Possible Snort IPS/IDS Fail because of a bad Open ET ruleset issue again
-
Is anyone else seeing this again?
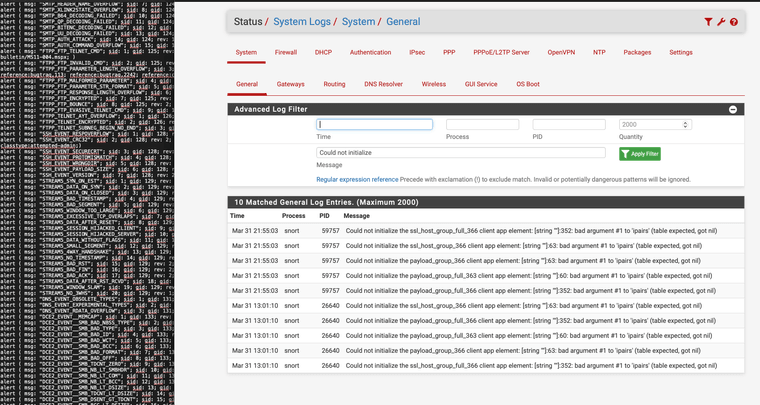
Could not initialize the payload_group_full_366 client app element: [string ""]:352: bad argument #1 to 'ipairs' (table expected, got nil)
Last time this occurred was on Dec 25th
-
@JonathanLee said in Possible Snort IPS/IDS Fail because of a bad Open ET ruleset issue again:
352
Line 352
alert ( msg: "DCE2_EVENT__SMB_CHAIN_OPEN_CLOSE"; sid: 25; gid: 133; rev: 2; metadata: policy max-detect-ips drop, rule-type preproc, service dcerpc ; classtype: bad-unknown; reference:url,msdn.microsoft.com/en-us/library/cc201989.aspx; )
-
-
The "352" is not a line number in the active rules file in this case. Instead, it is alerting you to an error in the Lua scripting for your OpenAppID rules. Something is wrong in OpenAppID, not in the ET Open ruleset.
And remember that the Snort binary will always FAIL TO START when it encounters any type of error parsing the supplied rules. This is just the way it was engineered. Suricata will print errors, skip the offending rule, and keep loading the things that are okay. Snort will NOT do that. When it encounters any kind of error, it exits.