Question regarding Acme and DDNS
-
@gregeeh if you have any questions just ask been doing it for years.. My gui cert is still good til 27, I have created it 2017.. This was before the browsers started complaining about long life certs..
I do need to get around to changing it, as want to completely move away from the local.lan domain have been using and use home.arpa - I have moved over some of my certs. But just haven't pulled the trigger on the webgui as of yet. Its working - not a lot of hurry to change it ;)
I have changed it on my unifi and nas because those certs were expiring..

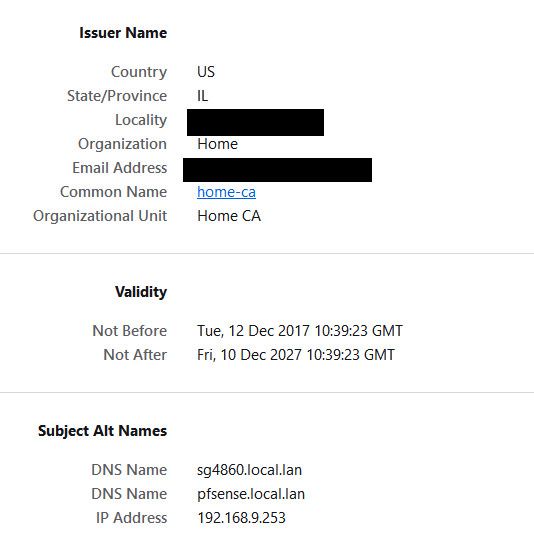
Here is the cert on the webgui of pfsense, you can see it has multiple names I can use and also the IP, so even when accessed via IP, say my local dns was down.. Cert is still trusted.
-
@johnpoz - Followed all your steps. Imported into Firefox and all good :)
As for Chrome, imported into Trusted Root Certification Authorities as Personal did not work. Hope this was correct?
So, to create certificates for say my NAS and Unifi Controller, I would just repeat those steps making a CA and CERT for each. Correct?
Thanks again, for all your help. Much easier then using Acme Certificates.
Greg
-
@johnpoz said in Question regarding Acme and DDNS:
I do need to get around to changing it, as want to completely move away from the local.lan domain have been using and use home.arpa - I have moved over some of my certs. But just haven't pulled the trigger on the webgui as of yet. Its working - not a lot of hurry to change it ;)
Hello johnpoz
I have a question following your sentence. Why do you want to change this?
I copied your explanations (old but still valid) where you had used "local.lan" ... and now I see your message and I would very much like to understand the meaning of your remark.
I'm learning a lot here, THANK YOU!!!

-
@gregeeh said in Question regarding Acme and DDNS:
@johnpoz - Followed all your steps. Imported into Firefox and all good :)
As for Chrome, imported into Trusted Root Certification Authorities as Personal did not work. Hope this was correct?
So, to create certificates for say my NAS and Unifi Controller, I would just repeat those steps making a CA and CERT for each. Correct?
Thanks again, for all your help. Much easier then using Acme Certificates.
Greg
I have the same question because I just can't get it. For access to my Pfsense it's all OK, but not for my "UCK_Gen2-Plus"!? Does it take time for the certificate to propagate?
-
@gregeeh said in Question regarding Acme and DDNS:
making a CA and CERT for each. Correct?
No you only need the 1 CA, you can now create certs with that ca for any of your devices. And your browser will use them because it trusts the CA.
-
@SwissSteph said in Question regarding Acme and DDNS:
understand the meaning of your remark
Oh I don't actually "need" too - but home.arpa is the new recommended domain to use locally..
https://datatracker.ietf.org/doc/html/rfc8375.html
Special-Use Domain 'home.arpa.'I do believe pfsense now defaults to that.. There is no "need" to move away from my local.lan domain I could continue to use it - but there is no reason I shouldn't use the home.arpa so at some point I will make sure everything locally is using it..
-
@SwissSteph said in Question regarding Acme and DDNS:
but not for my "UCK_Gen2-Plus"
The controller is a pita to get to use new certs.. I have no idea why they don't make it simple to change out via the gui, like my nas was, or even my printer. There are instructions out there to do it..
Here are my notes for changing it on the unifi controller.
From the CA, have these files available:ca.cert.pem (CA cert)server.domain.net.cert.pem (server cert)server.domain.net.key.pem (server key) copy them to the unifi controller. delete the old keystore and restart unifi to create an empty keystore:sudo rm /var/lib/unifi/keystore sudo service unifi restart Create a central file to upload to the keystore:openssl pkcs12 -export -in server.domain.net.cert.pem -inkey server.domain.net.key.pem -certfile ca.cert.pem -out unifi.p12 -name unifi -password pass:aircontrolenterprise This gives you the file unifi.p12. Now import this into the unifi keystore:keytool -importkeystore -srckeystore unifi.p12 -srcstoretype PKCS12 -srcstorepass aircontrolenterprise -destkeystore /usr/lib/unifi/data/keystore -storepass aircontrolenterprise Restart unifi sudo service unifi restart And we're good to go. more info keytool -list -keystore data/keystore -v keytool error: java.io.IOException: keystore password was incorrect when using Openssl to export, add -legacy so openssl v3 will revert back to legacy mode, and then keytool was able to import. openssl pkcs12 -export -legacy -
@johnpoz said in Question regarding Acme and DDNS:
@SwissSteph said in Question regarding Acme and DDNS:
understand the meaning of your remark
Oh I don't actually "need" too - but home.arpa is the new recommended domain to use locally..
https://datatracker.ietf.org/doc/html/rfc8375.html
Special-Use Domain 'home.arpa.'I do believe pfsense now defaults to that.. There is no "need" to move away from my local.lan domain I could continue to use it - but there is no reason I shouldn't use the home.arpa so at some point I will make sure everything locally is using it..
Thank you for your reply with the link


-
@johnpoz said in Question regarding Acme and DDNS:
@SwissSteph said in Question regarding Acme and DDNS:
but not for my "UCK_Gen2-Plus"
The controller is a pita to get to use new certs.. I have no idea why they don't make it simple to change out via the gui, like my nas was, or even my printer. There are instructions out there to do it..
Here are my notes for changing it on the unifi controller.
From the CA, have these files available:ca.cert.pem (CA cert)server.domain.net.cert.pem (server cert)server.domain.net.key.pem (server key) copy them to the unifi controller. delete the old keystore and restart unifi to create an empty keystore:sudo rm /var/lib/unifi/keystore sudo service unifi restart Create a central file to upload to the keystore:openssl pkcs12 -export -in server.domain.net.cert.pem -inkey server.domain.net.key.pem -certfile ca.cert.pem -out unifi.p12 -name unifi -password pass:aircontrolenterprise This gives you the file unifi.p12. Now import this into the unifi keystore:keytool -importkeystore -srckeystore unifi.p12 -srcstoretype PKCS12 -srcstorepass aircontrolenterprise -destkeystore /usr/lib/unifi/data/keystore -storepass aircontrolenterprise Restart unifi sudo service unifi restart And we're good to go. more info keytool -list -keystore data/keystore -v keytool error: java.io.IOException: keystore password was incorrect when using Openssl to export, add -legacy so openssl v3 will revert back to legacy mode, and then keytool was able to import. openssl pkcs12 -export -legacyThanks for your explanation, it's going to go beyond my skills and I don't want to break anything on this unify controller ... it's complicated enough (for me) with Unify when there's a new camera, for example, and it's not seen ....
-
@gregeeh said in Question regarding Acme and DDNS:
Hope this was correct?
Sure as long as your browser trusts the CA is all that matters.