/29.112/29.112/0.000 ms -
@maverickws said in Unbound Resolver - failed to resolve host:
filterdns
Are you on 23.09 - I thought I saw some issues with urls in aliases having some issues.. That is a filterdns log entry..
I think is is prob related
-
@johnpoz yes, there are url's in alias, but the issue is unbound not being able to resolve them. Just like it doesn't resolve
acb.netgate.comsometimes and get those errors as well. This address isn't in any alias. I believe it's hardcoded.
I'm not sure what you mean by "that is a filterdns log entry" if it has some special meaning, But when I go to Status > System Logs > DNS Resolver and use the log filter to search for the termfailedthat's what shows up.Considering the
acb.netgate.comsituation detail, I would say that redmine issue doesn't cover this problem. Also as I just showed, pinginglogin.live.comdirectly from the firewall fails resolution in an initial moment. -
@maverickws and when you had a problem with this login.live.com did you run a +trace
CNAME login.msa.msidentity.com.
CNAME www.tm.lg.prod.aadmsa.trafficmanager.net.
CNAME prdv4a.aadg.msidentity.com.
CNAME www.tm.v4.a.prd.aadg.akadns.net.
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.14
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.11
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.18
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.13
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.19
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.21
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.28.22
www.tm.v4.a.prd.aadg.akadns.net. 300 IN A 40.126.7.32
;; Received 188 bytes from 193.108.88.128#53(a1-128.akadns.net) in 30 msLook at the train of cnames involved in getting there.. Do you have qname min set, especially with strict this can cause problems when you have lots of cnames to work through..
-
@johnpoz I didn't do a +trace no, I simply waited for the problem to solve on its own like always does.
I do not have strict query name minimisation enabled. Actually let me put my DNS Resolver config here.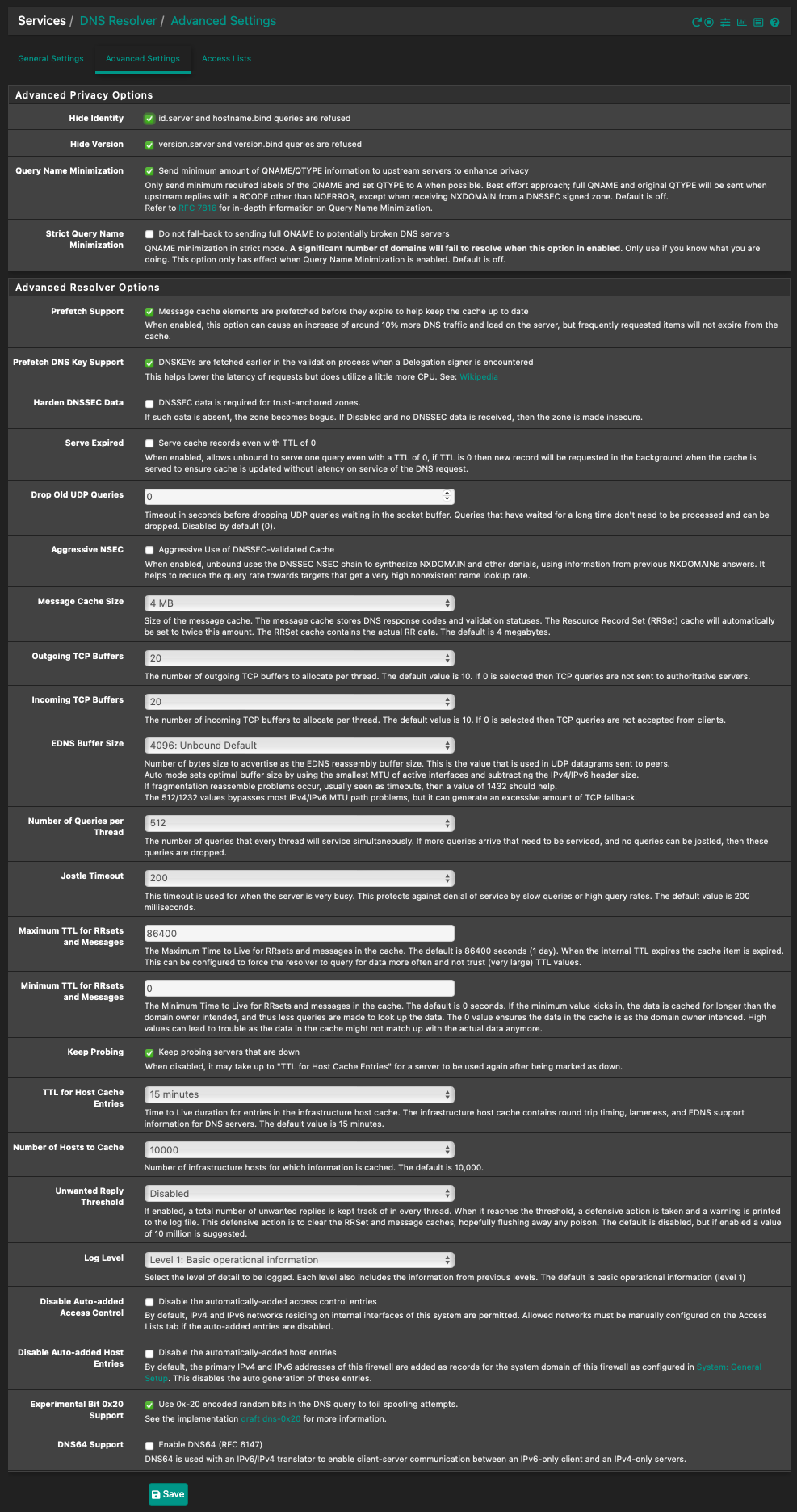
Anyway, with CDN's and whatever, that chain of CNAMES is expected, its quite common.
Anyway I thought well let's do a trace to
acb.netgate.comsince it's another failing address. This turned to be a fun one:[23.09-RELEASE][admin@pfs-fw]/root: dig acb.netgate.com +trace ; <<>> DiG 9.18.16 <<>> acb.netgate.com +trace ;; global options: +cmd . 35906 IN NS i.root-servers.net. . 35906 IN NS j.root-servers.net. . 35906 IN NS k.root-servers.net. . 35906 IN NS l.root-servers.net. . 35906 IN NS m.root-servers.net. . 35906 IN NS a.root-servers.net. . 35906 IN NS b.root-servers.net. . 35906 IN NS c.root-servers.net. . 35906 IN NS d.root-servers.net. . 35906 IN NS e.root-servers.net. . 35906 IN NS f.root-servers.net. . 35906 IN NS g.root-servers.net. . 35906 IN NS h.root-servers.net. . 35906 IN RRSIG NS 8 0 518400 20231121210000 20231108200000 46780 . Dez3g0tBHaJpwK0mSw4kEhBGlITDUeu4+IDZ3Wtjp4tgc+ZfaQlqVcsb UWw+bjkWkFz81UGpl6Ru+JZQUT3Tg3K2h14KUzOexBWPoiOH4QnjU3Qi VnkPQjW7y5ywx7AtsDHYH1L+fwf6UXu87z+xBQ9KwMzOMTQ9sk0qJDZV 4+4pFH64xY8AmsxFVaKjP+RF3TiAnpQ8Re+CdsP5mxGeTlPqjrslb0KG KFVYyJ54zZ9mIOHAxM1BTMKN9IpEWSTtNHltCzjRUzN3y2BqsZOTUXeI kKAsKqeSEr458sgvGY2qUZr2/msO+tDnlUx7ccVKmj1fjNN05g9Glehx gYal5w== couldn't get address for 'j.root-servers.net': not found couldn't get address for 'm.root-servers.net': not found couldn't get address for 'a.root-servers.net': not found couldn't get address for 'b.root-servers.net': not found couldn't get address for 'd.root-servers.net': not found couldn't get address for 'f.root-servers.net': not found couldn't get address for 'g.root-servers.net': not found ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20231122050000 20231109040000 46780 . v+dvjVQahOi5azOEOfZY4Y2XX4G0ZlJ4YNaEOHRVN5pYa6KaVsWITwuz k5kDqtZ9oOYAmHFmyo/ybEToqZEtCqY6guI0UQgk++gvQgAtOSTUNN0G 2xloZxLQzWOSAq3++KpuI+fxNjO/zQ94iojT6eSxKoYDDrurAuKuNtcq qCH+S3UIHG9sm0yk+wVpuYXFIsNNOKjFX+TbQGdFnPLvX/0ZKO+15Pzp +vtOGQ1Ra51k3FVop/SJ20BbGVbhhD4wjW+7eVkenVOFDbu2SHiv/2BJ yPK1nwAgk/ABGZNec9A5+S+tCXYhftkkuRdICy4H/c5qZFVCSB296QgL gDb1YQ== ;; Received 1206 bytes from 192.36.148.17#53(i.root-servers.net) in 51 ms netgate.com. 172800 IN NS ns1.netgate.com. netgate.com. 172800 IN NS ns2.netgate.com. netgate.com. 172800 IN NS ns3.netgate.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20231114052550 20231107041550 63246 com. Qeg8YllC8KbvaizuSmn3Jlaro97H5qydstgnIDAE9qEXbMUxqrt5ZJ/x tlFiZ9Y9O1ep/ZuIhe5BAzPLMAPDUCzahuBq1VNN5BvQMwx53bMSij+V cPBLPd45H9yACQH0W6fw4Omy4Zj/De9a36P7Q/5+/P7f4ItDuWLsqakG 7qpeIkIS7CwJdpcS5hL8lomNNsaboST+YSCNtDptHRr4iA== 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 86400 IN NSEC3 1 1 0 - 2U546JK1TS9KBOQUQCUA3NNLO26FTDRN NS DS RRSIG 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 86400 IN RRSIG NSEC3 8 2 86400 20231115051637 20231108040637 63246 com. MnuXQIcWWQr7ruCa+qpsd9oWYaym21R+Wa8ushn1uNCZjqdV4q/YBvQk sTG5j9KmLN+eS9VjrU8bzJzcGtWDXv6EjmeBofv7GkAymX7u1h/dGOAf jTScF9kUggIEez//mFctnuBtEc2gDxETZ0iDD9W0XKt6o0GuM2nQwgLd LSmkDHJojmqMxcp7M+cWd0W1IJ+G1G7C9pIK/L+yCdkOKA== ;; Received 779 bytes from 192.5.6.30#53(a.gtld-servers.net) in 33 ms acb.netgate.com. 300 IN A 208.123.73.212 netgate.com. 3600 IN NS ns3.netgate.com. netgate.com. 3600 IN NS ns2.netgate.com. netgate.com. 3600 IN NS ns1.netgate.com. ;; Received 274 bytes from 208.123.73.90#53(ns2.netgate.com) in 155 ms -
And here's another one.
[23.09-RELEASE][admin@pfs-fw]/root: dig msg.aliexpress.com +trace ; <<>> DiG 9.18.16 <<>> msg.aliexpress.com +trace ;; global options: +cmd . 35238 IN NS f.root-servers.net. . 35238 IN NS g.root-servers.net. . 35238 IN NS h.root-servers.net. . 35238 IN NS i.root-servers.net. . 35238 IN NS j.root-servers.net. . 35238 IN NS k.root-servers.net. . 35238 IN NS l.root-servers.net. . 35238 IN NS m.root-servers.net. . 35238 IN NS a.root-servers.net. . 35238 IN NS b.root-servers.net. . 35238 IN NS c.root-servers.net. . 35238 IN NS d.root-servers.net. . 35238 IN NS e.root-servers.net. . 35238 IN RRSIG NS 8 0 518400 20231121210000 20231108200000 46780 . Dez3g0tBHaJpwK0mSw4kEhBGlITDUeu4+IDZ3Wtjp4tgc+ZfaQlqVcsb UWw+bjkWkFz81UGpl6Ru+JZQUT3Tg3K2h14KUzOexBWPoiOH4QnjU3Qi VnkPQjW7y5ywx7AtsDHYH1L+fwf6UXu87z+xBQ9KwMzOMTQ9sk0qJDZV 4+4pFH64xY8AmsxFVaKjP+RF3TiAnpQ8Re+CdsP5mxGeTlPqjrslb0KG KFVYyJ54zZ9mIOHAxM1BTMKN9IpEWSTtNHltCzjRUzN3y2BqsZOTUXeI kKAsKqeSEr458sgvGY2qUZr2/msO+tDnlUx7ccVKmj1fjNN05g9Glehx gYal5w== couldn't get address for 'f.root-servers.net': not found couldn't get address for 'm.root-servers.net': not found ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20231122050000 20231109040000 46780 . v+dvjVQahOi5azOEOfZY4Y2XX4G0ZlJ4YNaEOHRVN5pYa6KaVsWITwuz k5kDqtZ9oOYAmHFmyo/ybEToqZEtCqY6guI0UQgk++gvQgAtOSTUNN0G 2xloZxLQzWOSAq3++KpuI+fxNjO/zQ94iojT6eSxKoYDDrurAuKuNtcq qCH+S3UIHG9sm0yk+wVpuYXFIsNNOKjFX+TbQGdFnPLvX/0ZKO+15Pzp +vtOGQ1Ra51k3FVop/SJ20BbGVbhhD4wjW+7eVkenVOFDbu2SHiv/2BJ yPK1nwAgk/ABGZNec9A5+S+tCXYhftkkuRdICy4H/c5qZFVCSB296QgL gDb1YQ== ;; Received 1178 bytes from 199.7.91.13#53(d.root-servers.net) in 2 ms aliexpress.com. 172800 IN NS ns1.alibabadns.com. aliexpress.com. 172800 IN NS ns2.alibabadns.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20231114052550 20231107041550 63246 com. Qeg8YllC8KbvaizuSmn3Jlaro97H5qydstgnIDAE9qEXbMUxqrt5ZJ/x tlFiZ9Y9O1ep/ZuIhe5BAzPLMAPDUCzahuBq1VNN5BvQMwx53bMSij+V cPBLPd45H9yACQH0W6fw4Omy4Zj/De9a36P7Q/5+/P7f4ItDuWLsqakG 7qpeIkIS7CwJdpcS5hL8lomNNsaboST+YSCNtDptHRr4iA== IU8ST58L7MCIRM2A1G8UNVIMG6RTJ5J1.com. 86400 IN NSEC3 1 1 0 - IU8TIRN4KSOABTMMDH6NG4MPE11UOFMA NS DS RRSIG IU8ST58L7MCIRM2A1G8UNVIMG6RTJ5J1.com. 86400 IN RRSIG NSEC3 8 2 86400 20231113053629 20231106042629 63246 com. dK98q/JxBGKa3k64KCwHJcC8Jw1kD+gJkBtMXWCefue/zJMo5RzTpmdT C9EgSNuYhWE0uoGLE8ztr9aZ6rRMPwkO96q1EjRpuoq9aM/HS86Yo4LH 4c/p9nAJ67aMnwUb/qgBm0Y6UdTK4ILHuNzZ5qOzt5bm/xe88RR5WFO+ WJF1JWQrFdT4EPt5ROfocn/1gfY8tkm1Ok1aKN4fmFkjqg== ;; Received 827 bytes from 192.31.80.30#53(d.gtld-servers.net) in 31 ms msg.aliexpress.com. 300 IN CNAME global-aebridge.aliexpress.com. ;; Received 91 bytes from 47.88.74.36#53(ns2.alibabadns.com) in 167 msNotice how on the trace for
acb.netgate.comyou get:couldn't get address for 'd.root-servers.net': not found
And on this trace:Received 1178 bytes from 199.7.91.13#53(d.root-servers.net) in 2 msIf this is not an unbound problem then I really would like to know where's the culprit.
-
@maverickws the roots error is a bit odd..
What does unbound actually show.
[23.05.1-RELEASE][admin@sg4860.local.lan]/root: unbound-control -c /var/unbound/unbound.conf lookup . The following name servers are used for lookup of . ;rrset 75046 13 1 11 5 . 75046 IN NS a.root-servers.net. . 75046 IN NS b.root-servers.net. . 75046 IN NS c.root-servers.net. . 75046 IN NS d.root-servers.net. . 75046 IN NS e.root-servers.net. . 75046 IN NS f.root-servers.net. . 75046 IN NS g.root-servers.net. . 75046 IN NS h.root-servers.net. . 75046 IN NS i.root-servers.net. . 75046 IN NS j.root-servers.net. . 75046 IN NS k.root-servers.net. . 75046 IN NS l.root-servers.net. . 75046 IN NS m.root-servers.net. . 75046 IN RRSIG NS 8 0 518400 20231122050000 20231109040000 46780 . AI7nQpQeUvrxX6D+Ihl24ERJoxe3XvWSOYJPdsfZVyevQ+gioQlzVE8qnd9rfbKeEhMpNACcgGI+WDCHPrIClEBgcnYfM4hLbiBHBWB+J0/qj4eh4237cxgVzottiNSHbT5OUWmX4Wsbb0JDqU3xMuMInr1I5aD0gLBuLR+cD5T+kpzzA73Hx8yVpQGm7azpKou0tEIEQ07W+lyaRF1uleO6YMP4v6BpSPMumklsoNMoThCHCz3f4ENPuIjky1V4sE/tf6zIkzzr1wlxp7pMp2P1iXi814jgUX4Vxs5EC3n4S9z5FAgkR9sd0iq8QZEqe3R1gQ3fcZ9jjeFySnkDdw== ;{id = 46780} ;rrset 84506 1 0 8 3 m.root-servers.net. 84506 IN A 202.12.27.33 ;rrset 84506 1 0 8 3 m.root-servers.net. 84506 IN AAAA 2001:dc3::35 ;rrset 84506 1 0 8 3 l.root-servers.net. 84506 IN A 199.7.83.42 ;rrset 84506 1 0 8 3 l.root-servers.net. 84506 IN AAAA 2001:500:9f::42 ;rrset 84506 1 0 8 3 k.root-servers.net. 84506 IN A 193.0.14.129 ;rrset 84506 1 0 8 3 k.root-servers.net. 84506 IN AAAA 2001:7fd::1 ;rrset 84506 1 0 8 3 j.root-servers.net. 84506 IN A 192.58.128.30 ;rrset 84506 1 0 8 3 j.root-servers.net. 84506 IN AAAA 2001:503:c27::2:30 ;rrset 84506 1 0 8 3 i.root-servers.net. 84506 IN A 192.36.148.17 ;rrset 84506 1 0 8 3 i.root-servers.net. 84506 IN AAAA 2001:7fe::53 ;rrset 84506 1 0 8 3 h.root-servers.net. 84506 IN A 198.97.190.53 ;rrset 84506 1 0 8 3 h.root-servers.net. 84506 IN AAAA 2001:500:1::53 ;rrset 84506 1 0 8 3 g.root-servers.net. 84506 IN A 192.112.36.4 ;rrset 84506 1 0 8 3 g.root-servers.net. 84506 IN AAAA 2001:500:12::d0d ;rrset 84506 1 0 8 3 f.root-servers.net. 84506 IN A 192.5.5.241 ;rrset 84506 1 0 8 3 f.root-servers.net. 84506 IN AAAA 2001:500:2f::f ;rrset 84506 1 0 8 3 e.root-servers.net. 84506 IN A 192.203.230.10 ;rrset 84506 1 0 8 3 e.root-servers.net. 84506 IN AAAA 2001:500:a8::e ;rrset 84506 1 0 8 3 d.root-servers.net. 84506 IN A 199.7.91.13 ;rrset 84506 1 0 8 3 d.root-servers.net. 84506 IN AAAA 2001:500:2d::d ;rrset 84506 1 0 8 3 c.root-servers.net. 84506 IN A 192.33.4.12 ;rrset 84506 1 0 8 3 c.root-servers.net. 84506 IN AAAA 2001:500:2::c ;rrset 84506 1 0 8 3 b.root-servers.net. 84506 IN A 199.9.14.201 ;rrset 84507 1 0 8 3 b.root-servers.net. 84507 IN AAAA 2001:500:200::b ;rrset 84506 1 0 8 3 a.root-servers.net. 84506 IN A 198.41.0.4 ;rrset 84506 1 0 8 3 a.root-servers.net. 84506 IN AAAA 2001:503:ba3e::2:30 Delegation with 13 names, of which 0 can be examined to query further addresses. It provides 26 IP addresses. 2001:503:ba3e::2:30 not in infra cache. 198.41.0.4 expired, rto 3587048 msec, tA 0 tAAAA 0 tother 0. 2001:500:200::b not in infra cache. 199.9.14.201 expired, rto 3587048 msec, tA 0 tAAAA 0 tother 0. 2001:500:2::c not in infra cache. 192.33.4.12 expired, rto 3587048 msec, tA 0 tAAAA 0 tother 0. 2001:500:2d::d not in infra cache. 199.7.91.13 rto 302 msec, ttl 446, ping 2 var 75 rtt 302, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:500:a8::e not in infra cache. 192.203.230.10 not in infra cache. 2001:500:2f::f not in infra cache. 192.5.5.241 not in infra cache. 2001:500:12::d0d not in infra cache. 192.112.36.4 not in infra cache. 2001:500:1::53 not in infra cache. 198.97.190.53 not in infra cache. 2001:7fe::53 not in infra cache. 192.36.148.17 rto 414 msec, ttl 446, ping 14 var 100 rtt 414, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:503:c27::2:30 not in infra cache. 192.58.128.30 not in infra cache. 2001:7fd::1 not in infra cache. 193.0.14.129 not in infra cache. 2001:500:9f::42 not in infra cache. 199.7.83.42 not in infra cache. 2001:dc3::35 not in infra cache. 202.12.27.33 not in infra cache. [23.05.1-RELEASE][admin@sg4860.local.lan]/root: -
@maverickws said in Unbound Resolver - failed to resolve host:
Actually let me put my DNS Resolver config here.
Would you mind also posting the settings you have on the General Settings page view as well?
Also I don't remember seeing in any of the threads you are active in for this subject, if you are running pfBlockerNG or not. Are you?
I like @johnpoz has mentioned in some of the other threads. have never had a problem with DNS Resolver, hanging, not resolving etc but my DNS setup is also a bit unique.
Thanks
-
@jrey another good question would be if registering dhcp.. When unbound restarts constantly you could have all kinds of issues that seem odd. Even if the restart is almost instant, it still flushes cache for everything..
I am not on 23.09 yet, so its not out of the realm of possibility that something odd with unbound with 23.09, but has even changed versions - yup quick look and "Changed: Update Unbound to 1.18.0"
I will most likely update to 23.09 this weekend.. So will be able to see if start having the same sort of issues.. But I tend to lean not on that.. If there was something inherently wrong with unbound 1.18 I would think it would be big news.. I was looking over the release notes since 1.19 just dropped the yesterday, and nothing jumped out to me any sort of bug fix or anything that would cause any sort of major problems with 1.18 resolving stuff.
-
@maverickws said in Unbound Resolver - failed to resolve host:
Today I couldn't make it into login.live.com
[23.09-RELEASE][admin@pfs-fw]/root: date && ping login.live.com
Thu Nov 9 13:37:28 WET 2023
ping: Unknown host
[23.09-RELEASE][admin@pfs-fw]/root: date && ping login.live.com
Thu Nov 9 13:40:27 WET 2023
PING www.tm.v4.a.prd.aadg.akadns.net (20.190.177.23): 56 data bytes
64 bytes from 20.190.177.23: icmp_seq=0 ttl=115 time=29.112 ms
^C
--- www.tm.v4.a.prd.aadg.akadns.net ping statistics ---
1 packets transmitted, 1 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 29.112/29.112/29.112/0.000 msIf I was pinging a host like "login.live.com" and "Unknown host" came back, I would :
Saying to myself : "well, why not - it even happened to facebook ones"
But then I would look up in my "what's unbound actually doing" list (the pfBlockerng dns_reply.log is great for this) and look up what happened with the question "what is the A of "login.live.com" ?
I'm resolving, so, if there was no answer, I would know that all ( !! ) the domain name servers Microsoft were down. I would be calling right away fox fox.news or msnbc (take your pick) and you'll, and Microsoft, will be hot news.
The 13 DNS root servers can't be down, as that means that the "Internet is down" for everybody.Or are you forwarding ? Great. call them.
I do presume that you took care of all the unbound settings, and that you know it isn't restarting all the time, as during a restart, DNS request are lost.
If you've done your home work, your unbound restart not that often. So here for what happens on my pfSense. Last week looks a bit messy : was was putting 23.09 trough its passes.
Know example about how not to do thing : check this one :
and you have a first class ticket for DNS-h*ll.
Or : the next best : ask pfBlockerng to update all the DNSBL feeds every hour or so.
Or : your LAN(s) and/or WAN(s) interfaces disconnect/re connect often.
Etc.Still, " login.live.com" not resolving, I would tell me something is not done very well.
Keep always in mind that the close to perfect solution isn't far : fire the current admin, take a new one, reset pfSense to default, add/change only the admin password, do not add anything (anything in big red capitals here) and .... no more DNS issues
( if still issues, in this order : change ISP, change government, change country ) -
I am on 23.09 but did not have a problem on prior versions either.
I can't comment on the impact of DHCP, and restarting Resolver. I do have DHCP in the network. DHCP is NOT handled on the NetGate.
My DNS Resolver on the Netgate, almost never restarts. Except on Reboot or when I tell it to. pfBlocker does not restart all the time either (normal IP type lists will not cause a restart, as we know they change load Alias and impact the rules not the resolver. DNSBL list updates and only when there is an update, that will cause a restart)Certainly from the point of view unbound just starting/restarting I can often go days,
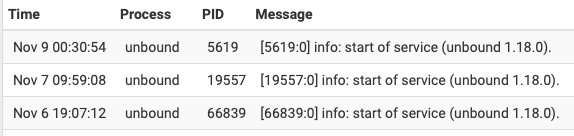
The 6th and 7th are a result of me (rebooting)
the 9th is a result of the DNSBL getting and update so of course the is expected, and is usually the most common reason for a restart)
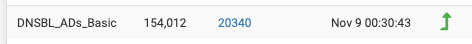
- and before anyone gets too excited about the :30 time stamp, I have my pfBlocker cron job offset by 30 minutes, so any schedule updates run 30 minute mark not the top of the hour 00. ie it didn't take 30:43 to update it took 43 seconds. LOL
-
Ok, your unbound is doing fine - is not the issue.
Because you have pfBlockerng : go here :
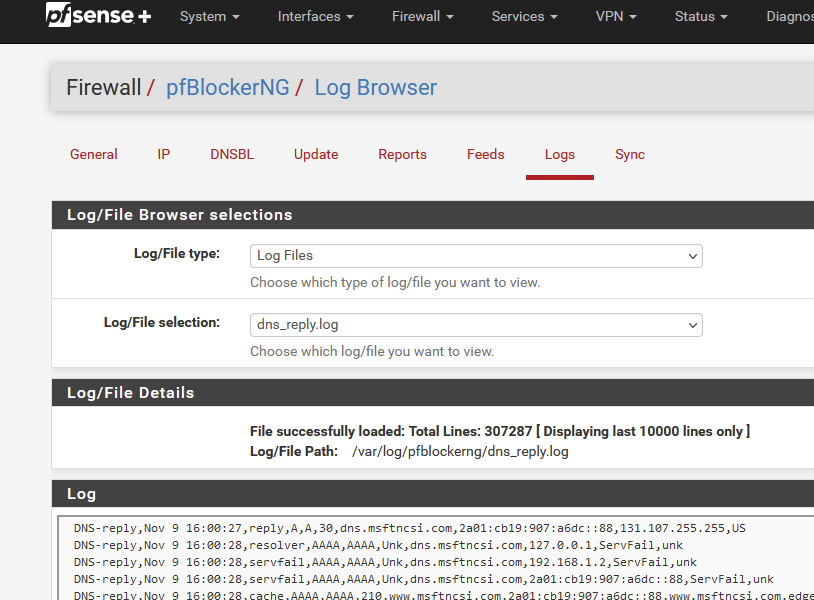
now clear your local - on your device - DNS cache.
Stop unbound - and start it : pfSense (unbound) DNS cache gone.Goto live.com, and then have a look at the logs (refresh the page).
Did it handle the request for live.com ? -
@Gertjan said in Unbound Resolver - failed to resolve host:
Ok, your unbound is doing fine - is not the issue.
You seem confused by responding specifically to me. I'm not the one with the issue.
No issues with DNS Resolver or pfBlocker, or anything else here on the network side for that matter.
The original OP @maverickws seems to have a problem, I'm just trying to put another set of eyes on his issue.
Cheers
-
Ok so lots of interactions all of the sudden, let me go over this and try to get all the questions:
To take one off the table, yes I have pfBlockerNG-devel running.
@jrey asking for the general settings config
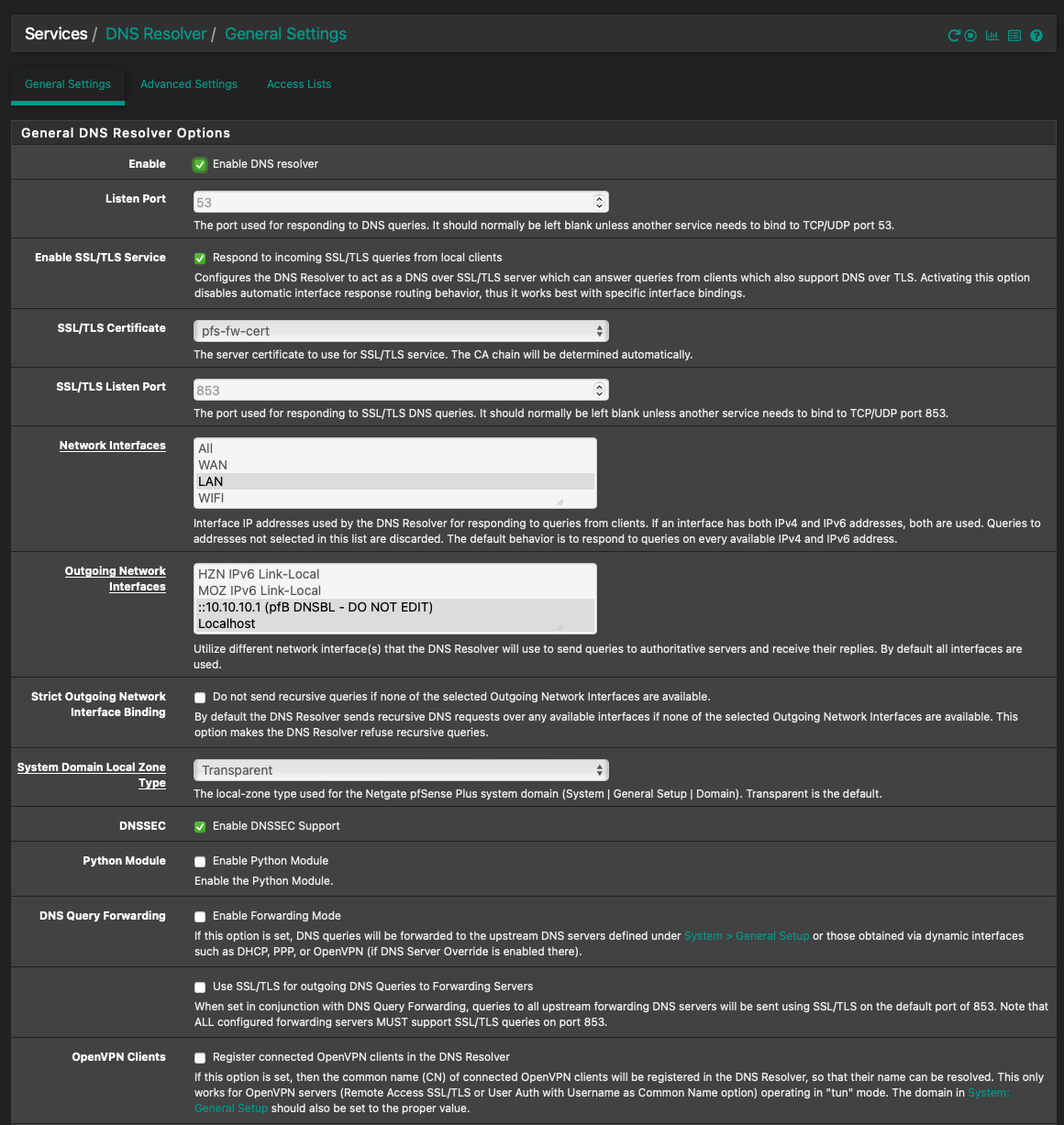
@Gertjan
Yeah I'm calling Fox or MSNBC saying "freaking unbound resolver failing and no one seems to actually address the issue" that's what I'd be saying right?
Cause apparently the thing is so fragile an hiccup blows it away.
Anyway, aboutdns_reply.logthat's empty[23.09-RELEASE][admin@pfs-fw]/root: cat /var/log/pfblockerng/dns_reply.log [23.09-RELEASE][admin@pfs-fw]/root:No, I'm not forwarding. This has been clear like water from the start.
And about the DHCP Registration option, that got me going around for a while, but the news here are: If you enable KEA DHCP backend, that option goes away. It was not ticked anyway.I don't have flapping interfaces,
My pfBlockerNG config already checks for DNSBL feeds every hour or so. (EDIT: checked, I have 4 DNSBL lists, three update every 2h, one every 4h)
I have dual-WAN. I'm not commenting on the "change country bit" because its just starting to get ridiculous like some parts of your comments I didn't really appreciate, but moving on...@johnpoz
here's the start/stop log entries for unbound for the last three days
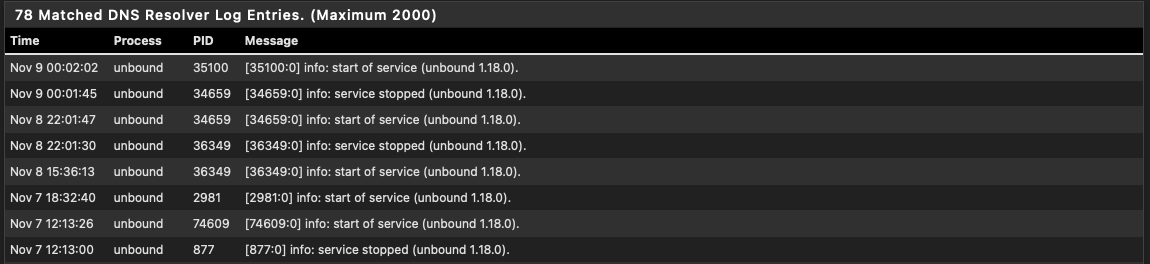
And:
[23.09-RELEASE][admin@pfs-fw]/root: unbound-control -c /var/unbound/unbound.conf lookup . The following name servers are used for lookup of . ;rrset 31141 13 1 11 5 . 31141 IN NS a.root-servers.net. . 31141 IN NS b.root-servers.net. . 31141 IN NS c.root-servers.net. . 31141 IN NS d.root-servers.net. . 31141 IN NS e.root-servers.net. . 31141 IN NS f.root-servers.net. . 31141 IN NS g.root-servers.net. . 31141 IN NS h.root-servers.net. . 31141 IN NS i.root-servers.net. . 31141 IN NS j.root-servers.net. . 31141 IN NS k.root-servers.net. . 31141 IN NS l.root-servers.net. . 31141 IN NS m.root-servers.net. . 31141 IN RRSIG NS 8 0 518400 20231121210000 20231108200000 46780 . Dez3g0tBHaJpwK0mSw4kEhBGlITDUeu4+IDZ3Wtjp4tgc+ZfaQlqVcsbUWw+bjkWkFz81UGpl6Ru+JZQUT3Tg3K2h14KUzOexBWPoiOH4QnjU3QiVnkPQjW7y5ywx7AtsDHYH1L+fwf6UXu87z+xBQ9KwMzOMTQ9sk0qJDZV4+4pFH64xY8AmsxFVaKjP+RF3TiAnpQ8Re+CdsP5mxGeTlPqjrslb0KGKFVYyJ54zZ9mIOHAxM1BTMKN9IpEWSTtNHltCzjRUzN3y2BqsZOTUXeIkKAsKqeSEr458sgvGY2qUZr2/msO+tDnlUx7ccVKmj1fjNN05g9GlehxgYal5w== ;{id = 46780} ;rrset 81667 1 0 8 3 m.root-servers.net. 81667 IN A 202.12.27.33 ;rrset 31141 1 0 3 3 m.root-servers.net. 31141 IN AAAA 2001:dc3::35 ;rrset 81665 1 0 8 3 l.root-servers.net. 81665 IN A 199.7.83.42 ;rrset 81666 1 0 8 3 l.root-servers.net. 81666 IN AAAA 2001:500:9f::42 ;rrset 81664 1 0 8 3 k.root-servers.net. 81664 IN A 193.0.14.129 ;rrset 82306 1 0 8 3 k.root-servers.net. 82306 IN AAAA 2001:7fd::1 ;rrset 81648 1 0 8 3 j.root-servers.net. 81648 IN A 192.58.128.30 ;rrset 81648 1 0 8 3 j.root-servers.net. 81648 IN AAAA 2001:503:c27::2:30 ;rrset 81635 1 0 8 3 i.root-servers.net. 81635 IN A 192.36.148.17 ;rrset 81635 1 0 8 3 i.root-servers.net. 81635 IN AAAA 2001:7fe::53 ;rrset 31141 1 0 3 3 h.root-servers.net. 31141 IN A 198.97.190.53 ;rrset 81745 1 0 8 3 h.root-servers.net. 81745 IN AAAA 2001:500:1::53 ;rrset 31141 1 0 3 3 g.root-servers.net. 31141 IN A 192.112.36.4 ;rrset 82305 1 0 8 3 g.root-servers.net. 82305 IN AAAA 2001:500:12::d0d ;rrset 31141 1 0 3 3 f.root-servers.net. 31141 IN A 192.5.5.241 ;rrset 31141 1 0 3 3 f.root-servers.net. 31141 IN AAAA 2001:500:2f::f ;rrset 81736 1 0 8 3 e.root-servers.net. 81736 IN A 192.203.230.10 ;rrset 81736 1 0 8 3 e.root-servers.net. 81736 IN AAAA 2001:500:a8::e ;rrset 81731 1 0 8 3 d.root-servers.net. 81731 IN A 199.7.91.13 ;rrset 31141 1 0 3 3 d.root-servers.net. 31141 IN AAAA 2001:500:2d::d ;rrset 81730 1 0 8 3 c.root-servers.net. 81730 IN A 192.33.4.12 ;rrset 82312 1 0 8 0 c.root-servers.net. 82312 IN AAAA 2001:500:2::c ;rrset 82311 1 0 8 0 b.root-servers.net. 82311 IN A 199.9.14.201 ;rrset 82312 1 0 8 3 b.root-servers.net. 82312 IN AAAA 2001:500:200::b ;rrset 81689 1 0 8 3 a.root-servers.net. 81689 IN A 198.41.0.4 ;rrset 81689 1 0 8 3 a.root-servers.net. 81689 IN AAAA 2001:503:ba3e::2:30 Delegation with 13 names, of which 0 can be examined to query further addresses. It provides 26 IP addresses. 2001:503:ba3e::2:30 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 198.41.0.4 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:200::b expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 199.9.14.201 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:2::c expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.33.4.12 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:2d::d expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 199.7.91.13 expired, rto 3613192 msec, tA 1 tAAAA 0 tother 0. 2001:500:a8::e expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.203.230.10 expired, rto 3613192 msec, tA 1 tAAAA 0 tother 0. 2001:500:2f::f expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.5.5.241 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:12::d0d expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.112.36.4 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:1::53 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 198.97.190.53 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:7fe::53 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.36.148.17 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:503:c27::2:30 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 192.58.128.30 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:7fd::1 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 193.0.14.129 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 2001:500:9f::42 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 199.7.83.42 expired, rto 3613192 msec, tA 1 tAAAA 0 tother 0. 2001:dc3::35 expired, rto 3613192 msec, tA 0 tAAAA 0 tother 0. 202.12.27.33 expired, rto 3613192 msec, tA 1 tAAAA 0 tother 0. -
@maverickws said in Unbound Resolver - failed to resolve host:
general settings config
seems you have
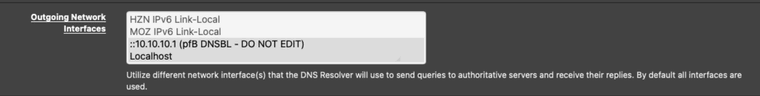
pointing to (::10.10.10.1 ) selected, was that recommended somewhere?
Seems wrong to have it selected given the description of the Outgoing Network Interface
"Utilize different network interface(s) that the DNS Resolver will use to send queries to authoritative servers and receive their replies. By default all interfaces are used."by the way my entry on that field does not show the :: in front

The address is actually (normally) from this setting (a web server on a virtual IP)
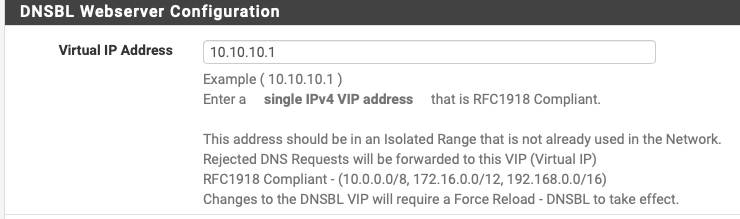
-
@jrey the
::come from IPv6 being in use. It's automatically added, had no part in it.
I don't remember why that interface is selected but I vaguely remember reading somewhere it should be used. (Well, I'm thinking, if it's not selected, how can the DNSBL filters work? maybe I'm wrong here).What I have selected is:
On the Inbound, I have only local interfaces selected.
On the Outbound, I have only those two (and also why I focused that bit on the screenshot).Under pfBlockerNG DNSBL Webserver Configuration the entry is exactly like yours, with the
10.10.10.1. -
@maverickws said in Unbound Resolver - failed to resolve host:
@maverickws said in Unbound Resolver - failed to resolve host:
the :: come from IPv6 being in use
Sorry I missed you have IPv6 running
if it's not selected, how can the DNSBL filters work?
has nothing to do with DNSBL filters, has to do with
"Rejected DNS Requests will be forwarded to this VIP (Virtual IP)"- poorly worded, I'l give you that, but your browser will be directed to this VIP Webpage when a request if blocked by DNSBL.Meaning when a DNS Lookup fails because of the DNSBL , it will display a "Web Page" saying you are blocked. (if you are setup that way, there are options to prevent even this was well)
There is no way that IP can respond as a
"DNS Resolver will use to send queries to authoritative servers" type requestsThe DNSBL will works independent of that setting.
-
@jrey in regard to the requests blocked by the DNSBL I get forwarded to the error page and everything in that aspect seemed like it was working fine.
But for debugging purpose I've removed the selection from the pfBlockerNG VIP. Let's see how this goes.
-
@maverickws said in Unbound Resolver - failed to resolve host:
requests blocked by the DNSBL I get forwarded to the error page
and it would, all that shows is you are running the webpage.
You can easily test that - hit a page you know is blocked by DNSBL, still get the page? you should.
The change on the resolver setting, will only stop the resolver from trying to talk to that IP as a DNS server which it is not.
I'm not sure at this point if you might need to force a Resolver restart, or it may have done one already. check the log for a restart, if you don't see one, do one.
This wording in the DNS Resolver documentation is also suspect
"it will source the query from whichever interface and IP address is closest to the target server from a routing perspective."is 10.10.10.1 (even selection is wrong) closer than another root/authoritative server. I would think the answer is yes. Which them implies most of your DNS queries are going there first. (seems closer) Then will be trying to figure out what that response it likely didn't get really was (ie timeout) , followed by who's next on the list if there is still time.
Cheers