OpenVPN recommended Data Encryption Algorithms when using SG-2100 appliance's crypto engine?
-
https://forums.openvpn.net/viewtopic.php?p=119900
I posted here also to see what OpenVPN community says about the chips

-
I got the impression from the discussion that was had here:
and specifically
@stephenw10 said in Resolved: The command '/usr/local/sbin/ping-auth -s > /etc/thoth/thothid 2>/dev/null' returned exit code '127', the output was '':
It is not. The current 2100s do not include it.
that the newer (2100's) don't have the chip anymore and that "they" would prefer it just not be used. Hence the issue you saw when you installed to a fresh SSD the install didn't include "stuff".
I have no background in the choice they made in this regard, but it likely boils down to simply a choice of don't support the chip even if the device has one. or dev speak support 1 code path, not 2.
Did you ever get a comment on the redmine you opened? -
@jrey My 2100 has it and in OpenVPN it sees it, the comments on the redmine is that the application that can read the chip id is no longer supported in 23.09 so they are going to remove the GUI window for it in future releases. Again my 2100 was purchased with it and it seems to be functional in that regard so I am a bit confused. Maybe going forward all 2100s will not support it.
-
@jrey haha didn't include "stuff"
Well it does after we fixed the missing file
-
@JonathanLee said in OpenVPN recommended Data Encryption Algorithms when using SG-2100 appliance's crypto engine?:
application that can read the chip id is no longer supported
Yes, but i'd be betting that if this ^ "stuff" was removed this round, eventually so will support for the chip for those of us (you, me and others that still have the chip) vs. the newer 2100's that don't have it.
Certainly OpenVPN can see it now and the problem of it not being supported at all can be pushed down the road. (maybe even past the life of the equipment) That's all.
However, if they "wanted" the GUI to display the ID, the logic could have been added to "you Have one = display it" , "Not there = don't" but the choice was made to simply remove it for all fresh installs. Always step one in eventual feature removal.
-
@jrey 23.09.01 does not see it in OpenVPN but it does see it in the menus and advance configuration, 23.05.01 listed it in openVPN
-
FYI- The "thoth" chip on the 1100/2100 is not associated with cryprographic acceleration, it's for other operations such as authentication. Not quite the same as a TPM but closer to that than an accelerator.
The accelerator on the 2100 is SafeXcel.
DCO only supports ChaCha and AES-GCM, and the only one of those that the SafeXcel chip accelerates is AES-GCM, so remove ChaCha from the list on the server and it should be OK.
Though you may be better off disabling SafeXcel and enabling the newer IPsec-MB acceleration since (a) in most cases it's faster than crypto accelerator chips, and (b) it can accelerate both AES-GCM and ChaCha so you aren't limited in algorithm choices. Despite the name, IPsec-MB also accelerates OpenVPN DCO and WireGuard. See https://docs.netgate.com/pfsense/en/latest/hardware/cryptographic-accelerators.html#supported-devices
You can change that under System > Advanced on the Misc tab, enable IPsec-MB and disable SafeXcel and then reboot.
-
@jimp
curious for platforms that support QAT which is better? To enable IPsec-MB or to rely on QAT?
Im running an ovpn client privacy vpn and with DCO enabled im getting great speeds but i noticed wireguard has the edge in performance. -
@michmoor said in OpenVPN recommended Data Encryption Algorithms when using SG-2100 appliance's crypto engine?:
@jimp
curious for platforms that support QAT which is better? To enable IPsec-MB or to rely on QAT?
Im running an ovpn client privacy vpn and with DCO enabled im getting great speeds but i noticed wireguard has the edge in performance.I don't have any exact results handy (they may be posted on the shop somewhere) but in many cases IPsec-MB meets/exceeds the speed of QAT. There are some hints in the docs about using both together.
https://docs.netgate.com/pfsense/en/latest/config/advanced-misc.html
-
@jimp
Ahh gotcha. Whats interesting is that IPsec MB works with chacha20.
In my use case it makes sense to actually enable MB as i get the best of both worlds - Support for both types of encryption (GCM/chacha) and the implicit support of WireGuard which QAT doesnt support (yet?!).
I need to do more testing but this is interesting.
For what its worth im testing on a 6100 -
@michmoor There are some newer QAT devices that support ChaCha but IIRC they are not yet widely available and even if they were, I don't think FreeBSD has drivers for them yet. But since IPsec-MB performs so well (and it really flies on the CPU in the 4200 with AVX2), there are even less reasons to lean on hardware QAT in the future for these sorts of roles.
But the hardware is always evolving, we try to keep on top of whatever is best as new things develop.
-
@jimp I still can't get vmstat to show anything for OpenVPN on the SafeXcel chip use with IPsec-MB enabled, disabled ChaCha removed, added, DOC enabled, disabled, it shows this ID error.
Is there something I am doing wrong? I think you told me it should be automatically used but its showing nothing for use and this ID error when I connect. I created a different post for that as that is issues not related to this post.
dco_update_peer_stat: invalid peer ID 1 returned by kernel
https://forum.netgate.com/topic/185411/23-09-01-hardware-crypto-showing-no-hardware-crypto-acceleration-for-system-with-crypto-chip-installed/
I understand that it is automagic now but it still is having issues for my 2100 in 23.09.01
Thanks
-
@jimp
Ive loaded IPsec MB, fresh reboot, and so far its about the same with QAT. Doesnt hurt to keep it enabled so i'll leave it.
We know that DCO takes the load off the CPU but i just want to share my monitoring graph. Can you tell when DCO was enabled? haha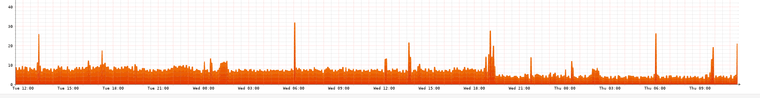
-
@jimp
Internet line is 500/500 but ATT Fiber does over-provision.
Here are the wireguard results with IPsec MB
Im not complaining.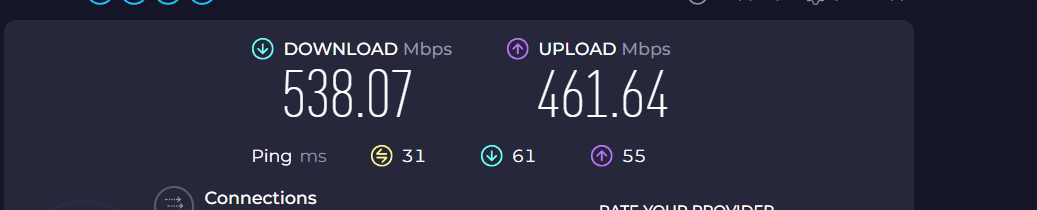
-
@JonathanLee said in OpenVPN recommended Data Encryption Algorithms when using SG-2100 appliance's crypto engine?:
@jimp I still can't get vmstat to show anything for OpenVPN on the SafeXcel chip use with IPsec-MB enabled, disabled ChaCha removed, added, DOC enabled, disabled, it shows this ID error.
ARM is not like x86, not everything shows up like interrupts, IIRC there is no visible way to tell that SafeXcel is being used except by secondary observations (e.g. improved encryption throughput when enabled vs disabled or lower CPU usage when enabled vs disabled).
I'd keep that discussion going on your other thread since it's more relevant there. But if you can pass traffic, the error is probably not harmful. And you'll need to run performance tests with it enabled/disabled and measure at least CPU usage and throughput when testing. But again, do all that and post it in the other thread.
-
@jimp thanks I got it to show logs I posted everything in the other forum.
Have a good one
-
@jimp Quick Question I am learning that you should not enable both IPsec-MB and SafeXel at the same time, is this true? If so should I open a redmine so that it will not allow the GUI to enable both?
Per @kprovost "JonathanLee I mean, you can't use both at the same time. The data's only ever going to be processed by one of them. I'd have to go dig deep in the code to tell you how the selection is made if both are enabled, but it looks like in this case it ends up using IIMB.
IIMB is fine, but probably not quite as fast as SafeXcel. You're getting crypto acceleration either way, just in a different way."
Leading to if @kprovost has a bug fixe for crypto-graphic code set that OpenVPN uses and it looks like it was merged. So I am confused at this point.
Can we or can't we use both of them?
This was the bug fix he worked on. So I assume he is a reputable source to state you can't use both with OpenVPN.
This was the buffer bug fix
https://sourceforge.net/p/openvpn/mailman/message/58728397/
https://github.com/OpenVPN/openvpn/issues/487Does anyone have clarity with what occurs when both are enabled?
When the GUI has both IP-sec and SafeXel marked active -
@JonathanLee Either one will work. Things will even work if you have both activated, but then only one of them will do the work. We're not going to be splitting the cryptographic work between the two, or doing it twice just so both will get used.
-
@kprovost The speed difference is substantial with only having one enabled so much so I would say this would need a Redmine to only allow one to be selected at a time. Anyone else agree?