RESTCONF & NACM, which modules are needed for RESTCONF access?
-
Tried to give netgate-acl access for a single user via NACM, RESTCONF login does not work. Which additional modules are needed to enable RESTCONF login but restrict the modules? I don't want to add the user to the admin group. I tried the "netgate-restconf-cli" too, but that does not work.
Here is an example that does not work:
nacm rule-list api-acl
group api-acl
rule netgate-acl
module netgate-acl
access-operations *
action permit
exit
rule netgate-restconf-cli
module netgate-restconf-cli
access-operations *
action permit
exit
exit -
What do you need to know that is not covered here:
https://docs.netgate.com/tnsr/en/latest/nacm/index.html
And here:
https://docs.netgate.com/tnsr/en/latest/restconf/index.html
??
-
@Derelict Ah just the simple “how can I create a NACM user that can login via RESTCONF but has only access to certain modules, and which modules are needed for the RESTCONF login to work”, because it seems to be able to login to RESTCONF the user needs to be an admin and needs access to all modules. That’s why I asked, which modules are needed for RESTCONF login to work? My above example shows exactly what I mean and what you configure in TNSR for that purpose, but, the user can’t login via RESTCONF, only if I add the user to the admin group it works. Because your documentation has no requirements for the modules for RESTCONF to work. Neither does it say anywhere that it’s even possible to have a restricted user login via RESTCONF.
or simply put: I have a user that has only access to the module "netgate-acl", how can this user still login via RESTCONF?
This does not work, use can't login via RESTCONF.
nacm rule-list api-acl group api-acl rule netgate-acl module netgate-acl access-operations * action permit exit rule netgate-restconf-cli module netgate-restconf-cli access-operations * action permit exit exit -
Where is the rest of the nacm configuration?
And the restconf configuration?
What, specifically, are you doing to access? Testing with curl? Something else? What exactly is happening?
-
Not that these lines would matter:
auth user api-acl password ************ exit nacm group api-acl member api-acl exitnor these:
restconf enable true server host *.*.*.* 443 true global authentication-type user global server-ca-cert-path restconf-CA global server-certificate restconf global server-key restconf exitand I wrote already that RESTCONF shows access denied. How much easier do I have to phrase my question? How hard is it to grasp the concept of a user that needs to login via restconf but has only access to the acl module? What more do you need? It's all default on a test instance, nothing is configured, and I wrote restconf access works when I grant access to all modules but that invalidates everything within nacm.
-
@Derelict So I guess not even netgate knows how to have a user login via RESTCONF but having only access to the acl module?
-
@meatprofit
global authentication-type user
Users can be authenticated against any source supported by PAM modules in the operating system.
Once authenticated, the username is processed through NACM to determine group access privileges for the RESTCONF API.
so if the answer is "access denied" when you try to login it's PAM that's rejecting it and not NACM? did you try global authentication-type client-certificate ? -
@kiokoman Thanks for you reply. Sadly no, I can login (SSH) with the api-acl user just fine, so PAM is not prohibiting the access. RESTCONF is. I’m still convinced that only users with all permissions can login via RESTCONF and a user that has limited privileges can’t, but @Derelict does neither confirm or deny this.
Here is an example output, as you can see I can login via SSH, but can't access the module I have all privileges for:
# login as restconf-test TNSR01 tnsr# conf TNSR01 tnsr(config)# show acl tnsr_cli_get: Failed to retrieve /ngacl:acl-state/ngacl:acl-table Dec 13 10:08:59: Query failure: application access-denied default deny TNSR01 tnsr(config)# show int tnsr_cli_get: Failed to retrieve /ngif:interfaces-state/ngif:interface Dec 13 10:09:00: Query failure: application access-denied default deny TNSR01 tnsr(config)# # show nacm as tnsr NACM ==== NACM Enable: true Default Read policy : deny Default Write policy: deny Default Exec policy : deny Group: admin -------------------- root tnsr Group: restconf-test -------------------- restconf-test Rule List: admin-rules -------------------------- Groups: admin Name Action Op Module Type --------------- ------ -- -------------------- ---- permit-all permit * * Rule List: restconf-test -------------------------- Groups: restconf-test Name Action Op Module Type --------------- ------ -- -------------------- ---- netgate-acl permit * netgate-acl netgate-restconf-cli permit * netgate-restconf-cliit seems you need exec permission on all modules to even be able to login via RESTCONF, this works, all other modules are not accessible.
nacm rule-list api-acl-rules group api-acl rule exec module * access-operations exec action permit exit rule netgate-acl module netgate-acl access-operations * action permit exit exit -
full solution for anyone else:
pki generate-restconf-certs restconf enable true server host *.*.*.* 443 true global authentication-type user global server-ca-cert-path restconf-CA global server-certificate restconf global server-key restconf exit auth user api-acl password ************* exit nacm group api-acl member api-acl exit nacm rule-list api-acl-rules group api-acl rule exec module * access-operations exec action permit exit rule netgate-acl module netgate-acl access-operations * action permit exit exit -
@meatprofit
there is an interesting section starting from here explaining ACLhttps://datatracker.ietf.org/doc/html/rfc8341#section-3
As an example, if an action is defined as
/interfaces/interface/reset-interface, the group must be authorized
to (1) read /interfaces and /interfaces/interface and (2) execute on
/interfaces/interface/reset-interface.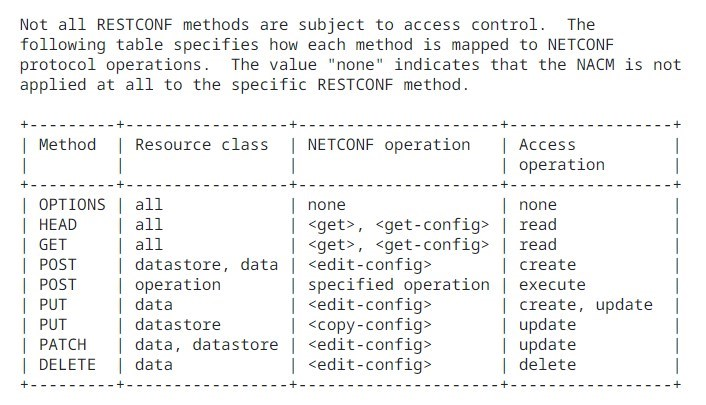
glad you have solved anyway