Issue with pfsense firewall rule
-
Hi,
I'm having some problems with a rule.
Here there are my two interfaces ruleset.
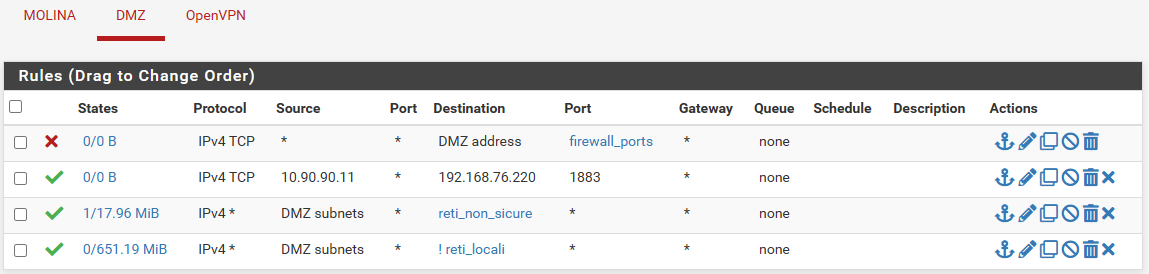
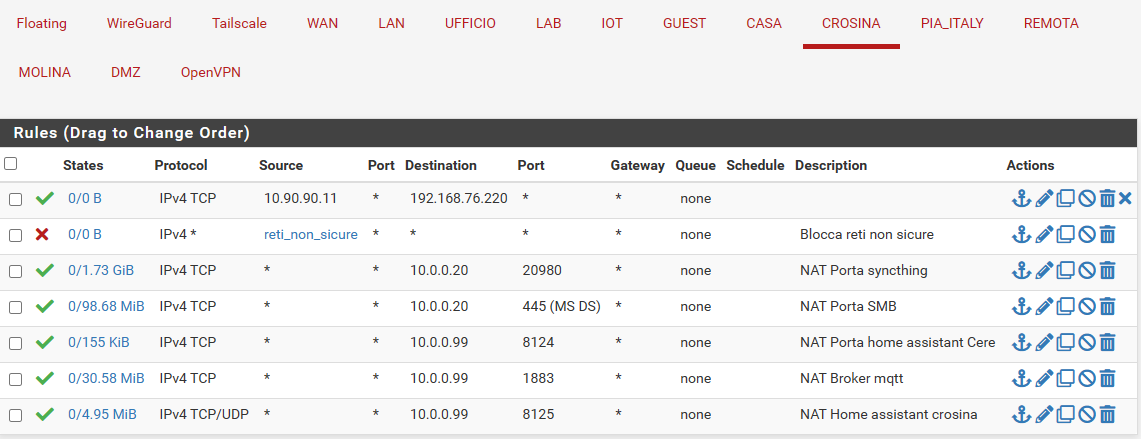
But when I try to connect to 192.168.76.220 from 10.90.90.11 on port 1883 the firewall blocks the packets

I can't figure out where the problem is. I've also tryed with the easypass rule automatically gernerated but I doesn't work either.
Thank in advance for the help
Best regards -
@nicber
if 10.90.90.11 is the DMZ network it can't be the source for CROSINA's network
so the first rule of CROSINA is wrong
reti_non_sicure can't be the source of CROSINA, this is wrong too
is 10.90.90.0/24 the network of DMZ ?
what network do you have on CROSINA? 192.168.76.0/24 ?
did you post all the rules of DMZ and CROSINA? -
Thank for the fast reply.
Yess, these are all the rules on the two interfaces.As I understand from your reply rules only matter for outgoing packets, right?
So, the two top rules in CROSINA are not needed.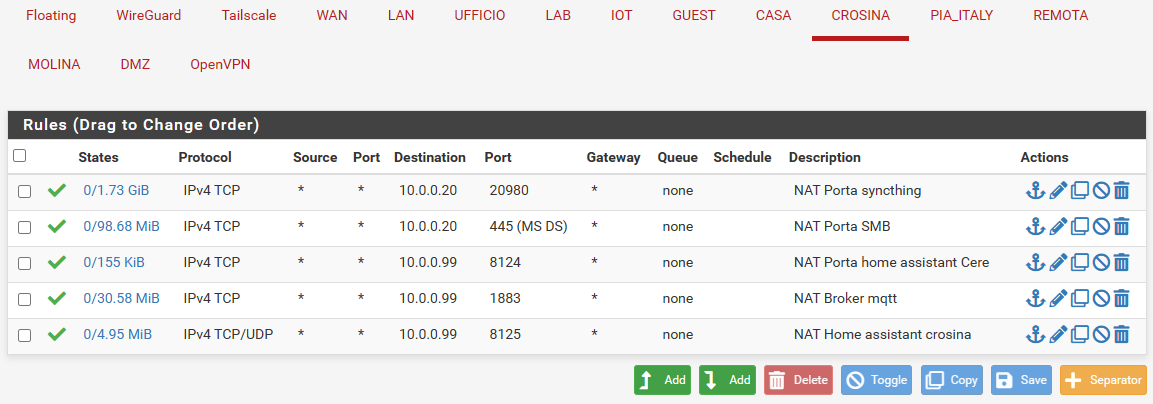
The two networks are DMZ 10.90.90.0/24 CROSINA 192.168.76.0/24.
Thanks
-
@nicber
yes, indeed, rules only matter for outgoing packets.
now i'm trying to understand why traffic does not match with your second rule on DMZ ... -
If it could help this is how the two interfaces are configured. DMZ is a normal VLAN while CRSOINA is a separatd physical network with is own gateway.
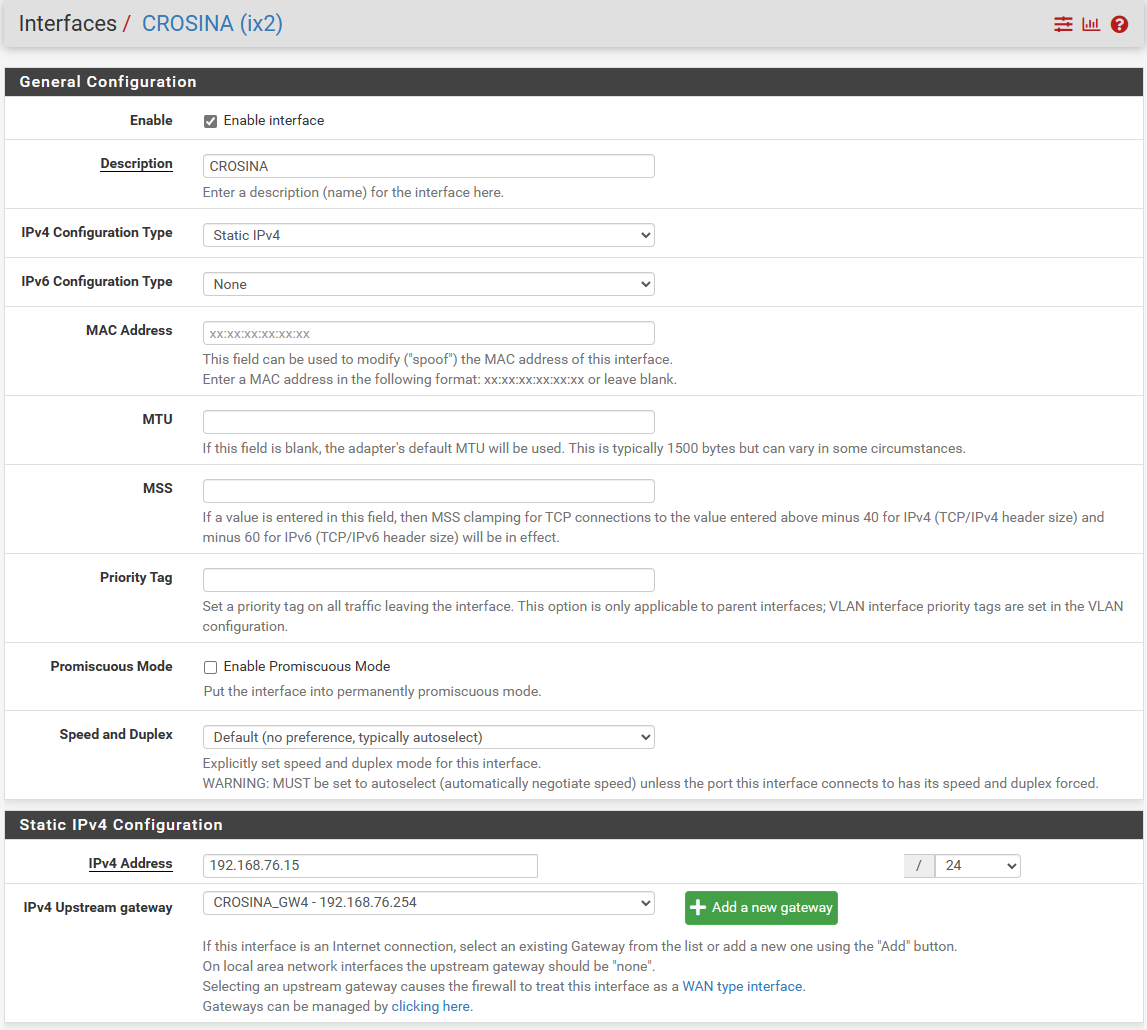
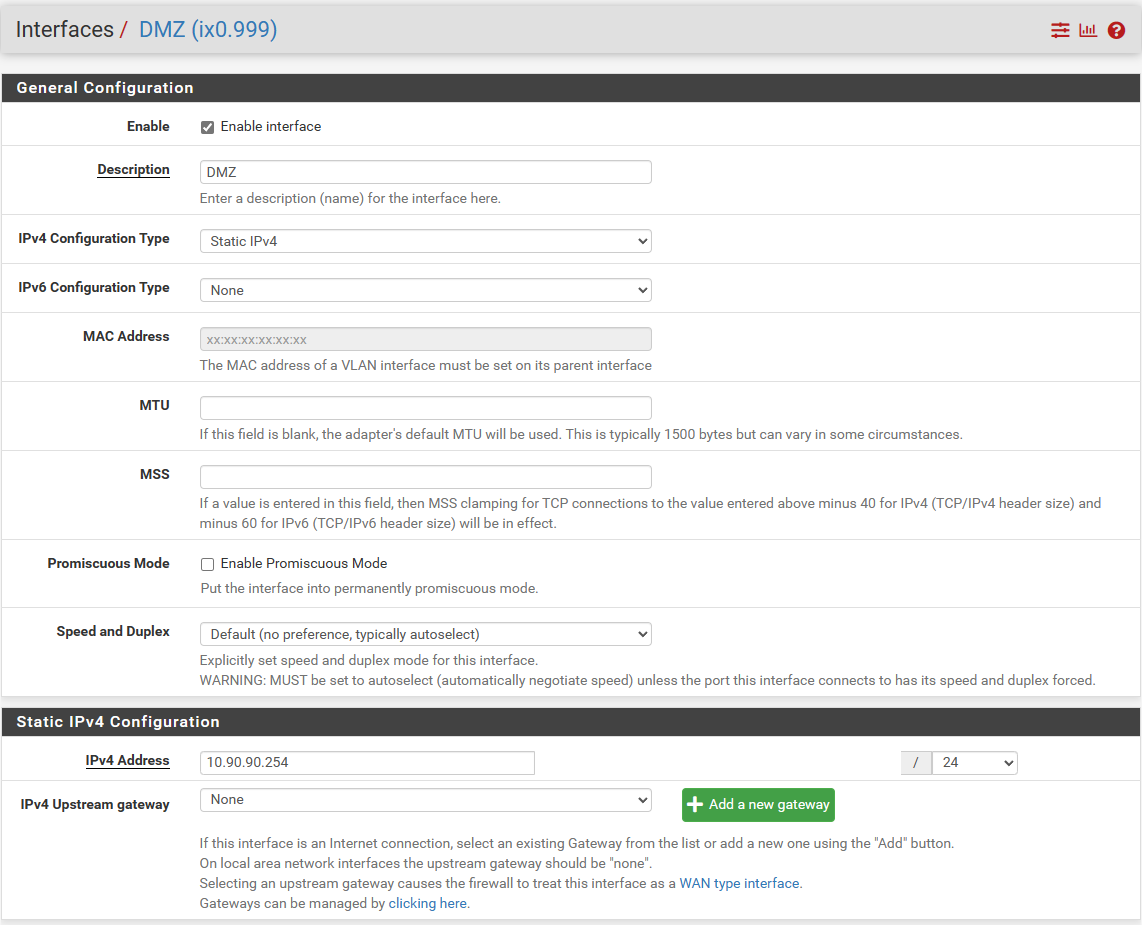
-
@nicber said in Issue with pfsense firewall rule:
CRSOINA is a separatd physical network with is own gateway.
So a wan connection then?
-
Yess, exactly.
-
@nicber
default deny rule IPv4 ... could it be Block private networks and loopback addresses or Block bogon networks ? -
@nicber well device on your wan to get to stuff behind that network would have to hit the pfsense IP and be forwarded. And would assume other devices on this "wan" of pfsense are not using pfsense as its gateway.. So if you tried to do routing on this networks gateway you run into asymmetrical traffic flow..