Autobackup fails with certificate error for acb.netgate.com
-
openssl s_client -connect acb.netgate.com:443 -showcertsor :
[24.03-RELEASE][root@pfSense.bhf.tld]/root: openssl s_client -connect acb.netgate.com:443 -showcerts | grep 'NotAfter' depth=2 C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority verify return:1 depth=1 C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA verify return:1 depth=0 CN = *.netgate.com verify return:1 v:NotBefore: Mar 28 00:00:00 2024 GMT; NotAfter: Apr 28 23:59:59 2025 GMT v:NotBefore: Nov 2 00:00:00 2018 GMT; NotAfter: Dec 31 23:59:59 2030 GMT v:NotBefore: Mar 12 00:00:00 2019 GMT; NotAfter: Dec 31 23:59:59 2028 GMT ....They all look fine and valid to me.
-
@Gertjan Thanks for check
However when attempt an automated backup via acb in pfsense webgui it fails with the following error.
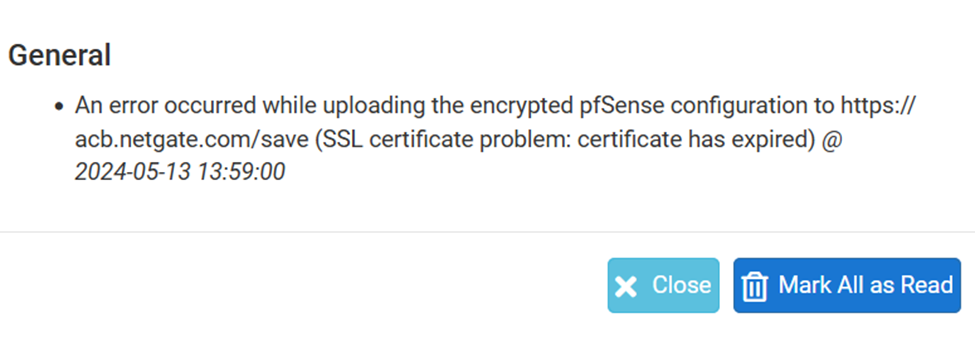
Additionally when I inspect the cert via the browser I only see the old cert...
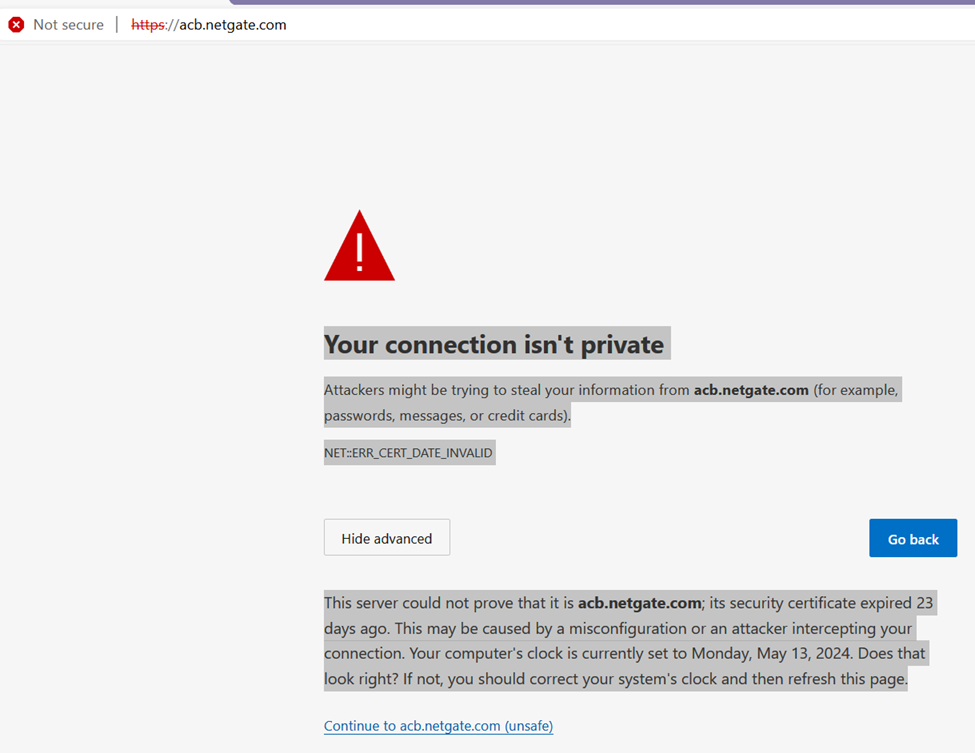
These errors persist after cache and site settings purging in the browser.
Not sure what to do to re-establish connectivity to acb.netgate.com within pfsense. Nor why my browsers do not see the current certs.
Again thanks for assistance.
-
Strange.
No issues what so ever.
Most of the 1+ million pfSense routers use acb at least every day.I've many lines like this :
What do you see when you execute :
openssl s_client -connect acb.netgate.com:443 -showcerts(console or SSH access - option 8)
-
If it was not strange I would not be asking for help.
The response to the openssl query is below.
-- bob h.
[2.7.2-RELEASE][admin@frontdoor.holzmans.net]/root: openssl s_client -connect acb.netgate.com:443 -showcerts
CONNECTED(00000003)
depth=2 C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
verify return:1
depth=1 C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
verify return:1
depth=0 CN = *.netgate.com
verify error:num=10:certificate has expired
notAfter=Apr 20 23:59:59 2024 GMT
verify return:1
depth=0 CN = *.netgate.com
notAfter=Apr 20 23:59:59 2024 GMT
verify return:1Certificate chain
0 s:CN = *.netgate.com
i:C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Mar 21 00:00:00 2023 GMT; NotAfter: Apr 20 23:59:59 2024 GMT
-----BEGIN CERTIFICATE-----
MIIGMTCCBRmgAwIBAgIRAPPMkhpx6g8NIGNyX+WdM6IwDQYJKoZIhvcNAQELBQAw
gY8xCzAJBgNVBAYTAkdCMRswGQYDVQQIExJHcmVhdGVyIE1hbmNoZXN0ZXIxEDAO
BgNVBAcTB1NhbGZvcmQxGDAWBgNVBAoTD1NlY3RpZ28gTGltaXRlZDE3MDUGA1UE
AxMuU2VjdGlnbyBSU0EgRG9tYWluIFZhbGlkYXRpb24gU2VjdXJlIFNlcnZlciBD
QTAeFw0yMzAzMjEwMDAwMDBaFw0yNDA0MjAyMzU5NTlaMBgxFjAUBgNVBAMMDSou
bmV0Z2F0ZS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCy+Wd9
CUV/gI0XcBL3d2AOHkNrOxfwGPG+HYcWy+VQMQdyq9ZC6WOEg/VVcHjNvByG/WT+
hrr42nTqTwN60KEwccFdI7bYRvy0i1z8x6WgzOoBZZF/OORtzCakpLpFoX3P9dpa
D4Z+bfykZVmAnEBFjuONPssVDScgIn9rw2sT+v9KzNFOdFmxL/PQFVa7nNGxwnMa
0L1RX6CKaVlhKr2rxnZ2KG9XnToThiJqF519jfrYhoU7MDv/nOU1Fr598JkJj1Z8
oM0uhpdLLLkaVsJU5/grT466LP+8gJh7XhbueB7+t5hfVMzJDLWrJQF6wu851iCx
GF2UnkleupdKdOpfAgMBAAGjggL8MIIC+DAfBgNVHSMEGDAWgBSNjF7EVK2K4Xfp
m/mbBeG4AY1h4TAdBgNVHQ4EFgQUvD/jBgkYHEcGS6aX0lInN62iWBowDgYDVR0P
AQH/BAQDAgWgMAwGA1UdEwEB/wQCMAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsG
AQUFBwMCMEkGA1UdIARCMEAwNAYLKwYBBAGyMQECAgcwJTAjBggrBgEFBQcCARYX
aHR0cHM6Ly9zZWN0aWdvLmNvbS9DUFMwCAYGZ4EMAQIBMIGEBggrBgEFBQcBAQR4
MHYwTwYIKwYBBQUHMAKGQ2h0dHA6Ly9jcnQuc2VjdGlnby5jb20vU2VjdGlnb1JT
QURvbWFpblZhbGlkYXRpb25TZWN1cmVTZXJ2ZXJDQS5jcnQwIwYIKwYBBQUHMAGG
F2h0dHA6Ly9vY3NwLnNlY3RpZ28uY29tMCUGA1UdEQQeMByCDSoubmV0Z2F0ZS5j
b22CC25ldGdhdGUuY29tMIIBfgYKKwYBBAHWeQIEAgSCAW4EggFqAWgAdgB2/4g/
Crb7lVHCYcz1h7o0tKTNuyncaEIKn+ZnTFo6dAAAAYcE93tjAAAEAwBHMEUCIQCv
BDkuRb471AChwKELpE3CVMBzncDlOtPi7J0Pu/C7MQIgL175rec6oTGljsSeSjee
fSzDj1204sZODg7uLPyxvukAdgDatr9rP7W2Ip+bwrtca+hwkXFsu1GEhTS9pD0w
SNf7qwAAAYcE93u3AAAEAwBHMEUCIQCAX5CyBg+bjrUV0b3fuP0rZPNV/VDWjl6o
tDb0zlP4YwIgW/2QwO4Pb0TuFL0iIzexr+LDAPfV9xLtKRMehwIJPvsAdgDuzdBk
1dsazsVct520zROiModGfLzs3sNRSFlGcR+1mwAAAYcE93uHAAAEAwBHMEUCIQC0
kgZijXE25dgNInUtr9vjqyCmK/Q6hLsNzosg6qvVoQIgP1d3glCV/TkwJCxhn/pS
jrj8eXFSaCCPIb3OCQyVh1QwDQYJKoZIhvcNAQELBQADggEBAMCesq1QHfQr9V5L
BhMjuE6LFVYB113oVnSp3AcZNoHfx0IFfkusdQN4JlMLsJXFWvU7bggD/NQOk/c8
xlLcBbKsgfbGI64Ab4VPLkgmkny6HpxUSx86t91SZw/AaCepcScX2cX36j7z8S2K
O9q8ZE9vqMgFSfk9PBBiUUY30Adqms6KSovaFeklbAQULilg+N39wuVBRhOrLF8g
Y5GlE3jBZlwoaZUM/42JD/lZv9joL6CcvfpUmLViQ0bBBnqVrLXw27uRr4QaUXAq
H98m6VY98Co1++JlXaiuISHJF/9y+lMecB8DQ3JBeqLfPzi07BFnZ0J/7fABPIug
+xeMKlA=
-----END CERTIFICATE-----
1 s:C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
i:C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA384
v:NotBefore: Nov 2 00:00:00 2018 GMT; NotAfter: Dec 31 23:59:59 2030 GMT
-----BEGIN CERTIFICATE-----
MIIGEzCCA/ugAwIBAgIQfVtRJrR2uhHbdBYLvFMNpzANBgkqhkiG9w0BAQwFADCB
iDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0pl
cnNleSBDaXR5MR4wHAYDVQQKExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNV
BAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTgx
MTAyMDAwMDAwWhcNMzAxMjMxMjM1OTU5WjCBjzELMAkGA1UEBhMCR0IxGzAZBgNV
BAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UEBxMHU2FsZm9yZDEYMBYGA1UE
ChMPU2VjdGlnbyBMaW1pdGVkMTcwNQYDVQQDEy5TZWN0aWdvIFJTQSBEb21haW4g
VmFsaWRhdGlvbiBTZWN1cmUgU2VydmVyIENBMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEA1nMz1tc8INAA0hdFuNY+B6I/x0HuMjDJsGz99J/LEpgPLT+N
TQEMgg8Xf2Iu6bhIefsWg06t1zIlk7cHv7lQP6lMw0Aq6Tn/2YHKHxYyQdqAJrkj
eocgHuP/IJo8lURvh3UGkEC0MpMWCRAIIz7S3YcPb11RFGoKacVPAXJpz9OTTG0E
oKMbgn6xmrntxZ7FN3ifmgg0+1YuWMQJDgZkW7w33PGfKGioVrCSo1yfu4iYCBsk
Haswha6vsC6eep3BwEIc4gLw6uBK0u+QDrTBQBbwb4VCSmT3pDCg/r8uoydajotY
uK3DGReEY+1vVv2Dy2A0xHS+5p3b4eTlygxfFQIDAQABo4IBbjCCAWowHwYDVR0j
BBgwFoAUU3m/WqorSs9UgOHYm8Cd8rIDZsswHQYDVR0OBBYEFI2MXsRUrYrhd+mb
+ZsF4bgBjWHhMA4GA1UdDwEB/wQEAwIBhjASBgNVHRMBAf8ECDAGAQH/AgEAMB0G
A1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAbBgNVHSAEFDASMAYGBFUdIAAw
CAYGZ4EMAQIBMFAGA1UdHwRJMEcwRaBDoEGGP2h0dHA6Ly9jcmwudXNlcnRydXN0
LmNvbS9VU0VSVHJ1c3RSU0FDZXJ0aWZpY2F0aW9uQXV0aG9yaXR5LmNybDB2Bggr
BgEFBQcBAQRqMGgwPwYIKwYBBQUHMAKGM2h0dHA6Ly9jcnQudXNlcnRydXN0LmNv
bS9VU0VSVHJ1c3RSU0FBZGRUcnVzdENBLmNydDAlBggrBgEFBQcwAYYZaHR0cDov
L29jc3AudXNlcnRydXN0LmNvbTANBgkqhkiG9w0BAQwFAAOCAgEAMr9hvQ5Iw0/H
ukdN+Jx4GQHcEx2Ab/zDcLRSmjEzmldS+zGea6TvVKqJjUAXaPgREHzSyrHxVYbH
7rM2kYb2OVG/Rr8PoLq0935JxCo2F57kaDl6r5ROVm+yezu/Coa9zcV3HAO4OLGi
H19+24rcRki2aArPsrW04jTkZ6k4Zgle0rj8nSg6F0AnwnJOKf0hPHzPE/uWLMUx
RP0T7dWbqWlod3zu4f+k+TY4CFM5ooQ0nBnzvg6s1SQ36yOoeNDT5++SR2RiOSLv
xvcRviKFxmZEJCaOEDKNyJOuB56DPi/Z+fVGjmO+wea03KbNIaiGCpXZLoUmGv38
sbZXQm2V0TP2ORQGgkE49Y9Y3IBbpNV9lXj9p5v//cWoaasm56ekBYdbqbe4oyAL
l6lFhd2zi+WJN44pDfwGF/Y4QA5C5BIG+3vzxhFoYt/jmPQT2BVPi7Fp2RBgvGQq
6jG35LWjOhSbJuMLe/0CjraZwTiXWTb2qHSihrZe68Zk6s+go/lunrotEbaGmAhY
LcmsJWTyXnW0OMGuf1pGg+pRyrbxmRE1a6Vqe8YAsOf4vmSyrcjC8azjUeqkk+B5
yOGBQMkKW+ESPMFgKuOXwIlCypTPRpgSabuY0MLTDXJLR27lk8QyKGOHQ+SwMj4K
00u/I5sUKUErmgQfky3xxzlIPK1aEn8=
-----END CERTIFICATE-----
2 s:C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
i:C = GB, ST = Greater Manchester, L = Salford, O = Comodo CA Limited, CN = AAA Certificate Services
a:PKEY: rsaEncryption, 4096 (bit); sigalg: RSA-SHA384
v:NotBefore: Mar 12 00:00:00 2019 GMT; NotAfter: Dec 31 23:59:59 2028 GMT
-----BEGIN CERTIFICATE-----
MIIFgTCCBGmgAwIBAgIQOXJEOvkit1HX02wQ3TE1lTANBgkqhkiG9w0BAQwFADB7
MQswCQYDVQQGEwJHQjEbMBkGA1UECAwSR3JlYXRlciBNYW5jaGVzdGVyMRAwDgYD
VQQHDAdTYWxmb3JkMRowGAYDVQQKDBFDb21vZG8gQ0EgTGltaXRlZDEhMB8GA1UE
AwwYQUFBIENlcnRpZmljYXRlIFNlcnZpY2VzMB4XDTE5MDMxMjAwMDAwMFoXDTI4
MTIzMTIzNTk1OVowgYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpOZXcgSmVyc2V5
MRQwEgYDVQQHEwtKZXJzZXkgQ2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBO
ZXR3b3JrMS4wLAYDVQQDEyVVU0VSVHJ1c3QgUlNBIENlcnRpZmljYXRpb24gQXV0
aG9yaXR5MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAgBJlFzYOw9sI
s9CsVw127c0n00ytUINh4qogTQktZAnczomfzD2p7PbPwdzx07HWezcoEStH2jnG
vDoZtF+mvX2do2NCtnbyqTsrkfjib9DsFiCQCT7i6HTJGLSR1GJk23+jBvGIGGqQ
Ijy8/hPwhxR79uQfjtTkUcYRZ0YIUcuGFFQ/vDP+fmyc/xadGL1RjjWmp2bIcmfb
IWax1Jt4A8BQOujM8Ny8nkz+rwWWNR9XWrf/zvk9tyy29lTdyOcSOk2uTIq3XJq0
tyA9yn8iNK5+O2hmAUTnAU5GU5szYPeUvlM3kHND8zLDU+/bqv50TmnHa4xgk97E
xwzf4TKuzJM7UXiVZ4vuPVb+DNBpDxsP8yUmazNt925H+nND5X4OpWaxKXwyhGNV
icQNwZNUMBkTrNN9N6frXTpsNVzbQdcS2qlJC9/YgIoJk2KOtWbPJYjNhLixP6Q5
D9kCnusSTJV882sFqV4Wg8y4Z+LoE53MW4LTTLPtW//e5XOsIzstAL81VXQJSdhJ
WBp/kjbmUZIO8yZ9HE0XvMnsQybQv0FfQKlERPSZ51eHnlAfV1SoPv10Yy+xUGUJ
5lhCLkMaTLTwJUdZ+gQek9QmRkpQgbLevni3/GcV4clXhB4PY9bpYrrWX1Uu6lzG
KAgEJTm4Diup8kyXHAc/DVL17e8vgg8CAwEAAaOB8jCB7zAfBgNVHSMEGDAWgBSg
EQojPpbxB+zirynvgqV/0DCktDAdBgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rID
ZsswDgYDVR0PAQH/BAQDAgGGMA8GA1UdEwEB/wQFMAMBAf8wEQYDVR0gBAowCDAG
BgRVHSAAMEMGA1UdHwQ8MDowOKA2oDSGMmh0dHA6Ly9jcmwuY29tb2RvY2EuY29t
L0FBQUNlcnRpZmljYXRlU2VydmljZXMuY3JsMDQGCCsGAQUFBwEBBCgwJjAkBggr
BgEFBQcwAYYYaHR0cDovL29jc3AuY29tb2RvY2EuY29tMA0GCSqGSIb3DQEBDAUA
A4IBAQAYh1HcdCE9nIrgJ7cz0C7M7PDmy14R3iJvm3WOnnL+5Nb+qh+cli3vA0p+
rvSNb3I8QzvAP+u431yqqcau8vzY7qN7Q/aGNnwU4M309z/+3ri0ivCRlv79Q2R+
/czSAaF9ffgZGclCKxO/WIu6pKJmBHaIkU4MiRTOok3JMrO66BQavHHxW/BBC5gA
CiIDEOUMsfnNkjcZ7Tvx5Dq2+UUTJnWvu6rvP3t3O9LEApE9GQDTF1w52z97GA1F
zZOFli9d31kWTz9RvdVFGD/tSo7oBmF0Ixa1DVBzJ0RHfxBdiSprhTEUxOipakyA
vGp4z7h/jnZymQyd/teRCBaho1+V
-----END CERTIFICATE-----Server certificate
subject=CN = *.netgate.com
issuer=C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CANo client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bitsSSL handshake has read 5131 bytes and written 401 bytes
Verification error: certificate has expiredNew, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 10 (certificate has expired)
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 3A7762FC3006B3684DE6C7457DCBA3076648109C9A91A0C5EE7E70E97CED3128
Session-ID-ctx:
Resumption PSK: 7084DDB0F37B1602F7B4F2FE3A43211332E6B2FE9A86E818BA106B755A645DA9CE55B9DA7C13A4132986091E4CC56278
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 5d 8d 4e ab 95 6c 31 26-db 89 4a 7f a8 60 bb 73 ].N..l1&..J...s 0010 - 57 2f 83 bf 5f 03 cf d8-ce af a1 4f d1 58 46 1a W/.._......O.XF. 0020 - fe e0 72 9d 46 bb e4 72-e1 b0 b9 d8 b5 00 36 e8 ..r.F..r......6. 0030 - 58 d9 a6 38 b5 a7 7d 73-a0 76 d1 bc b9 19 82 dd X..8..}s.v...... 0040 - f0 f1 68 87 2d 58 65 ba-9a 49 c6 23 6c 4e b1 48 ..h.-Xe..I.#lN.H 0050 - d9 9d cc 78 0a ff c4 2d-00 81 f7 26 62 bb ae f2 ...x...-...&b... 0060 - a9 29 ff 1b 75 eb 96 86-6c d4 f5 23 a7 f5 1a cc .)..u...l..#.... 0070 - a2 8e bb 0d 58 b4 8f 98-33 94 b3 9a ec aa db 0f ....X...3....... 0080 - c1 f2 f7 3e 28 d6 2f f6-30 f5 00 b3 22 88 c2 7f ...>(./.0..."... 0090 - cb 69 f6 16 d9 eb 17 80-23 82 fb 2d 7f 18 8d c6 .i......#..-.... 00a0 - ff 6a 57 99 a0 da 11 a5-23 09 6d 96 4f 26 40 74 .jW.....#.m.O&@t 00b0 - 0b 89 0a f2 1f c1 07 33-d1 b9 5f c3 7b 8f 4c 33 .......3.._.{.L3 00c0 - 00 76 79 a2 b3 1c 76 11-36 36 04 3e c8 f9 2e 3e .vy...v.66.>...> 00d0 - 7e e4 8f 0b 96 71 c4 60-0e 00 95 7b a9 f8 49 bb ~....q....{..I.Start Time: 1715686502 Timeout : 7200 (sec) Verify return code: 10 (certificate has expired) Extended master secret: no Max Early Data: 0
read R BLOCK
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: EFD0A9727F203FFCDEECA1BB18F2E49567CE081E94A8AF2E12A58DEDC00ACB7E
Session-ID-ctx:
Resumption PSK: 2684BDEE6D7958673899B089FC129CDBC05AF2D2636001D784BB83921307F6A0EB7E533B3781F698CFB8D7DF651E173F
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 5d 8d 4e ab 95 6c 31 26-db 89 4a 7f a8 60 bb 73 ].N..l1&..J..`.s
0010 - fd 2e b3 0b 0d bd 99 ee-0f 7b c2 4d 48 3b 85 65 .........{.MH;.e
0020 - a3 c0 7b 85 62 07 79 0f-bb d8 35 6b 78 e2 cf 95 ..{.b.y...5kx...
0030 - d2 72 09 f1 da 21 71 3f-81 d3 8b 89 6e ed 7f 12 .r...!q?....n...
0040 - 3f 27 c1 34 38 d0 29 4a-c7 51 f7 7d dc e6 73 cf ?'.48.)J.Q.}..s.
0050 - ea 0d d2 21 38 7c e5 20-42 35 b8 06 5c 8f 7e 82 ...!8|. B5...~.
0060 - 65 92 f0 0e 96 94 be 68-3b 5d 62 7a 12 0b 32 4b e......h;]bz..2K
0070 - 68 c3 0d 15 c1 a1 ce b8-74 11 82 b8 3f e3 b4 3f h.......t...?..?
0080 - 19 06 83 54 2e 9b c4 19-c5 26 1d 69 ef af 11 eb ...T.....&.i....
0090 - b3 da 1b 7f a1 77 d8 6f-28 cb a5 a1 96 ae e4 fe .....w.o(.......
00a0 - 36 45 42 e8 78 4d 33 6a-a6 3b 0f ae 03 9a f0 65 6EB.xM3j.;.....e
00b0 - b2 80 40 35 1a 2e 28 1e-5f 8d ba 27 1f b2 97 da ..@5..(._..'....
00c0 - e3 ed 51 af 90 db 23 2e-84 39 7a 17 3e 47 25 b5 ..Q...#..9z.>G%.
00d0 - 99 b3 19 ac 34 b6 fe 2d-6f 4d 98 07 14 f4 04 e7 ....4..-oM......Start Time: 1715686502 Timeout : 7200 (sec) Verify return code: 10 (certificate has expired) Extended master secret: no Max Early Data: 0
read R BLOCK
closed -
I don't get it.
Your expired *.netgate.com certificate, that's the certificate of 'last year'.
"acb.netgate.com" is "208.123.73.69" for you, right ?
The same *.netgate.com certificate is used for this forum. -
Actually, it is not. For me acb.netgate.com is reachable at 208.123.73.69.
Here's a ping from my pfsense box
[2.7.2-RELEASE][admin@frontdoor.holzmans.net]/root: ping acb.netgate.com
PING acb.netgate.com (208.123.73.212): 56 data bytes
64 bytes from 208.123.73.212: icmp_seq=0 ttl=50 time=56.295 ms
64 bytes from 208.123.73.212: icmp_seq=1 ttl=50 time=55.002 ms
64 bytes from 208.123.73.212: icmp_seq=2 ttl=50 time=49.690 ms
64 bytes from 208.123.73.212: icmp_seq=3 ttl=50 time=56.802 ms
64 bytes from 208.123.73.212: icmp_seq=4 ttl=50 time=54.678 msand a traceroute
[2.7.2-RELEASE][admin@frontdoor.holzmans.net]/root: traceroute acb.netgate.com
traceroute to acb.netgate.com (208.123.73.212), 64 hops max, 40 byte packets
1 syn-068-174-240-001.res.spectrum.com (68.174.240.1) 17.734 ms 15.232 ms 1 5.167 ms
2 lag-56.nyquny9102h.netops.charter.com (68.173.201.58) 14.417 ms 16.880 ms 16.691 ms
3 lag-102.nyquny9101r.netops.charter.com (68.173.198.122) 16.018 ms 27.869 m s 7.463 ms
4 lag-25.nycmny837aw-bcr00.netops.charter.com (107.14.19.22) 13.968 ms
lag-15.nycmny837aw-bcr00.netops.charter.com (66.109.6.76) 16.838 ms
lag-25.nycmny837aw-bcr00.netops.charter.com (107.14.19.22) 17.234 ms
5 lag-20.nwrknjmd67w-bcr00.netops.charter.com (66.109.5.139) 24.029 ms 9.439 ms
lag-11.nwrknjmd67w-bcr00.netops.charter.com (66.109.6.26) 10.484 ms
6 * * *
7 * * *
8 4.14.49.2 (4.14.49.2) 54.334 ms 52.970 ms 51.256 ms
9 net66-219-34-194.static-customer.corenap.com (66.219.34.194) 49.493 ms 51.850 ms 57.439 ms
10 fw1-zcolo.netgate.com (208.123.73.4) 53.851 ms 56.786 ms 58.468 ms
11 acb.netgate.com (208.123.73.212) 67.462 ms 58.284 ms 62.263 ms -
@robhol said in Autobackup fails with certificate error for acb.netgate.com:
208.123.73.212
Ok, bingo :
[24.03-RELEASE][root@pfSense.bhf.tld]/root: openssl s_client -connect 208.123.73.212:443 -showcerts | grep 'NotAfter' Can't use SSL_get_servername depth=2 C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority verify return:1 depth=1 C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA verify return:1 depth=0 CN = *.netgate.com verify error:num=10:certificate has expired notAfter=Apr 20 23:59:59 2024 GMT verify return:1 depth=0 CN = *.netgate.com notAfter=Apr 20 23:59:59 2024 GMT verify return:1 v:NotBefore: Mar 21 00:00:00 2023 GMT; NotAfter: Apr 20 23:59:59 2024 GMT v:NotBefore: Nov 2 00:00:00 2018 GMT; NotAfter: Dec 31 23:59:59 2030 GMT v:NotBefore: Mar 12 00:00:00 2019 GMT; NotAfter: Dec 31 23:59:59 2028 GMTI see the same thing now.
"208.123.73.212" still uses an old certificate
@stephenw10 : acb.netgate.com, on "208.123.73.212" serves expired domain certificate.
Can you push a button somewhere
-
Those results prompted me to look at pfsense's hosts file. That address is hardwired in that file. I will try commenting out and see what happens.
Commenting out the address fails. Apparently the hosts file regenerates on reboot and it contains the wrong address for acb.netgate.com.
-
@robhol said in Autobackup fails with certificate error for acb.netgate.com:
look at pfsense's hosts file
This one : /etc/hosts ?
127.0.0.1 localhost localhost.bhf.tld ::1 localhost localhost.bhf.tld xxxxThe xxx are all the Static DHCP MAC leases (here : at the bottom of : Services > DHCP Server > LAN of every LAN)
and
the unbound domain overrides I've set up. Here : Services > DNS Resolver > General Settings at the bottom.By default this file contains (24.03 & 2.7.2) just two lines (AFAIK).
Certainly not a... 208.123.73.212 acb.netgate.com. ...edit : https://forum.netgate.com/topic/181704/unable-to-resolve-acb-netgate-com-notifications-every-10-seconds-for-hours/4?_=1715691230253 it was 208.123.73.212 for me a last year.
-
Problem solved! Mea culpa as you might have suspected.
Earlier this am I determined that host file contained the .212 address and that it was unremovable because the hosts file was regenerated on reboot. That and your last post led me to the DNS resolver and I found that I had put in an override for acb.netgate.com, apparently some time ago when I was having some upgrade issues. Removed the override and all is now well with autoconfig backup.
Thanks for your patience!!
-- bob h