Can’t reach remote host in peer-to-peer network
-
It sure must look like I am spamming this forum. It’s just that I have so many questions. Each time I tweak a parameter and it doesn’t solve the issue, it raises new questions. I think, I have the tunnel network and assigned client addresses in the tunnel network figured out. This is from Status → OpenVPN:
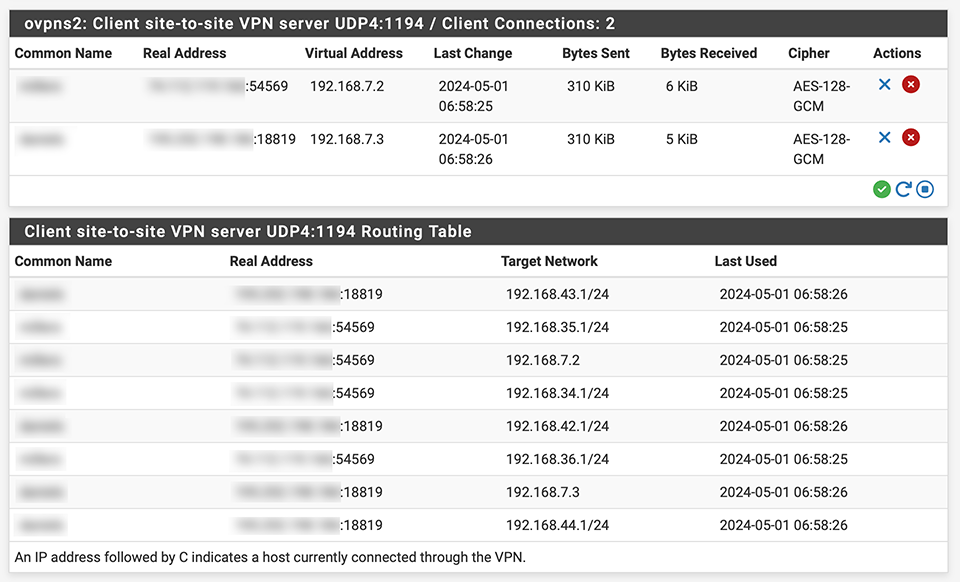
The problem is that even though ostensibly connected, I cannot reach the remote pfSense appliances at either 192.168.7.2 and 192.168.7.3 or their corresponding addresses 192.168.34.1 and 192.168.42.1 in their own local subnets. Connections time out.
-
@DominikHoffmann said in Can’t reach remote host in peer-to-peer network:
I cannot reach the remote pfSense appliances at either 192.168.7.2 and 192.168.7.3
At least these virtual IPs should be reachable if access is allowed on the remote OpenVPN interface.
So first off check the firewall rules on the remote sites.If you still are unable to access the remote virtuell IPs set the servers log level to 3, reconnect and check the OpenVPN log after.
-
@viragomann said in Can’t reach remote host in peer-to-peer network:
At least these virtual IPs should be reachable if access is allowed on the remote OpenVPN interface.
So first off check the firewall rules on the remote sites.Does access have to be allowed explicitly? I do not have an interface defined for the VPN network on the remote appliances. Should I, and then allow access from 192.168.1.1 in the firewall rules?
If you still are unable to access the remote virtuell IPs set the servers log level to 3, reconnect and check the OpenVPN log after.
I have a lot of this in my OpenVPN log:
May 1 09:22:52 openvpn 43411 client1/xxx.xxx.xxx.xxx:18819 UDPv4 WRITE [340] to [AF_INET]xxx.xxx.xxx.xxx:18819: P_DATA_V2 kid=2 DATA len=339 May 1 09:22:52 openvpn 43411 client2/yyy.yyy.yyy.yyy:54569 UDPv4 WRITE [340] to [AF_INET]yyy.yyy.yyy.yyy:54569: P_DATA_V2 kid=2 DATA len=339 May 1 09:22:52 openvpn 43411 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 1 09:22:53 openvpn 43411 MANAGEMENT: CMD 'status 2' May 1 09:22:53 openvpn 43411 MANAGEMENT: CMD 'quit' May 1 09:22:53 openvpn 43411 MANAGEMENT: Client disconnected May 1 09:22:55 openvpn 43411 client1/xxx.xxx.xxx.xxx:18819 UDPv4 WRITE [156] to [AF_INET]xxx.xxx.xxx.xxx:18819: P_DATA_V2 kid=2 DATA len=155 May 1 09:22:55 openvpn 43411 client2/yyy.yyy.yyy.yyy:54569 UDPv4 WRITE [156] to [AF_INET]yyy.yyy.yyy.yyy:54569: P_DATA_V2 kid=2 DATA len=155This is Verosity Level 6. The MANAGEMENT lines occur only rarely.
-
@DominikHoffmann said in Can’t reach remote host in peer-to-peer network:
Does access have to be allowed explicitly? I do not have an interface defined for the VPN network on the remote appliances. Should I, and then allow access from 192.168.1.1 in the firewall rules?
No, this is not necessary for site-to-site access.
You can just add the rules on the OpenVPN tab.This is Verosity Level 6. The MANAGEMENT lines occur only rarely.
To much noise there with level 6 at all. Use level 4. This will also show enough for troubleshooting this , also if the CSO is treated properly, which is not logged on level 3 though.
-
@viragomann: Back to Verbosity 4:
May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 TLS: soft reset sec=3249/3248 bytes=2981463/-1 pkts=8102/0 May 2 07:46:00 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 07:46:00 openvpn 23011 MANAGEMENT: Client disconnected May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY WARNING: depth=0, unable to get certificate CRL: C=US, ST=$state, L=$location, O=$serverorg, CN=$clientname May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=pfSense-CA, C=US, ST=$state, L=$location, O=$serverorg May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY SCRIPT OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location, O=$serverorg May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location, O=$serverorg May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY SCRIPT OK: depth=0, C=US, ST=$state, L=$location, O=$serverorg, CN=$clientname May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 VERIFY OK: depth=0, C=US, ST=$state, L=$location, O=$serverorg, CN=$clientname May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_VER=2.6.8 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_PLAT=freebsd May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_TCPNL=1 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_MTU=1600 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_NCP=2 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 peer info: IV_PROTO=990 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519 May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 07:46:00 openvpn 23011 clientname/xxx.xxx.xxx.xxx:16834 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit keyThese are the most recent lines related to one of the clients. It all looks fine, doesn’t it? Still, I cannot reach the client pfSense appliance at the assigned IP of 192.168.7.2. Overnight the browser tab I had pointed to that loaded the login page, but this morning I could no longer reload it. Is this intermittency an indication of something specific?
Maybe the logs on the client would shed some light, but I am unable to go there physically to check right now.
-
@DominikHoffmann
Maybe a bit too few lines to say anything regarding the problem.
All posted lines were logged within one second. They neither show the assignment of the virtual client IP.Maybe you can post some more log lines.
Yes, there might have been troubles with the forum today's morning. I was unable to log in as well.
-
@viragomann: Thanks very much for working with me on this (again)!
Here are more log lines. There is nothing in here that is in addition to what I had posted before.
May 2 09:31:52 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:31:53 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:31:53 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:31:53 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:32:57 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:32:57 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:32:57 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:32:57 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:34:01 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:34:01 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:34:01 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:34:01 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 TLS: soft reset sec=3249/3248 bytes=2023297/-1 pkts=5446/0 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY WARNING: depth=0, unable to get certificate CRL: C=US, ST=$state, L=$location1, O=$serverorg, CN=$client1 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY SCRIPT OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY SCRIPT OK: depth=0, C=US, ST=$state, L=$location1, O=$serverorg, CN=$client1 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 VERIFY OK: depth=0, C=US, ST=$state, L=$location1, O=$serverorg, CN=$client1 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_VER=2.6.8 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_PLAT=freebsd May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_TCPNL=1 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_MTU=1600 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_NCP=2 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 peer info: IV_PROTO=990 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519 May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 09:34:17 openvpn 23011 $client1/xxx.xxx.xxx.xxx:16834 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 09:35:05 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:35:05 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:35:06 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:35:06 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:36:09 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:36:09 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:36:10 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:36:10 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:37:13 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:37:14 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:37:14 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:37:14 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:38:18 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:38:18 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:38:18 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:38:18 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:39:22 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:39:22 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:39:22 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:39:22 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 TLS: soft reset sec=3535/3535 bytes=2169648/-1 pkts=5803/0 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=$client2, C=US, ST=$state, L=$location2, O=$clientorg2 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY SCRIPT OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$location1, O=$serverorg May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY SCRIPT OK: depth=0, CN=$client2, C=US, ST=$state, L=$location2, O=$clientorg2 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 VERIFY OK: depth=0, CN=$client2, C=US, ST=$state, L=$location2, O=$clientorg2 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_VER=2.6.8 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_PLAT=freebsd May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_TCPNL=1 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_MTU=1600 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_NCP=2 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 peer info: IV_PROTO=990 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519 May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 09:39:25 openvpn 23011 $client2/yyy.yyy.yyy.yyy:18764 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 09:40:26 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:40:26 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:40:26 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:40:26 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:41:30 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:41:30 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:41:30 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:41:30 openvpn 23011 MANAGEMENT: Client disconnected11 repeating instances removed
May 2 09:54:19 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:54:19 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:54:20 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:54:20 openvpn 23011 MANAGEMENT: Client disconnected May 2 09:55:23 openvpn 23011 MANAGEMENT: Client connected from /var/etc/openvpn/server2/sock May 2 09:55:23 openvpn 23011 MANAGEMENT: CMD 'status 2' May 2 09:55:24 openvpn 23011 MANAGEMENT: CMD 'quit' May 2 09:55:24 openvpn 23011 MANAGEMENT: Client disconnectedWhat would have been the wording of an assignment of the clients’ virtual IP addresses? It would be helpful to search the log for a corresponding keyword.
-
@viragomann said in Can’t reach remote host in peer-to-peer network:
They neither show the assignment of the virtual client IP.
Would it look like this?
openvpn[32194]: UDPv4 link remote: 1.2.3.4:1194 openvpn[32194]: Peer Connection Initiated with 192.168.110.2:1194 openvpn[32194]: Initialization Sequence CompletedSource: Check the OpenVPN logs from the Netgate Docs.
Is that example from a client or a server log?
-
@viragomann: I now also have an excerpt from the client’s log. It shows the last entry, before I upped the verbosity level to 4, and then everything subsequent. The GUI indicated that the connection was established:
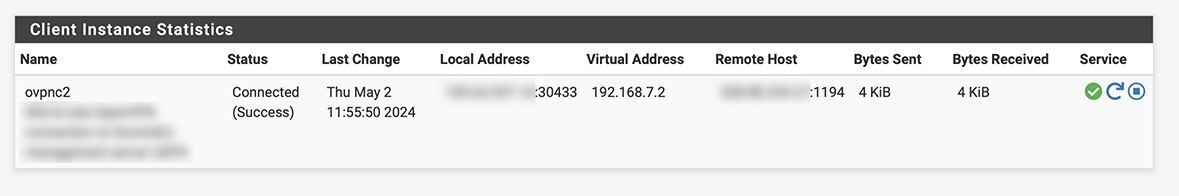
Here is the log, which shows “
ERROR: FreeBSD route add command failed: external program exited with error status: 1.” Would that be an indication of what to dig into?May 2 00:32:53 openvpn 88086 Initialization Sequence Completed May 2 11:55:43 openvpn 88086 event_wait : Interrupted system call (fd=-1,code=4) May 2 11:55:43 openvpn 88086 SIGTERM received, sending exit notification to peer May 2 11:55:44 openvpn 88086 /sbin/ifconfig ovpnc2 192.168.7.2 -alias May 2 11:55:44 openvpn 88086 /sbin/ifconfig ovpnc2 destroy May 2 11:55:44 openvpn 88086 /usr/local/sbin/ovpn-linkdown ovpnc2 1500 0 192.168.7.2 255.255.255.0 init May 2 11:55:44 openvpn 74717 Flushing states on OpenVPN interface ovpnc2 (Link Down) May 2 11:55:44 openvpn 88086 SIGTERM[soft,exit-with-notification] received, process exiting May 2 11:55:45 openvpn 75682 Note: ignoring --dev-node as it has no effect when using data channel offload May 2 11:55:45 openvpn 75682 Current Parameter Settings: May 2 11:55:45 openvpn 75682 config = '/var/etc/openvpn/client2/config.ovpn' May 2 11:55:45 openvpn 75682 mode = 0 May 2 11:55:45 openvpn 75682 show_ciphers = DISABLED May 2 11:55:45 openvpn 75682 show_digests = DISABLED May 2 11:55:45 openvpn 75682 show_engines = DISABLED May 2 11:55:45 openvpn 75682 genkey = DISABLED May 2 11:55:45 openvpn 75682 genkey_filename = '[UNDEF]' May 2 11:55:45 openvpn 75682 key_pass_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 show_tls_ciphers = DISABLED May 2 11:55:45 openvpn 75682 connect_retry_max = 0 May 2 11:55:45 openvpn 75682 Connection profiles [0]: May 2 11:55:45 openvpn 75682 proto = udp4 May 2 11:55:45 openvpn 75682 local = '100.64.207.16' May 2 11:55:45 openvpn 75682 local_port = '0' May 2 11:55:45 openvpn 75682 remote = 'hoffmann.homeunix.net' May 2 11:55:45 openvpn 75682 remote_port = '1194' May 2 11:55:45 openvpn 75682 remote_float = DISABLED May 2 11:55:45 openvpn 75682 bind_defined = DISABLED May 2 11:55:45 openvpn 75682 bind_local = ENABLED May 2 11:55:45 openvpn 75682 bind_ipv6_only = DISABLED May 2 11:55:45 openvpn 75682 connect_retry_seconds = 1 May 2 11:55:45 openvpn 75682 connect_timeout = 120 May 2 11:55:45 openvpn 75682 socks_proxy_server = '[UNDEF]' May 2 11:55:45 openvpn 75682 socks_proxy_port = '[UNDEF]' May 2 11:55:45 openvpn 75682 tun_mtu = 1500 May 2 11:55:45 openvpn 75682 tun_mtu_defined = ENABLED May 2 11:55:45 openvpn 75682 link_mtu = 1500 May 2 11:55:45 openvpn 75682 link_mtu_defined = DISABLED May 2 11:55:45 openvpn 75682 tun_mtu_extra = 0 May 2 11:55:45 openvpn 75682 tun_mtu_extra_defined = DISABLED May 2 11:55:45 openvpn 75682 tls_mtu = 1250 May 2 11:55:45 openvpn 75682 mtu_discover_type = -1 May 2 11:55:45 openvpn 75682 fragment = 0 May 2 11:55:45 openvpn 75682 mssfix = 1492 May 2 11:55:45 openvpn 75682 mssfix_encap = ENABLED May 2 11:55:45 openvpn 75682 mssfix_fixed = DISABLED May 2 11:55:45 openvpn 75682 explicit_exit_notification = 1 May 2 11:55:45 openvpn 75682 tls_auth_file = '[INLINE]' May 2 11:55:45 openvpn 75682 key_direction = 1 May 2 11:55:45 openvpn 75682 tls_crypt_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 tls_crypt_v2_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 Connection profiles END May 2 11:55:45 openvpn 75682 remote_random = DISABLED May 2 11:55:45 openvpn 75682 ipchange = '[UNDEF]' May 2 11:55:45 openvpn 75682 dev = 'ovpnc2' May 2 11:55:45 openvpn 75682 dev_type = 'tun' May 2 11:55:45 openvpn 75682 dev_node = '[UNDEF]' May 2 11:55:45 openvpn 75682 tuntap_options.disable_dco = DISABLED May 2 11:55:45 openvpn 75682 lladdr = '[UNDEF]' May 2 11:55:45 openvpn 75682 topology = 3 May 2 11:55:45 openvpn 75682 ifconfig_local = '192.168.7.2' May 2 11:55:45 openvpn 75682 ifconfig_remote_netmask = '255.255.255.0' May 2 11:55:45 openvpn 75682 ifconfig_noexec = DISABLED May 2 11:55:45 openvpn 75682 ifconfig_nowarn = DISABLED May 2 11:55:45 openvpn 75682 ifconfig_ipv6_local = '[UNDEF]' May 2 11:55:45 openvpn 75682 ifconfig_ipv6_netbits = 0 May 2 11:55:45 openvpn 75682 ifconfig_ipv6_remote = '[UNDEF]' May 2 11:55:45 openvpn 75682 shaper = 0 May 2 11:55:45 openvpn 75682 mtu_test = 0 May 2 11:55:45 openvpn 75682 mlock = DISABLED May 2 11:55:45 openvpn 75682 keepalive_ping = 10 May 2 11:55:45 openvpn 75682 keepalive_timeout = 60 May 2 11:55:45 openvpn 75682 inactivity_timeout = 0 May 2 11:55:45 openvpn 75682 session_timeout = 0 May 2 11:55:45 openvpn 75682 inactivity_minimum_bytes = 0 May 2 11:55:45 openvpn 75682 ping_send_timeout = 10 May 2 11:55:45 openvpn 75682 ping_rec_timeout = 60 May 2 11:55:45 openvpn 75682 ping_rec_timeout_action = 2 May 2 11:55:45 openvpn 75682 ping_timer_remote = ENABLED May 2 11:55:45 openvpn 75682 remap_sigusr1 = 0 May 2 11:55:45 openvpn 75682 persist_tun = ENABLED May 2 11:55:45 openvpn 75682 persist_local_ip = DISABLED May 2 11:55:45 openvpn 75682 persist_remote_ip = DISABLED May 2 11:55:45 openvpn 75682 persist_key = ENABLED May 2 11:55:45 openvpn 75682 passtos = DISABLED May 2 11:55:45 openvpn 75682 resolve_retry_seconds = 1000000000 May 2 11:55:45 openvpn 75682 resolve_in_advance = DISABLED May 2 11:55:45 openvpn 75682 username = '[UNDEF]' May 2 11:55:45 openvpn 75682 groupname = '[UNDEF]' May 2 11:55:45 openvpn 75682 chroot_dir = '[UNDEF]' May 2 11:55:45 openvpn 75682 cd_dir = '[UNDEF]' May 2 11:55:45 openvpn 75682 writepid = '/var/run/openvpn_client2.pid' May 2 11:55:45 openvpn 75682 up_script = '/usr/local/sbin/ovpn-linkup' May 2 11:55:45 openvpn 75682 down_script = '/usr/local/sbin/ovpn-linkdown' May 2 11:55:45 openvpn 75682 down_pre = DISABLED May 2 11:55:45 openvpn 75682 up_restart = DISABLED May 2 11:55:45 openvpn 75682 up_delay = DISABLED May 2 11:55:45 openvpn 75682 log = DISABLED May 2 11:55:45 openvpn 75682 nice = 0 May 2 11:55:45 openvpn 75682 mute = 0 May 2 11:55:45 openvpn 75682 status_file_version = 1 May 2 11:55:45 openvpn 75682 occ = ENABLED May 2 11:55:45 openvpn 75682 sockflags = 0 May 2 11:55:45 openvpn 75682 comp.alg = 0 May 2 11:55:45 openvpn 75682 route_default_gateway = '[UNDEF]' May 2 11:55:45 openvpn 75682 route_delay = 0 May 2 11:55:45 openvpn 75682 route_nopull = DISABLED May 2 11:55:45 openvpn 75682 allow_pull_fqdn = DISABLED May 2 11:55:45 openvpn 75682 management_port = 'unix' May 2 11:55:45 openvpn 75682 management_log_history_cache = 250 May 2 11:55:45 openvpn 75682 management_client_group = '[UNDEF]' May 2 11:55:45 openvpn 75682 shared_secret_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 ncp_ciphers = 'AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305' May 2 11:55:45 openvpn 75682 replay = ENABLED May 2 11:55:45 openvpn 75682 replay_time = 15 May 2 11:55:45 openvpn 75682 test_crypto = DISABLED May 2 11:55:45 openvpn 75682 ca_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 cert_file = '/var/etc/openvpn/client2/cert' May 2 11:55:45 openvpn 75682 pkcs12_file = '[UNDEF]' May 2 11:55:45 openvpn 75682 cipher_list_tls13 = '[UNDEF]' May 2 11:55:45 openvpn 75682 tls_export_cert = '[UNDEF]' May 2 11:55:45 openvpn 75682 verify_x509_name = '[UNDEF]' May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 65535 May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 0 May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 0 May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 0 May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 0 May 2 11:55:45 openvpn 75682 remote_cert_ku[i] = 0 May 2 11:55:45 openvpn 75682 remote_cert_eku = 'TLS Web Server Authentication' May 2 11:55:45 openvpn 75682 renegotiate_bytes = -1 May 2 11:55:45 openvpn 75682 handshake_window = 60 May 2 11:55:45 openvpn 75682 push_peer_info = DISABLED May 2 11:55:45 openvpn 75682 tls_crypt_v2_metadata = '[UNDEF]' May 2 11:55:45 openvpn 75682 pkcs11_protected_authentication = DISABLED May 2 11:55:45 openvpn 75682 pkcs11_private_mode = 00000000 ay 2 11:55:45 openvpn 75682 pkcs11_cert_private = DISABLED May 2 11:55:45 openvpn 75682 pkcs11_pin_cache_period = -1 May 2 11:55:45 openvpn 75682 server_network = 0.0.0.0 May 2 11:55:45 openvpn 75682 server_netmask = 0.0.0.0 May 2 11:55:45 openvpn 75682 server_network_ipv6 = :: May 2 11:55:45 openvpn 75682 server_bridge_netmask = 0.0.0.0 May 2 11:55:45 openvpn 75682 server_bridge_pool_start = 0.0.0.0 May 2 11:55:45 openvpn 75682 ifconfig_pool_defined = DISABLED May 2 11:55:45 openvpn 75682 ifconfig_pool_netmask = 0.0.0.0 May 2 11:55:45 openvpn 75682 ifconfig_pool_persist_refresh_freq = 600 May 2 11:55:45 openvpn 75682 ifconfig_ipv6_pool_netbits = 0 May 2 11:55:45 openvpn 75682 real_hash_size = 256 May 2 11:55:45 openvpn 75682 client_connect_script = '[UNDEF]' May 2 11:55:45 openvpn 75682 client_disconnect_script = '[UNDEF]' May 2 11:55:45 openvpn 75682 ccd_exclusive = DISABLED May 2 11:55:45 openvpn 75682 push_ifconfig_local = 0.0.0.0 May 2 11:55:45 openvpn 75682 push_ifconfig_ipv6_defined = DISABLED May 2 11:55:45 openvpn 75682 enable_c2c = DISABLED May 2 11:55:45 openvpn 75682 cf_per = 0 May 2 11:55:45 openvpn 75682 cf_initial_per = 10 May 2 11:55:45 openvpn 75682 auth_user_pass_verify_script = '[UNDEF]' May 2 11:55:45 openvpn 75682 auth_token_lifetime = 0 May 2 11:55:45 openvpn 75682 port_share_host = '[UNDEF]' May 2 11:55:45 openvpn 75682 vlan_accept = all May 2 11:55:45 openvpn 75682 client = DISABLED May 2 11:55:45 openvpn 75682 OpenVPN 2.6.8 aarch64-portbld-freebsd15.0 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] [DCO] May 2 11:55:45 openvpn 75682 library versions: OpenSSL 3.0.13 24 Oct 2023, LZO 2.10 May 2 11:55:45 openvpn 75682 DCO version: FreeBSD 15.0-CURRENT #0 plus-RELENG_24_03-n256311-e71f834dd81: Fri Apr 19 00:30:27 UTC 2024 root@freebsd:/var/jenkins/workspace/pfSense-Plus-snapshots-24_03-main/obj/aarch64/Jqi6F4gT/var/jenkins/workspace/pfSense-Plus-snapshots-24_03-main/sources/Free May 2 11:55:45 openvpn 75750 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2/sock May 2 11:55:45 openvpn 75750 WARNING: using --pull/--client and --ifconfig together is probably not what you want May 2 11:55:45 openvpn 75750 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts May 2 11:55:45 openvpn 75750 WARNING: experimental option --capath /var/etc/openvpn/client2/ca May 2 11:55:45 openvpn 75750 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 11:55:45 openvpn 75750 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 11:55:45 openvpn 75750 Control Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1250 tun_max_mtu:0 headroom:126 payload:1600 tailroom:126 ET:0 ] May 2 11:55:50 openvpn 75750 Data Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ] May 2 11:55:50 openvpn 75750 TCP/UDP: Preserving recently used remote address: [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 11:55:50 openvpn 75750 Socket Buffers: R=[42080->42080] S=[57344->57344] May 2 11:55:50 openvpn 75750 UDPv4 link local (bound): [AF_INET]100.64.207.16:0 May 2 11:55:50 openvpn 75750 UDPv4 link remote: [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 11:55:50 openvpn 75750 TLS: Initial packet from [AF_INET]zzz.zzz.zzz.zzz:1194, sid=fa988316 9bf7128a May 2 11:55:50 openvpn 75750 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=server, C=US, ST=$state, L=$locality, O=$serverorg May 2 11:55:50 openvpn 75750 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=pfSense-CA, C=US, ST=$state, L=$locality, O=$serverorg May 2 11:55:50 openvpn 75750 VERIFY OK: depth=1, CN=pfSense-CA, C=US, ST=$state, L=$locality, O=$serverorg May 2 11:55:50 openvpn 75750 VERIFY KU OK May 2 11:55:50 openvpn 75750 Validating certificate extended key usage May 2 11:55:50 openvpn 75750 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication May 2 11:55:50 openvpn 75750 VERIFY EKU OK May 2 11:55:50 openvpn 75750 VERIFY OK: depth=0, CN=server, C=US, ST=$state, L=$locality, O=$serverorg May 2 11:55:50 openvpn 75750 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519 May 2 11:55:50 openvpn 75750 [server] Peer Connection Initiated with [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 11:55:50 openvpn 75750 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1 May 2 11:55:50 openvpn 75750 TLS: tls_multi_process: initial untrusted session promoted to trusted May 2 11:55:50 openvpn 75750 PUSH: Received control message: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,route 192.168.8.0 255.255.255.0,route-gateway 192.168.7.1,topology subnet,ping 10,ping-restart 60,route 192.168.8.0 255.255.255.0,ifconfig 192.168.7.2 255.255.255.0,peer-id 0,cipher AES-128-GCM,protocol-flags cc-exit tls-ekm dyn-tls-crypt,tun-mtu 1500' May 2 11:55:50 openvpn 75750 OPTIONS IMPORT: --ifconfig/up options modified May 2 11:55:50 openvpn 75750 OPTIONS IMPORT: route options modified May 2 11:55:50 openvpn 75750 OPTIONS IMPORT: route-related options modified May 2 11:55:50 openvpn 75750 OPTIONS IMPORT: tun-mtu set to 1500 May 2 11:55:50 openvpn 75750 ROUTE_GATEWAY 100.64.192.1/255.255.240.0 IFACE=mvneta0.4090 HWADDR=f0:ad:4e:34:5f:bf May 2 11:55:50 openvpn 75750 DCO device ovpnc2 opened May 2 11:55:50 openvpn 75750 do_ifconfig, ipv4=1, ipv6=0 May 2 11:55:50 openvpn 75750 /sbin/ifconfig ovpnc2 192.168.7.2/24 mtu 1500 up May 2 11:55:50 openvpn 75750 /usr/local/sbin/ovpn-linkup ovpnc2 1500 0 192.168.7.2 255.255.255.0 init May 2 11:55:50 openvpn 75750 /sbin/route add -net 192.168.8.0 192.168.7.1 255.255.255.0 May 2 11:55:50 openvpn 75750 /sbin/route add -net 192.168.1.0 192.168.7.1 255.255.255.0 May 2 11:55:50 openvpn 75750 /sbin/route add -net 192.168.8.0 192.168.7.1 255.255.255.0 May 2 11:55:50 openvpn 75750 ERROR: FreeBSD route add command failed: external program exited with error status: 1 May 2 11:55:50 openvpn 75750 /sbin/route add -net 192.168.8.0 192.168.7.1 255.255.255.0 May 2 11:55:50 openvpn 75750 ERROR: FreeBSD route add command failed: external program exited with error status: 1 May 2 11:55:50 openvpn 75750 Data Channel MTU parms [ mss_fix:1400 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ] May 2 11:55:50 openvpn 75750 Outgoing dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key May 2 11:55:50 openvpn 75750 Outgoing dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 11:55:50 openvpn 75750 Incoming dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key May 2 11:55:50 openvpn 75750 Incoming dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 11:55:50 openvpn 75750 Initialization Sequence Completed May 2 11:55:50 openvpn 75750 Data Channel: cipher 'AES-128-GCM', peer-id: 0 May 2 11:55:50 openvpn 75750 Timers: ping 10, ping-restart 60 May 2 11:55:50 openvpn 75750 Protocol options: explicit-exit-notify 1, protocol-flags cc-exit tls-ekm dyn-tls-crypt -
@DominikHoffmann said in Can’t reach remote host in peer-to-peer network:
Would it look like this?
openvpn[32194]: UDPv4 link remote: 1.2.3.4:1194
openvpn[32194]: Peer Connection Initiated with 192.168.110.2:1194
openvpn[32194]: Initialization Sequence CompletedI'd rather expect this to see from the client instance.
My server logs this for example:
May 2 20:04:47 openvpn 27059 MULTI: primary virtual IP for <commonname>/<clientIP>:63580: 10.0.41.106 May 2 20:04:47 openvpn 27059 MULTI: Learn: 10.0.41.106 -> <commonname>/<clientIP>:63580 May 2 20:04:47 openvpn 27059 <commonname>/<clientIP>:63580 OPTIONS IMPORT: reading client specific options from: /var/etc/openvpn/server3/csc/<commonname>Lines 1 and 2 indicate the successful client connection and IP assignment.
The third line notes that the CSO was applied properly. So this entry is very important, when using CSO for the concerned client.
This is only logged with verbosity level 4 and higher.
If you don't see this line the CSO is not applied and you have to research for the reason.Also if you have stated clients remote networks in the CSO you should see a row, which tells you, that the routes for these subnets pointing to the clients virtual IP were added to the server. This is essential for site-to-site communication.
Here is the log, which shows “ERROR: FreeBSD route add command failed: external program exited with error status: 1.” Would that be an indication of what to dig into?
This is an issue, that should be fixed for sure. However, I don't believe that this is the reason for your basic problem.
As the "push options" line shows, a route for 192.168.8.0/24 is pushed twice:
May 2 11:55:50 openvpn 75750 PUSH: Received control message: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,route 192.168.8.0 255.255.255.0,route-gateway 192.168.7.1,topology subnet,ping 10,ping-restart 60,route 192.168.8.0 255.255.255.0,ifconfig 192.168.7.2 255.255.255.0,peer-id 0,cipher AES-128-GCM,protocol-flags cc-exit tls-ekm dyn-tls-crypt,tun-mtu 1500'And I guess, the client just complains here, that he cannot add it a second time.
So check the server settings for the reason for this. Note that you don't need state "local networks" in the CSO if you have the same settings already in the server configuration.
-
@viragomann: Just a tidbit… I can currently bring up
https://192.168.7.2/andhttps://192.168.7.3/in my browser. It is completely intermittent.Let’s see, whether I find some of what you mentioned in your most recent response in my OpenVPN log.
This is what I found (or didn’t): no mention of the assigned IP address 192.168.7.2 or 192.168.7.3; no occurrence of “
MULTI.” -
More strangeness after adding a third client:
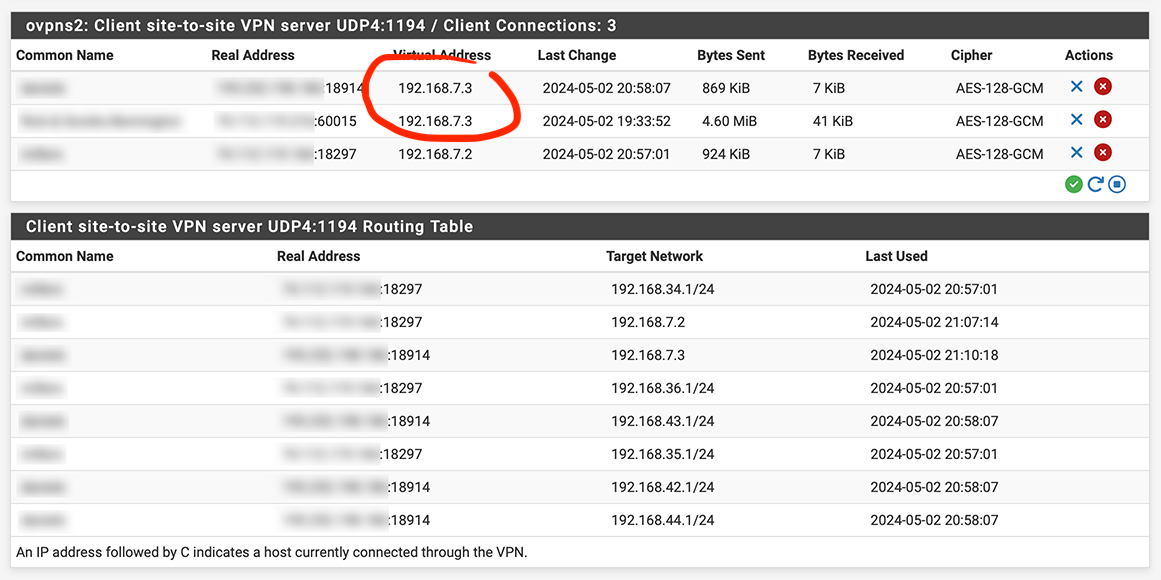
Why do both of them have the same IP address in the tunnel?
-
Now I have logs from what looks like a successfully established peer-to-peer connection.
On the client side:
May 2 20:57:52 openvpn 94573 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) May 2 20:57:52 openvpn 94573 TLS Error: TLS handshake failed May 2 20:58:07 openvpn 94573 Failed to delete peer: No such file or directory (errno=2) May 2 20:58:07 openvpn 94573 Initialization Sequence Completed May 2 21:56:52 openvpn 94573 Failed to delete key: No such file or directory (errno=2) May 2 21:56:52 openvpn 94573 Failed to delete peer: No such file or directory (errno=2) May 2 21:56:52 openvpn 94573 SIGUSR1[soft,dco update keys error] received, process restarting May 2 21:56:53 openvpn 94573 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts May 2 21:56:53 openvpn 94573 TCP/UDP: Preserving recently used remote address: [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 21:56:53 openvpn 94573 UDPv4 link local (bound): [AF_INET]xxx.xxx.xxx.xxx:0 May 2 21:56:53 openvpn 94573 UDPv4 link remote: [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 21:56:53 openvpn 94573 [server] Peer Connection Initiated with [AF_INET]zzz.zzz.zzz.zzz:1194 May 2 21:56:53 openvpn 94573 Preserving previous TUN/TAP instance: ovpnc2 May 2 21:56:53 openvpn 94573 Initialization Sequence CompletedOn the server side:
May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Re-using SSL/TLS context May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Control Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1250 tun_max_mtu:0 headroom:126 payload:1600 tailroom:126 ET:0 ] May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Data Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ] May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=<client1>, C=US, ST=<clientstate>, L=<clientlocality>, O=<clientorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=pfSense-CA, C=US, ST=<serverstate>, L=<serverlocality>, O=<serverorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY SCRIPT OK: depth=1, CN=pfSense-CA, C=US, ST=<serverstate>, L=<serverlocality>, O=<serverorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY OK: depth=1, CN=pfSense-CA, C=US, ST=<serverstate>, L=<serverlocality>, O=<serverorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY SCRIPT OK: depth=0, CN=<client1>, C=US, ST=<clientstate>, L=<clientlocality>, O=<clientorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 VERIFY OK: depth=0, CN=<client1>, C=US, ST=<clientstate>, L=<clientlocality>, O=<clientorg> May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_VER=2.6.8 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_PLAT=freebsd May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_TCPNL=1 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_MTU=1600 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_NCP=2 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 peer info: IV_PROTO=990 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 TLS: tls_multi_process: initial untrusted session promoted to trusted May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519 May 2 21:56:53 openvpn 43949 xxx.xxx.xxx.xxx:18500 [<clieentcommonname>] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI_sva: pool returned IPv4=192.168.7.2, IPv6=(Not enabled) May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 OPTIONS IMPORT: reading client specific options from: /var/etc/openvpn/server2/csc/<clieentcommonname> May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.7.3 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: primary virtual IP for <clieentcommonname>/xxx.xxx.xxx.xxx:18500: 192.168.7.3 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.44.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.44.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.43.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.43.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.42.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.42.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500 May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Data Channel MTU parms [ mss_fix:1400 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ] May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Outgoing dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Outgoing dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Incoming dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Incoming dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 SENT CONTROL [<clieentcommonname>]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,route 192.168.8.0 255.255.255.0,route-gateway 192.168.7.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.7.3 255.255.255.0,peer-id 0,cipher AES-128-GCM,protocol-flags cc-exit tls-ekm dyn-tls-crypt,tun-mtu 1500' (status=1) May 2 21:56:54 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Data Channel: cipher 'AES-128-GCM', peer-id: 0 May 2 21:56:54 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Timers: ping 10, ping-restart 120 May 2 21:56:54 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 Protocol options: protocol-flags cc-exit tls-ekm dyn-tls-cryptSo, it can work. Why does it not each and every time?
-
@DominikHoffmann said in Can’t reach remote host in peer-to-peer network:
Why do both of them have the same IP address in the tunnel?
Do the clients use the same SSL certificate by any chance?
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.44.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.44.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.43.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.43.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: internal route 192.168.42.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500
May 2 21:56:53 openvpn 43949 <clieentcommonname>/xxx.xxx.xxx.xxx:18500 MULTI: Learn: 192.168.42.1/24 -> <clieentcommonname>/xxx.xxx.xxx.xxx:18500Seems you didn't state real network addresses in the CSO. Instead of 192.168.44.1/24 use 192.168.44.0/24 and so on.
-
@viragomann said in Can’t reach remote host in peer-to-peer network:
Do the clients use the same SSL certificate by any chance?
I was asking myself that, too. I updated the certificate of one (one that happened to be connected at the time), which kicked it off the connection. It has not come back since.
Still, they all have different CNs (common names), so that means that their certificates are unique, doesn’t it?
-
@DominikHoffmann said in Can’t reach remote host in peer-to-peer network:
I updated the certificate of one (one that happened to be connected at the time), which kicked it off the connection.
The client certificate?
If so, I don't expect that it behaves like that.The client certificate is verified by the server only once, when the client starts the connection.
Updating it either on pfSense (renew) or on the client should not force the client to reconnect.Still, they all have different CNs (common names), so that means that their certificates are unique, doesn’t it?
Yes. So I'd expect that each get a unique virtual IP from the server, as long as you didn't set the IPs in the CSO.
-
D DominikHoffmann referenced this topic on
-
Please see https://forum.netgate.com/post/1181349 and https://forum.netgate.com/post/1181336 for the final puzzle pieces that got it to work.