default deny rule blocking allowed traffic
-
Hello,
I'm having an issue where the default deny rule on my WAN is blocking traffic to port 1196 (for vpn) even though I have an allow rule in place for that port.
Anyone have any idea why that is happening?
I thought I messed up the second VPN server config but I found today the traffic was just being blocked at the FW.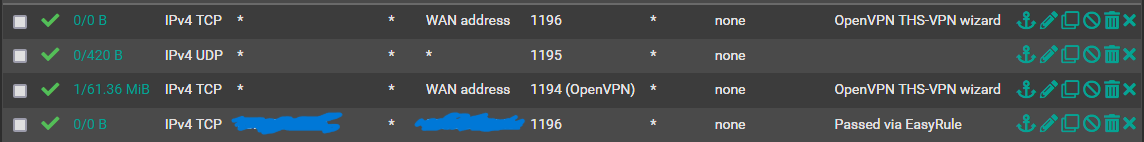
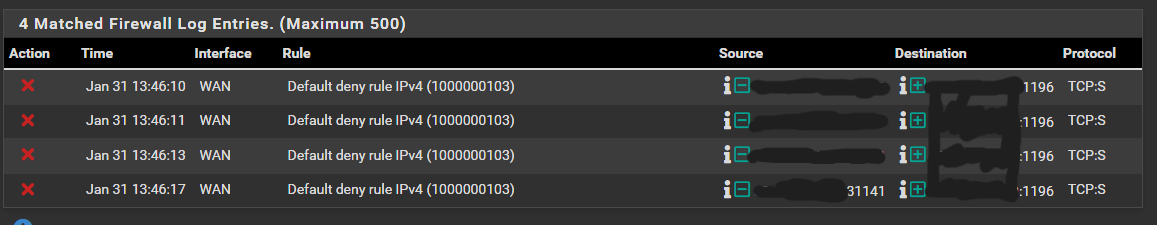
-
If you reset the states does that still occur? The second server is configured for TCP rather than UDP?
-
@Popolou 1195 is for a p2p that is unrelated.
The active primary remote access is 1194.
I did reset the state and I got the same error. -
@ziggy94 Sure, but i am referring to the second OpenVPN server as you wrote, not the second table entry.
-
@Popolou yes the second one is to be used by end users while primary is for IT.
Should the second one be set for UDP over TCP even if it's not for a fail over or something along those lines? -
@ziggy94 UDP instead of TCP* sorry that was poor wording.
-
@ziggy94 Either is fine & UDP is default but TCP is 443 IIRC. Is the second server configured to use the WAN interface?
-
@Popolou sorry, I'm not sure what you mean here.
-
Check your settings for the second OpenVPN server, such that this is what it should be for the default: -
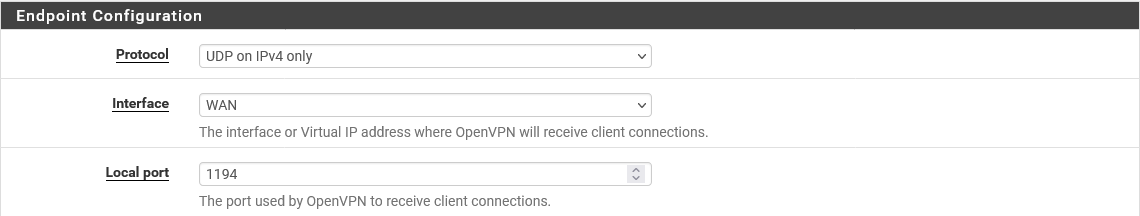
If you want the second server to work against that FW rule, you want to change the protocol to TCP and the port to 1196 on the WAN.
-
@Popolou yes so the default server was that and I did change it to use TCP instead of UDP on port 1194. That is the primary used by IT.
The secondary one I just built yesterday using TCP on port 1196.
both are using the WAN.
so did I make a config error here? -
@Popolou It's been a long day so sorry if I am just being a bit dense here. haha
-
@ziggy94 Cannot see one myself. There is no special routing going on presumably? Very odd especially if one server is running well. Perhaps leave everything as is and do a reboot to see if that cleans things up. Not convenient, i know.