Not able to block facebook website
-
@jrey Not denying that

-
Other options you can use..
You can use Snort with an open AppID custom text rule for Facebook and just set it to block.
Or my favorite Squidguard with Squid and add Facebook to the block list. But Squid is not really recommended because of it's level of complexity.
-
@rajukarthik said in Not able to block facebook website:
@jrey I tried it but still facebook is accessible. Could you please help
I can and will help.
I just tried what has been said in the other thread, notably by BBcan177, author of pfBlockerng.
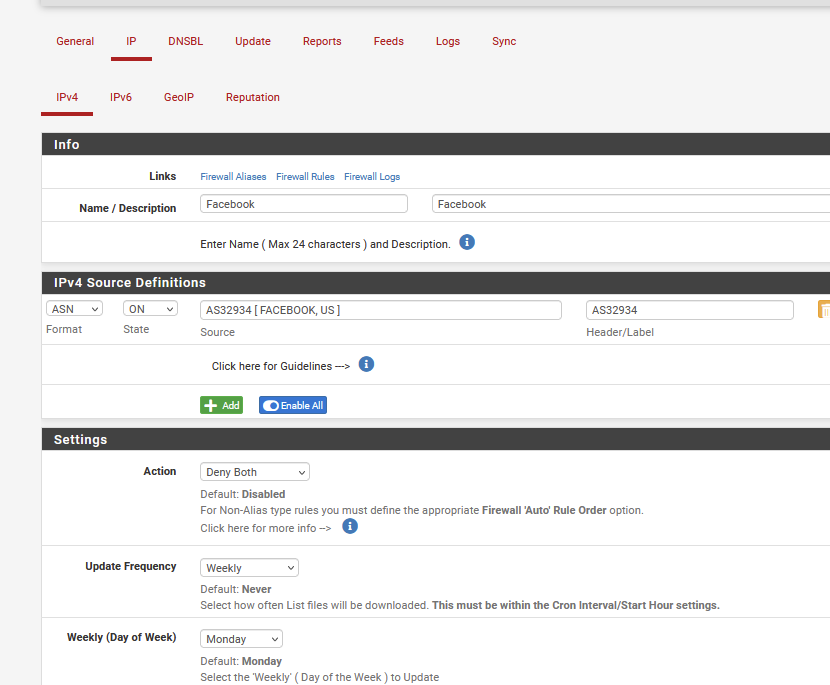
As I have pfBlockerng installed, it tried blocking using "ASN".I've created :
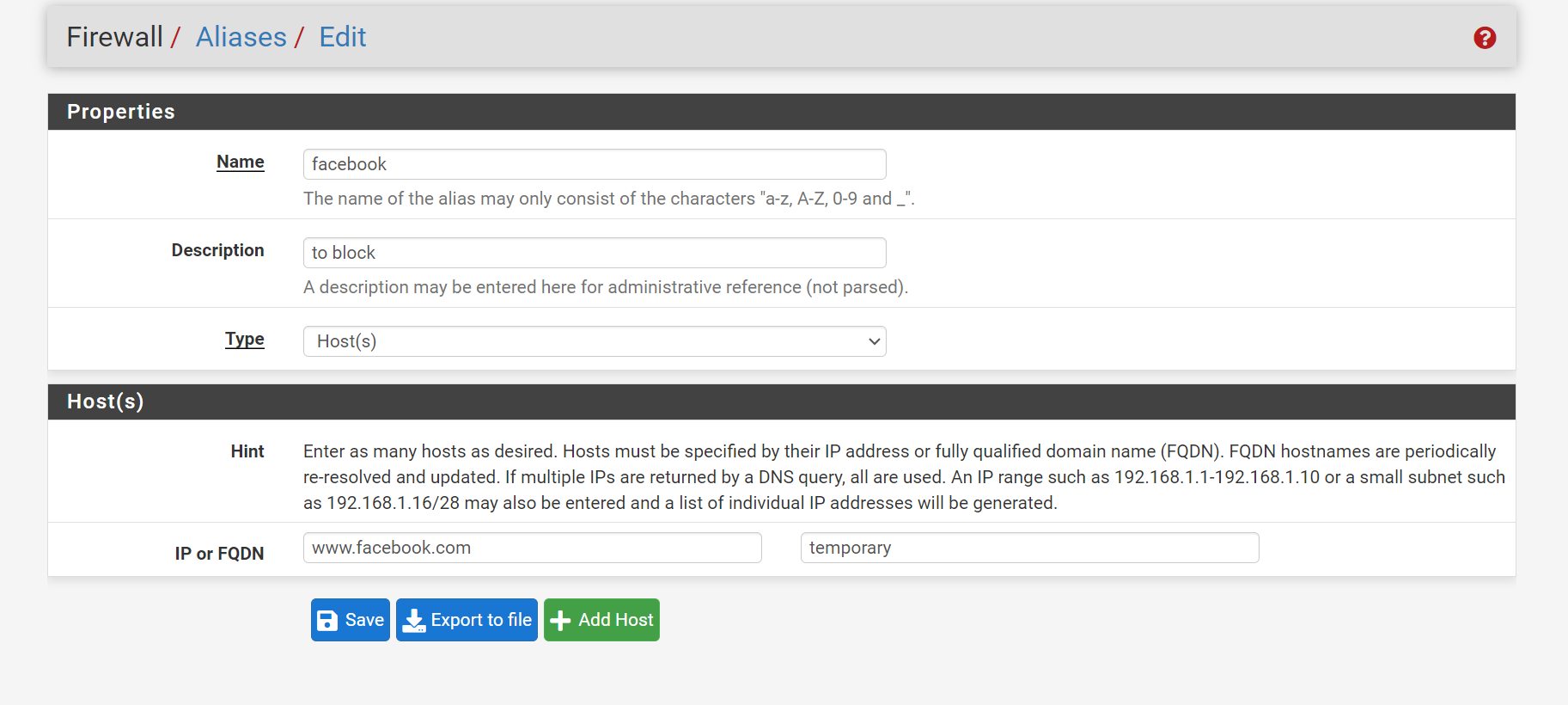
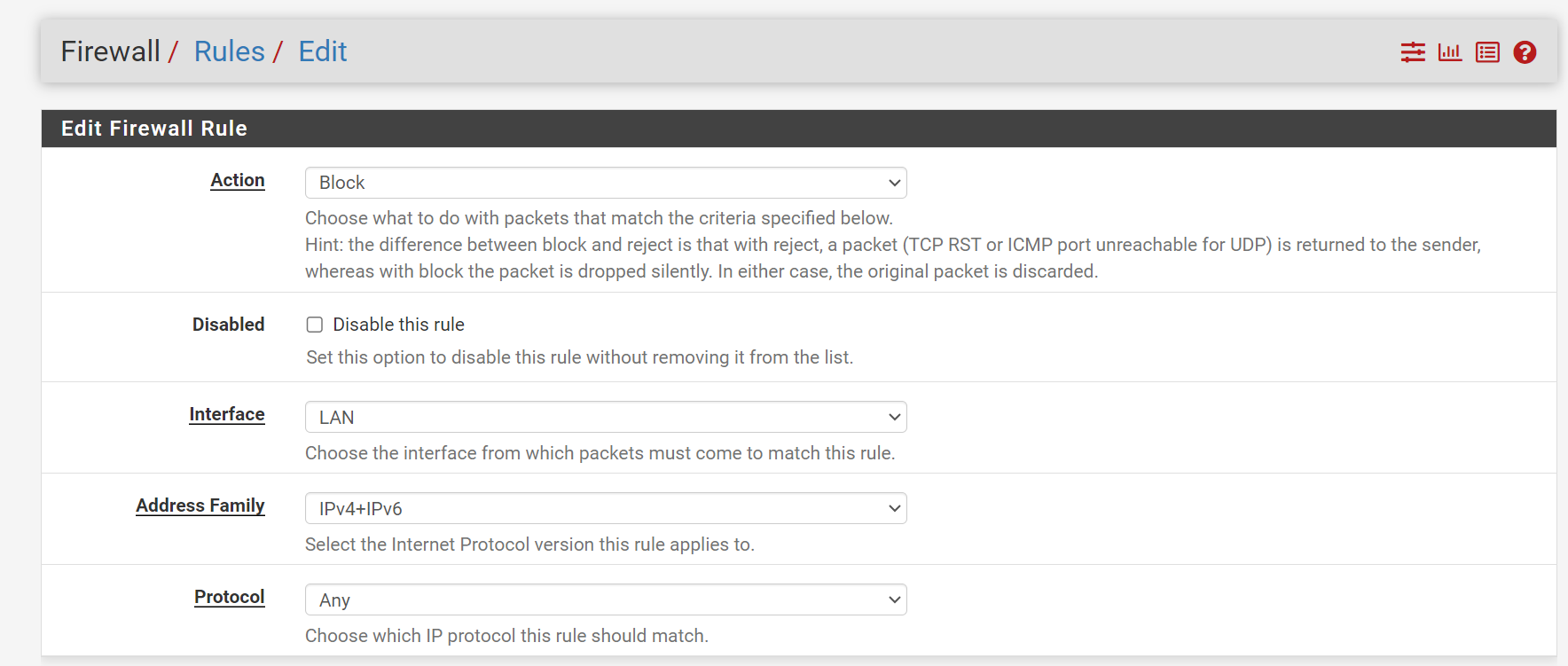
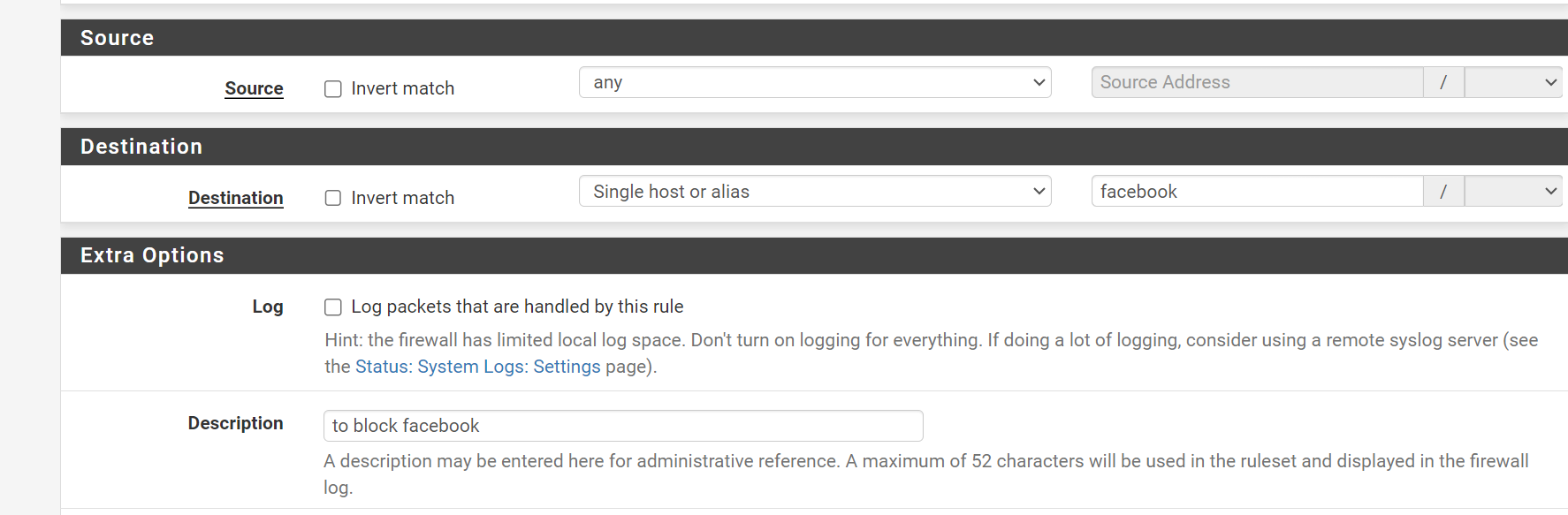
And saved.
And reloaded the config.I knew "ASN" is just a list of IP networks, so I wasn't surprised to see this :
and it did't take long.
You had to be there to believe it : some one was already yelling in the buidling that 'Whatapp" stopped working.Btw : my Whatapp phone app showed me this :
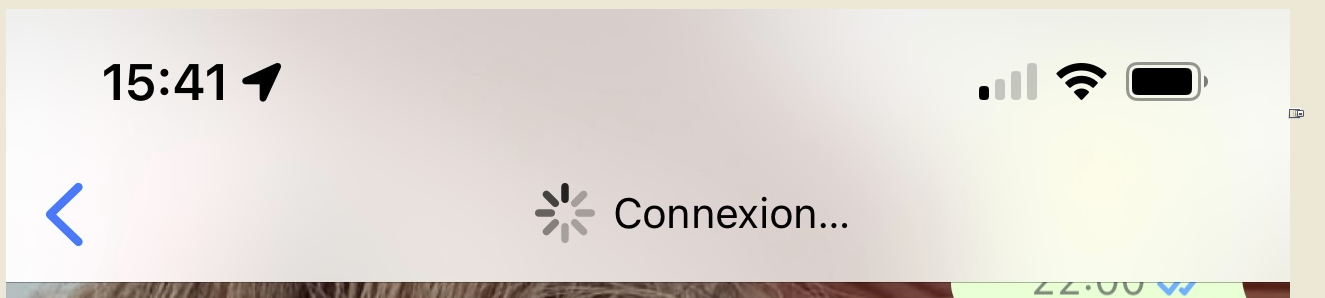
So, sorry @rajukarthik I disagree.
"It works for me ...".
Please tell us what you did.
Or check what I did - I've posted images, and happy to post more details.edit : and now they come to me ..... I'll better undo this "ASN 32934" blocking fast, as I don't want to sleep in the dog house this evening.
-
Of course blocking the ASN directly will work, but what happens when the OP chooses to add other DNSBL rules or features ?
Doesn't appear to me from what has been provided that the DNS path is correct and therefore any client will simply bypass whatever other features of DNSBL may be selected (now or in the future) not just facebook.
Maybe that's important / maybe not. -
@jrey said in Not able to block facebook website:
Of course blocking the ASN directly will work, but what happens when the OP chooses to add other DNSBL rules or features ?
If the OP was trying to block another ASN he could add it to his original pfblocker rule or just create a new alias and new firewall rule.
If you look at my example I block multiple ASN numbers.
The advantage of using pfblocker is its blocking the destination rather than a lookup of the destination
-
You're missing the point, I think -- what if the OP (who said he was new to pfSense) decides he wants to block (say for example ADs) by selecting another DNSBL list.
Last I checked ADs basic alone listed some 158,000+ items, are you suggesting that ASN is the only way to go ??? I suspect that is not the case you are trying to make.
Having a properly working DNS from client to resolution is critical. But you can certainly block facebook with the ASN and then wait for the next question of "I selected (x y or z) and it doesn't work, can you help me?"
Blocking the ASN will certainly work to just block facebook. Just doesn't seem to me to be the underlying question.
just like blocking "facebook.com" isn't all that is required to block facebook. Blocking only their specific ASN doesn't block them entirely either. They like most, also have IP space that is not in directly in their ASN block.
Twitter is really good at this, (not that facebook isn't) they have multiple domains that are embedded everywhere that aren't in any of the twitter registered ASN blocks.
None of the solutions is 100%, but surely we must agree that 0% on the dns front is less than ideal. For laughs I just checked one of the known twitter twit spaces and the IP is actually in the ASN for Akamai International.
Each to his own.
-
@jrey Use Squid Proxy and splice it as transparent mode, install Squid guard and create a rule to block facebooks urls. Any get request will be blocked from the start. No need for DNS resolving it simply blocks the URL http get request. I suspect your DNS is being accessed with DoT DoH DNS over TLS, and many other experimental protocols. A great way to block is in the http get requests works 100% of the time. Just make it simple with transparent mode.
-
I think you are directing your response to the wrong person. I don't have any issue with blocking or DoT, DoH or DNS over TLS or blocking any url if or as required.
The OP on the other hand stated is just learning pfSense. Do you think that Squid Proxy and splice are the way to direct the OP to start, given that basic DNS traffic flow seems to be a challenge, from what has been provided.
But then on the other hand do you ever stop for a minute and wonder why your 2100 is so bloated ? or I think as you put it "I was bogged down so much I had to go back to the last stable version.".
Just because you can, doesn't mean you should or even need to.
https://forum.netgate.com/topic/184125/23-0-5-1-23-09-issues-sg210max?_=1700684164315
Rest assured it is not the device or 23.09. It is likely the laundry list of packages you are running, as listed the thread referenced.
I run 30-60 (varies, typical day ~40 (the arp table currently has 45 entries)) client systems behind a 2100 and although yes there has been a slight increase in Memory usage with 23.09 it is rarely above a 15% baseline, where under 23.05.1 was running around 12%
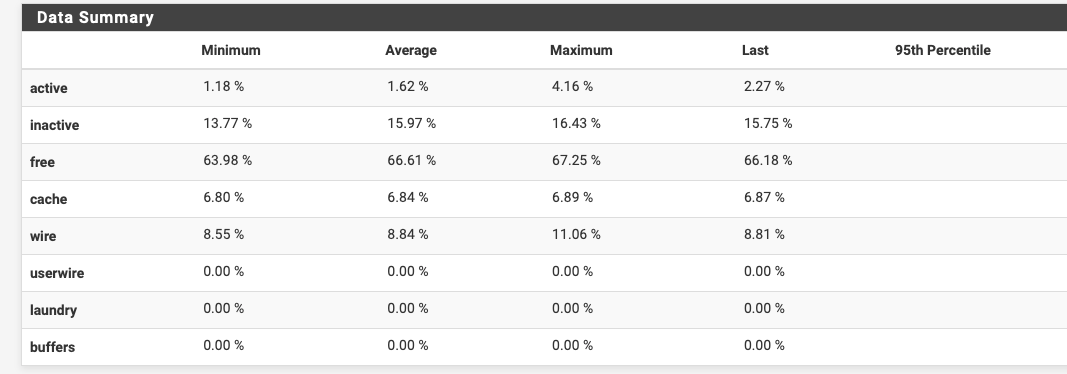
Do whatever works for you. Suggesting more bloat likely not a good choice for most people.
-
I was unaware this user is just starting out. This user is having issues blocking items. I simply provided a different package option. Just simply show casing the other options. Yes I am still running 23.05.1 it's the most stable version I have seen. 23.29 has response time issues for my 2100 alongside Snort's core dump errors. Keep in mind avg memory utilization for me is 20-30% without ClamAV per TAC support I was told it runs better without ClamAV. I agree if DNS blocking is a problem to configure Squid would be very overwhelming. Snort's AppID would be very simple with use of text rules also however Snort on 23.29 does not currently work because of core dumps. It's not just me that has 23.29 issues some packages like Snort do also. If you run the system in bare bones I am sure 23.29 is fine, again, I like to push the 2100's limits because it can do it and has been. It might be Snort's core dumps that caused my issues.
The 2100 is amazing the size of it and all it can do... Wait until the Broadcom BCM2712 quad-core Arm Cortex A76 processor is put into something....Bloat will be nill.
-
@jrey
RT-AX3000-4B90 is my wifi router. I had accessed Pfsense gui via VPN yesterday.
Now i have connected my laptop to the pfsense lan directly and posting the screenshots for your reference.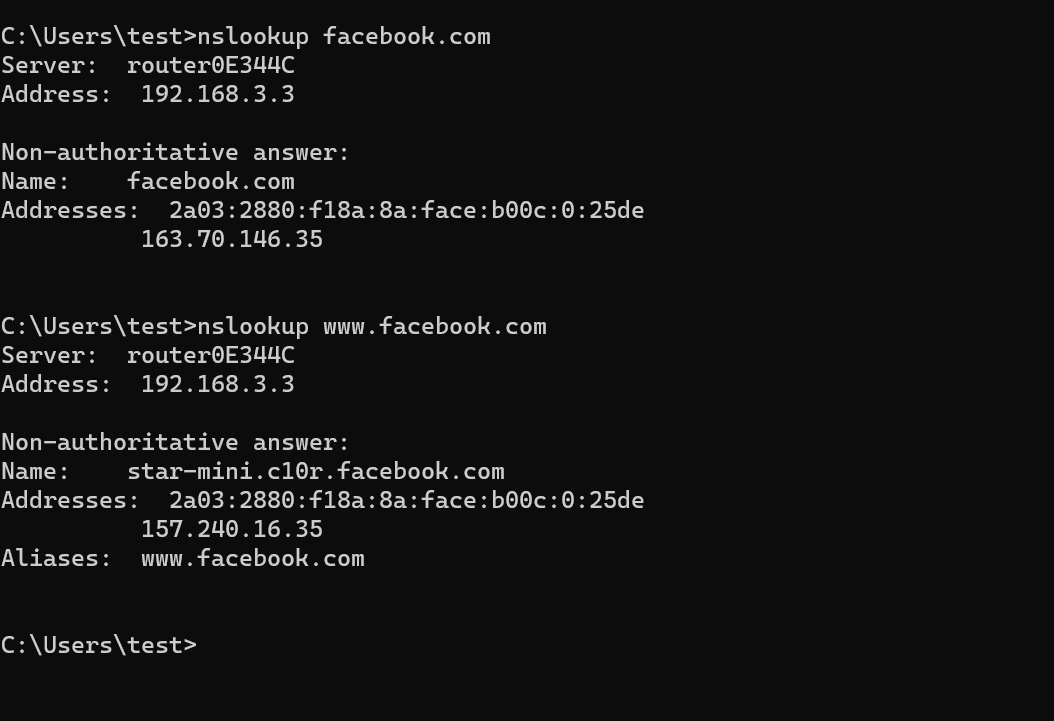
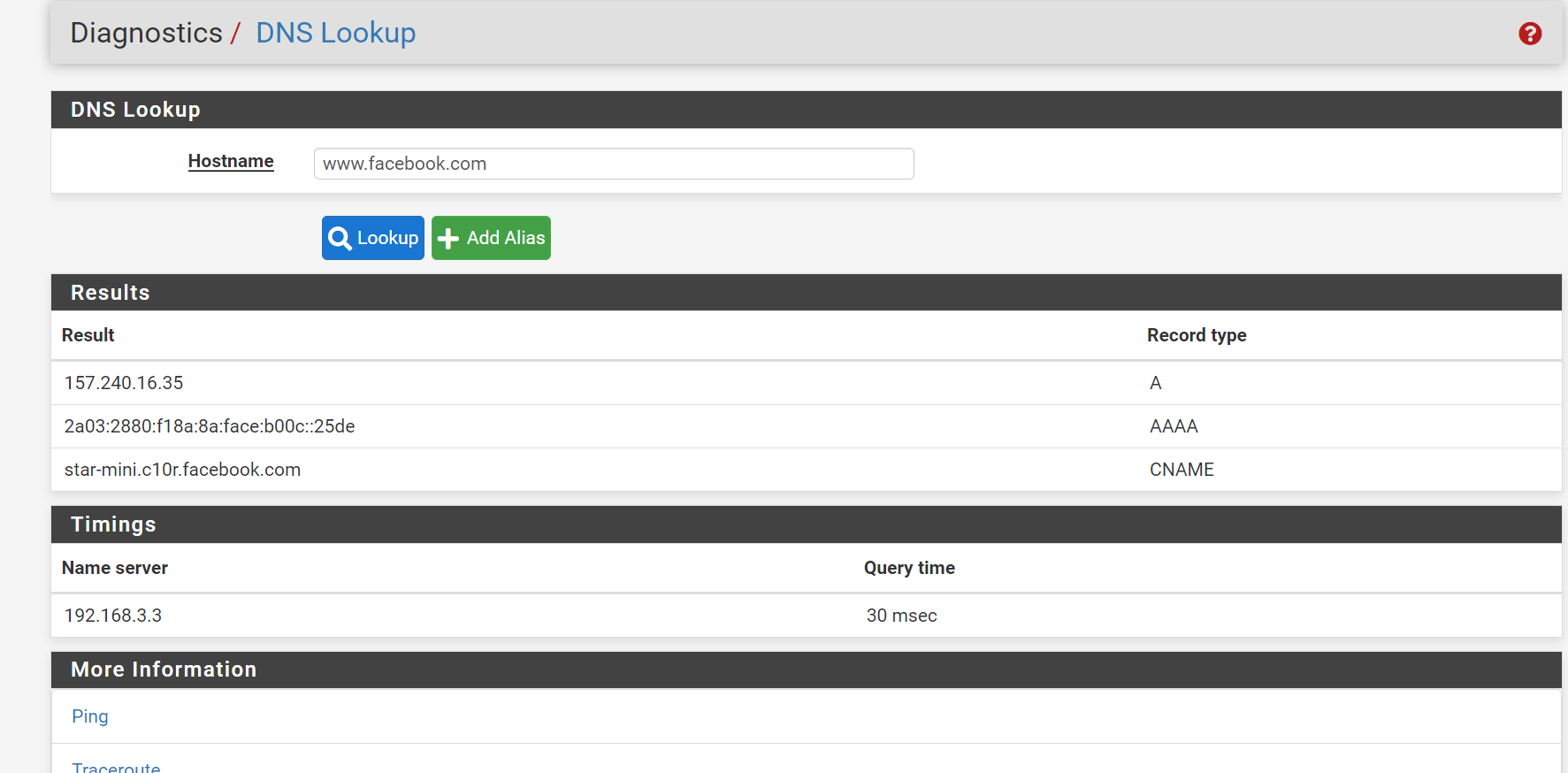
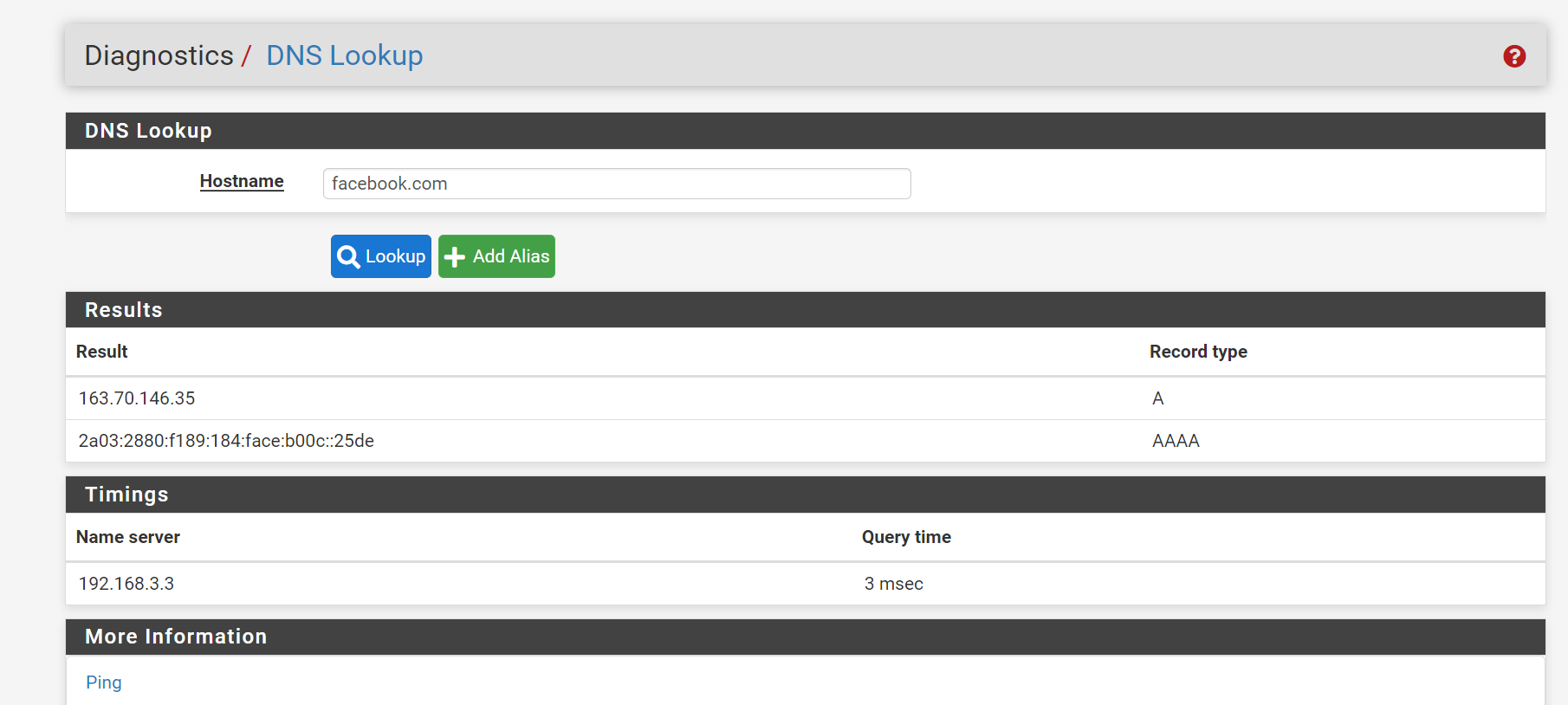
Also I have disabled DNS resolver in my PFsense firewall.
Screenshots for your reference.
I also request you to kindly let me know how to add website entries in dnsbl to block it. I feel I had made mistake in DNSBL entries too.Thanks and Regards,
Karthik -
@rajukarthik said in Not able to block facebook website:
Also I have disabled DNS resolver in my PFsense firewall.
Then who is doing the DNS for your networks ?
Disabling the resolver also disables pfBlockerng.Things get even better :
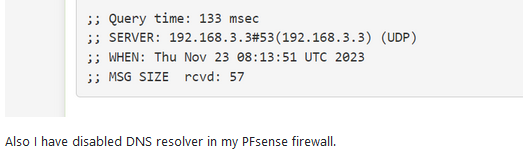
In the top of the image you can see that 192.168.3.3 was answering (port 53 == DNS) over UDP.
But unbound was stopped ?!?
Who is 192.168.3.3 ?
This :
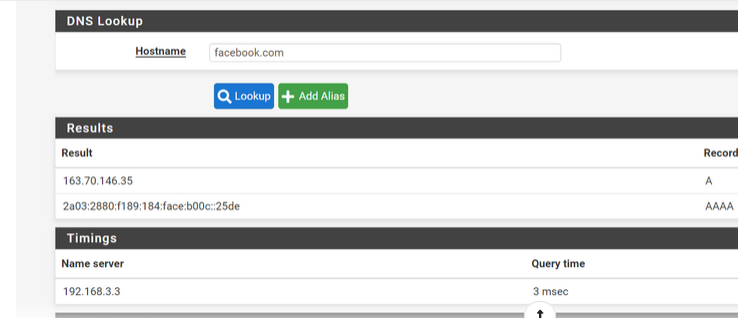
can be explained.
if 'facebook.com' was resolved ones in the past, the resolver keeps the result in it local DNS cache for 'some time' (ok, true : "300" or 5 minutes ... depending your unbound settings).
Ones in the cache, pfBlockerng can't help you anymore : unbound (resolver) will reply directly out of his cache, hence the very fast "3 ms" answer time.
If facebook.com wasn't present in the resolver cache, the resolving will resolve, and this resolving will get parsed by 'pfBlockerng' ..... and thus blocked.General advise : when you handle 'DNS stuff', on pour PC :
ipconfig /flushdnsas your PC is also doing DNS caching.
On pfSense, for good manners : stop and start unbound - the resolver, from the dashboard GUI. This will flush the pfSense resolver DNS cache.
-
@Gertjan Actually 192.168.3.3 is my cisco router. I have configured Pfsense firewall after cisco router.
I have configured 8.8.8.8 and 4.2.2.2 as dns servers in cisco routers.
I have cleared the cache but no luck.I want to block all social media websites, OTTS and torrents (A big list).
-
@jrey could you please help me to configure dnsbl to block websites.
-
@Gertjan said in Not able to block facebook website:
can be explained.
if 'facebook.com' was resolved ones in the past, the resolver keeps the resultnot entirely true at the resolver side. Why.
DNSBL - TDL setup as originally describedso with nothing in place
- dns lookup facebook.com (you should get the IP)
- then add facebook.com to the list
- for it or any DNSBL list to work, you either have to wait for the next cron job cycle, OR as is most recommended Force reload the DNSBL - that restarts the resolver as it restarts during that process.
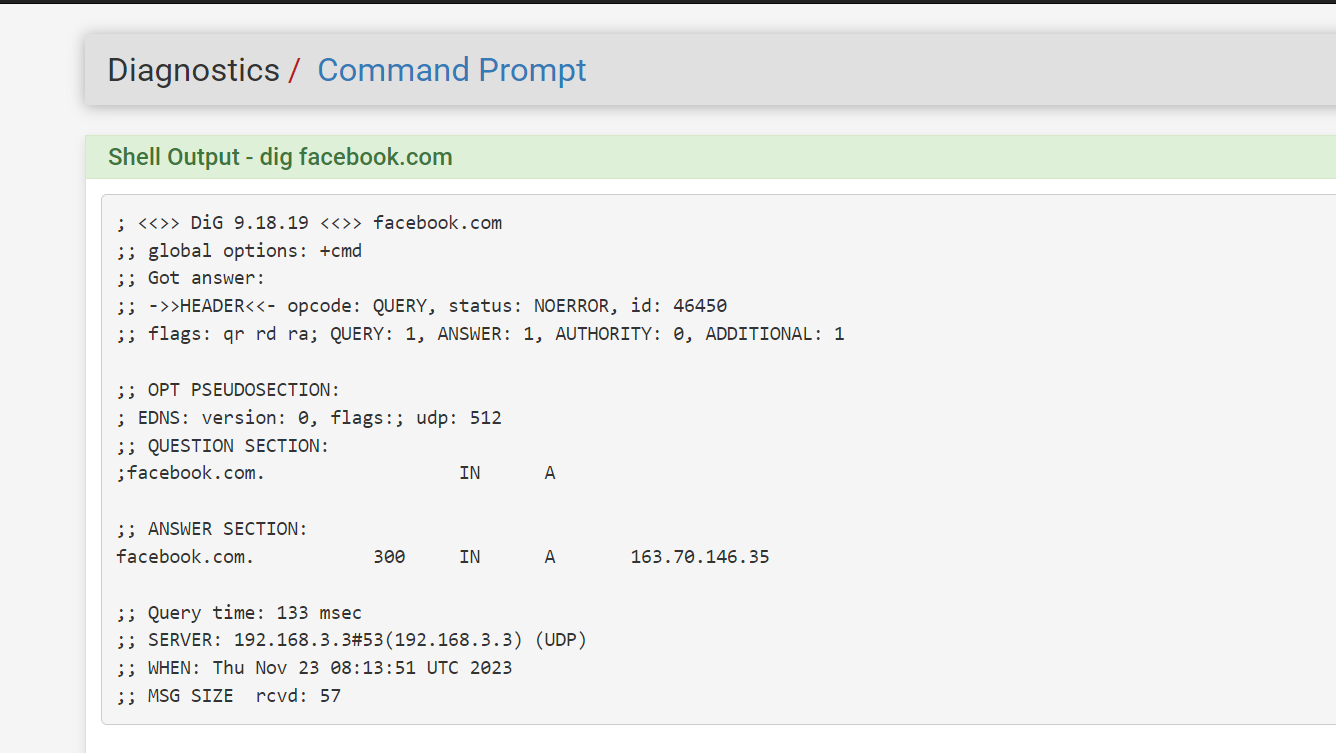
x@LUBUNTU:~$ date Thu 23 Nov 2023 07:09:55 AM EST x@LUBUNTU:~$ dig facebook.com ; <<>> DiG 9.18.18-0ubuntu0.22.04.1-Ubuntu <<>> facebook.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34996 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;facebook.com. IN A ;; ANSWER SECTION: facebook.com. 101 IN A 157.240.229.35 ;; Query time: 40 msec ;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP) ;; WHEN: Thu Nov 23 07:10:00 EST 2023 ;; MSG SIZE rcvd: 57 *** here I added facebook.com to list and reloaded DNSBL x@LUBUNTU:~$ date Thu 23 Nov 2023 07:11:51 AM EST x@LUBUNTU:~$ dig facebook.com ; <<>> DiG 9.18.18-0ubuntu0.22.04.1-Ubuntu <<>> facebook.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 59990 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;facebook.com. IN A ;; ANSWER SECTION: facebook.com. 60 IN A 0.0.0.0 ;; Query time: 40 msec ;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP) ;; WHEN: Thu Nov 23 07:11:59 EST 2023 ;; MSG SIZE rcvd: 57No cache flush performed on the client, just added the entry and reloaded the DNSBL
On pfSense, for good manners : stop and start unbound - the resolver,
no need the cron job if you wait or the force reload if you want results now, does this for you (and is way faster than anyone can navigate to the menu and do it manually)
the appropriate log file reveals:
Saving DNSBL statistics... completed [ 11/23/23 07:11:36 ] Reloading Unbound Resolver (DNSBL python). Stopping Unbound Resolver. Unbound stopped in 2 sec. Additional mounts (DNSBL python): No changes required. Starting Unbound Resolver... completed [ 11/23/23 07:11:38 ]- you need to plan out a path for your DNS traffic to follow. Don't let us tell you, because only you know what other things you have/need your network to do.
- It does seem that you have multiple devices answering the DNS Queries.
- The DNSBL on the Netgate will do nothing if it is not in the DNS traffic path and/or the resolver is not running.
The DNS Resolver should resolve out of the box, if enabled. By default it would go to the root servers for anything it can't answer. (it doesn't have to and can be used with any other upstream DNS, that's a choice you have to make)
I had start a response on the layout, and notice you had posted this
Actually 192.168.3.3 is my cisco router. I have configured Pfsense firewall after cisco router.
I have configured 8.8.8.8 and 4.2.2.2 as dns servers in cisco routers.
I have cleared the cache but no luck.
I want to block all social media websites, OTTS and torrents (A big list).so
WAN <-> Cisco <-> pfSense <-> Clients or WAN <-> Cisco <-> pfSense \<-> Clients or Something Else are all your clients are connected to the Cisco?, perhaps then WAN <-> pfSense <-> Cisco <-> ClientsFollow the DNS traffic and plan the path (you need to get pfSense in the DNS traffic path and generally just in the traffic path, or it won't block anything)
Do you have a network diagram you can share?
I think before you tackle the DNSBL you have to sort out the traffic flow in your case, or at least let us better understand it.
You have mentioned multiple sub nets so far with devices on
192.168.50.*
192.168.3.*
Where is the Netgate (IP)? -
@jrey said in Not able to block facebook website:
No cache flush performed on the client, just added the entry and reloaded the DNSBL
Euh, yeah.
I forgot something else : about the DNS(bl) and cache : ASNs are lists with IP addresses and networks.
=> Has nothing to do with DNS lookups ( !! stupid me !! )
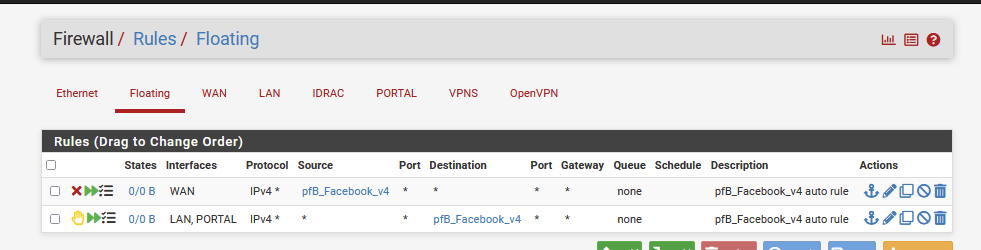
facebook can and will gets resolved just fine. No big deal.What doesn't work anymore : see my "floating" firewall rules above : all the IP addresses and networks of Facebook will get blocked at the firewall level.
In my example above I had selected "No outbound" which means : nothing from 'LAN' can reach these networks and IPs anymore. -
Try this:
On the pfSense box
- Enable DNS resolver (I'm going to assume that all the default settings are in place
- Diagnostics menu -> Command line
dig facebook.com- the following from your client machine (windows)
nslookup facebook.com- then the following from your client machine (windows)
nslookup server (ip of your pfSense box) facebook.com- share all three results
pfBlockerNG (assuming 3.2.0_6)
- make sure it is enabled (Firewall -> pfBlockerNG ->General)
Edit - Sorry one of the images / steps didn't appear
this is under Firewall -> pfBlockerNG -> DNSBL
-
Firewall -> pfBlockerNG -> DNSBL -> DNSBL Groups
-
add a new group - call it Socials (or whatever)
Settings- Action Unbound
- just select Every 2 hours for now.
- Scroll to the bottom in the section DNSBL Custom_List
in the box enter facebook.com - Save DNSBL Settings (Button at bottom of screen)
-
at the top of screen, right next to DNSBL select the Update (tab/page)
- Select 'Force' option - click "reload"
- Select 'Reload' option - click "DNSBL"
- click the Run button (wait until is says "UPDATE PROCESS ENDED" in the view below the run button.)
-
repeat the three tests above (1 dig on the pfSense, 2 nslookup on the client)
post the results
-
@Gertjan said in Not able to block facebook website:
all the IP addresses and networks of Facebook will get blocked at the firewall level.
Not entirely true
All the IPs in their ASN will get blocked, however they also use (randomly) IP addresses that are not in their ASN (ie the leased space)
here are a few of them associated with fb
As I said previously neither method is 100% you have to use a combination to get closer to that level. so again it all comes down to the definition of "Block Facebook" and the requirements
facebook.com will block most of the "user browsing traffic" but not all the other "things they embed here there and everywhere"
for that you would also have to include this, and more (as the list doesn't include their content servers) (however, beware, you will notice that some of entries listed have nothing to do with facebook directly, that is because the IP's float within the AWS network and other leased space.
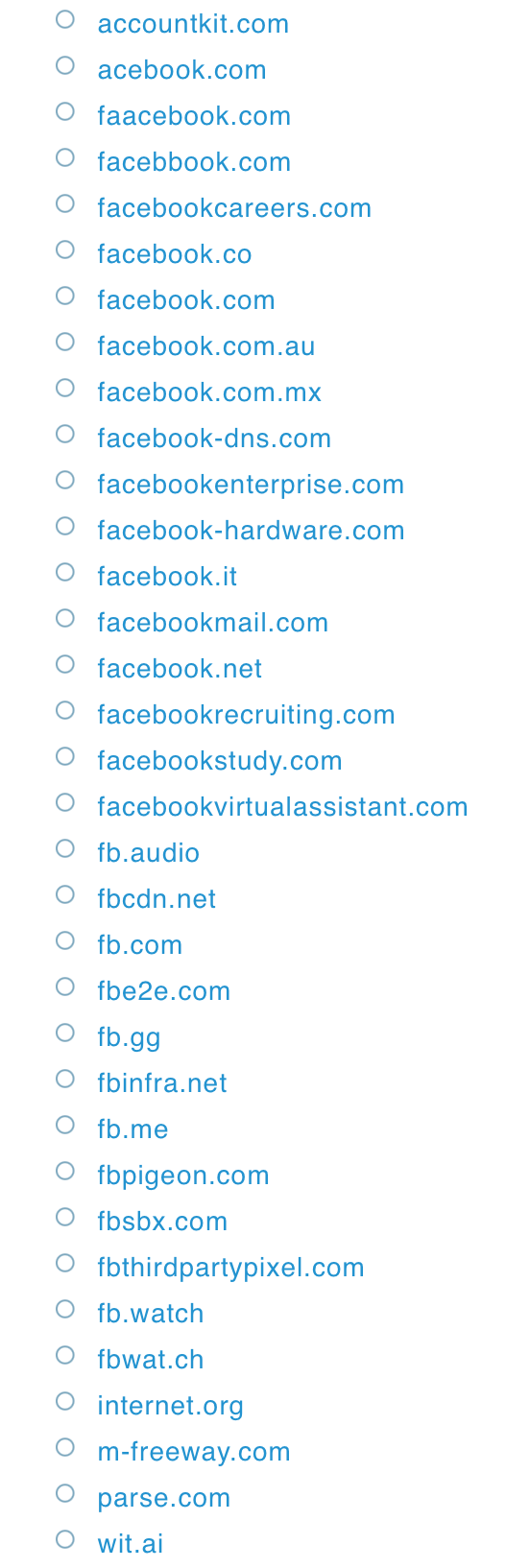
-
Just as a side note, we have to keep a couple of statements from the OP in mind when proposing solutions
stated:
Actually im new to PFSense so could you please help me to find how to check if my clients are using Netgate as DNS
has also said:
could you please help me to configure dnsbl to block websites.
and has also changed the requirements from "block facebook.com". I knew this would be happening based on the first statement about being new -- but as stated now the requirement is:
I want to block all social media websites, OTTS and torrents (A big list).
if you want to go ahead and start looking up the ASN for "all social media websites" go for it. It ultimately would add to a more robust blocking package.
OR we could answer the questions sort out the DNS, get DNSBL running properly and then finally throw a list of socials into the TLD block list and hit 95% of the requirement to "block all social media websites"
Does it block it "ALL social media" - not even close!facebook.com
tiktok.com
twitter.com
instagram.com
whatsapp.com
tumblr.com
wechat.com
weixin.qq.com
telegram.org
snapchat.com
douyin.com
quora.com
threads.net
tinder.com
discord.com
clubhouse.com
bereal.com -
-
@jrey said in Not able to block facebook website:
@Gertjan said in Not able to block facebook website:
all the IP addresses and networks of Facebook will get blocked at the firewall level.Not entirely true
All the IPs in their ASN will get blocked, however they also use (randomly) IP addresses that are not in their ASN (ie the leased space)
here are a few of them associated with fbCorrect. You're right.
I won't try not to be funny here, but the best way would be : contact each large social media and ask them for all the IPv4 (and IPv6) they use. Most will be 'in' their ASN they own. But they can use more then that. If I was working for them, I would do exactly that : using 'random' Iv4 addresses so my clients can use my social media at any time. No one would be able to block the access.That's why "I want to block the biog ones' isn't really an issue. As it can not be done for 100 %.
Blocking the big social networks can only happen if you have all ( ! ) the IPs they use. This list with Ips probably changes all the time.
And they will never give you this list.