FreeRadius Issue
-
I am facing the following problem. I'm using freeradius as a second authentication feature for my openvpn in pfsense, it works well, however, I found a security flaw. When I use the vpn file from user A, and when freeradius asks for a token to continue with the authentication/connection, if I use another token from user B, the communication connects normally. I would like to know if this is a bug or a known issue?
-
You mean User A also has the credentials of user B ?
@alvescaio said in FreeRadius Issue:
freeradius asks for a token
Can you detail : what is "token" here ? What does user A have that belongs to user B ?
But at least give a step by step explanation how you surfaced this issue.
-
Yes more info needed. Commonly the ovpn client file would be common to all users in some configurations. Though not if you are passing user certs in it.
-
hello guys.
I will explain better with an example.
Assuming that user A tries to connect to the C2S VPN via Openvpn, my openvpn is configured with Radius as the second authentication factor. for user A to connect to the VPN he needs the vpn .conf file installed on his desktop client, when user A initiates the connection he goes through the first authentication step that authenticates the certificate and data and is in the .conf file , in the second moment it asks for a token number that we obtain from the authenticator that is linked to freeradius, in my case the Microsoft authenticator the problem occurs at this stage, because if I use any token from any other user in the user A authentication process , the connection occurs normally, which should not occur, it should only occur with the token of user A, who is being authenticated
-
Ok so you have the server configured as 'Remote Access (SSL/TLS + User Auth)'?
Do you have
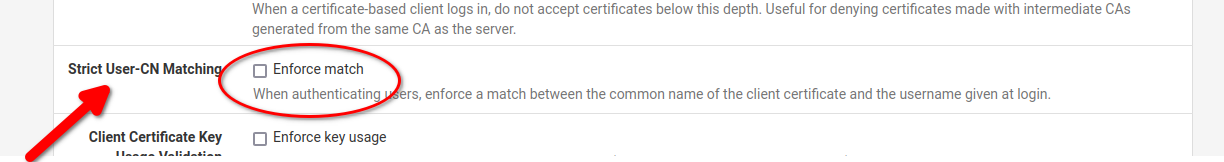
Strict User-CN Matchingenabled? -
To first question yes,
Whats restrict CN?
-
My question is not focused on your problem but I want to take advantage and ask you: Is your freeradius configured with an AD to obtain the users from there and not create them locally?
-
@oscar-pulgarin Freeradius not connect with AD, FreeRdius is configured only locally, with user created only freeradius base
-
@stephenw10 What's Strict User-CN Matching?
-
Strict User-CN Matching Enforce match: When authenticating users, enforce a match between the common name of the client certificate and the username given at login. -
@alvescaio hey there,
so, do you have (at least) two separate users in freeradius? And each having their own Init-Secret, so creating different OTPs with that authenticator app?
So user A has Init-Secret A1 and user B has Init-Secret B1.
Problem is: user A can authenticate with B1 as well as A1, while user B can do that with A1 and B1...
That about describing the prob? -
@stephenw10 said in FreeRadius Issue:
Strict User-CN Matching
Enforce match: When authenticating users, enforce a match between the common name of the client certificate and the username given at login.How do I check this
-
It's a setting the OpenVPN server config.
-
There...
But wouldn't that only make sure, that users have their own (common name matching!) certs?
-
Yes, but otherwise you could have a common cert for all users. Or, as may be happening here, a user could login using a username that doesn't match the user cert.
-
hey there,
okay, I use openvpn with freeradius and 2fa (otp) as well.I just tried this:
- created a testuser
- gave him his own usercert
- created a freeradius user for testuser, gave him his own init-secret (not the same one as my main user)
- I work with pins (additional to otp), gave testuser his own 4-digit pin
- did not set cn-match active
- exported vpn-config and imported on android device
...
a) tried with my main user and OTP of testuser....auth failed
b) tried vice-versa (testuser with OTP from mainuser)...auth failed
So, I cannot really create that problem here on my machine it seems...
Each user has his/her/its own username, usercert AND init-secret for OTP creation. It won't work using user A with OTP from user B here (which is what you want in the 1st place, right?).
So, no clue why it ain't working for you.Does this criss-crossing of OTPs also work with pfsense's Test Authentication under Diagnostics > Authentication? Here it won't. Each user need his /her own name and OTP...at least that's what my testing showed (hoping I did it right)... ;)
-
@the-other So gentlemen, I did exactly the process listed above, each user has their own certificate that is created when the user is created, I don't know if there is any way to link the user manager user with the freeradius user. EXAMPLE: when I create user A, and then create a user in freeradius for this user A authentication, I have to do some additional configuration.
-
@alvescaio I don't think a "link" is necessary...
Use the same name in User Management as in Freeradius User.
In Freeradius no password needs to be set (since you use OTP...and PIN).
Generate the init-secret, chose PIN (if wanted), scan QR-code, import in Auth-app. Then make sure you test under Diagnostics > Auth...should get a green sign with positive result.
Export openvpn cert with external auth, import...should do the trick, I hope. -
@the-other I think if something that I dont seeing.
-
If you set
Strict User-CN Matchingthen the use can only login with a username matching the cert CN. That will be defined in the local users but as long as Freeradius uses the same usernames it will apply the same there. It will fail if they try to login using a different username.