Cannot access pfSense Webui from LAN
-
Hi ,
I was experimenting with snort on pfsense and locked myself out of ui.
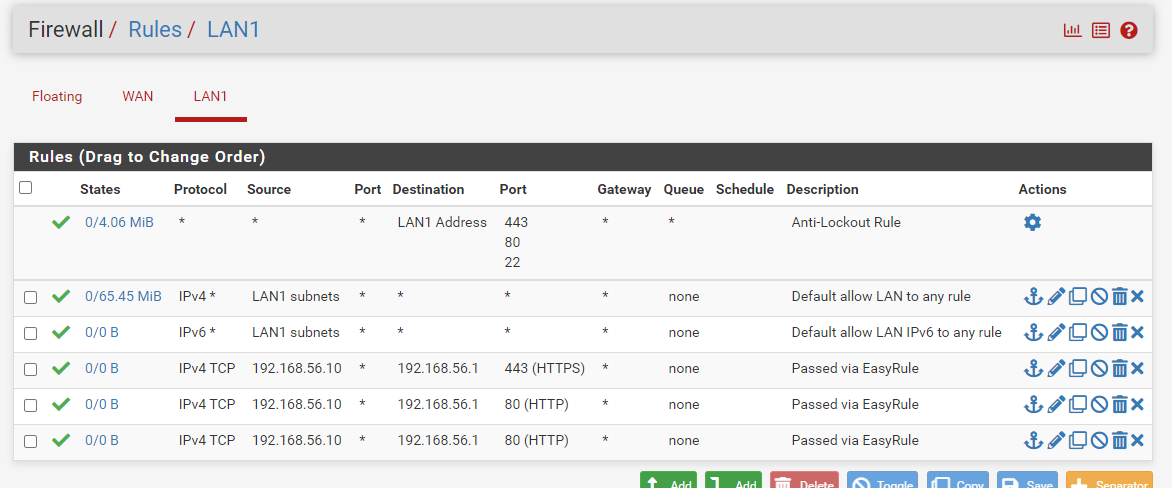
using console i entered cli mode and using pfctl -d i disabled the firewall and managed to access the webui from a clinet on same subnet whose gateway is defined on pfsense.I disabled snort. Still i cannot access webui. the web ui is on port 443 and on lan interface proper rules exits.
The ip from which i am accessing the firewall is 192.168.56.10 and firewall ip is 192.168.56.1
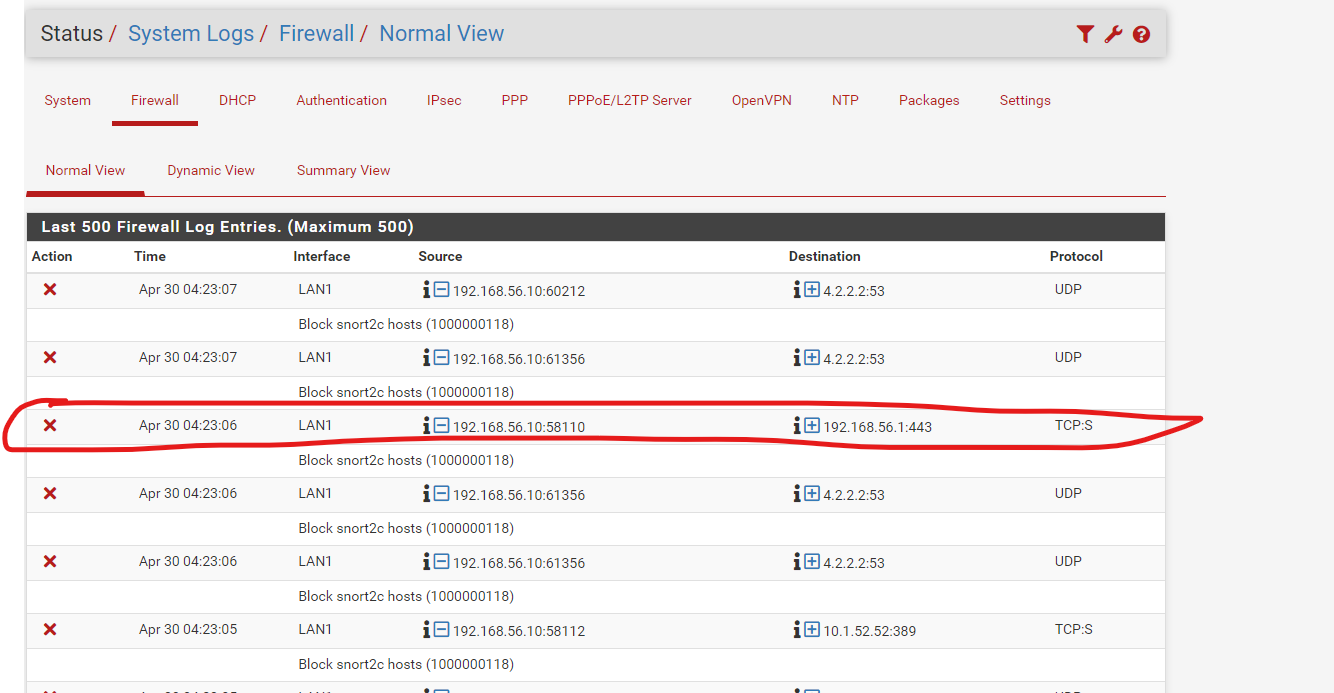
In firewall logs i see below
under /tmp/rules.debug i see below
set hostid 0x7232ea56
set limit table-entries 400000
set optimization normal
set limit states 198000
set limit src-nodes 198000#System aliases
loopback = "{ lo0 }"
WAN = "{ em0 }"
table <WAN__NETWORK> persist { 192.168.100.0/24 }
WAN__NETWORK = "<WAN__NETWORK>"
LAN1 = "{ em1 }"
table <LAN__NETWORK> persist { 192.168.56.0/24 }
LAN__NETWORK = "<LAN__NETWORK>"#SSH Lockout Table
table <sshguard> persist
#Snort tables
table <snort2c>
table <virusprot>
table <bogons> persist file "/etc/bogons"User Aliases
table <fw_host_IP_Alias> { 192.168.56.10 }
fw_host_IP_Alias = "<fw_host_IP_Alias>"Gateways
GWWANGW = " "
GWWAN_DHCP6 = " "set loginterface em1
set skip on pfsync0
set keepcountersscrub from any to <vpn_networks> fragment no reassemble
scrub from <vpn_networks> to any fragment no reassemble
scrub on $WAN inet all fragment reassemble
scrub on $WAN inet6 all fragment reassemble
scrub on $LAN1 inet all fragment reassemble
scrub on $LAN1 inet6 all fragment reassembleno nat proto carp
no rdr proto carp
nat-anchor "natearly/"
nat-anchor "natrules/"Outbound NAT rules (manual)
Outbound NAT rules (automatic)
Subnets to NAT
tonatsubnets = "{ 127.0.0.0/8 ::1/128 192.168.56.0/24 }"
nat on $WAN inet from $tonatsubnets to any port 500 -> 192.168.100.45/32 static-port
nat on $WAN inet6 from $tonatsubnets to any port 500 -> (em0) static-port
nat on $WAN inet from $tonatsubnets to any -> 192.168.100.45/32 port 1024:65535
nat on $WAN inet6 from $tonatsubnets to any -> (em0) port 1024:65535TFTP proxy
rdr-anchor "tftp-proxy/*"
NAT Inbound Redirects
anchor "openvpn/"
anchor "ipsec/"block IPv4 link-local. Per RFC 3927, link local "MUST NOT" be forwarded by a routing device,
and clients "MUST NOT" send such packets to a router. FreeBSD won't route 169.254./16, but
route-to can override that, causing problems such as in redmine #2073
block in log quick from 169.254.0.0/16 to any ridentifier 1000000101 label "Block IPv4 link-local"
block in log quick from any to 169.254.0.0/16 ridentifier 1000000102 label "Block IPv4 link-local"
#---------------------------------------------------------------------------default deny rules
#---------------------------------------------------------------------------
block in log inet all ridentifier 1000000103 label "Default deny rule IPv4"
block out log inet all ridentifier 1000000104 label "Default deny rule IPv4"
block in log inet6 all ridentifier 1000000105 label "Default deny rule IPv6"
block out log inet6 all ridentifier 1000000106 label "Default deny rule IPv6"IPv6 ICMP is not auxiliary, it is required for operation
See man icmp6(4)
1 unreach Destination unreachable
2 toobig Packet too big
128 echoreq Echo service request
129 echorep Echo service reply
133 routersol Router solicitation
134 routeradv Router advertisement
135 neighbrsol Neighbor solicitation
136 neighbradv Neighbor advertisement
pass quick inet6 proto ipv6-icmp from any to any icmp6-type {1,2,135,136} ridentifier 1000000107 keep state
Allow only bare essential icmpv6 packets (NS, NA, and RA, echoreq, echorep)
pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {129,133,134,135,136} ridentifier 1000000108 keep state
pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {129,133,134,135,136} ridentifier 1000000109 keep state
pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000110 keep state
pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000111 keep state
pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000112 keep state
pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000113 keep stateWe use the mighty pf, we cannot be fooled.
block log quick inet proto { tcp, udp } from any port = 0 to any ridentifier 1000000114 label "Block traffic from port 0"
block log quick inet proto { tcp, udp } from any to any port = 0 ridentifier 1000000115 label "Block traffic to port 0"
block log quick inet6 proto { tcp, udp } from any port = 0 to any ridentifier 1000000116 label "Block traffic from port 0"
block log quick inet6 proto { tcp, udp } from any to any port = 0 ridentifier 1000000117 label "Block traffic to port 0"Snort package
block log quick from <snort2c> to any ridentifier 1000000118 label "Block snort2c hosts"
block log quick from any to <snort2c> ridentifier 1000000119 label "Block snort2c hosts"SSH lockout
block in log quick proto tcp from <sshguard> to (self) port 22 ridentifier 1000000301 label "sshguard"
webConfigurator lockout
block in log quick proto tcp from <sshguard> to (self) port 443 ridentifier 1000000351 label "GUI Lockout"
block in log quick from <virusprot> to any ridentifier 1000000400 label "virusprot overload table"allow our DHCPv6 client out to the WAN
pass in quick on $WAN proto udp from fe80::/10 port = 546 to fe80::/10 port = 546 ridentifier 1000000461 label "allow dhcpv6 client in WAN"
pass in quick on $WAN proto udp from any port = 547 to any port = 546 ridentifier 1000000462 label "allow dhcpv6 client in WAN"Add Priority to dhcp6c packets if enabled
pass out quick on $WAN proto udp from any port = 546 to any port = 547 ridentifier 1000000463 label "allow dhcpv6 client out WAN"
antispoof log for $WAN ridentifier 1000001470
antispoof log for $LAN1 ridentifier 1000002520allow access to DHCP server on LAN1
pass in quick on $LAN1 proto udp from any port = 68 to 255.255.255.255 port = 67 ridentifier 1000002541 label "allow access to DHCP server"
pass in quick on $LAN1 proto udp from any port = 68 to 192.168.56.1 port = 67 ridentifier 1000002542 label "allow access to DHCP server"
pass out quick on $LAN1 proto udp from 192.168.56.1 port = 67 to any port = 68 ridentifier 1000002543 label "allow access to DHCP server"loopback
pass in on $loopback inet all ridentifier 1000002561 label "pass IPv4 loopback"
pass out on $loopback inet all ridentifier 1000002562 label "pass IPv4 loopback"
pass in on $loopback inet6 all ridentifier 1000002563 label "pass IPv6 loopback"
pass out on $loopback inet6 all ridentifier 1000002564 label "pass IPv6 loopback"let out anything from the firewall host itself and decrypted IPsec traffic
pass out inet all keep state allow-opts ridentifier 1000002565 label "let out anything IPv4 from firewall host itself"
pass out inet6 all keep state allow-opts ridentifier 1000002566 label "let out anything IPv6 from firewall host itself"pass out route-to ( em0 192.168.100.1 ) from 192.168.100.45 to !192.168.100.0/24 ridentifier 1000002661 keep state allow-opts label "let out anything from firewall host itself"
make sure the user cannot lock himself out of the webConfigurator or SSH
pass in quick on em1 proto tcp from any to (em1) port { 443 80 22 } ridentifier 10001 keep state label "anti-lockout rule"
User-defined rules follow
anchor "userrules/*"
pass in quick on $WAN reply-to ( em0 192.168.100.1 ) inet proto tcp from 192.168.100.24 to 192.168.100.45 port 443 ridentifier 1714416329 flags S/SA keep state label "USER_RULE: Passed via EasyRule" label "id:1714416329"
pass in quick on $LAN1 inet from $LAN__NETWORK to any ridentifier 0100000101 keep state label "USER_RULE: Default allow LAN to any rule" label "id:0100000101"source address is empty. label "USER_RULE: Default allow LAN IPv6 to any rule"
pass in quick on $LAN1 inet proto tcp from 192.168.56.10 to 192.168.56.1 port 443 ridentifier 1714417028 flags S/SA keep state label "USER_RULE: Passed via EasyRule" label "id:1714417028"
pass in quick on $LAN1 inet proto tcp from 192.168.56.10 to 192.168.56.1 port 80 ridentifier 1714418032 flags S/SA keep state label "USER_RULE: Passed via EasyRule" label "id:1714418032"
pass in quick on $LAN1 inet proto tcp from 192.168.56.10 to 192.168.56.1 port 80 ridentifier 1714419658 flags S/SA keep state label "USER_RULE: Passed via EasyRule" label "id:1714419658"VPN Rules
anchor "tftp-proxy/*"
The ip from which i am accessing is in pass list on snort and that list is called properly on the interface. and the alias is created for that ip.
-
@Snailkhan said in Cannot access pfSense Webui from LAN:
In firewall logs i see below
I saw this : the green part :
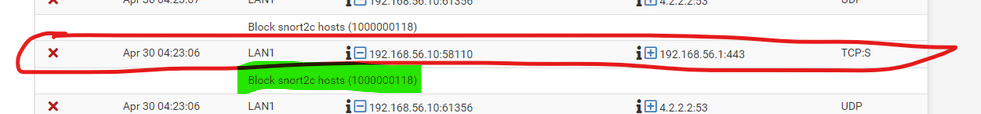
I don't know what 'snort' is, but sure enough :
Disable it or if possible, edit the snort2c hosts alias and remove your IP, and redo the snort settings so it won't block legit local traffic anymore.Btw : the alias snort2c must be used somewhere. You've looked at the Floating firewall page ? ;)
It's also blocking DNS traffic (to 4.2.2.2 port 53).
@Snailkhan said in Cannot access pfSense Webui from LAN:
table <fw_host_IP_Alias> { 192.168.56.10 }
That's explains everything : you've managed to lock yourself out.
Locate this "192.168.56.10" device, switch to a temporary static IP setup, like 192.168.56.11, and with some luck you can edit the snort settings faster as that snort will also lock the door on you again.