[SOLVED] Do not log TCP packets with flags TCP:RA / TCP:PA etc.
-
Same here, I have default deny logging off, and only log syn that hits my wan.. And then have another log rule for udp on ports that might be of interest..
The net is pretty noisy place - trimming down the log to only interesting info keeps it a bit less noisy.
-
@johnpoz said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
Same here, I have default deny logging off, and only log syn that hits my wan.. And then have another log rule for udp on ports that might be of interest..
The net is pretty noisy place - trimming down the log to only interesting info keeps it a bit less noisy.
hmmm, interesting.. How I didn't think about this before ??!
Edit:
In my case, for both WANs, last 5 days, very little noise:NOT pf_tcp_flags:S AND source:filterlog[*]: AND (pf_interface:ix2 OR pf_interface:ix3) AND pf_ipv4_protocol:tcp
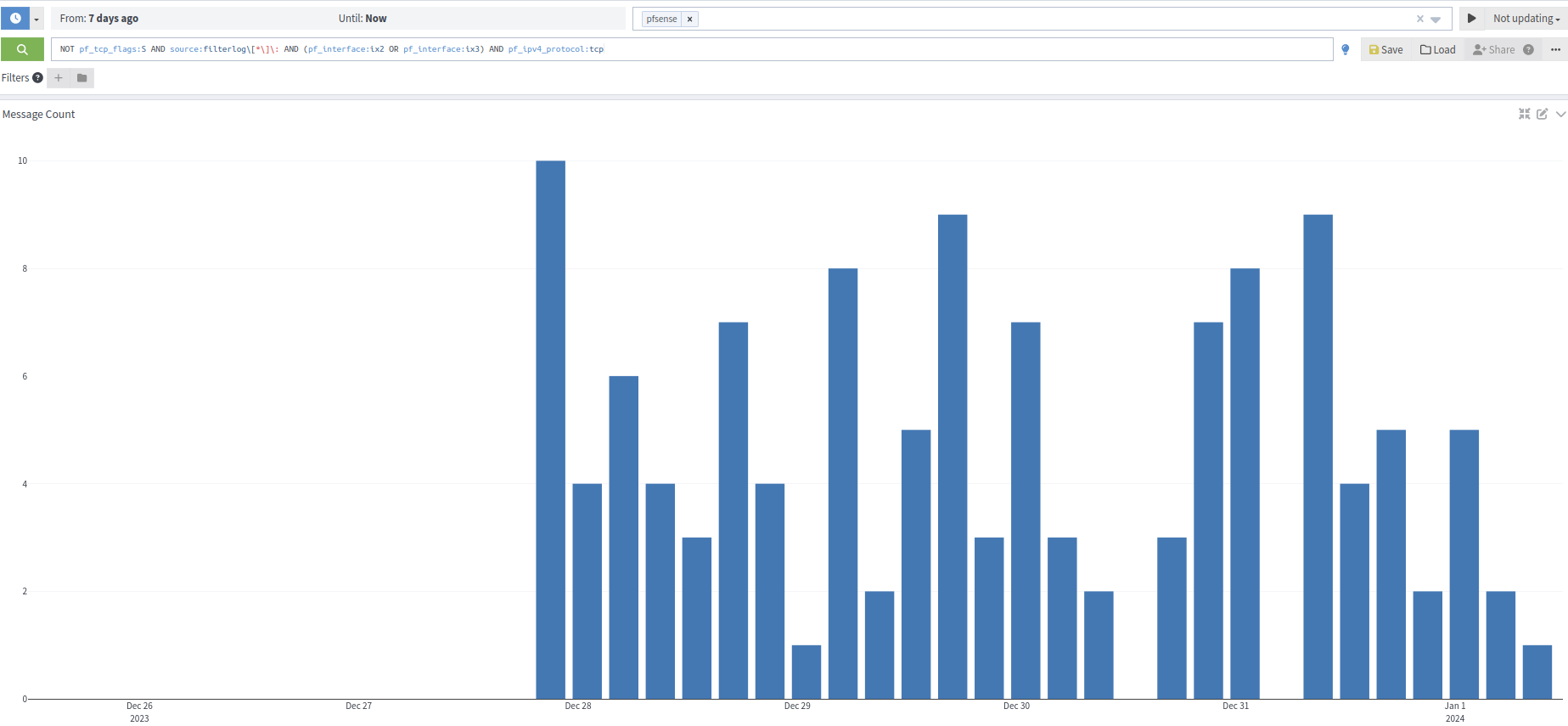
-
@mcury said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
How I didn't think about this before ??!
That is a good question, how long you been working with firewalls? @bmeeks has been in the field for many many a year ;) hehe And myself as well.. When you have to look at logs of this stuff, you look for ways to clean them up and only have stuff your interested in ;)
-
That is a good question, how long you been working with firewalls? @bmeeks has been in the field for many many a year ;) hehe And myself as well.. When you have to look at logs of this stuff, you look for ways to clean them up and only have stuff your interested in ;)
More than 10 years, I guess I'm used to suffer when checking logs

-
@mcury 10 years - just a baby then, heheh that does look pretty quiet - that is just non Syn traffic looks like. What about UDP noise? You doing any filtering by source IP that your not logging?
I block most if not all of the scanners, like shodan, etc. I also limit traffic by geoip on who can actually hit my port forwards.. Now I currently log all this traffic, if it is syn only..
There are multiple was to reduce the noise that is logged..
-
@johnpoz said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
10 years - just a baby then
Yeap, I started with Cisco routers and switches and around 15 years ago, and around 10 years ago it was just firewalls, Cisco ASA, Fortigate, Checkpoint, Palo Alto and Sonicwall, never looked back but we never forget the routing stuff =)
@johnpoz said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
that is just non Syn traffic looks like.
In the pic above, I was just filtering just TCP, but excluding SYN.. let me include UDP in it. Here it goes:
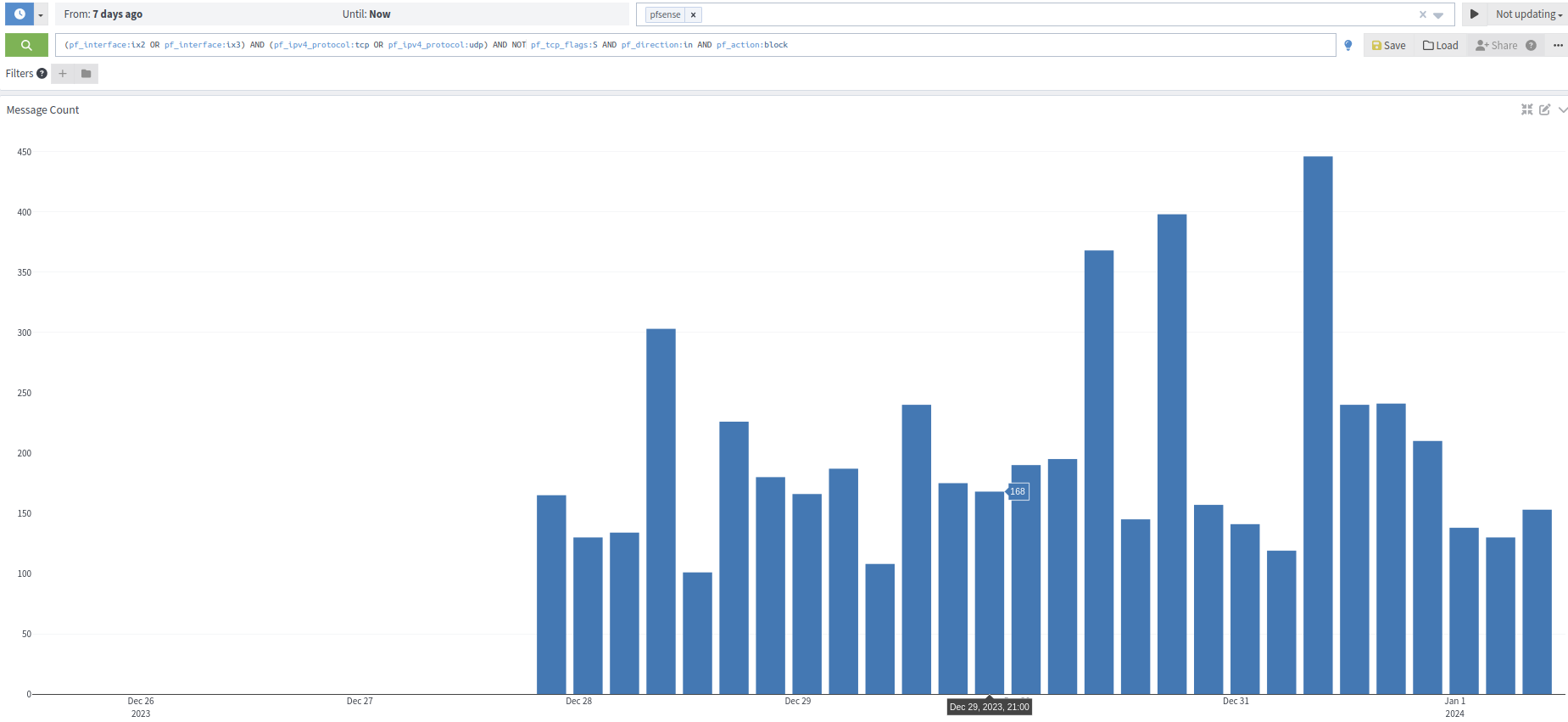
@johnpoz said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
What about UDP noise? You doing any filtering by source IP that your not logging?
Edit: Logging all TCP but TCP:S and all UDP traffic that hit both WANs, disabled packets that are blocked by the implicit default block rule.
-
@mcury said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
and all UDP traffic that hit both WANs
You might want to limit that to interesting ports if your goal is trim down the amount of noise your logging. My interesting ports is a pretty long list, but it does reduce some of the noise not logging every port ;)
-
@johnpoz said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
You might want to limit that to interesting ports if your goal is trim down the amount of noise your logging. My interesting ports is a pretty long list, but it does reduce some of the noise not logging every port ;)
I'll start preparing that list now.. =)
-
@mcury here is my list.. It prob way longer than need/should be but I had does some looking to what ports to put in there while back..
2:3 Entry added Thu, 17 Oct 2019 06:17:40 -0500 7 Entry added Thu, 17 Oct 2019 06:17:40 -0500 9 Entry added Thu, 17 Oct 2019 06:17:40 -0500 13 Entry added Thu, 17 Oct 2019 06:17:40 -0500 17 Entry added Thu, 17 Oct 2019 06:17:40 -0500 19:23 Entry added Thu, 17 Oct 2019 06:17:40 -0500 37:38 Entry added Thu, 17 Oct 2019 06:17:40 -0500 42 Entry added Thu, 17 Oct 2019 06:17:40 -0500 49 Entry added Thu, 17 Oct 2019 06:17:40 -0500 67:69 Entry added Thu, 17 Oct 2019 06:17:40 -0500 80 Entry added Thu, 17 Oct 2019 06:17:40 -0500 88 Entry added Thu, 17 Oct 2019 06:17:40 -0500 111:113 Entry added Thu, 17 Oct 2019 06:17:40 -0500 120 Entry added Thu, 17 Oct 2019 06:17:40 -0500 135:139 Entry added Thu, 17 Oct 2019 06:17:40 -0500 158 Entry added Thu, 17 Oct 2019 06:17:40 -0500 161:162 Entry added Thu, 17 Oct 2019 06:17:40 -0500 177 Entry added Thu, 17 Oct 2019 06:17:40 -0500 192 Entry added Thu, 17 Oct 2019 06:17:40 -0500 199 Entry added Thu, 17 Oct 2019 06:17:40 -0500 207 Entry added Thu, 17 Oct 2019 06:17:40 -0500 217 Entry added Thu, 17 Oct 2019 06:17:40 -0500 363 Entry added Thu, 17 Oct 2019 06:17:40 -0500 389 Entry added Thu, 17 Oct 2019 06:17:40 -0500 402 Entry added Thu, 17 Oct 2019 06:17:40 -0500 407 Entry added Thu, 17 Oct 2019 06:17:40 -0500 427 Entry added Thu, 17 Oct 2019 06:17:40 -0500 434 Entry added Thu, 17 Oct 2019 06:17:40 -0500 443 Entry added Thu, 17 Oct 2019 06:17:40 -0500 445 Entry added Thu, 17 Oct 2019 06:17:40 -0500 464 Entry added Thu, 17 Oct 2019 06:17:40 -0500 497 Entry added Thu, 17 Oct 2019 06:17:40 -0500 500 Entry added Thu, 17 Oct 2019 06:17:40 -0500 502 Entry added Thu, 17 Oct 2019 06:17:40 -0500 512:515 Entry added Thu, 17 Oct 2019 06:17:40 -0500 517:518 Entry added Thu, 17 Oct 2019 06:17:40 -0500 520 Entry added Thu, 17 Oct 2019 06:17:40 -0500 539 Entry added Thu, 17 Oct 2019 06:17:40 -0500 559 Entry added Thu, 17 Oct 2019 06:17:40 -0500 593 Entry added Thu, 17 Oct 2019 06:17:40 -0500 623 Entry added Thu, 17 Oct 2019 06:17:40 -0500 626 Entry added Thu, 17 Oct 2019 06:17:40 -0500 631 Entry added Thu, 17 Oct 2019 06:17:40 -0500 639 Entry added Thu, 17 Oct 2019 06:17:40 -0500 643 Entry added Thu, 17 Oct 2019 06:17:40 -0500 657 Entry added Thu, 17 Oct 2019 06:17:40 -0500 664 Entry added Thu, 17 Oct 2019 06:17:40 -0500 682:689 Entry added Thu, 17 Oct 2019 06:17:40 -0500 764 Entry added Thu, 17 Oct 2019 06:17:40 -0500 767 Entry added Thu, 17 Oct 2019 06:17:40 -0500 772:776 Entry added Thu, 17 Oct 2019 06:17:40 -0500 780:782 Entry added Thu, 17 Oct 2019 06:17:40 -0500 786 Entry added Thu, 17 Oct 2019 06:17:40 -0500 789 Entry added Thu, 17 Oct 2019 06:17:40 -0500 800 Entry added Thu, 17 Oct 2019 06:17:40 -0500 814 Entry added Thu, 17 Oct 2019 06:17:40 -0500 826 Entry added Thu, 17 Oct 2019 06:17:40 -0500 829 Entry added Thu, 17 Oct 2019 06:17:40 -0500 838 Entry added Thu, 17 Oct 2019 06:17:40 -0500 902:903 Entry added Thu, 17 Oct 2019 06:17:40 -0500 944 Entry added Thu, 17 Oct 2019 06:17:40 -0500 959 Entry added Thu, 17 Oct 2019 06:17:40 -0500 965 Entry added Thu, 17 Oct 2019 06:17:40 -0500 983 Entry added Thu, 17 Oct 2019 06:17:40 -0500 989:990 Entry added Thu, 17 Oct 2019 06:17:40 -0500 996:1001 Entry added Thu, 17 Oct 2019 06:17:40 -0500 1007:1008 Entry added Thu, 17 Oct 2019 06:17:40 -0500 1012:1014 Entry added Thu, 17 Oct 2019 06:17:40 -0500 1019:1051 Entry added Thu, 17 Oct 2019 06:17:40 -0500 1053:1060 Entry added Thu, 17 Oct 2019 06:17:40 -0500 53 Entry added Thu, 17 Oct 2019 12:07:49 -0500 123 Entry added Sat, 11 Apr 2020 02:33:04 -0500 33434 Odd port from pfsense forumsWow from 2019, man time flies.. Doesn't seem like that long ago that I did that ;)
-
@bmeeks
Unfortunately it seems not to work that way. I still get packets logged with these flags set: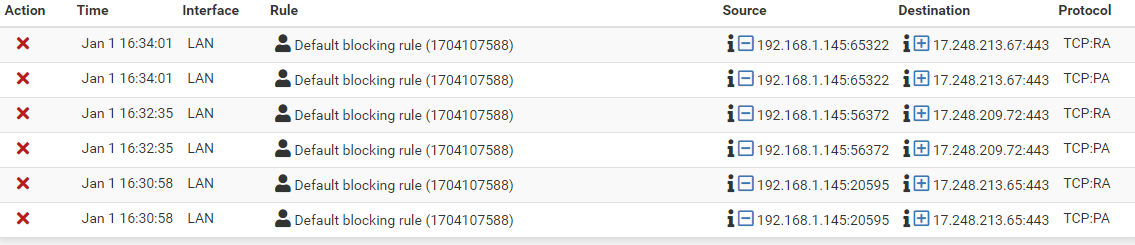
Do not get confused, I named my self created rule "Default blocking rule", but the ID is my own rule and not the pfSense default rule.
Here is the rule I created:

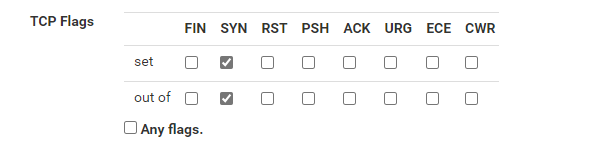
What am I doing wrong?
-
@johnpoz Wol, that is indeed a long list, I was thinking about ports:
7 WOL common used 9 WOL default 53 DNS 67:68 DHCP 80 QUIC 88 Kerberos 123 NTP 443 QUIC 500 IPsec 514 Syslog 1194:1198 Common OpenVPN ports.. 4500 NAT-T -
@m0urs said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
What am I doing wrong?
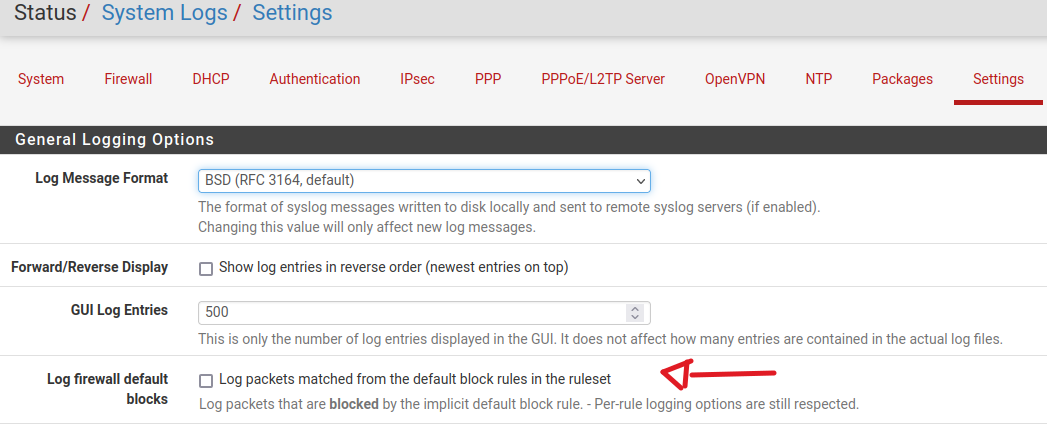
Did you disable this ?
-
@mcury yeah its a bit long.. I went a bit overboard when was looking into ports that might be good to log.. I could prob trim it down.. But I really don't see much udp traffic even with that long list.
Yeah default deny logging is off
-
@mcury said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
Did you disable this ?
Yes.
As I said: The logging comes from my own created rule and not from the pfSense default blocking rule.
-
@m0urs said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
The logging comes from my own created rule and not from the pfSense default blocking rule.
I'm trying to replicate this here, but now filtering TCP:S only, in my LAN networks.
-
Are you using that "Invert match" option for source or destination in that rule ? So far, I'm unable to replicate this behavior here but I'm not using those options.
-
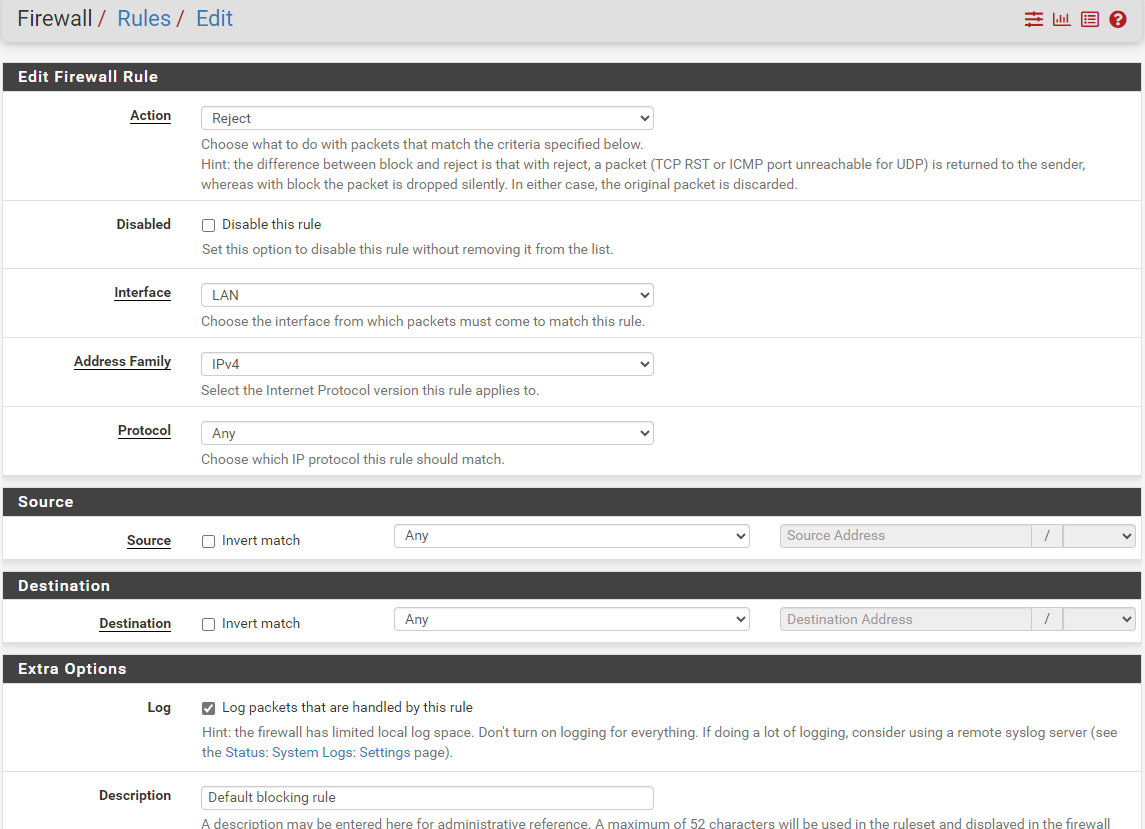
@mcury No, I do not use "Invert Match". That is my definition, together with that TCP Flags option mentioned above:
-
@mcury ah, maybe this does not work if protocol set to "Any"? I will try with Protocol set to "TCP" ...
-
No, unfortunately that did not change anything. These kind of packets are still logged by that rule:
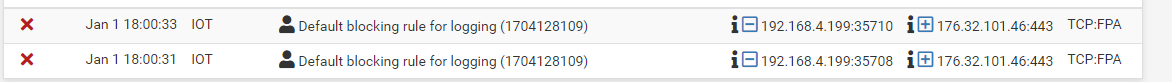
You you explain me a bit more, what how this "TCP flag" setting is working? I still did not get it. What exactly is meant by "set" and "out of"?
-
@m0urs said in Do not log TCP packets with flags TCP:RA / TCP:PA etc.:
What exactly is meant by "set" and "out of"?
https://docs.netgate.com/pfsense/en/latest/firewall/configure.html#tcp-flags