Initial Configuration
-
Hello Everyone,
Very new user to pfSense even though I am learning a lot. I am not a network guy and it's driving me nuts. I have 3 nics in my hosts and the 3 Nics are divided up in to 3 VLans. I am wanting the Vlans to have seperate roles. VLan 1 is for VM Communication, Vlan 2 is for management type things, and Vlan3 is strictly for storage and it is a multi gb switch which is at 2.5 gb right now.
So I do have the hosts hooked up to the last switch and they are able to communicate among themselves. The problem is my Workstation is on a diff vlan, If I move my ws to the VLan3 I can't get to the internet. So the other day i had a thought to add the Vlan3 to my pfsense firewall all well and good right.
However I can't ping the hosts from the firewall, nor can i ping the firewall from the hosts. I need help please.
Thank you,
MichaelP.S. I think I explained it correctly .....
-
@Coop59 said in Initial Configuration:
Hello Everyone,
Very new user to pfSense even though I am learning a lot. I am not a network guy and it's driving me nuts. I have 3 nics in my hosts and the 3 Nics are divided up in to 3 VLans. I am wanting the Vlans to have seperate roles. VLan 1 is for VM Communication, Vlan 2 is for management type things, and Vlan3 is strictly for storage and it is a multi gb switch which is at 2.5 gb right now.
So I do have the hosts hooked up to the last switch and they are able to communicate among themselves. The problem is my Workstation is on a diff vlan, If I move my ws to the VLan3 I can't get to the internet. So the other day i had a thought to add the Vlan3 to my pfsense firewall all well and good right.
However I can't ping the hosts from the firewall, nor can i ping the firewall from the hosts. I need help please.
Thank you,
MichaelP.S. I think I explained it correctly .....
Are you saying you have all 3 vlans on each interface or are you saying you have 3 separate networks, each assigned to a physical interface?
If the second, did you actually create vlans or just assign networks to the interface?
There's a difference between adding a vlan and assigning a network.Either way, it's gonna come down to firewall rules.
By default the "LAN" network will have full outbound access, you'll have to give the others outbound access.
Best bet is to post pics of the interface and firewall rules settings.
On the rules, don't just capture the rule section, include the header at the top that shows the interface those rules are on.If you want to try, you can copy the default "any,any" rule from the LAN to the other interfaces. Should give you a start and they would all have access to anywhere. You can then "tune" them as needed.
-
@Coop59 said in Initial Configuration:
I have 3 nics in my hosts and the 3 Nics are divided up in to 3 VLans.
Yup this is unclear. Is that the client host devices or pfSense? All you local hosts are multihomed on 3 VLANs?
-
Hello,
Thank you for responding. No they are individual to each Nic (Vlan1 is on Nic one), (Vlan2 is on Nic2) and (VLan3 is on Nic 3). I hope that explains it better.
And yes each host has 3 nics in them.
Thanks in advance,
Michael -
Sorry if I was unclear, I apologize I usually am more clear. Each vlan is assigned to a Nic if that makes sense.
-
@Coop59 said in Initial Configuration:
Each vlan is assigned to a Nic if that makes sense.
Still not clear - are they actual vlans, ie with an ID setup on a nic - ok.. And this nic has no native network? Need to understand if this is a native vlan or a tagged vlan.. Is pfsense look for tag and sending with a tag or not, etc.
As to each device is multihomed? That is going to be problematic for sure - why??
If your going to put all your device in all your vlans - the whole point of a vlan or segmentation at all is just pretty pointless..
-
@Coop59 said in Initial Configuration:
Each vlan is assigned to a Nic
In pfSense? The unclear part is that you said 'hosts' which made us wonder if that meant the other hosts on the network. That would be unexpected but...

Edit: Oh it actually is that each host has an interface in each vlan?
Assuming it is in pfSense then all traffic between VLAN is routed through pfSense. pfSense will route that by default as long as firewall rules exist to pass it.
Hosts on those VLANs may not respond to connections from other subnets though.
-
They are actual VLans 1 2 and 3, 1 is the actual 1st network. 1.0/24, VLan 2 is .2.0/24, VLan 3 is .3.0/24. They are just on the Proxmox Hosts sorry if that confused you. Each Proxmox Hosy has 3 nics, The Vlans are assigned to the Nics.
I hope that is more clear. I am not sure but i have the 2 of the 3 Vlans tagged (2 and 3) No pfsense is not configure to do so I just created a Vlan and assigned to the Interfaces.
I don't know anything about mutlihomed so the answer would be a no. No I am not wanting to put all my devices on all the VLans I want one workstatuin and all pf the Proxmox hosts there are only 4 of them.\
-
Thank you sir. Like I said I am not a network guy so I have no clue I am learning as I go. I have 2 Vlans created in pfSense one is assigned to my 2nd Nic and Vlan3 is assigned to the 3rd nic. I figured that issue may be I have to create rules so I will try to do that.
Thank you for your response.
Michael -
@Coop59 said in Initial Configuration:
I hope that is more clear. I am not sure but i have the 2 of the 3 Vlans tagged (2 and 3) No pfsense is not configure to do so I just created a Vlan and assigned to the Interfaces.
Please just show us your pfsense setup.. These a vlans..
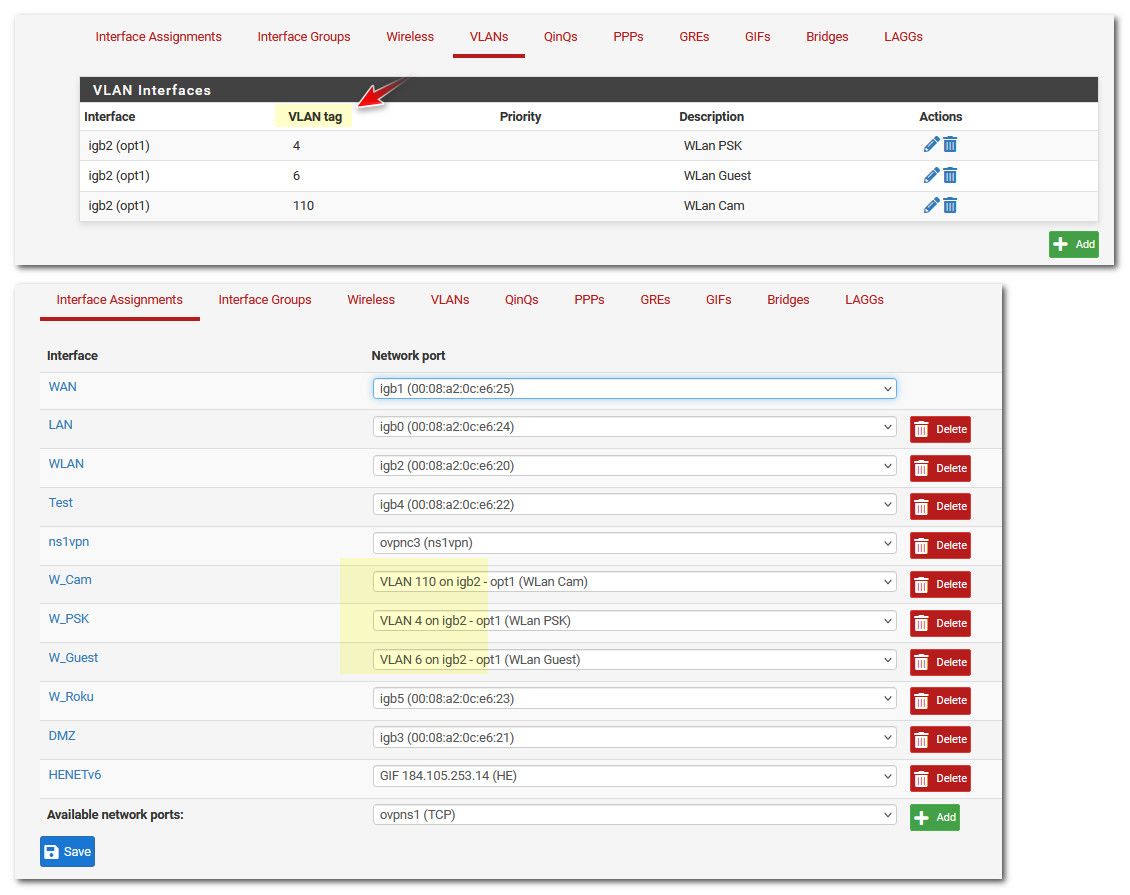
If pfsense just has interfaces - these or not "vlans" on pfsense - you might have them as vlans on your switch.. But they are not "vlans" to pfsense.
see lan wlan dmz w_roku, etc.. those are just native networks on those interfaces in pfsense. No tags..
-
@johnpoz
The nics as you can tell are physical nics and the vlans are assigned to them I know it is wrong.That could be why it didn't work:
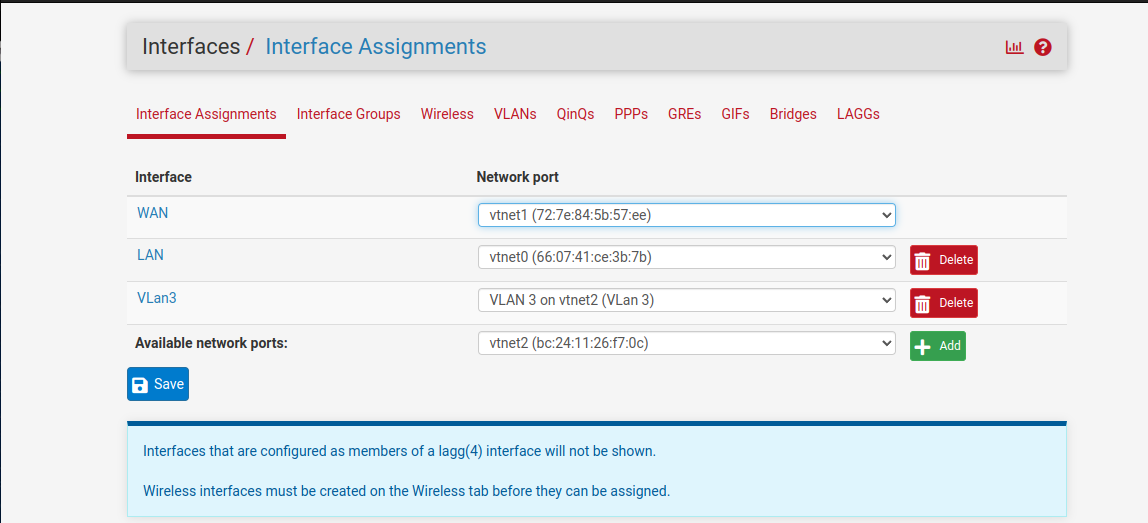
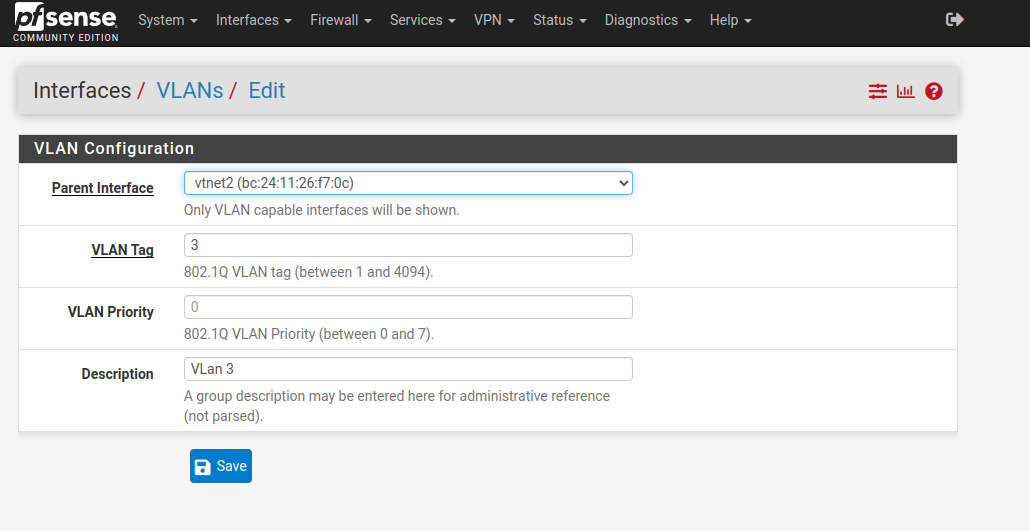
I am pretty sure this is wrong, sorry guys, I am trying to be clear and concise on this.
-
That's not necessarily wrong. It depends what those NICs are connected to and how that is configured (I expect switch ports).
However vtnet is a virtual NIC type. pfSense is running as a VM? How is the hypervisor configured.
-
How do you mean how is it configured?
I have the 3 physical Nics 2 of the 3 Nics are configured as VLan aware.
each one is assigned an IP range.
the 3rd Nic is for storage and is on a multi GB Switch.
-
I mean how the switch ports are configured that it's connected to.
But since it looks like you are also running those connections through a hypervisor it also depends how that is configured.Do you have 3 separate network bridges configured in Proxmox? You may not need VLANs at all here if everything is virtual.
-
@stephenw10
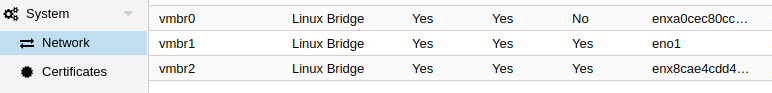
Each host is configured like this (above)The Main Switch:
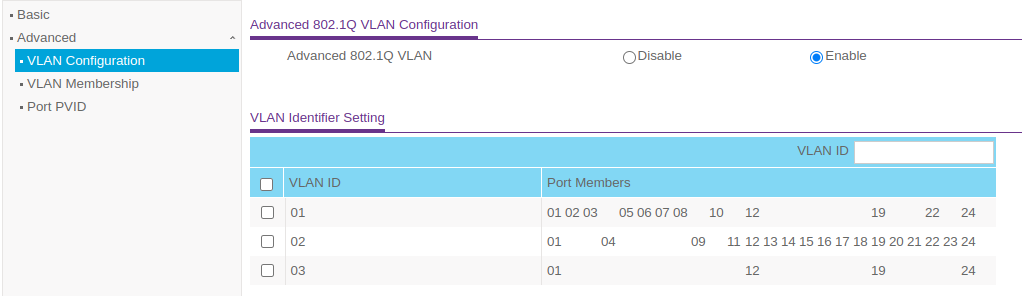
VLan 1
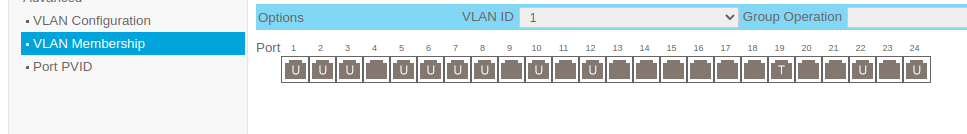
Vlan2
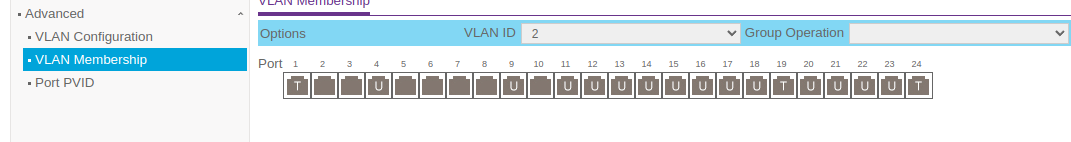
Vlan3
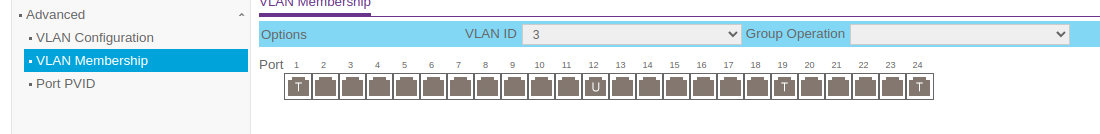
I think that should be enough to give you an idea. Thank you in advance for your time.
Michael -
OK, so which switch ports are the NIXs in Proxmox from each bridge connected to?
Where are the hosts connected that cannot communicate?
-
@stephenw10
Hey Stephen,Thank you for responding sorry I was busy at work all week. Just now seeing this.
Port 12 is the trunk port to the unmanaged switch and the PVID is 3, and the Promox hosts are connected to 11,12,13,15 and the PVIDs are 2.Now with that said the 3rd Nic in the Proxmox hosts are physically plugged in to ports 1,2,3,4 of the unmanaged 2.5 gb switch. They talk to each other fine I can ping host1 from host2, host3 amd so on and vice-versa. However I get a failed response when I ping pfsense at .3.0/24 network (Vlan3). Just an fyi it does ping itself successfully (pfSense I mean). Oh, and I can ping .3.1 (pfSense) from my workstation which is on .2.0/24 network. So I am trying to figure out where the disconnect is. I create a rule in the firewall from the lan to the wan and I also created a rule from the lan to the lan as well and it still is not working.
I hope that explains it better.
Thank you again,
MichaelP.S. @johnpoz @stephenw10 Thank you sincerely for helping I appreciate you guys. Since my last post I have bought a Managed Multi GB router that has 8 access ports and one uplink port. A Cheap one but I am learning when I get good at this I will buy a nice one.
-
@Coop59 said in Initial Configuration:
Port 12 is the trunk port to the unmanaged switch
You mean port 19? That's the only trunk port shown in the screenshots.
All 3 VLANs are untagged on port 12 which is odd. You would normally only ever have one VLAN untagged on a port and that should match the PVID in order to pass traffic both ways.
You have 4 Proxmox hosts? With VMs on each?
I think a diagram may help here.
-
@stephenw10 said in Initial Configuration:
All 3 VLANs are untagged on port 12 which is odd.
Odd is the wrong word, borked is the word your looking for ;)
You can't run multiple untagged vlans on same port and expect something to figure out what traffic is what..
-
I mean... there are some scenarios where that's legitimate but.... probably not this one!
