Unable to Access WebConfigurator UI and Unable to SSH into pfsense
-
I was able to ssh into the firewall from the console as described above. I also was able to get a response using the curl command as described above.
Yes, pfBlockerNG and Suricata are running on this firewall although Suricata is not in the blocking mode.
I see that there is a command in the console menu (#15) to restore from a previous configuration backup. However, when I list these backups I can only see the last 7 backups and these are one hour apart starting about an hour and 15 minutes ago. How can I see the rest of the 30 backups? The reason for each of the 7 most recent backups that I could see on the screen is "pfblockerNG: saving Unbound custom options". This leads me to suspect there might be something wonky going on with pfblockerNG...
-
@dougs yeah pfblocker loves to do that - I keep meaning to look into a way to stop it, or change how often it does it.. Part of the reason I changed my number to 100 hehehe
I would consider an update to items in a list or alias to be a config change.. That it makes constant changes to your config backup could be problematic for sure, especially when they happen often.. If it was once a day, or only when you actually interacted with the config via the pfblocker gui, etc.
If you have the antilock out rule enabled, it should be impossible for pfblocker to create a rule that would lock you out.
-
There's an anti-lockout rule in place so I shouldn't be locked out. However, I am!
I haven't made any changes to pfblockerNG in days.
It looks like I might need to do a reset to defaults and restore from a backup, yes? I'm fine with doing that as long there isn't any other easier way of remedying this! I just have to work around my wife! She thinks everything is fine as long as she has a working Internet connection! :)
-
Yup the anti-lockout rule should apply before anything pfBlocker does if it's present.
-
How can I verify if the anti-lock out rule is in effect or not from the console?
-
I'm reviewing this page: https://docs.netgate.com/pfsense/en/latest/troubleshooting/locked-out.html
If I enable WAN access to the firewall as follows: #pfSsh.php playback enableallowallwan, would this still require that one authenticate in order to access the Web GUI? I don't want to open the door to the whole wide world if such authentication isn't needed!
-
@dougs Yes it still needs the password.
To be clear the anti lockout rule is a firewall rule...it controls whether the client can connect to the web server or not, not whether one can log in. If you see an SSH prompt or web page then the firewall isn't blocking you.
-
Yes you still have to authenticate but doing that adds pass rules on the WAN which you probably don't want as you say.
Try running:
pfctl -vvsr | grep -A 4 anti
That will show you if the antilock rules are present and if they are opening states and passing packets.You can add a pass rule to LAN using easyrule if you have to.
https://docs.netgate.com/pfsense/en/latest/firewall/easyrule.htmlDo you use policy routing at all? With gateways set on the rules? That can end up bypassing the firewall itself.
-
Running "pfctl -vvsr | grep -A 4 anti" gave me this: https://imgur.com/a/fgXHIEx Looks like the anti-lock out rule is in effect, yes?
I tried:
#easyrule pass lan tcp <my computer IP addr> <firewall LAN addr> 443Didn't work for both Web GUI and ssh . Is this easyrule only for WAN addresses?
I'm not familiar with policy routing so I would imagine it's not being used here.
-
@dougs said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
I'm not familiar with policy routing so I would imagine it's not being used here.
Did you have rules with a gateway selected, or is the gateway just an *
-
Not sure. I might have had an alias pointing to the firewall and used that in some rules instead of an asterisk. We use only one ISP so one gateway.
-
@dougs said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
The reason for each of the 7 most recent backups that I could see on the screen is "pfblockerNG: saving Unbound custom options". This leads me to suspect there might be something wonky going on with pfblockerNG
Pretty sure it saves a new config every time an update runs. (I would think, because it's regenerating rules)
-
@dougs said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
We use only one ISP so one gateway.
Talking about your lan side rules, do you have say your wan_dhcp selected?
example..
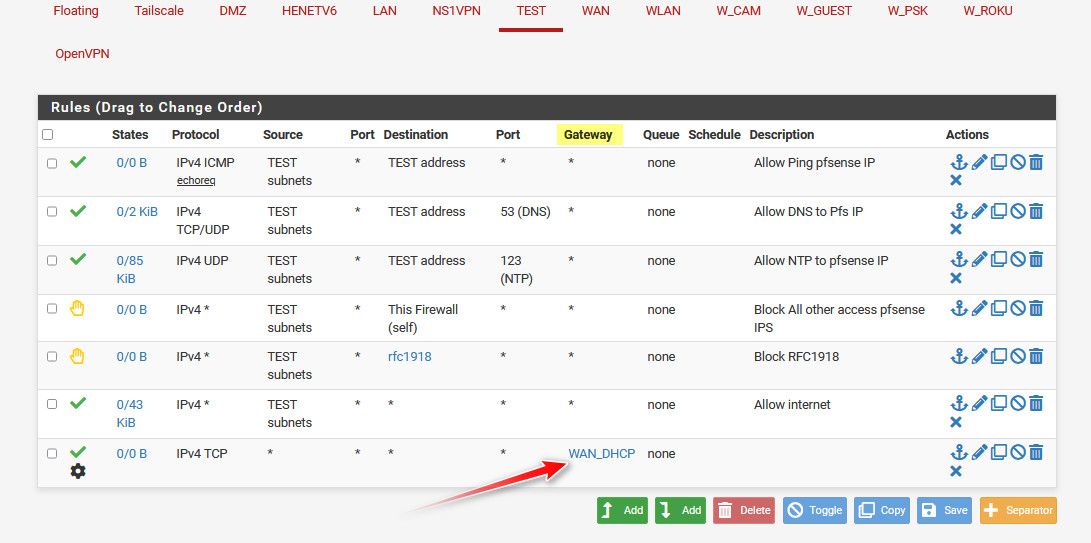
See where the gateway is called out - that would be policy routing.
-
I don't believe we manipulate the gateway address in that fashion.
-
@dougs said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
I don't believe
Prob behoove you to double check, you never know what gets set sometime - I agree normally you wouldn't have this set unless you had a specific reason. But you would be surprised how many posts end up being they are doing PBR is the cause they can't get some other vlan, etc.
And even if you were doing it, it shouldn't prevent access with antilock which would be evaluated first.
-
@dougs said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
https://imgur.com/a/fgXHIEx
Yes that shows the anti-lockout rules are present on LAN. But also that they have passed nothing; 0 bytes/packets/states.
So either some other rule is passing them. Somehow. Or maybe the traffic never reaches pfSense. Or perhaps it's being forwarded.
You could try running a tcpdump from the CLI while you try to connect to confirm it's at least trying.
-
@stephenw10 said in Unable to Access WebConfigurator UI and Unable to SSH into pfsense:
CLI while you try to connect to confirm it's at least trying
could be sending it to something else.. sniff is yeah what I would do - have access to console, sniff on pfsense itself to validate traffic gets there.
-
About a week ago, I decided to reset the pfSense firewall to factory defaults from the console menu and left it running without changing any configuration options aside from setting the WAN/LAN interfaces, modifying the console dashboard and creating a DHCP server IP address range. Everything else was left as is.
I was able to access the Web GUI for a couple days. Just 2 days ago, I discovered I could not access it nor could I ssh into it!
Restarting the Web Configurator does not allow me to access the firewall web site.
Executing
pfctl -vvsr | grep -A 4 antishows this:
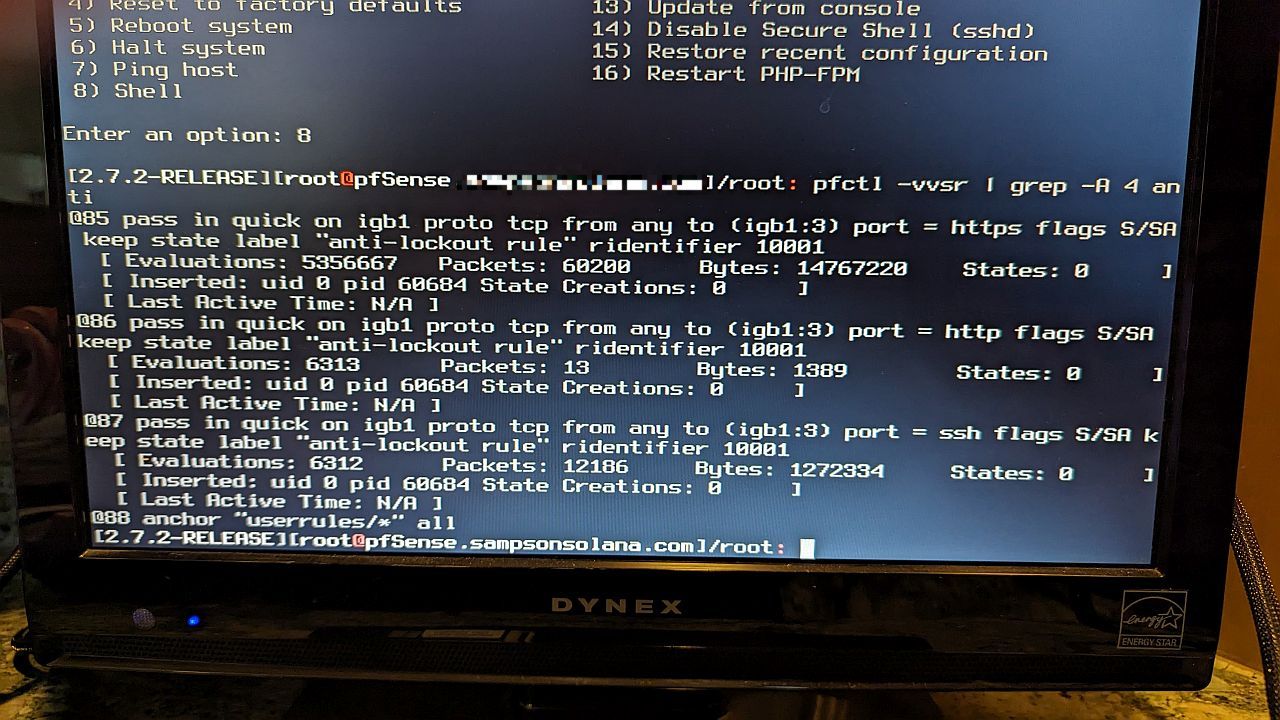
https://imgur.com/a/J2mbVCxTried running:
#easyrule pass lan tcp <my computer IP addr> <firewall LAN addr> 443and it states the rule was successfully created. However, I cannot access the LAN address of the firewall nor could I ping it from the computer IP address. Tried it from another computer with similar results.Did a
zpool scrub pfSenseand did not indicate any errors.Every system on the LAN side can access the Internet normally-- including our Samsung TV sets and an Enphase IoT device among others.
This is on an older Protectli FW6C purchased in 2021. https://protectli.com/wp-content/uploads/2019/01/FW6C-Datasheet-190104.pdf
At this point, I am not sure what else to do aside from reformatting the drive and starting all over again. Please advise.
-
@dougs and no simple tcpdump?
You could have no rules and completely wide open, still never works if your traffic never gets there..
Your anti lock rule is there.. don't show any states.. Do a simple tcpdump when you try and get there..
-
Mmm, that sure starts to look like it's just not hitting pfSense at all.