Client can't see LAN servers after connect
-
@utnuc
According to the client log, the server pushes the ifconfig 10.0.0.3/24, and as you said above 10.0.0.2 is the LAN IP of the server.
This could only happen if the server is in tap mode, however. Or there is something pretty faulty on the server.Also in the outbound NAT, there are two entries 10.0.0.0/24.
Check out in Status > interfaces, which are using this subnet. -
@viragomann I think he is using the tunnel network same as his lan network.. Which is going be problematic for sure..
Here is mine for example.. You can see the tunnel networks are auto added to the outbound nat.
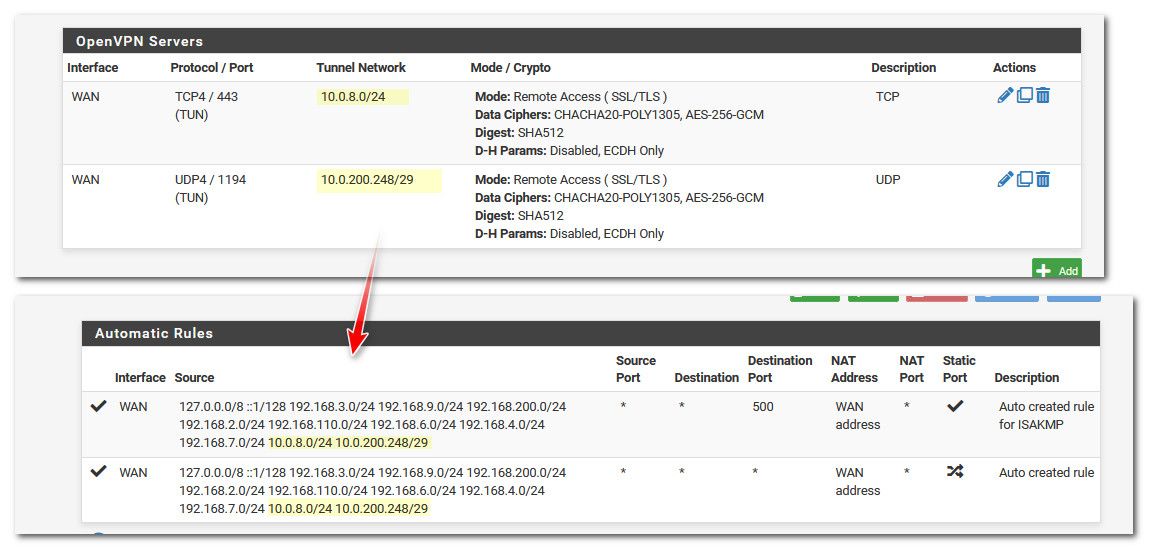
-
@johnpoz
Ah, this could be the reason for sure. -
@johnpoz Thanks. Is there an easy fix for this? I'm willing to reconfigure the VPN from scratch. Although I'm not sure if this will fix the problem with my DNS resolver.
-
@utnuc your tunnel network should just be some other network that does not overlap with your existing network(s).. That is just a 2 second fix, change it.
As to your dns problem.. That could be related to your problem with overlapping tunnel network.
You also need to make sure your ACLs on unbound are allowing a query from whatever your tunnel network is.. if your using the automatic acls, I do believe they are auto allowed. If your using manual acls on unbound you would need to make sure your tunnel network is allowed.
Sometimes clients don't actually want to query the dns you hand out in your vpn config, validate your client can actually query whatever dns your handing it.. that resolves your local resources.
-
@johnpoz said in Client can't see LAN servers after connect:
@utnuc your tunnel network should just be some other network that does not overlap with your existing network(s).. That is just a 2 second fix, change it.
As to your dns problem.. That could be related to your problem with overlapping tunnel network.
You also need to make sure your ACLs on unbound are allowing a query from whatever your tunnel network is.. if your using the automatic acls, I do believe they are auto allowed. If your using manual acls on unbound you would need to make sure your tunnel network is allowed.
Sometimes clients don't actually want to query the dns you hand out in your vpn config, validate your client can actually query whatever dns your handing it.. that resolves your local resources.
Thanks guys, changing the tunnel network fixed both problems! I really appreciate your expertise and time. Great community.
-
@utnuc Oh, one last thing. Everything works great: I can connect to the web configurator with pfsense.sonoclipshare.com, so the DNS resolver works. But when I connect to the VPN I can only connect to pfsense with 10.0.0.2. Stranger is that when I ping pfsense.sonoclipshare.com while connected, I get 10.0.0.2.
-
@utnuc said in Client can't see LAN servers after connect:
web configurator with pfsense.sonoclipshare.com
is that pfsense name? For example it defaults now to home.arpa - if your just pointing some name to it.. you would need to say set an alternate name.. Do you get some sort of error, your saying the page just doesn't load?
here is mine for example.
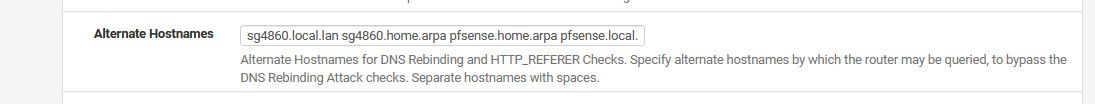
That is what comes to mine when you say the fqdn resolves to the correct IP.
-
@johnpoz Yes, I have pfsense.sonoclipshare.com listed as an alternate host name, and DNS Resolver points that domain to 10.0.0.2. The page never loads, like a network timeout, as if the server isn't even there. I did get it working by actually creating an A-Record with cloudflare to point to 10.0.0.2, but this seems unnecessary since the DNS Resolver should take care of it locally.
-
@utnuc said in Client can't see LAN servers after connect:
creating an A-Record with cloudflare to point to 10.0.0.2,
Well that tells me your client isn't using your local dns then, but you said it resolved to 10.0.0.2 - so maybe your browser wasn't using your dns.. But using doh, the makers of the browsers being smarter than us love to point the browser to their dns vs you know the one we tell the OS to use ;)