pfSense 2.7 + Captive Portal - Autentication URL not found
-
Hello.
Last weekend I update my pfSense from 2.6 to 2.7.
Now I have a problem with Captive Portal.
Bellow the screen error, its impossible to autenticate.
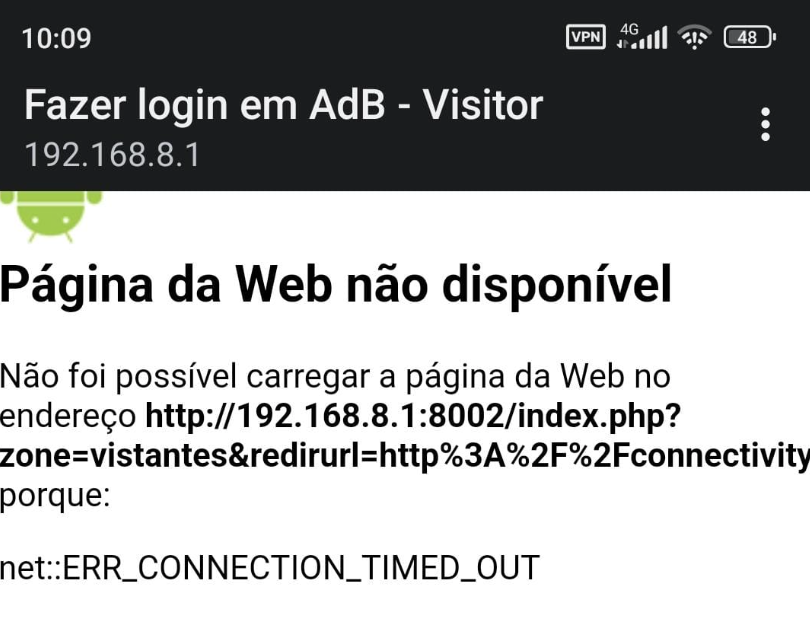
I tryed to manual modify the file from Captive Portal, not working.
Issue 14598I alread fix all the Patchs, restart the pfSense, with no success.
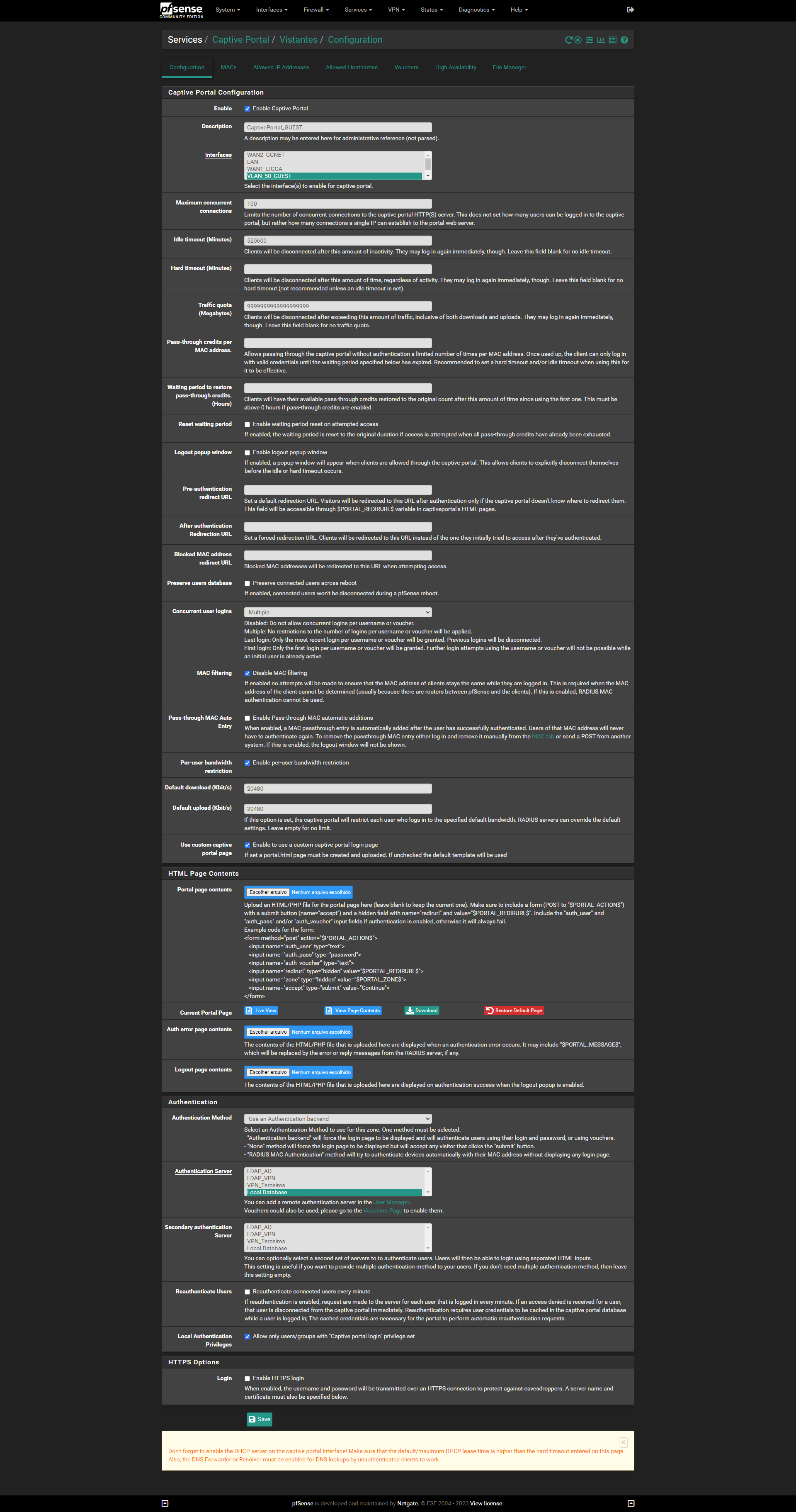
Bellow my configurations.
I need some help, what I can do?
Regards
-
@rec-br9 said in pfSense 2.7 + Captive Portal - Autentication URL not found:
what I can do?
Try this :

should be turned on only after yo have logged into the captive portal.
-
@Gertjan, thanks to awnser.
The problem is in captive portal WebServer.
The problem continius when I turn OFF the local VPN.
I have the same problem in a computer.
Regards.
-
@rec-br9
That
http://192.168.8.1:8002/index.php?zone=vistantes&redirurl=http://.......
it was you entered that URL or did you get it from the captive portal web server ?That URL is created here :
/var/etc/nginx-vistantes-CaptivePortal.conf - line 45.
That file is the main config file of the captive portal http web server, listing on port 8002.The pf firewall redirects all http (destination port 80) to the "interface IP" port 8002.
From there on, the captive portal web server takes over.Can you show :
sockstat -4 | grep '8002' -
@Gertjan said in pfSense 2.7 + Captive Portal - Autentication URL not found:
http://192.168.8.1:8002/index.php?zone=vistantes&redirurl=http://.......
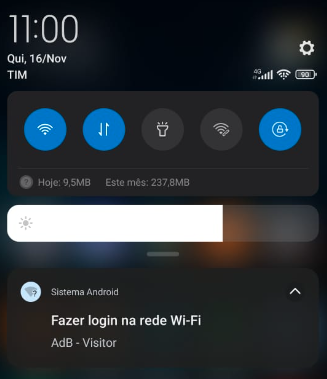
it was you entered that URL or did you get it from the captive portal web server ?I received automatic from Captive Portal when I connect in a Wireles, like this image bello. "Make loggin in a AdB - Visitor".
Bellow my code from /var/etc/nginx-vistantes-CaptivePortal.conf
# # nginx configuration file pid /var/run/nginx-vistantes-CaptivePortal.pid; user root wheel; worker_processes 6; error_log /dev/null; error_log syslog:server=unix:/var/run/log,facility=local5; events { worker_connections 1024; } http { include /usr/local/etc/nginx/mime.types; default_type application/octet-stream; add_header X-Frame-Options SAMEORIGIN; server_tokens off; sendfile off; access_log syslog:server=unix:/var/run/log,facility=local5 combined; limit_conn_zone $binary_remote_addr zone=addr:10m; keepalive_timeout 0; server { listen 8002; listen [::]:8002; client_max_body_size 200m; gzip on; gzip_types text/plain text/css text/javascript application/x-javascript text/xml application/xml application/xml+rss application/json; limit_conn addr 100; if ($http_host ~* 192.168.8.1) { set $cp_redirect no; } if ($cp_redirect = '') { rewrite ^ /index.php?zone=vistantes&redirurl=$request_uri break; } log_not_found off; root "/usr/local/captiveportal"; location / { index index.php index.html index.htm; } location ~ \.inc$ { deny all; return 403; } location ~ \.php$ { try_files $uri =404; # This line closes a potential security hole # ensuring users can't execute uploaded files # see: https://forum.nginx.org/read.php?2,88845,page=3 fastcgi_pass unix:/var/run/php-fpm.socket; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; # Fix httpoxy - https://httpoxy.org/#fix-now fastcgi_param HTTP_PROXY ""; fastcgi_read_timeout 180; include /usr/local/etc/nginx/fastcgi_params; } location ~ (^/status$) { allow 127.0.0.1; deny all; fastcgi_pass unix:/var/run/php-fpm.socket; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; # Fix httpoxy - https://httpoxy.org/#fix-now fastcgi_param HTTP_PROXY ""; fastcgi_read_timeout 360; include /usr/local/etc/nginx/fastcgi_params; } } }Bellow the rules from this interface.
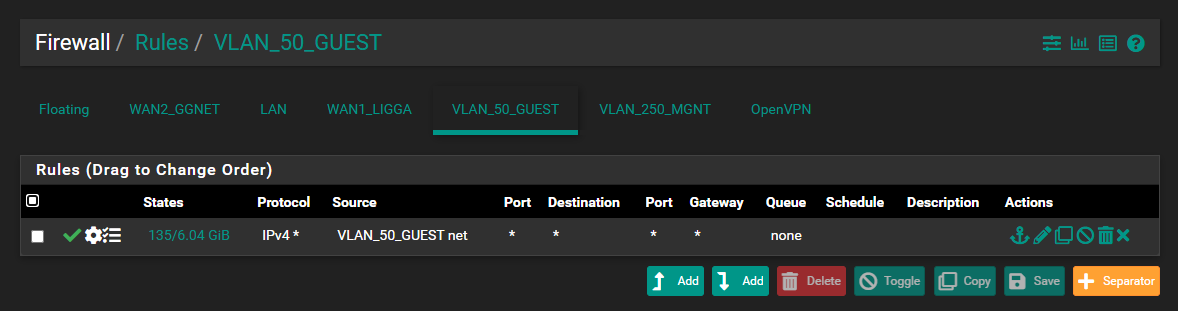
Best regards.
-
@Gertjan said in pfSense 2.7 + Captive Portal - Autentication URL not found:
Can you show :
sockstat -4 | grep '8002'
?
Btw : You and I have the same "/var/etc/nginx-XXXXXX-CaptivePortal.conf" file. Only the name of the zone changes.
Probably not related, but this seems strange to me :
error_log /dev/null; error_log syslog:server=unix:/var/run/log,facility=local5;You can use Diagnostics Packet Capture on your VLAN_50_GUEST interface, port 8002, protocol TCP.
192.168.8.1 is a /24 network, right ?
DHCP 192.168.8.1/24 is ok ?What happens when you remove your firewall rule and put this rule in place :
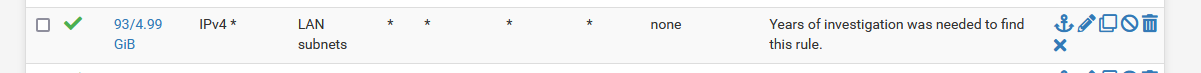 where LAN address = VLAN_5_GUEST address.
where LAN address = VLAN_5_GUEST address.Are you using the default Netgate login page ?
What happens when you use the Live view and View page content buttons :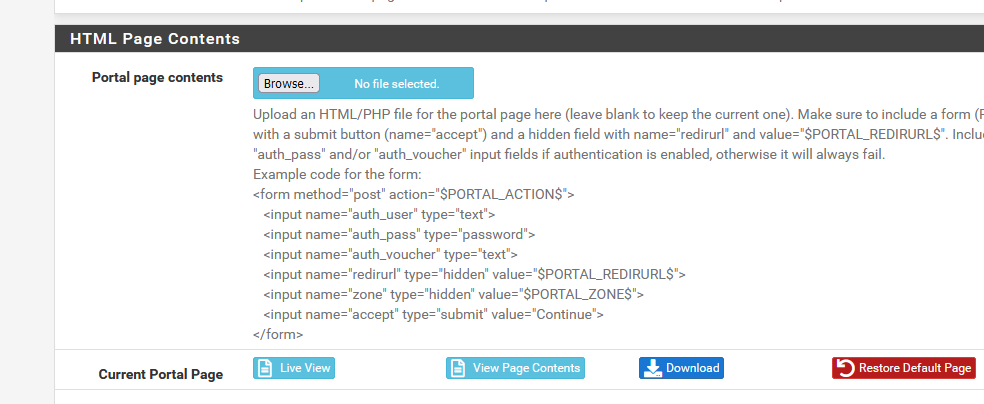
-
@Gertjan, thanks again.
sockstat -4 | grep '8002'
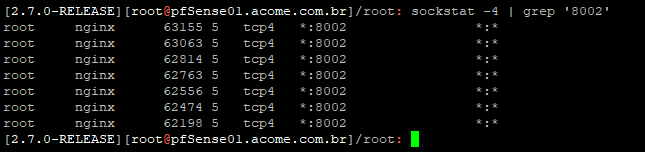
The VLAN_50_GUEST / 24
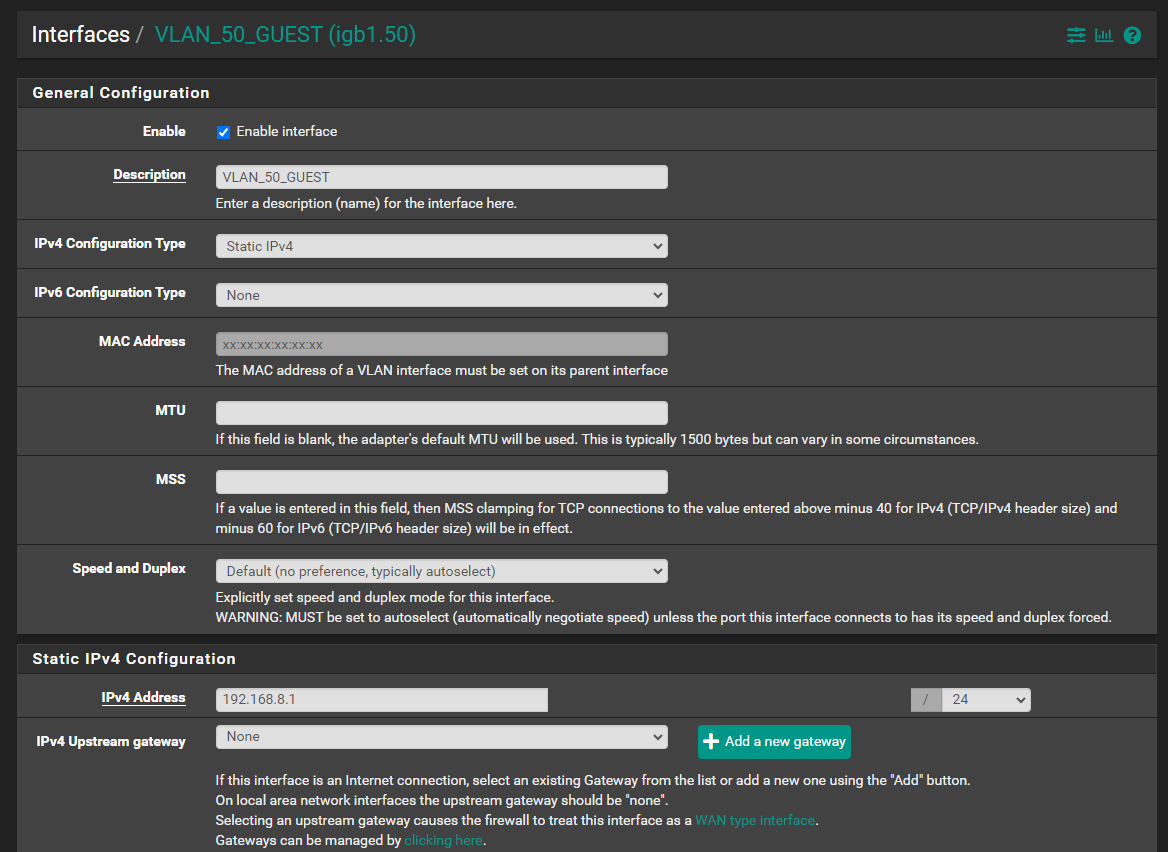
DHCP / 24
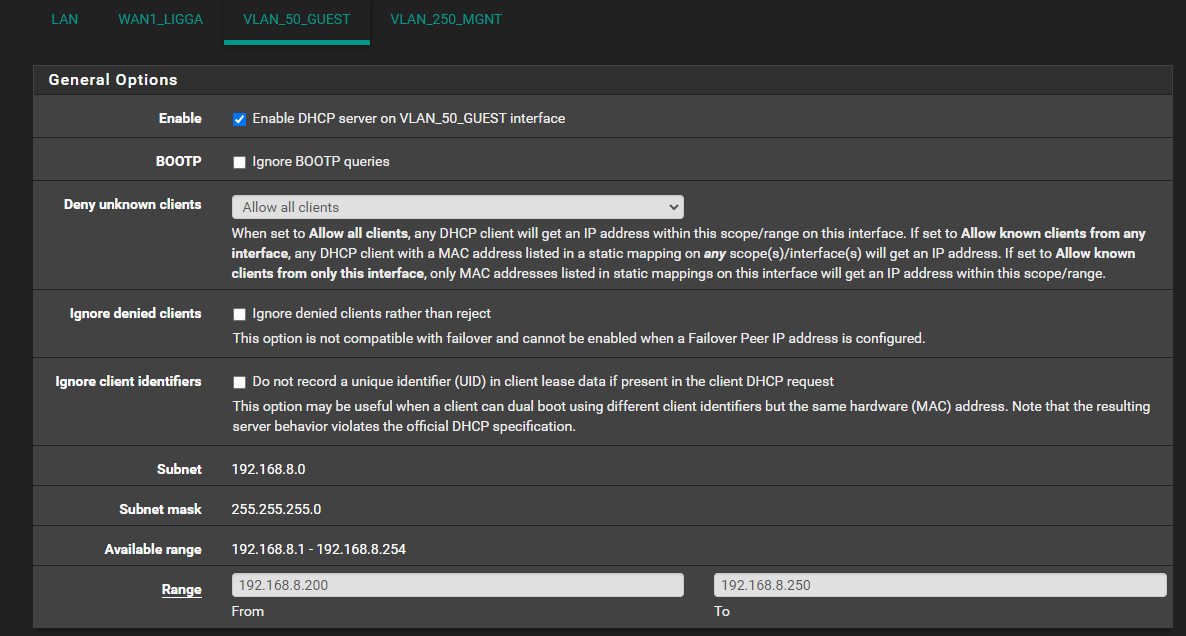
pfSense Rule VLAN_50_Guest
I changed to accept all the trafic, from all the interfaces. Continious the same error.
I deleted and recreate the rule.
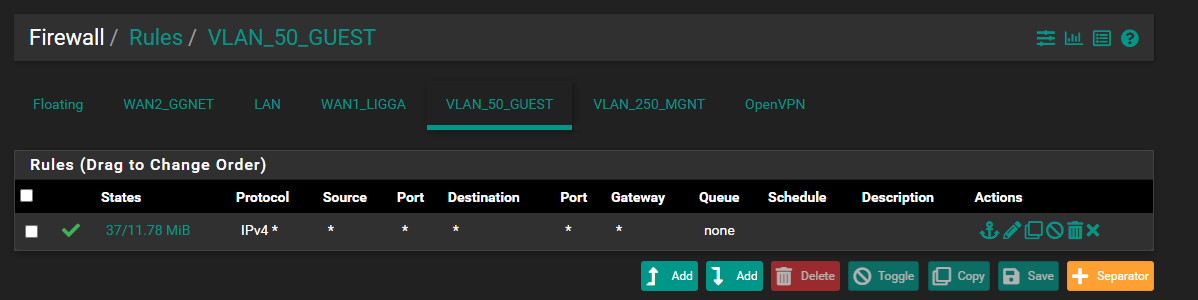
DEFAULT NETGATE LOGIN PAGE
When I remove the custom loggin page, I have the same error.
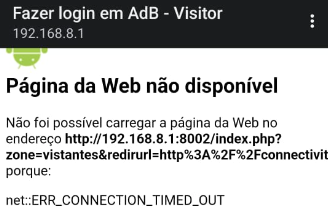
-
@Gertjan, today I update to 2.7.1 version, the problem continues. Regards.
-
@Gertjan, result of "Packet Capture".
Packet Capture Output: /tmp/packetcapture-igb1.50-20231218145414.pcap
17:50:56.426715 IP 192.168.8.1.67 > 192.168.8.60.68: UDP, length 307 17:50:56.441553 IP 192.168.8.1.67 > 192.168.8.60.68: UDP, length 307 17:50:56.517564 ARP, Request who-has 192.168.8.1 tell 192.168.8.60, length 42 17:50:56.517599 ARP, Reply 192.168.8.1 is-at 08:35:71:11:d8:45, length 28 17:50:56.693469 IP 192.168.8.60.18946 > 192.168.8.1.53: UDP, length 47 17:50:56.693613 IP 192.168.8.60.51224 > 192.168.8.1.53: UDP, length 32 17:50:56.693777 IP 192.168.8.1.53 > 192.168.8.60.18946: UDP, length 63 17:50:56.693952 IP 192.168.8.1.53 > 192.168.8.60.51224: UDP, length 48 17:50:56.718548 IP 192.168.8.60.46298 > 142.250.219.196.443: tcp 0 17:50:56.719798 IP 192.168.8.60.48394 > 142.251.129.163.80: tcp 0 17:50:56.719871 IP 142.251.129.163.80 > 192.168.8.60.48394: tcp 0 17:50:56.722575 IP 192.168.8.60.48394 > 142.251.129.163.80: tcp 0 17:50:56.729029 IP 192.168.8.60.48394 > 142.251.129.163.80: tcp 227 17:50:56.729073 IP 142.251.129.163.80 > 192.168.8.60.48394: tcp 0 17:50:56.739880 IP 142.251.129.163.80 > 192.168.8.60.48394: tcp 404 17:50:56.739910 IP 142.251.129.163.80 > 192.168.8.60.48394: tcp 0 17:50:56.744819 IP 192.168.8.60.48394 > 142.251.129.163.80: tcp 0 17:50:56.746418 IP 192.168.8.60.48394 > 142.251.129.163.80: tcp 0 17:50:56.746441 IP 142.251.129.163.80 > 192.168.8.60.48394: tcp 0 17:50:57.616563 IP 192.168.8.60.46298 > 142.250.219.196.443: tcp 0 17:51:12.007136 ARP, Request who-has 192.168.8.1 tell 192.168.8.60, length 42 17:51:12.007155 ARP, Reply 192.168.8.1 is-at 08:35:71:11:d8:45, length 28 17:51:31.157585 IP 192.168.8.60.46340 > 142.250.219.196.443: tcp 0 17:51:31.157708 IP 192.168.8.60.48436 > 142.251.129.163.80: tcp 0 17:51:31.157751 IP 142.251.129.163.80 > 192.168.8.60.48436: tcp 0 17:51:31.159824 IP 192.168.8.60.48436 > 142.251.129.163.80: tcp 0 17:51:31.160607 IP 192.168.8.60.48436 > 142.251.129.163.80: tcp 227 17:51:31.160635 IP 142.251.129.163.80 > 192.168.8.60.48436: tcp 0 17:51:31.176355 IP 142.251.129.163.80 > 192.168.8.60.48436: tcp 404 17:51:31.176421 IP 142.251.129.163.80 > 192.168.8.60.48436: tcp 0 17:51:31.180075 IP 192.168.8.60.48436 > 142.251.129.163.80: tcp 0 17:51:31.181185 IP 192.168.8.60.48436 > 142.251.129.163.80: tcp 0 17:51:31.181223 IP 142.251.129.163.80 > 192.168.8.60.48436: tcp 0 17:51:32.281166 IP 192.168.8.60.46340 > 142.250.219.196.443: tcp 0 17:51:34.241039 IP 192.168.8.60.46340 > 142.250.219.196.443: tcp 0 17:51:38.321484 IP 192.168.8.60.46340 > 142.250.219.196.443: tcp 0 -
@Gertjan, I found the problem!
Is my UBIQUITI Wi-Fi configuration.
When I marked this option the "GUEST Wi-Fi" isolate the client.
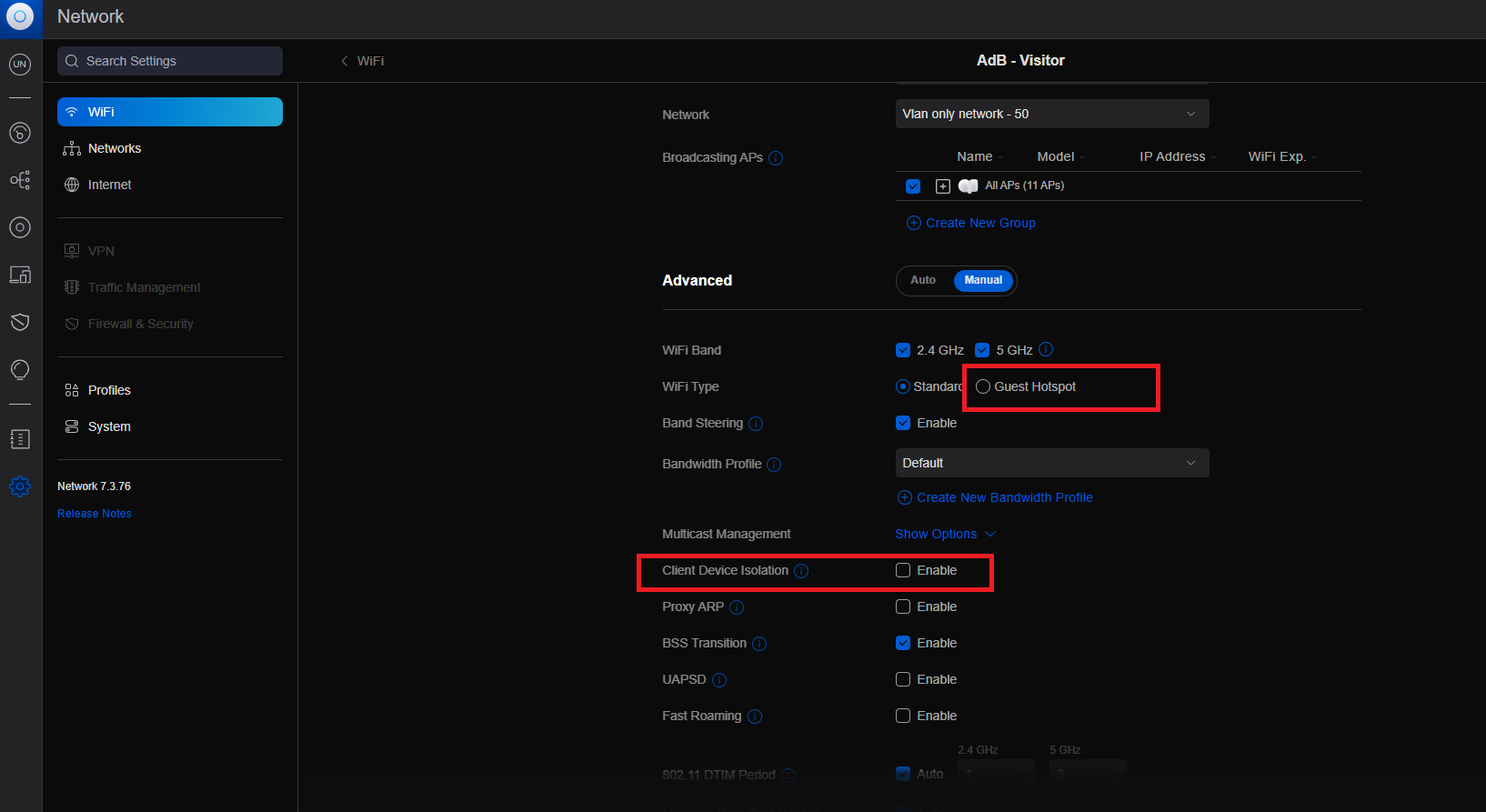 .
.The problem has been solved.
Thanks a lot.
Regards.