Certificate error
-
@johnpoz said in Certificate error:
complain about long life certs
I use edge and don't have any complains about that 10 years cert, do not see any warnings)))
-
@Antibiotic said in Certificate error:
I use edge and don't have any complains about that 10 years cert, do not see any warnings))
Microsoft can't publish more then one 'bad news' a day.
The update that will make Edge bark over "10 year certs" is probably already queued. -
@Antibiotic all the other browsers have implemented the like 1 year limit.. But seems from a quick google msedge finally got something right ;) If the CA is private, then the limit is not enforced..
oh - another quick google, and wow - seems they all do not enforce limits for private CAs.. Sweet!! When I had moved over to home.arpa and changed my certs I set them to 1 year.. When comes time to renew, back to 10 years for me ;)
See helping people you can learn something new yourself - thanks!!
-
@johnpoz Fine)))
-
 J johnpoz forked this topic on
J johnpoz forked this topic on
-
@Antibiotic I forked that question to a new thread..
https://forum.netgate.com/topic/187866/ns8250-uart-fcr-is-broken-duirng-boot-os
-
@johnpoz Ok. thanks
-
@johnpoz I read about that every now and then too...
BUT: here it is working with a cert lifetime of 10 years with chromium and firefox (both up to date) without any complaints... -
@the-other yeah I saw the headlines about the changes, etc but never really dove into the details.. Just figured it was all certs, and assumed my old certs were just grandfathered in - because I recall reading it was for certs issued after a specific date.
So when I redid mine to move to home.arpa I just made them for 1 year.. What I get for not reading the small print ;)
-
Mmm, I'm pretty sure it does apply to server certs. We had to change the default values for the gui and openvpn wizrad etc. But the CA cert can still be much longer.
-
@johnpoz Hello can me use pfSesne system/patches to apply this patch or its only for pfsesne inside system? I mean over this can implement any pacth to system or only from redmine.pfsense.org?
https://cgit.freebsd.org/src/commit/?id=c4b68e7e53bb352be3fa16995b99764c03097e66 -
Create a CA Root with 10 year lifetime. Then create another CA cert and have it signed by CA Root. And finally create your normal certs and have it signed by the previous CA cert. This is how chain of certificates work.
The reason for the chain is part of how you revoke the certs. So for example if you revoke the server cert you just recreate the new server cert and have it signed by previous CA cert which is also signed by CA Root.
Just import your CA root into your browser and trust it. From then on any certs signed by CA root will automatically be trusted.
CA Root << Primary root cert
CA cert << intermediate cert signed by CA Root
CA cert signed by intermediate cert which you use for servers such as HAproxy and webGUI.You should have three working certs.
Hope this helps.
-
@Antibiotic said in Certificate error:
@johnpoz Hello can me use pfSesne system/patches to apply this patch or its only for pfsesne inside system? I mean over this can implement any pacth to system or only from redmine.pfsense.org?
https://cgit.freebsd.org/src/commit/?id=c4b68e7e53bb352be3fa16995b99764c03097e66The System patches package only looks for pfSense commits if you try to create a patch by commit ID. You can of course import a diff file or copy/paste the diff in directly. However you can't do it with that patch because it's a compiled driver, that's the source code. You can on;y patch run time scripts in pfSense dircetly.
You should start a new thread for anything that isn't certificate related. It's very difficult to follow your questions when you keep changing topics part way through a thread.
Steve
-
@stephenw10 Ok. sorry
-
No worries.

-
@Antibiotic for questions that have nothing to do with the original thread, its best to create a new thread.
-
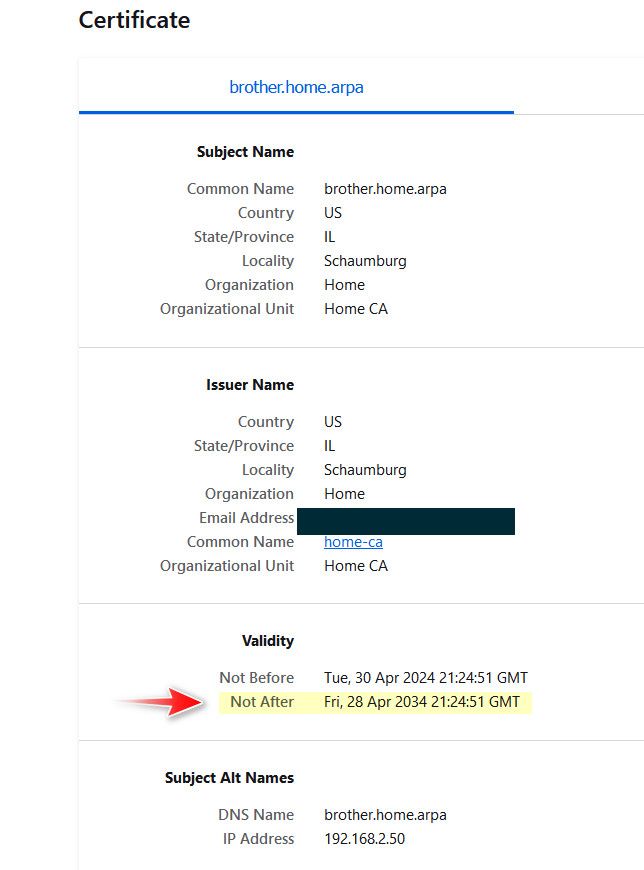
@stephenw10 I just check, created a cert for 10 years.. Put it on my printer and firefox didn't say a word about it being valid for 10 years.. Signed by my CA that it trusts..
Beginning with Chrome 85, TLS server certificates issued on or after 2020-09-01 00:00:00 UTC will be required to have a validity period of 398 days or less. This will only apply to TLS server certificates from CAs that are trusted in a default installation of Google Chrome, commonly known as "publicly trusted CAs", and will not apply to locally-operated CAs that have been manually configured.