Cant login on server: "Decoding PKCS12 failed. Probably wrong password or unsupported/legacy encryption"
-
Hello, friends. Im installing an OpenVPN connection client to site where the costumer starts the connection with its laptop to its server at his office but theres this error and I dont know how to get through. Just researched on google and cant figure out with a clear solution. Did I miss something with the client certificate or there is something wrong with the local server? S.O is a Win server 2016, installation provided by PfSense. I've changed the credentials password to 123 but theres no success. Here is the logs:
2023-11-27 11:56:20 OpenVPN 2.6.8 [git:v2.6.8/3b0d9489cc423da3] Windows [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] [DCO] built on Nov 17 2023
2023-11-27 11:56:20 Windows version 10.0 (Windows 10 or greater), amd64 executable
2023-11-27 11:56:20 library versions: OpenSSL 3.1.4 24 Oct 2023, LZO 2.10
2023-11-27 11:56:20 DCO version: N/A
2023-11-27 11:56:22 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2023-11-27 11:56:22 OpenSSL: error:0308010C:digital envelope routines::unsupported:Global default library context, Algorithm (RC2-40-CBC : 0), Properties ()
2023-11-27 11:56:22 OpenSSL: error:11800071:PKCS12 routines::mac verify failure:
2023-11-27 11:56:22 Decoding PKCS12 failed. Probably wrong password or unsupported/legacy encryption
2023-11-27 11:56:22 SIGUSR1[soft,private-key-password-failure] received, process restarting
2023-11-27 13:27:15 ERROR: could not read Auth username/password/ok/string from management interface
2023-11-27 13:27:15 Exiting due to fatal error -
@cezar_a said in Cant login on server: "Decoding PKCS12 failed. Probably wrong password or unsupported/legacy encryption":
2023-11-27 11:56:20 OpenVPN 2.6.8 [git:v2.6.8/3b0d9489cc423da3] Windows [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] [DCO] built on Nov 17 2023
2023-11-27 11:56:20 Windows version 10.0 (Windows 10 or greater), amd64 executable
2023-11-27 11:56:20 library versions: OpenSSL 3.1.4 24 Oct 2023, LZO 2.10Where do these logs come from ? Not pfSense .....
[23.09-RELEASE][root@pfSense.bhf.tld]/root: openssl version OpenSSL 3.0.12 24 Oct 2023 (Library: OpenSSL 3.0.12 24 Oct 2023) [23.09-RELEASE][root@pfSense.bhf.tld]/root: openvpn --version OpenVPN 2.6.7 amd64-portbld-freebsd14.0 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] [DCO] library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10 DCO version: FreeBSD 14.0-CURRENT amd64 1400094 #0 plus-RELENG_23_09-n256163-2763857e770: Wed Nov 1 21:18:24 UTC 2023 root@freebsd:/var/jenkins/workspace/pfSense-Plus-snapshots-23_09-main/obj/amd64/WrS3lKLo/var/jenkins/workspace/pfSense-Plus-snapshots-23_09-main/ Originally developed by James Yonan Copyright (C) 2002-2023 OpenVPN Inc <sales@openvpn.net> Compile time defines: enable_async_push=yes enable_comp_stub=no enable_crypto_ofb_cfb=yes enable_dco=yes enable_dco_arg=yes enable_debug=yes enable_dlopen=unknown enable_dlopen_self=unknown enable_dlopen_self_static=unknown enable_fast_install=needless enable_fragment=yes enable_iproute2=no enable_libtool_lock=yes enable_lz4=yes enable_lzo=yes enable_management=yes enable_pam_dlopen=no enable_pedantic=no enable_pkcs11=yes enable_plugin_auth_pam=yes enable_plugin_down_root=yes enable_plugins=yes enable_port_share=yes enable_selinux=no enable_shared=yes enable_shared_with_static_runtimes=no enable_silent_rules=no enable_small=no enable_static=yes enable_strict=yes enable_strict_options=no enable_systemd=no enable_unit_tests=no enable_werror=no enable_win32_dll=yes enable_wolfssl_options_h=yes enable_x509_alt_username=yes with_aix_soname=aix with_crypto_library=openssl with_gnu_ld=yes with_mem_check=no with_openssl_engine=auto with_sysroot=noI presume the logs shown are the output of a OpenVPN client ?
What I think ....
Your OpenVPN client (is it ?) is using the more modern OpenSSL 3.x
Same thing for the OpenVPN version, as 2.6.8 is more recent as the version that pfSense is using (2.6.7)Read this : Netgate Will Migrate to OpenSSL 3 in pfSense Plus Software Version 23.09 which invited you to ditch ancient (called legacy) stuff, as i think RC2-40-CBC is ancient (I've not checked)
You use a recent pfSense, like 2.7.1 or 2309, right ?
-
Thanks for the answer, @Gertjan and yes, its from a OpenVPN client. Sorry, im new into this. Not sure if the article you shared aims to my situation but heres the versions im using:
OpenVPN client is 2.6.8 version;
pfSense is 2.6.0 version. -
@Gertjan any hints? or does my certificate has been created under wrong conditions, actually?
-
We see the same issue and I found this commit:
https://github.com/pfsense/FreeBSD-ports/commit/f61ca6b81bab553e94046b1e6c5811a5f0e854e9Our client export was before this commit, so we can try to use the older OpenVPN 2.5.x version?
Edit:
Version 2.5.x works.
We try now a new export with the current 2.6.x version. -
@cezar_a said in Cant login on server: "Decoding PKCS12 failed. Probably wrong password or unsupported/legacy encryption":
OpenVPN client is 2.6.8 version;
pfSense is 2.6.0 version.That is a problematic combination - my very IMHO.
pfSense 2.6.0 is 'EOL', and uses a very 'EOL' OpenVPN version 2.5.x ( or even older ? ).
If you have to use pfSense 2.6.0 (for, dono : security reason ? ) and use the OpenVPN server of that pfSense version, then you should not update your OpenVPN client software neither. Or, at least, keep the two 'OpenVPN' versions on both sides as close as possible.
) and use the OpenVPN server of that pfSense version, then you should not update your OpenVPN client software neither. Or, at least, keep the two 'OpenVPN' versions on both sides as close as possible.I guess it is still possible to make the two work together, but then you need to sift out for yourself what is supported between the two, what is depreciated, etc etc. And that's often not worth the hassle.
Right now, my pfSense tells me I'm using a rather recent version of OpenVPN :
[23.09-RELEASE][root@pfSense.bhf.tld]/root: openvpn --version OpenVPN 2.6.8 amd64-portbld-freebsd14.0 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] [DCO] library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10 ......This also shows me (you) that the newer "OpenVPN 2.6.x" uses "OpenSSL 3", not not "OpenSSL 1", like in the good old days of "pfSense 2.6.0".
"OpenSSL 3" is now available, and for this reason alone its advised to upgrade pfSense.
I've you missed it : read this.Again : I'm pretty sure your OpenVPN client can 'talk' to your OpenVPN server. You probably will have to make some configuration changes on both sides.
-
in my eyes the problem is the PKCS#12 cert, openssl 3.x can not open this cert for some reasons.
OpenVPN clients with older and very old legacy clients still work fine with pfSense 2.7.1.
-
@slu said in Cant login on server: "Decoding PKCS12 failed. Probably wrong password or unsupported/legacy encryption":
some reasons.
Not 'some' any more. For the mentioned reason :
On the blog page :
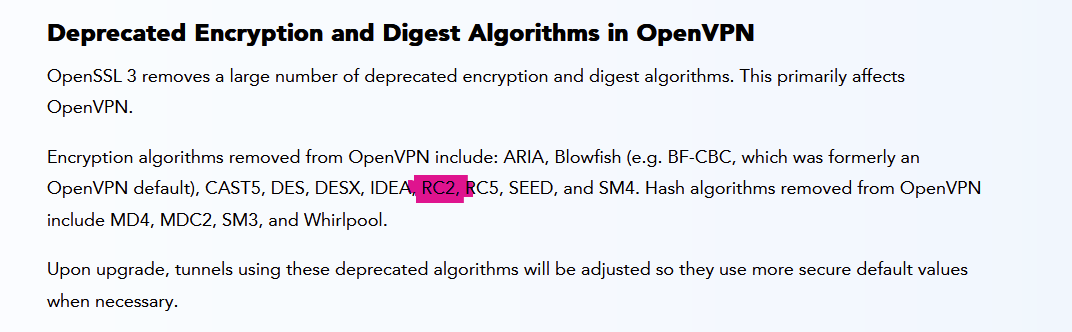
Compare with your error message :
OpenSSL: error:0308010C:digital envelope routines::unsupported:Global default library context, Algorithm (RC2-40-CBC : 0), Properties ()
The way I see it : "OpenSSL 3" support very well PKSC12 (see this as a file format), but not some stuff in your current PKSC12 cert file, like the "RC2" it found, which is a "algorithm".
On the pfSense OpenVPN server side : recreate the certs. Have the OpenVPN server use them. Send new client opvn files to the OpenVPN clients and you're good.
I'll keep my fingers crossed. -
that make sense!
My servers/clients certs are long time ago ecdsa-with-SHA512 but I see this drop down and it look like the default has changed.
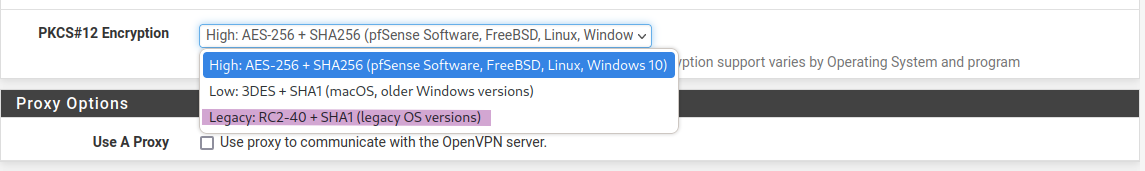
Maybe some of my VPN exports in 2022 was still in the old legacy version and thats the problem now.