openvpn ssh via iPhone connect to pfSense fails
-
@JonH said in openvpn ssh via iPhone connect to pfSense fails:
with the cmdline utility I am running on the iPhone.
Something isn't right here. You've root shelled an iPhone, and can't set up SSH ?
I'm using the WebSS iphone app myself.
This is - I have a PC - what I did :
On the, install the "must have" apps "Putty".With puttygen.exe, generate an an SHA256 2048 bits key.
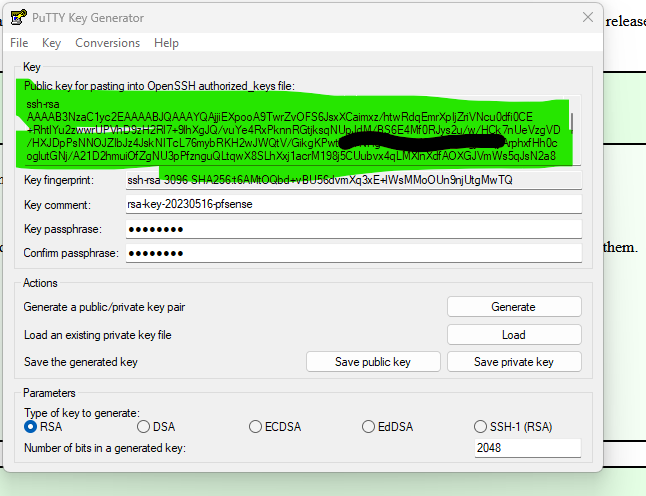
Add a passphrase (twice).
Copy paste the entire green section into here (the admin user) :
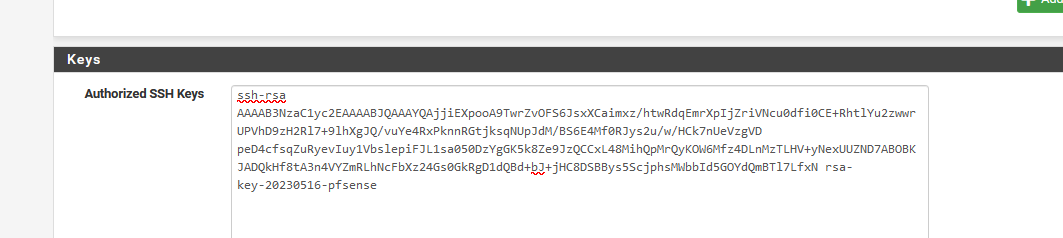
Use the "Save private key" button to generate a 'ppk' file.
In the iPhone WebSSH app, import this 'ppk' file (go the easy way : mail/Wap/whatever the file - a text fie - to yoruself, and open it up in the iPhone.
Send also the generated public key (the one you pasted into the admin user) to your phone.Create a SSH key in the app :
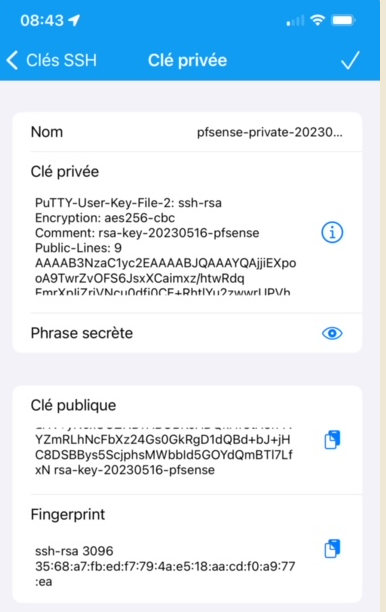
The ppk file goes into the first section - don't forget to also enter the passphrase.
The second section is the public key - the one you entered also in pfSense.The finger print : I'm not sure about that one. It will get auto generated ?
Save.
Now, create a connection :
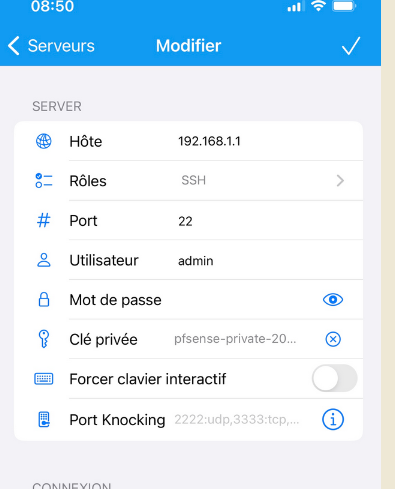
and select the SSH key you've created above.
You should be good.
You can try it when connected to the pfSEnse LAN, when connected locally with your phone.
And, when not at home, activate the VPN first, and then WebSSH will connect you also to SSH.Btw : I never managed to make this one working the first time.
I always, as I recreate new keys kets every 2 years or so, had to make several effort to make it work. -
@Gertjan said in openvpn ssh via iPhone connect to pfSense fails:
Something isn't right here. You've root shelled an iPhone, and can't set up SSH ?
No, I have not rooted my iPhone.
I'm trying to use a cmdline app on the iPhone to 'ssh admin@x.x.x.x'
Thanks for the info on putty. Maybe I can translate that info for an apple app.
I need to reread your reply more carefully but wanted to mention it is not a jailbroken phone.Adding: I forgot to mention I am using libterm, a cmdline interface for iPhone.
-
@JonH ok I tried that libterm - I don't think its updated I was getting an error with just exchanging keys with doesn't have anything to do with public key auth, etc. just don't think they could agree on what to use to communicate..
But I fired up the webssh that @Gertjan mentioned and was connected to pfsense in like 10 seconds. Just generated the key right in the app, using ED25519. Copied the pub key to pfsense for my test user and pasted it in..
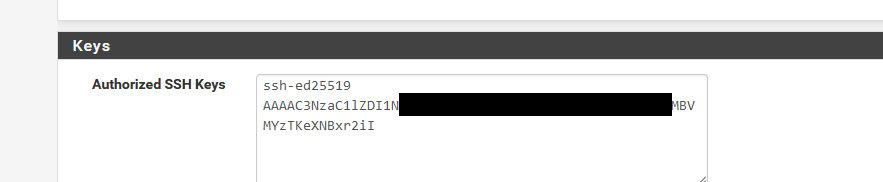
and bam I was connected using the private key for that pub on the webssh app..
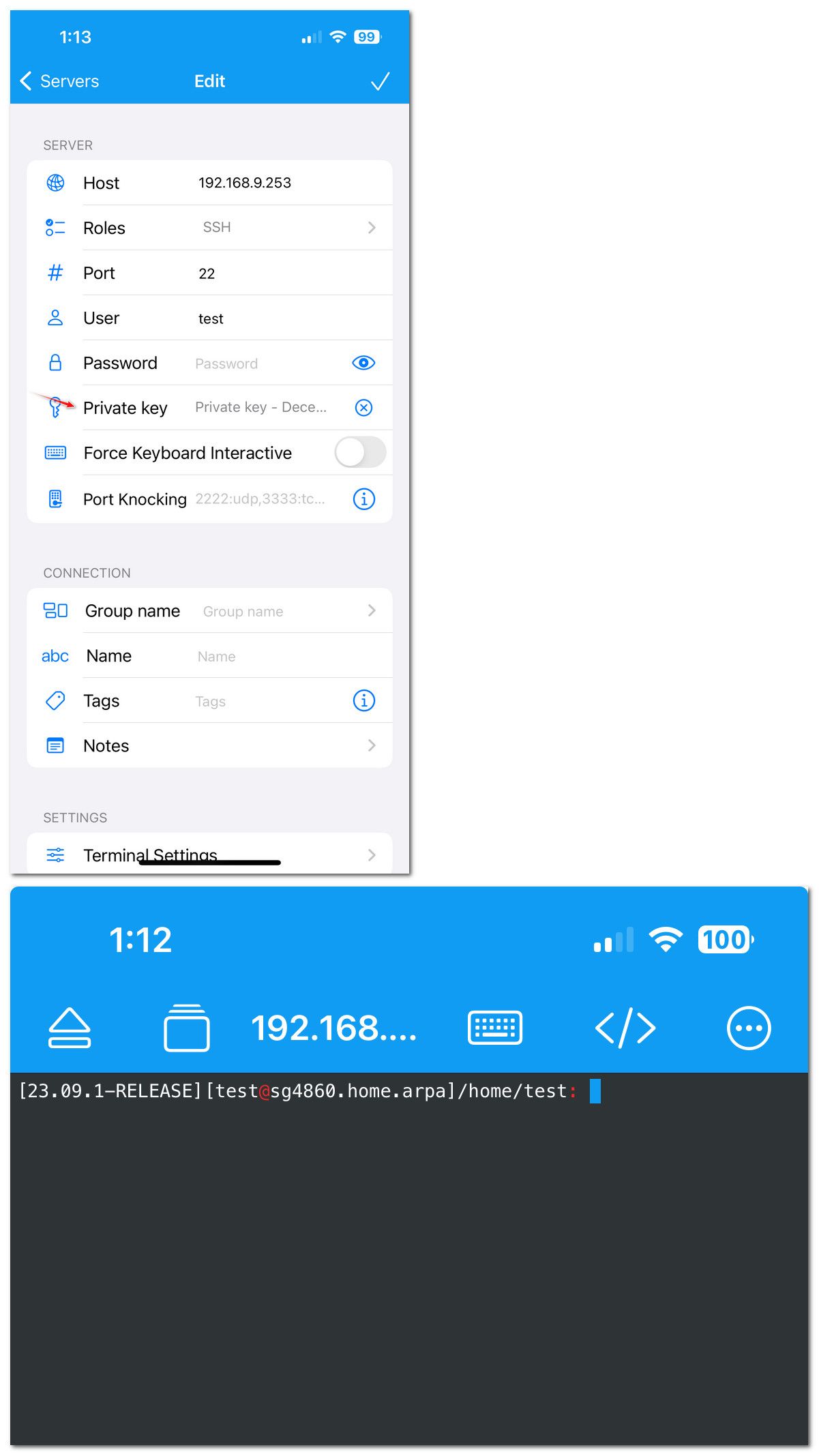
-
@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
ok I tried that libterm - I don't think its updated I was getting an error with just exchanging keys
The key exchange is the problem I was having.
Thanks for confirming the app I am using is inadequate for the intended purpose.
I did check the app store and found the app @Gertjan mentioned.Thanks for trying both apps and verifying that the app I am using is not sufficient, I was concerned that maybe I just wasn't doing something correctly.
I will give @Gertjan suggestion a try.Appreciate the great help here.
Thanks -
@JonH I might play with it a bit more to one of my other servers where its easier to adjust the config than pfsense
But I looked in the pfsense log and saw this
Dec 26 13:00:56 sshd 46903 Unable to negotiate with 192.168.2.198 port 50051: no matching host key type found. Their offer: ssh-rsa,ssh-dss [preauth]I thought pfsense did have a rsh host key
[23.09.1-RELEASE][admin@sg4860.home.arpa]/etc/ssh: cat sshd_config # This file is automatically generated at startup KexAlgorithms curve25519-sha256@libssh.org,diffie-hellman-group-exchange-sha256 Port 22 Protocol 2 HostKey /etc/ssh/ssh_host_rsa_key HostKey /etc/ssh/ssh_host_ed25519_key Compression delayed ClientAliveInterval 30 PermitRootLogin yes # Login via Key or Password ChallengeResponseAuthentication yes PasswordAuthentication yes PubkeyAuthentication yes UseDNS no LoginGraceTime 30s VersionAddendum none AllowAgentForwarding no X11Forwarding no Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr MACs hmac-sha2-512,hmac-sha2-256,umac-128@openssh.com # override default of no subsystems Subsystem sftp /usr/libexec/sftp-server [23.09.1-RELEASE][admin@sg4860.home.arpa]/etc/ssh:But maybe its a old rsa? that the client will only accept? I setup my current ssh client on my pc to only use what that client said it could do ssh-rsa and ssh-dss and got this in my debug on the client
debug1: kex: host key algorithm: (no match) Unable to negotiate with 192.168.9.253 port 22: no matching host key type found. Their offer: rsa-sha2-512,rsa-sha2-256,ssh-ed25519So I take it this old client doesn't like the current stuff.. Get the same warning in pfsense auth log
Dec 26 14:53:32 sshd 33329 Unable to negotiate with 192.168.9.100 port 30696: no matching host key type found. Their offer: ssh-rsa,ssh-dss [preauth]If I change my client to allow for rsa-sha2-256 then it works
ssh -vvv -o HostKeyAlgorithms=rsa-sha2-256 root@192.168.9.253Not sure when that lib thing was last updated, but prob not going to work with any modern ssh server that has kept up with current settings.. Pretty sure that old rsa stuff was deprecated many moons ago.
-
@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
Not sure when that lib thing was last updated, but prob not going to work with any modern ssh server that has kept up with current settings.. Pretty sure that old rsa stuff was deprecated many moons ago.
My error in pfSense system log was slightly different: " no matching host key type found. Their offer: ssh-rsa,ssh-dss [preauth]". The app was last updated 3 yrs ago so it's reasonable to assume this is my problem, like you said, the old rsa was deprecated long ago.
Also, I had already done the ssh patch that was released last week. I don't think this has anything to do with my original post but figured I should mention it.
I have forgotten the exact cmdline I used to create the new key, not sure if I specified sha2 or not but I did specified 256. The iPhone put the key in an unusual location and it didn't have the conventional name rsa_id. When I got nowhere with that I created a ~/.ssh directory on my iPhone and renamed the files to match the normal naming convention. None of that stuff worked. I was thinking it was because the keys are still in an unconventional location.
When I get some time I'll check out that the webSSH app. I've already wasted too much time on libterm.
-
@JonH doesn't matter what keypair you created - that error is the host key your client is willing to accept.. And what the host key actually is, etc.
This is what the host generated.. See the above sshd conf I posted, that is the too different host keys that pfsense has.. Neither of them are ssh-rsa, or ssh-dss.. So that is what the problem is.
Use the webssh thing that was mentioned, took me like 30 seconds to get in with public key auth to pfsense. Just generate the key pair on the app, and copy the pub key to your pfsense user you want to log in with via the user manager gui in pfsense,.
-
@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
different host keys that pfsense has.. Neither of them are ssh-rsa, or ssh-dss.. So that is what the problem is.
There is no question that I need to change client apps, I will do that.
I want to better understand what you wrote.@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
different host keys that pfsense has.. Neither of them are ssh-rsa, or ssh-dss.. So that is what the problem is.
From sshd.conf:
HostKey /etc/ssh/ssh_host_rsa_keySo ssh_host_rsa_key is not ssh-rsa even tho the matching pub key starts w/ the characters "rsa-key"?
Anyway, you have shown me what I need to do to fix it so I'll do that.
-
@JonH said in openvpn ssh via iPhone connect to pfSense fails:
HostKey /etc/ssh/ssh_host_rsa_key
Your client is looking for OLD school rsa key, not the new versions with sha2..
So if you check your key on pfsense..
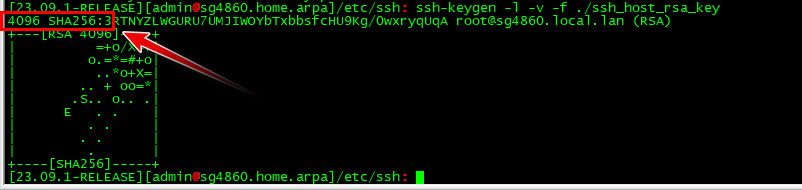
Your client is only accepting really old school ones..
See where client said only ssh-rsa, and ssh-dss.. Where when I looked at what pfsense was offering it was
Their offer: rsa-sha2-512,rsa-sha2-256,ssh-ed25519
-
@johnpoz OK, very good. My pfSense host key starts w/ 4096 SHA256:
BTW, the ed25519 host key is 256 SHA256
The libterm host key starts w/ 2048 SHA256:And I guess for security reasons there is no backward compatibility.
Guess I better fire up my linux laptop and check it's keys.
Thanks for spending your time to educate me. And thanks to @Gertjan too.
-
@JonH yeah when it comes time to depreciate some old encryption, its time to stop using it everywhere.
So they announced that was going away back in 8.2
https://www.openssh.com/txt/release-8.2
It is now possible[1] to perform chosen-prefix attacks against the
SHA-1 hash algorithm for less than USD$50K. For this reason, we will
be disabling the "ssh-rsa" public key signature algorithm that depends
on SHA-1 by default in a near-future release.And believe it was actually removed in 8.8
https://www.openssh.com/txt/release-8.8
This release disables RSA signatures using the SHA-1 hash algorithm
by default. This change has been made as the SHA-1 hash algorithm is
cryptographically broken, and it is possible to create chosen-prefix
hash collisions for <USD$50K [1]For most users, this change should be invisible and there is
no need to replace ssh-rsa keys. OpenSSH has supported RFC8332
RSA/SHA-256/512 signatures since release 7.2 and existing ssh-rsa keys
will automatically use the stronger algorithm where possible.Your host key itself is prob fine, but the exchange algo is gone, etc. You could enable it, but with pfsense that is a bit difficult since its more than just adjusting the sshd conf file, if you did that it would just get rewritten etc..
You prob want to read over the old release notes for info on migration away from that algo.. Keeping in mind the current version of ssh in pfsense is 9.4, with the current version being 9.6.. ssh has gotten some more attention as of late with the whole https://terrapin-attack.com/
There was a thread about it that jimp did, and there is a current patch you can apply, etc..
https://forum.netgate.com/topic/184941/terrapin-ssh-attack?_=1703677008519
It prob wouldn't be a bad idea to go over all of your hosts running ssh, and making sure your clients being used are current, etc
I have some stuff that ticks me off because its out of date and no way to update, etc.. My unifi APs for example - they are running ssh via dropbear that is many versions behind..
Hallway-BZ.6.6.56# dropbear -V Dropbear v2020.81 Hallway-BZ.6.6.56#And my cisco switch is pretty freaking dated as well.. That being said, if its just local network access its prob not the end of the world, etc. But it does behoove you to stay current with best practices, current ciphers and algos, etc.
Maybe take the opportunity make sure your all updated with client/server etc. and using best practices..
Maybe take a look at this tool.. https://github.com/jtesta/ssh-audit
Here is a sample ran against my AP for example.. Which ticks me off because there is no way to update it, need unifi to update and have been asking about them doing that for years, and just get back crickets..
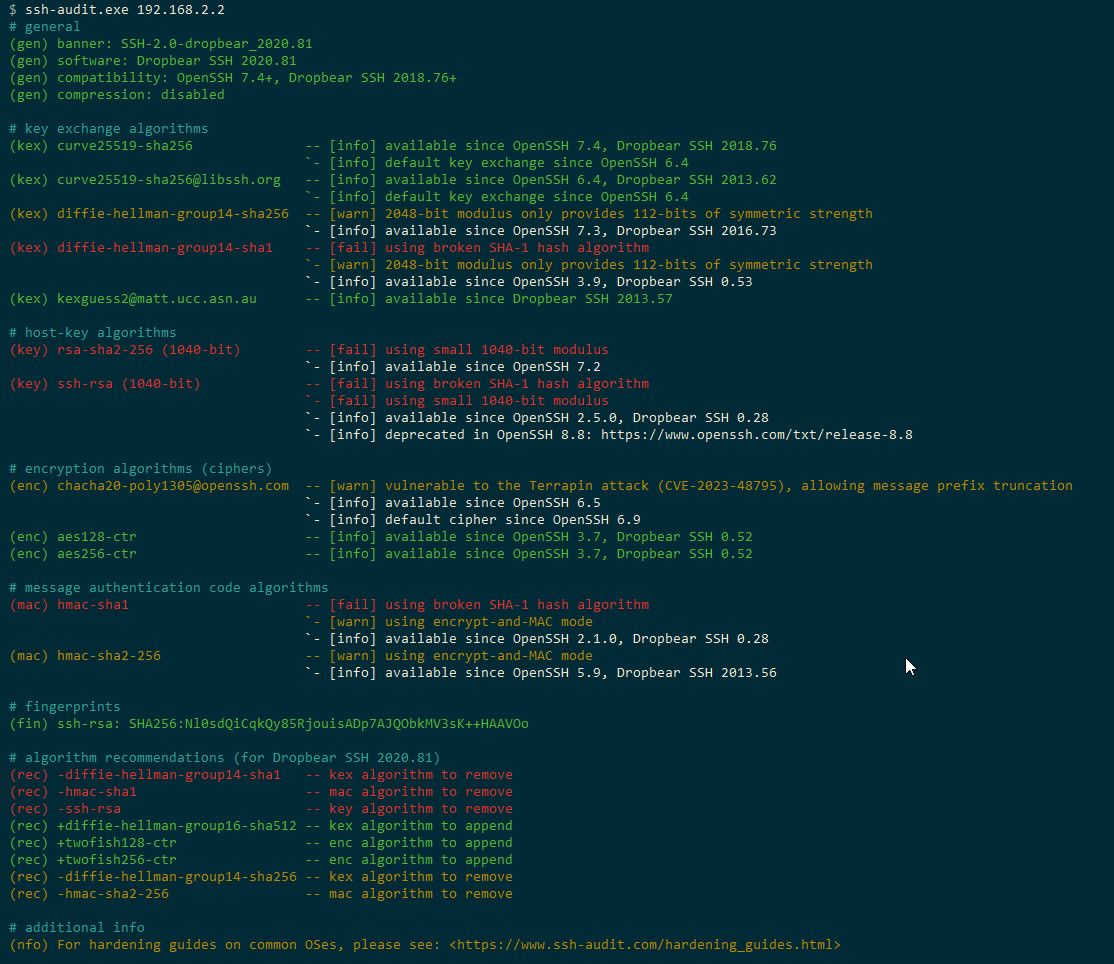
-
@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
I fired up the webssh that @Gertjan mentioned and was connected to pfsense in like 10 seconds. Just generated the key right in the app, using ED25519. Copied the pub key to pfsense for my test user and pasted it in..
@johnpoz i want to thank you so much for spending time explaining things to me. In spite of all that I still spent the better part of a week banging my head on the desk, keyboard, and anything else nearby in the hope of knocking some sense into myself.
My problem was the app, webssh. Ultimately I think the original install must have gone bad because I never could replicate the screenshots in the post I am replying to. After deleting webssl in frustration and reinstalling it I got the bingo! moment and it all fell into place. Testing w/ openvpn and my iPhone over a cell connection w/ openvpn on my wifi only iPad got me right into the console shell even tho it was a low data connection.
Thanks again and Happy New Year.
-
@JonH said in openvpn ssh via iPhone connect to pfSense fails:
because I never could replicate the screenshots in the post I am replying to
The ssh-audit screen, did you run ssh-audit?
-
@johnpoz said in openvpn ssh via iPhone connect to pfSense fails:
did you run ssh-audit?
I did not. I am embarrassedly deficit in my knowledge of github and there were no pre-built package for the Apple's iOS/iPados. The screenshots posted by @Gertjan and yourself were in posts mentioning the iOS all WebSSH and I failed to understand a later post about ssh-audit was the source of those particular screenshots.
No matter, WebSSH is working well for me now and I have learned a great deal more than I knew before.
I thank you and @Gertjan for the information that was posted.
-
@JonH I didn't run that off my phone, ran it off my pc to show what ciphers and algos and kex etc.. where being offered is all..
Glad you got it sorted.. Happy sshing ;)
-
@JonH said in openvpn ssh via iPhone connect to pfSense fails:
were no pre-built package for the Apple's iOS/iPados
Packages ?
There are only "apps" that you can install using the "App Store" app, like this one : WebSSH.I think he was talking about the ssh-audit not the ssh app for the phone.
-
@Gertjan said in openvpn ssh via iPhone connect to pfSense fails:
@JonH said in openvpn ssh via iPhone connect to pfSense fails:
were no pre-built package for the Apple's iOS/iPados
Packages ?
There are only "apps" that you can install using the "App Store" app, like this one : WebSSH.I think he was talking about the ssh-audit not the ssh app for the phone.
Yes, that is correct and my post was referring to my misunderstanding.
As for my poor choice of the word ‘package’, I was referring to pre-builts at GitHub.All that said, I have WebSSH finally set up and working on my iPad. And now that I better understand what ssh-audit is all about I will fire up a Linux box and try the pre-built .py
-
@JonH they also have a windows release, just a exe you can run.. Thats what I used in my screenshot