pfSense on top of Proxmox. Is m Setup okay?
-
Hello
I have a 6x LAN Port server, where I have installed Proxmox and on top of Proxmox I have installed pfSense.
Unfortunately, I'm not so familiar with networking and in the beginning of learning.
Therefore I ask here, if someone could have a look at my setup, to check, if this setup makes sense and if there are any suggestions what should be changed.
I am not restricted regarding IP addresses and subnets. So I can change pretty much anything based on suggestions.This is my networking situation.
My ISP Router is already in bridge mode.
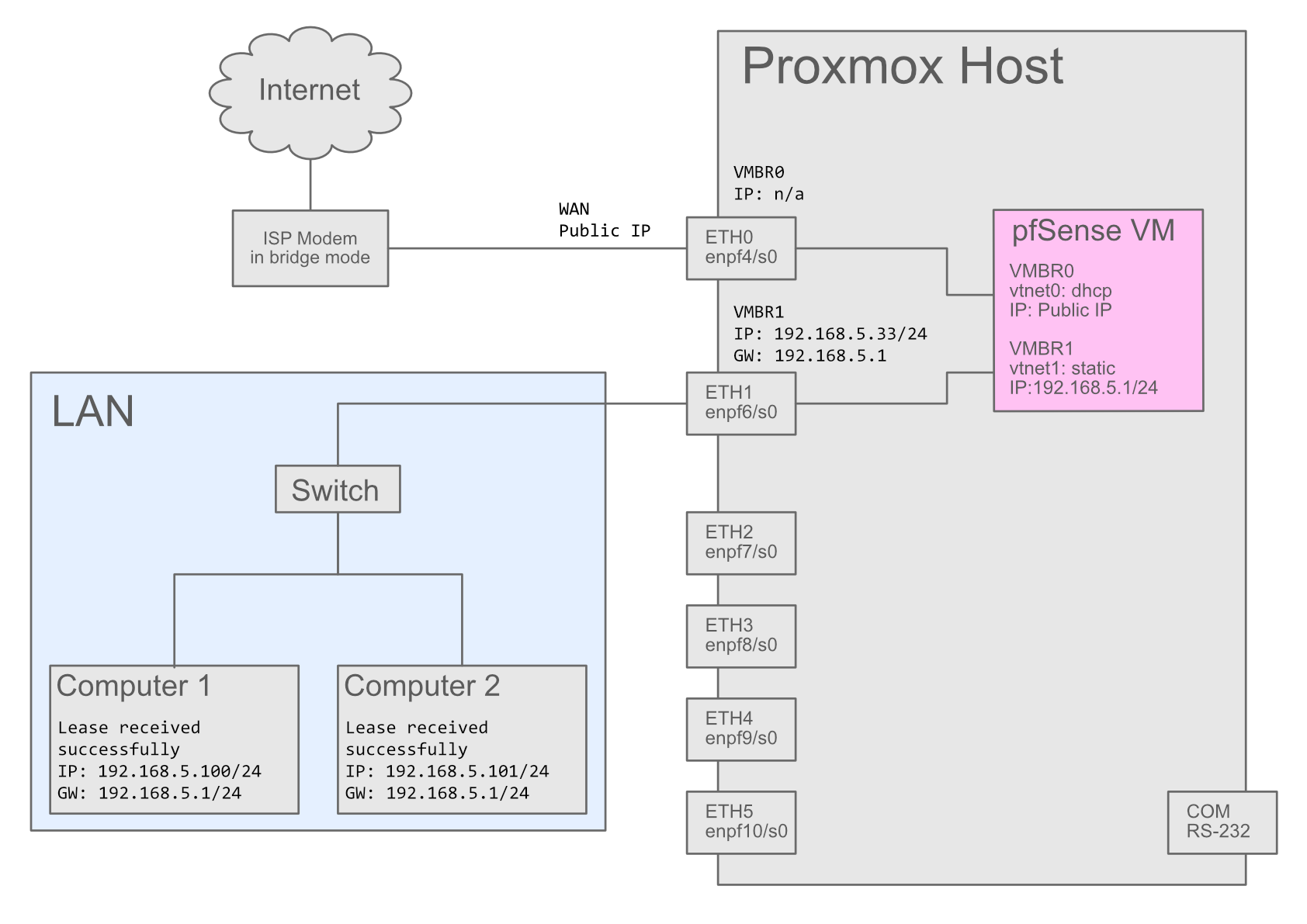
This is my
/etc/network/interfacesconfiguration:auto lo iface lo inet loopback iface enp4s0 inet manual #ETH0 - WAN iface enp6s0 inet manual #ETH1 - LAN iface enp7s0 inet manual #ETH2 - LAN iface enp8s0 inet manual #ETH3 - LAN iface enp9s0 inet manual #ETH4 - LAN iface enp10s0 inet manual #ETH5 - LAN auto vmbr1 iface vmbr1 inet static address 192.168.5.33/24 gateway 192.168.5.1 bridge-ports enp6s0 bridge-stp off bridge-fd 0 #ETH1 - LAN auto vmbr0 iface vmbr0 inet manual bridge-ports enp4s0 bridge-stp off bridge-fd 0 #ETH0 - Sunrise Modem source /etc/network/interfaces.d/*I am also not sure about all the log entries in my firewall log.
The log entries look as follows: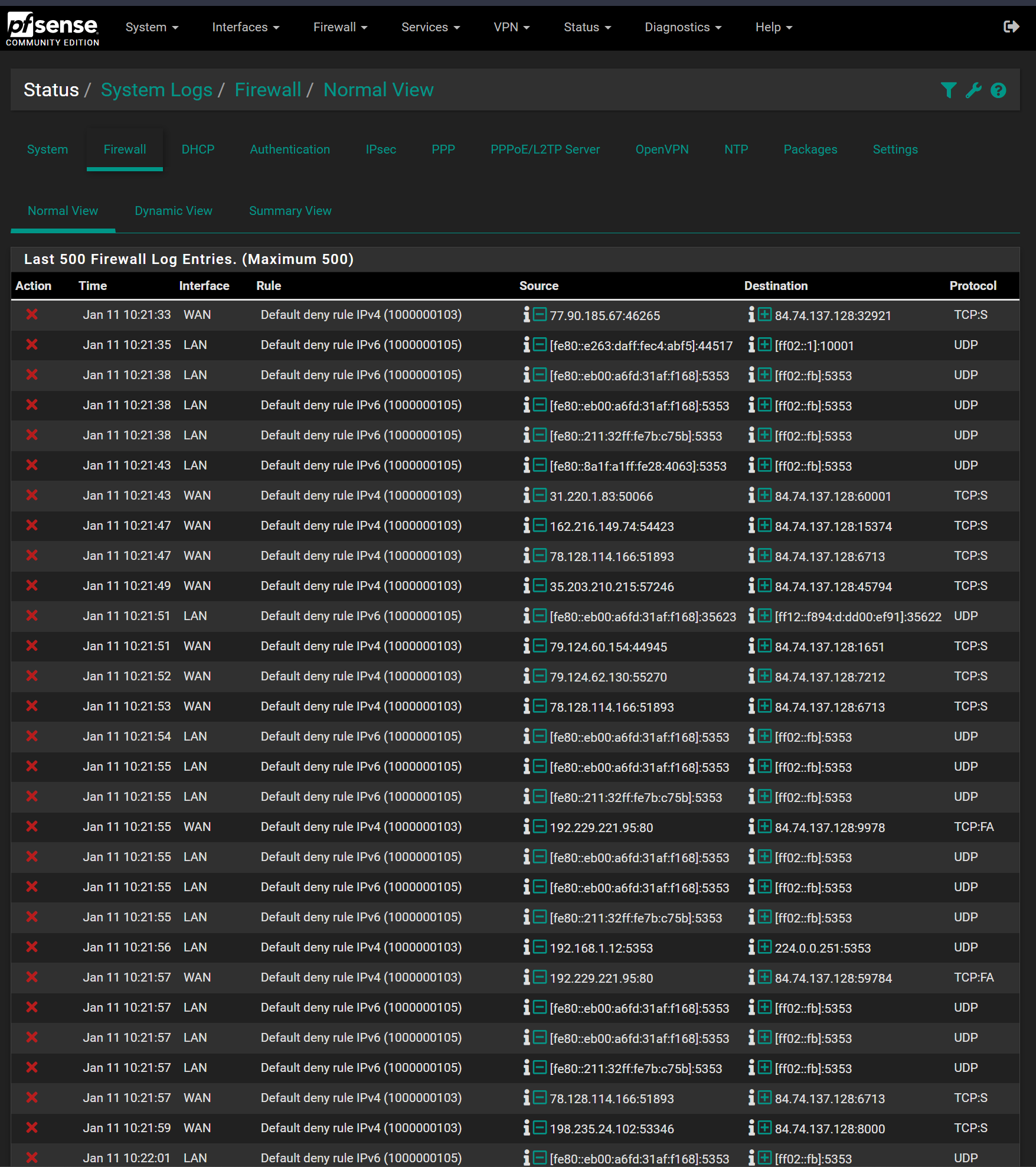
Do I have maybe somewhere made a mistake in my setup, because I have so many entries, or is this normal?
If someone could have a look at the whole situation, I would be very thankful.
Best regards
Simon -
@miracuru
It's a pretty simple setup. But it's all right so far.The blocks on the logs are just noise from the internet hitting your WAN address.
BTW: if you want to obscure your WAN IP you have also to do this in the filter log screenshot. -
Hi @viragomann
Thanks for the check. Okay, I thought about to obscure the WAN IP in the screenshot, but forgot somehow to do it.
I can't edit the post anymore, as it is only allowed in the first few minutes. -
I have here an additional question.
I watched a few tutorials on how to install pfSense on top of Proxmox.
Some of the tutorials did it the way I did it now. But in other tutorials, VMBR0 was not assigned to pfSense, but the interface "iface enp4s0 in my case" was forwarded to pfSense using IP tables. Does this setup have any advantages over my setup? -
@miracuru said in pfSense on top of Proxmox. Is m Setup okay?:
Does this setup have any advantages over my setup?
No, it is for cloud setups with one NIC only.
-
@miracuru
The sense of such configuration is that you can access Proxmox if it is hosted in the cloud, while all other traffic is forwarded to pfSense.
So Proxmox would need to own the public IP in this case. -
@viragomann and @Bob-Dig thanks for your help.
Okay, then I guess that the setup which I currently have, with two NIC's is better suited for my case, because the Proxmox host isn't exposed to the WAN network, if I get that correctly? -
@miracuru
In fact, it is. So you can have the public IP on pfSense and can let pfSense do the whole filtering.Otherwise you would have double-NAT for devices behind NAT and you would have to configure the masquerading for outbound traffic on Proxmox.
-
@viragomann Have many thanks for your kind help and explanation.
-
@miracuru
As was mentioned by @viragomann the "Default deny rule IPv(4|6)" logs are normal. Actually they show that pfSense is doing its basic job, which is (by default) blocking all incoming connections to WAN.You could implement a firewall rule on the WAN interface which does the same thing, but doesn't log the blocks. Enable that rule when you don't want pfSense to record all the WAN blocks in the logs. If you want to start logging the WAN blocks, just disable your rule and the defaults will kick in again.
Also, it may be possible to directly connect the enpf4s0 and enpf7s0 interfaces to pfSense via PCI-Passthrough. This will depend on hardware compatibility, but could be worth looking into; just food for thought.