OpenVPN does not work on bridged PFsense router
-
@viragomann Yeah, I tried that already, it doesn't work.
The highlight for me is that it works on Mobile networks, but doesn't work a the Home Router. Is this supposed to be a ISP issue or pfsense?
-
@george1116
So the server log, you've posted above shows IPv6 connection attempts. With an IPv4 only in the config, the client can only use v4. So I'm wondering, what the server log shows then. -
@george1116 said in OpenVPN does not work on bridged PFsense router:
The highlight for me is that it works on Mobile networks, but doesn't work a the Home Router
Over the internet to the WAN IP?
Which IP version does it use in this case?
-
Not quite.
When it showed the IPV6 connection we had indeed changed it to useUDP IPV4 and IPV6. But once I have changed it back toUDP IPV4it's only connecting via IPV4Over the internet to the WAN IP? Which IP version does it use in this case?In this case it uses IPV4
-
@george1116 On your firewall does WAN interface status show only IPV4??
-
@JonathanLee Yes, before we changed it it showed only IPV4, after we changed it I added IPV6 manually, but I have since returned to IPV4.
-
@george1116 under pfsense go to status and wan interface does that show a ipv4 address only? If so set that in the config file where f.q.d.n is
-
@JonathanLee Yeah, I did exactly that already. It didn't work sadly.
-
@george1116 On pfSense under Status ---> system logs ----> tab OpenVPN what is showing for errors?
-
@george1116 Can you access syslogs on your router in front of pfsense??
It looks like a certificate issues but you said it works. You said also it works without the pfSense firewall (hence you removed the firewall it to test VPN with only router and device you want to connect to) so I am thinking the certificate was generated without pfSense, thus you imported that certificate into pfSense right?
Regenerate the certificates or import the correct one into pfSense. You have some cert mix up here and it won't authenticate to it.
This is the area with the mix up you need the correct TLS certificate TLS Key has an issue.
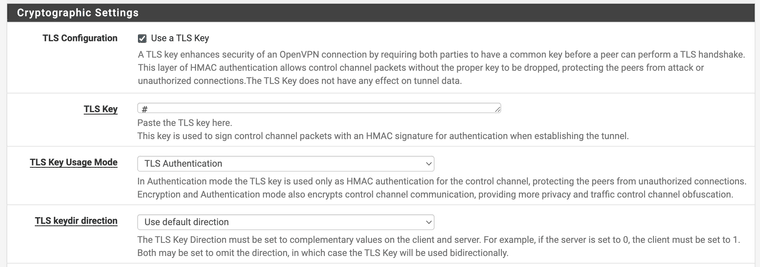
-
All the certificates were generated in pfsesne.
The error logs shown is the same on the server as the client, TLS handshake timing out.
-
@george1116 Try to to set the key direction a different way
-
@george1116 What did pfSense System Logs show for OpenVPN?
-
@JonathanLee
The same error as beforeJan 4 19:03:36 openvpn 23226 xx.xx.xx.xx:64486 TLS Error: TLS handshake failed Jan 4 19:03:36 openvpn 23226 xx.xx.xx.xx:64486 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Jan 4 18:17:26 openvpn 23226 Initialization Sequence Completed Jan 4 18:17:26 openvpn 23226 UDPv4 link remote: [AF_UNSPEC] -
It sees the connection at the firewall and shows TLS error, it's got to be the certificate negotiation. This is an issue with the certificates. If you look at your firewall logs now on that tab under system and look for that time stamp see if a port is blocked. Most often VPN rules are created automatically, are you running auto outbound nat? or manual?
-
I am running auto outband NAT. I haven't noticed any entry in the firewall logs to suggest that the port is blocked. If it's able to work on my mobile network but not on my other network I would assume it isn't blocked by the firewall.
-
@george1116 Is your mobile network going into pfsense?
Have you also created a user profile on pfsense? Are you removing pfsense from the equation?
-
I have considered my ISP, but I am using the same provider on my mobile so that shouldn't be the problem.
I have a user profile which I use to log into pfsense. The only way I can use pfsense OpenVPN right now is to create a hotspot from my mobile phone, connect my PC to that network and then the VPN works, it just doesn't make sense to me, if there are issues with tls handshake then I shouldn't be able to use my mobile as well hotspot no?
-
@george1116 said in OpenVPN does not work on bridged PFsense router:
Tunnelblick
This is a different vpn client here....
When you are using pfSense to authenticate you are going to use the login profile you created to log on to the firewall (vpn server) after that you need to direct traffic with the OpenVPN tab on the firewall rules.
I think what you did , correct me if I am wrong is created or set a VPN with the "Tunnelblick" software first and connected without pfsense in the equation after that you wanted it to be secure so you installed OpenVPN on pfsense following a guide like this??
https://www.wundertech.net/how-to-set-up-openvpn-on-pfsense/
However when you created a username and profile on the firewall locally you are going to be authenticating to that with that username and password so the client on the mac running Tunnelblick is not needed here. It would only need to direct traffic to that client as your VPN tunnel goes to the firewall and stops and traffic flows out of it as if your sitting on the lan.
Without pfsense your vpn goes directly to the client and that's what it is authenticating to meaning you are not using pfsense at all your wifi is connected to your hotspot? That is why I think this is the issue your using your Tunnelblick login and expecting that same login to work with pfSense however that is specific to Tunnelblick and that is why it has certificate issues as it says hey tunnelblick let me log in and pfsense says no way I want the pfsense version of software (OpenVPN)
For you to use only pfSense you need to use the username and password you created on the firewall for use with OpenVPN after use remote desktop locally with that private ip you want to access.
-
@george1116 Try this
follow this guide https://www.wundertech.net/how-to-set-up-openvpn-on-pfsense/
after use OpenVPN download make sure it is the specific OpenVPN application on a windows pc or mac or iphone, it looks like a orange keyhole.
use the remote username and login for pfsense created in the guide see if you can connect, nothing else do not use Tunnelblick do not delete it do not try to connect to it just use the firewall info, once you do that see if you get a connection, if you do we can create a lan rule so you can work without Tunnelblick software running.
https://openvpn.net/client/
Use this client to test it, for this test you are removing use of tunnelblick so just shut that pc off when you run this test set it up as if you are logging on to the pfSense as the openvpn server