OpenVPN: how to iptable NAT postrouting with masquerade
-
This post is deleted! -
@john-h said in OpenVPN: how to iptable NAT postrouting with masquerade:
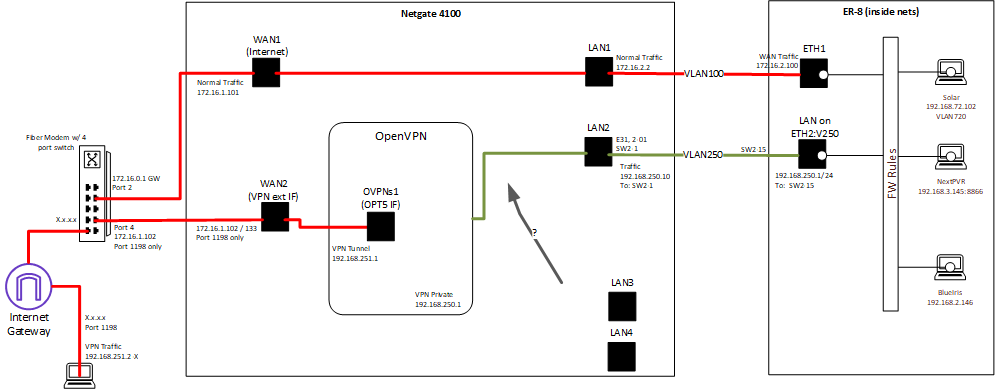
My intent is to have ALL VPN connections from the internet go via the Netgate 4100 WAN2 on port 1198 into OpenVPN and then get passed thru to the internal network (LAN) side of a downstream router (as local traffic).
The intenet here is to isolate the VPN traffice post modem from all other traffic.I cannot think of any benefit of this construct. OpenVPN creates a separated interface inside pfSense anyway, where the clients enter you LAN and what they are allowed to do, can be controlled on pfSense directly.
Anyway if you want to do this, masquerading is done with outbound NAT rules on pfSense.
Switch the outbound NAT into the hybrid mode if it's still in automatic and add a rule like this:
interface: LAN2
source: <OpenVPN tunnel network>
destination: any
translation: interface addressalso the OpenVPN client would access the internet via the 4100/WAN1 as if it was a normal client on the LAN side.
pfSense will not route out this upstream traffic on LAN2, hence the outbound NAT will not be applied to this.
If you want to restrict the traffic you have to do this on the OpenVPN interface. -
Thanks this did nudge me in the right direction.
I ended up creating vlan interfaces and made outbound nat rules. Since the pfsense LAN interfaces were already able to get to the internal VLANs it was simpler approach.