Missing Secure Cookie Attribute (HTTP) (CVSS: 6.4) OID: 1.3.6.1.4.1.25623.1.0.902661
-
Vulnerabilities by Issue on PFsense Firewall Issue 1: Missing Secure Cookie Attribute (HTTP) (CVSS: 6.4) OID: 1.3.6.1.4.1.25623.1.0.902661 Ports: 443/tcp (https) Summary: The remote HTTP web server / application is missing to set the 'Secure' cookie attribute for one or more sent HTTP cookie. Affected Nodes: Internal gateway (IP/MAC) Vulnerability Detection Result: The cookies: Set-Cookie: PHPSESSID=replaced; path=/ are missing the "Secure" cookie attribute. Solution: Set the 'Secure' cookie attribute for any cookies that are sent over a SSL/TLS connection. Vulnerability Insight: The flaw exists if a cookie is not using the 'Secure' cookie attribute and is sent over a SSL/TLS connection. This allows a cookie to be passed to the server by the client over non-secure channels (HTTP) and subsequently allows an attacker to e.g. conduct session hijacking attacks. Vulnerability Detection Method: Checks all cookies sent by the remote HTTP web server / application over a SSL/TLS connection for a missing 'Secure' cookie attribute. Details: Missing 'Secure' Cookie Attribute (HTTP) (OID: 1.3.6.1.4.1.25623.1.0.902661) Version used: 2023-01-17T10:10:58Z References: https://www.rfc-editor.org/rfc/rfc6265#section-5.2.5,https://owasp.org/www-community/controls/SecureCookieAttribute,https://wiki.owasp.org/index.php/Testing_for_cookies_attributes(OTG-SESS-002)
Is this vulnerability addressable?
-
The cookie from the GUI is marked secure and has been for years, provided your GUI is using HTTPS. If you are not using HTTPS then how can it be secure?
https://github.com/pfsense/pfsense/blob/master/src/etc/inc/auth.inc#L2090
You can check your browser's debug function and confirm it's set.
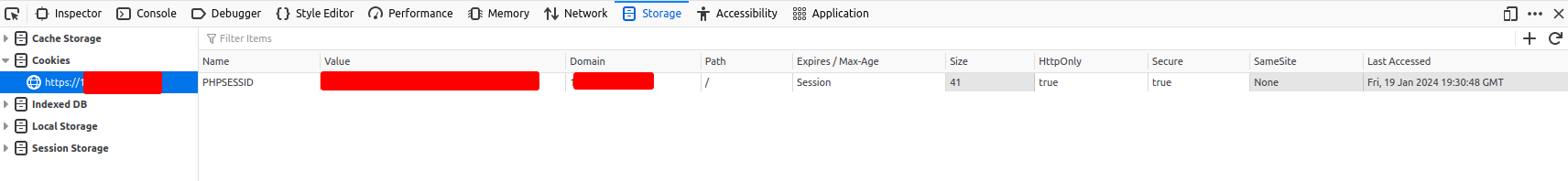
So there are two possibilities:
- Your GUI is not using HTTPS, in which case you should immediately correct that and change it to HTTPS.
- The scanner is not hitting the GUI web server, but some other web server, so you should focus on whatever that server is.
-
Thank you. I was able to confirm it was a false positive.